Staying on top of your system's vulnerabilities is the key to network security. But that's not easy given the huge complexity and the many failure points present in it.
This is where Vulnerability Assessment and Penetration Tools (VAPT) come in handy as they do the penetration testing and generate reports that contain a list of vulnerabilities. In many ways, these tools act as a dedicated IT admin whose only task is to constantly monitor the networks and look for vulnerabilities.
Here is our list of the best Vulnerability Assessment and Penetration Testing Tools:
- Invicti Security Scanner Automated VAPT tool scans the system for vulnerabilities and prioritizes the fix for each. Such an automated system makes web application testing a simple and reliable process.
- Acunetix Web Vulnerability Scanner Comprehensive web applications testing solution that works well for all environments. It comes with a host of features to enhance cybersecurity at a low cost.
- Intruder A cloud-based vulnerability scanner provides a number of deployment options that include external and network scanning, Web application security testing, and cloud platform connection security.
- Metasploit Advanced tool that helps its users to stay one step ahead of cybercriminals by empowering them with the right tools and framework to quickly identify and mitigate vulnerabilities.
- Nessus A vulnerability scanner that performs high-speed asset discovery, malware detection, target profiling, and more to keep your systems safe.
- Burp Suite Application testing tool for identifying the vulnerabilities of websites and applications automatically.
Undoubtedly, these tools are a convenient way to monitor networks and this explains why many companies have come up with VAPT tools with flexible and comprehensive features.
Our methodology for selecting the Best Vulnerability Assessment and Penetration Testing (VAPT) Tools:
We've broken down our analysis for you based on these key criteria:
- We focused on the tool's ability to comprehensively scan and identify vulnerabilities in various network environments.
- The capacity for continuous and automated testing was prioritized to ensure ongoing network security.
- We considered the tool's effectiveness in both web application security testing and cloud platform connection security.
- Ease of use and the ability to prioritize and manage identified vulnerabilities effectively were key criteria.
- We evaluated tools based on their advanced capabilities like high-speed asset discovery, malware detection, and target profiling.
The Best VAPT Tools
Here's a look at some of the tools to get an idea of what they offer and how they can benefit your business.
1. Invicti Security Scanner
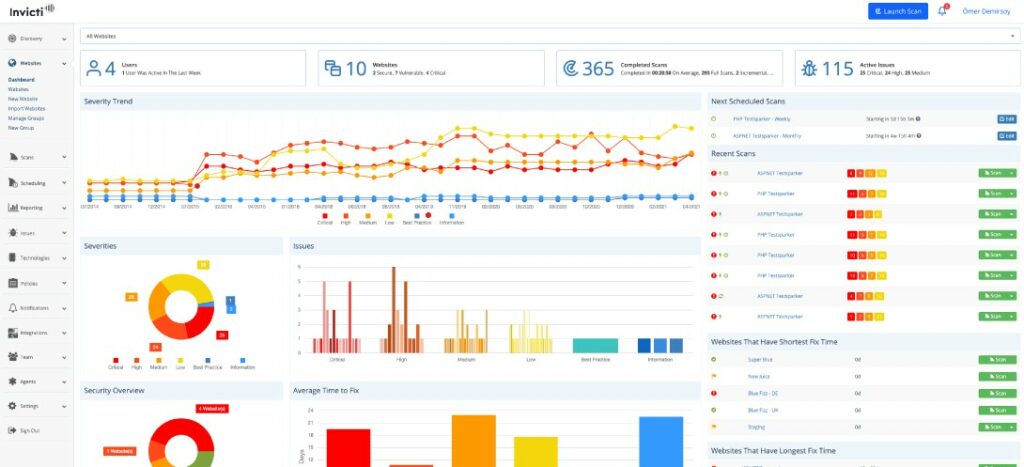
Invicti Security Scanner is a VAPT tool that fully automates the web security process. It automatically scans for vulnerabilities and helps to prioritize the fix, and in the process, protects the web assets.
Key Features:
- Crawls and scans all legacy and modern web applications
- Automatically assigns a severity level to every vulnerability, to help developers prioritize the fix
- Continuously scans the Internet to discover new assets based on their IP addresses and SSL certificates
- Generates a proof-of-exploit or proof-of-concept to confirm that the vulnerabilities are not false positives
- The dashboards are comprehensive and give all the information you need
- Uses scanning agents to reduce the scan time.
- The reports are extensive and customizable.
- Complies with all major standards such as ISO 27001, HIPAA, and PCI DSS.
- Integrates well with CI/CD platforms such as Jenkins and Bamboo.
Why do we recommend it?
Invicti stands out for its ability to fully automate the web security process, making it a valuable asset for continuous and comprehensive web asset protection.

Who is it recommended for?
It’s best suited for teams that manage legacy and modern web applications and require a solution that offers both severity-based prioritization and new asset discovery.
Pros:
- Features a highly intuitive and insightful admin dashboard
- Supports any web applications, web service, or API, regardless of framework
- Provides streamlined reports with prioritized vulnerabilities and remediation steps
- Eliminates false positives by safely exploiting vulnerabilities via read-only methods
- Integrates into dev ops easily providing quick feedback to prevent future bugs
Cons:
- Would like to see a trial rather than a demo
Pricing: Invicti offers three plans – Standard, Team, and Enterprise. They differ in the following important features.
Features | Standard | Team | Enterprise |
|---|---|---|---|
| Ideal for | Desktops | Hosted systems | Hosted and on-premise systems |
| Max number of websites | 20 | 50 | 50+ |
| API Access | Command Line | REST API | REST API |
| Dedicated tech support | No | No | Yes |
For pricing, contact the sales team.
Download: There are no free trials, but you can get a demo by clicking here.
2. Acunetix Web Vulnerability Scanner
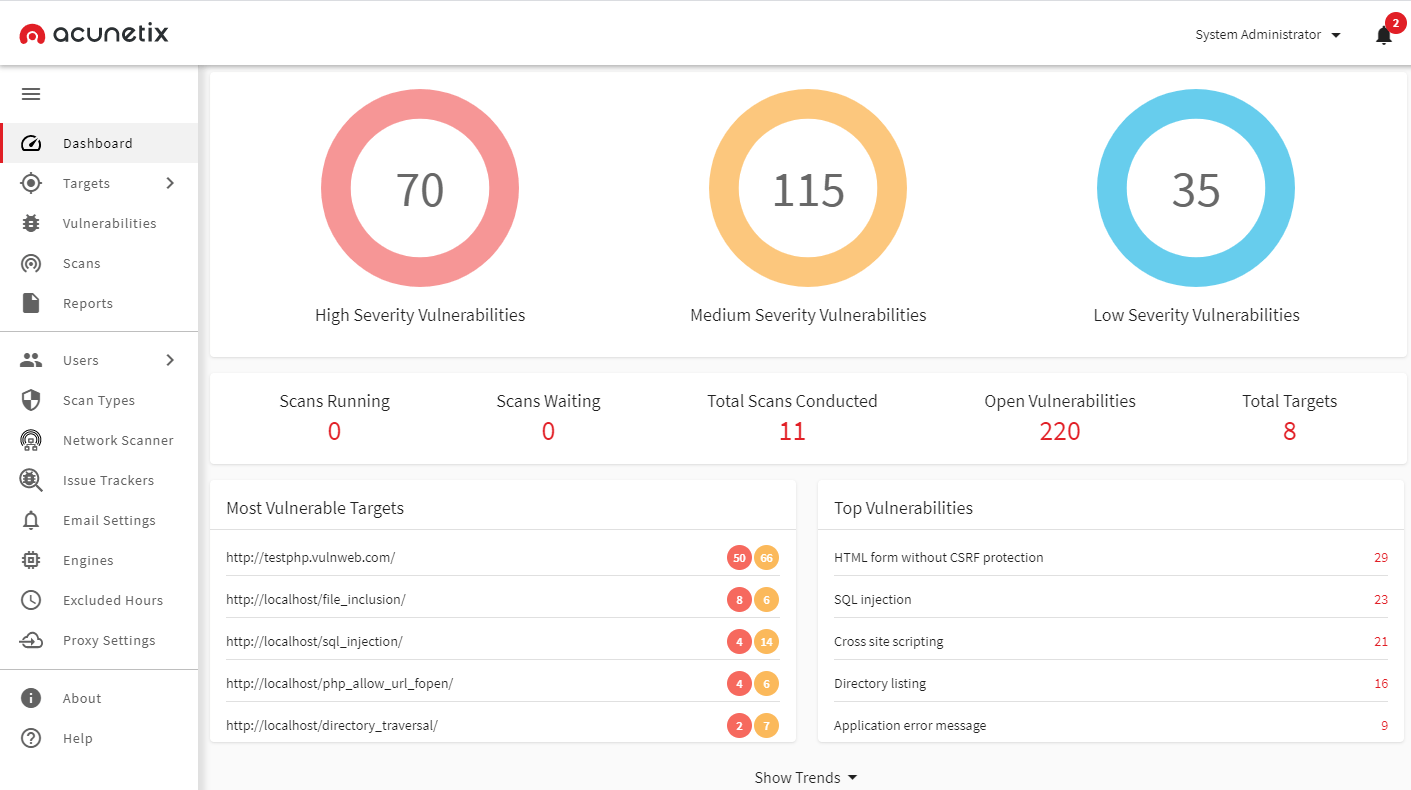
Acunetix is a comprehensive web application and security solution that identifies vulnerabilities and enhances your cybersecurity – all at a low cost. In this sense, Acunetix is more than just a vulnerability scanner and can rather be categorized as a complete web security solution.
Key Features:
- Integrates well with many applications such as Jenkins, Jira, GitHub, and Mantis.
- Provides its own API for integration with in-house tools
- One of the fastest web security tools available today
- Has one of the lowest false-positive rates
- Uses resources efficiently to identify new vulnerabilities and handle existing ones
- Supports the use of multiple scanning engines that are deployed locally
- Works well on Linux, macOS, and Windows operating systems
Why do we recommend it?
Acunetix is recommended for its speed and accuracy in identifying web vulnerabilities, coupled with one of the industry's lowest false-positive rates.

Who is it recommended for?
This tool is ideal for businesses of all sizes looking for a comprehensive web security solution, especially those that prioritize integration with a wide range of applications.
Pros:
- Designed specifically for application security
- Integrates with a large number of other tools such as OpenVAS
- Can detect and alert when misconfigurations are discovered
- Leverages automation to immediately stop threats and escalate issues based on the severity
Cons:
- Would like to see a trial version for testing
Pricing: There are three pricing plans – Standard, Premium, and Acunetix 360. The Standard plan starts at $4500 while the Premium starts at $7000 per year. The cost of Acunetix 360 is customized based on the number of applications hosted on the cloud or on-premises.
Download: There is no free trial but click here for a demo.
3. Intruder
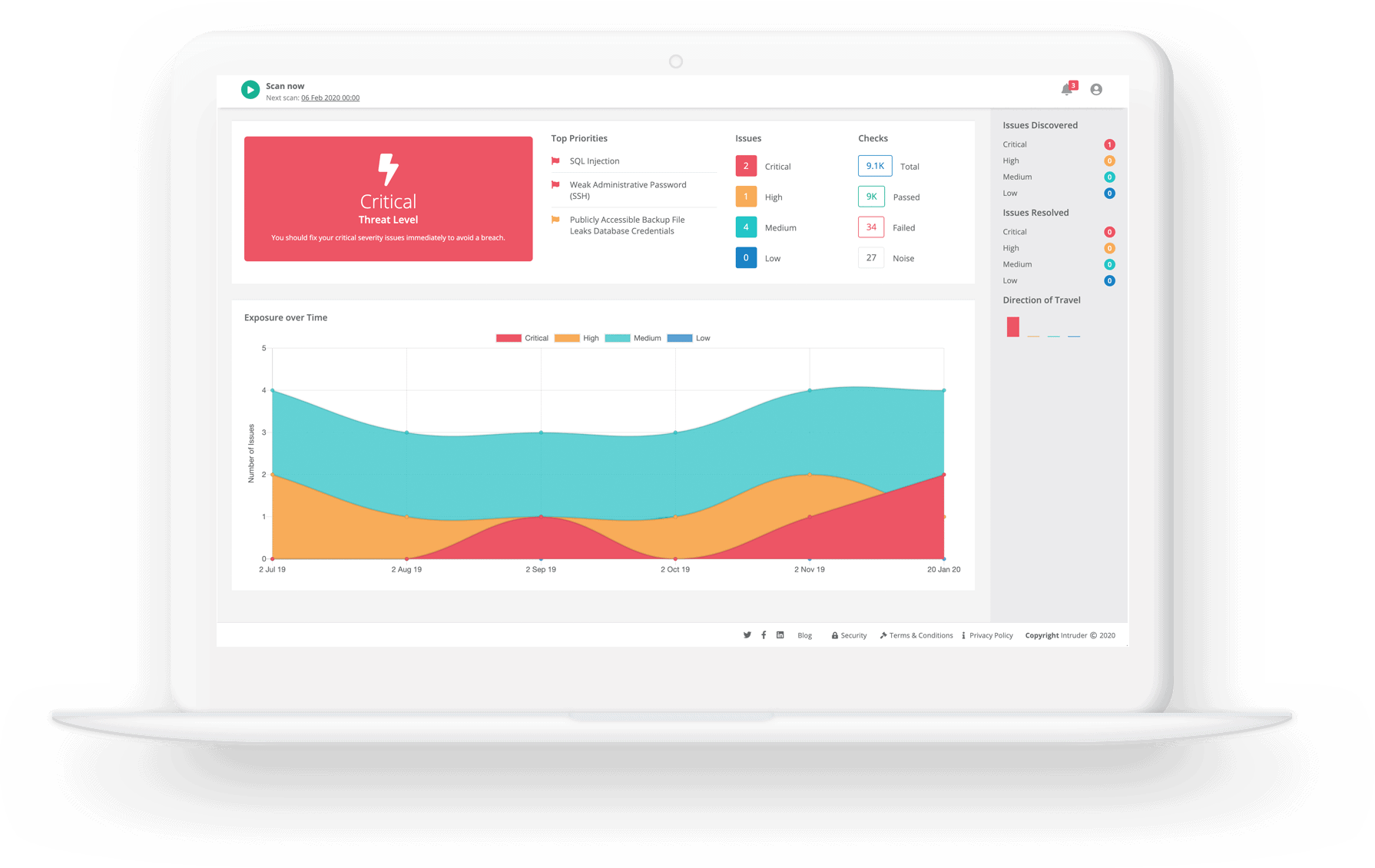
Intruder provides enterprise-grade security to thoroughly check an infrastructure for its vulnerabilities, so they can be fixed before hackers find it. With more than 140,000 pre-built security checks, it provides protection for all kinds of critical applications.
Key Features:
- Integrates well with the CI/CD pipeline and cloud providers
- An intuitive interface that also makes it easy to set up and use
- It automatically analyses the vulnerabilities and prioritizes them
- Reports only actionable issues that are likely to impact the security or efficiency of systems
- Provides streamlined visibility
Why do we recommend it?
Intruder is a top-tier choice for vulnerability management due to its comprehensive coverage and intelligent prioritization of threats. This makes it particularly effective for proactive security measures.

Who is it recommended for?
This tool is ideal for organizations seeking robust security solutions, especially those needing to safeguard critical applications and integrate security into their CI/CD pipeline.
Pros:
- Can perform scheduled vulnerability scans automatically
- Can scan all new devices for vulnerabilities and recommended patches for outdated machines
- Excellent UI – great over high-level insights and detailed breakdowns
- Offers human-powered penetration testing as a service
Cons:
- Is an advanced security platform that can take time to fully explore
- No free tier
Pricing: The Intruder has three plans and they are:
- Essential ($101 /month) – Provides external and internal scans and checks for over 10,000 security vulnerabilities and web application flaws.
- Pro ($161 / month) – Unlimited scans on demand, emerging threat notifications, and API integrations besides the features of the Essential plan.
- Vanguard ($1,195 / month) – Manual verification of scan results by expert pen testers, impact verification, reduction of false positives, and enterprise-grade scanning.
Get started by registering for the free trial.
4. Nessus
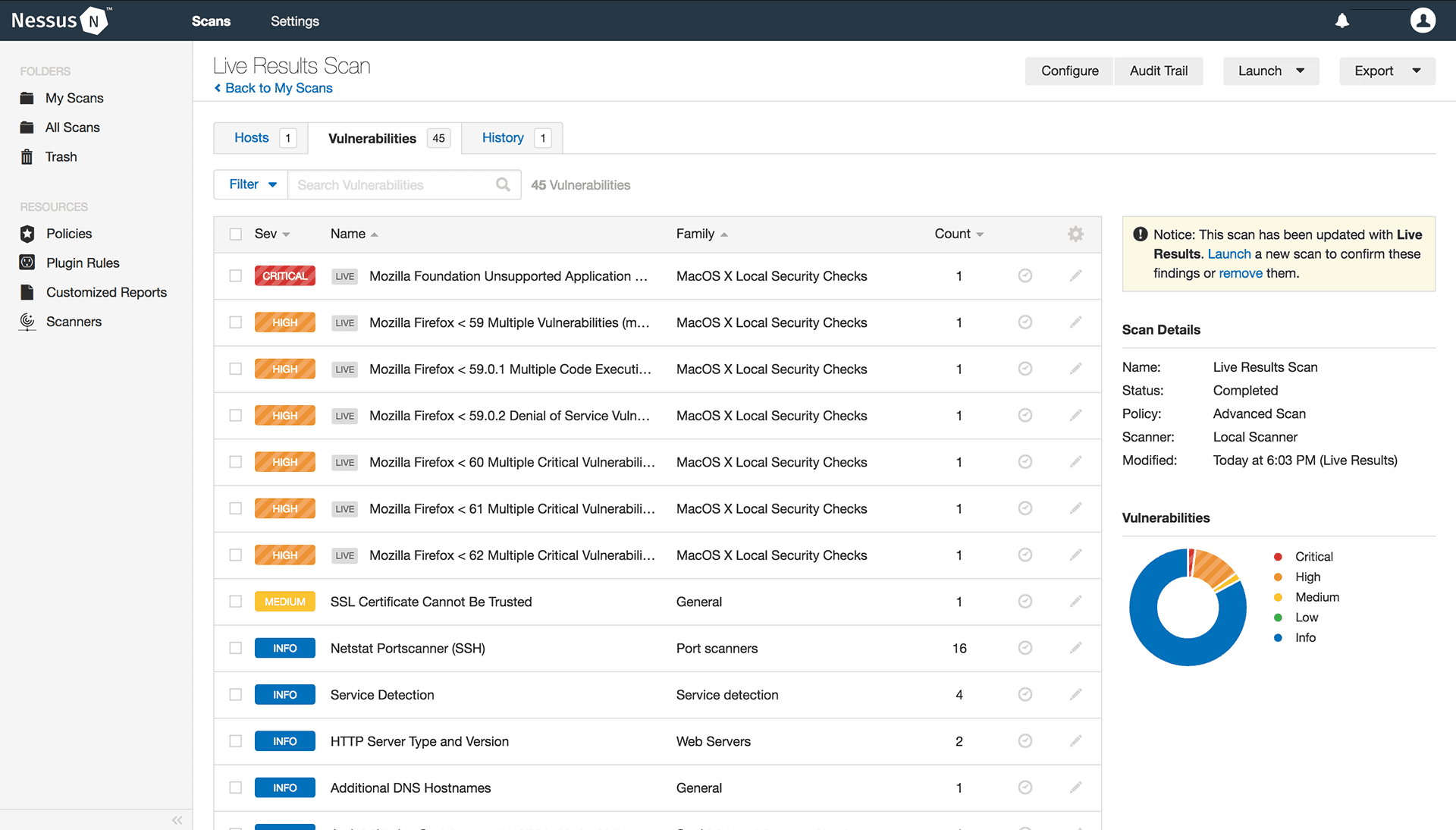
Nessus is another popular vulnerability scanning tool that scans all computers connected to a network and raises an alert at the first sign of intrusion or vulnerability, so these can be fixed at the earliest. It also comes with a host of convenient features that make scanning and fixing the vulnerabilities a quick and inexpensive process.
Key Features:
- Stays on top of the latest vulnerabilities, so the same can be identified quickly
- Comes with many pre-built templates that help to quickly understand the presence of vulnerabilities.
- Meets all compliance requirements with its 450+ compliance and configuration templates
- Makes it easy to create custom reports that are based on customized views and vulnerability types
- Allows you to group vulnerabilities based on several factors
- Gives you the option to “snooze” selected items, so you can focus on the issues that matter the most to you.
- Provides live results that help you track the progress of every vulnerability
- Generates reports in many formats such as CSV and HTML.
- Comes with a low false-positive rate, thanks to its stringent implementation of six sigma processes.
Why do we recommend it?
Nessus is renowned for its extensive vulnerability coverage and ease of use, making it an essential tool for efficient network security management.

Who is it recommended for?
This tool is recommended for organizations and individuals, including students and educators, seeking a versatile solution for network vulnerability scanning and compliance.
Pros:
- Offers a free vulnerability assessment tool
- Simple, easy-to-learn interface
- Little configuration needed, 450+ templates that support a range of devices and network types
- Includes vulnerability prioritization
Cons:
- Offers limited remediation tools and options
- Could benefit from more integrations into other SIEM platforms
Pricing: This tool comes in three plans and they are:
- Nessus Essentials (FREE) – Scans up to 16 IPs and is ideal for educators, students, and individuals who are starting their careers in this field.
- Nessus Professional ($2,790 per year) – Ideal for pen testers, security professionals, and consultants as it scans unlimited IPs, provides live results and comes with advanced support
- Tenable.io (Subscription-based) – This plan is most suited for enterprises of all sizes as it deploys unlimited scanners, enterprise scalability, predictive prioritization, role-based control, and advanced dashboards and reports.
Download: Click here to download the free version.
5. Burp Suite
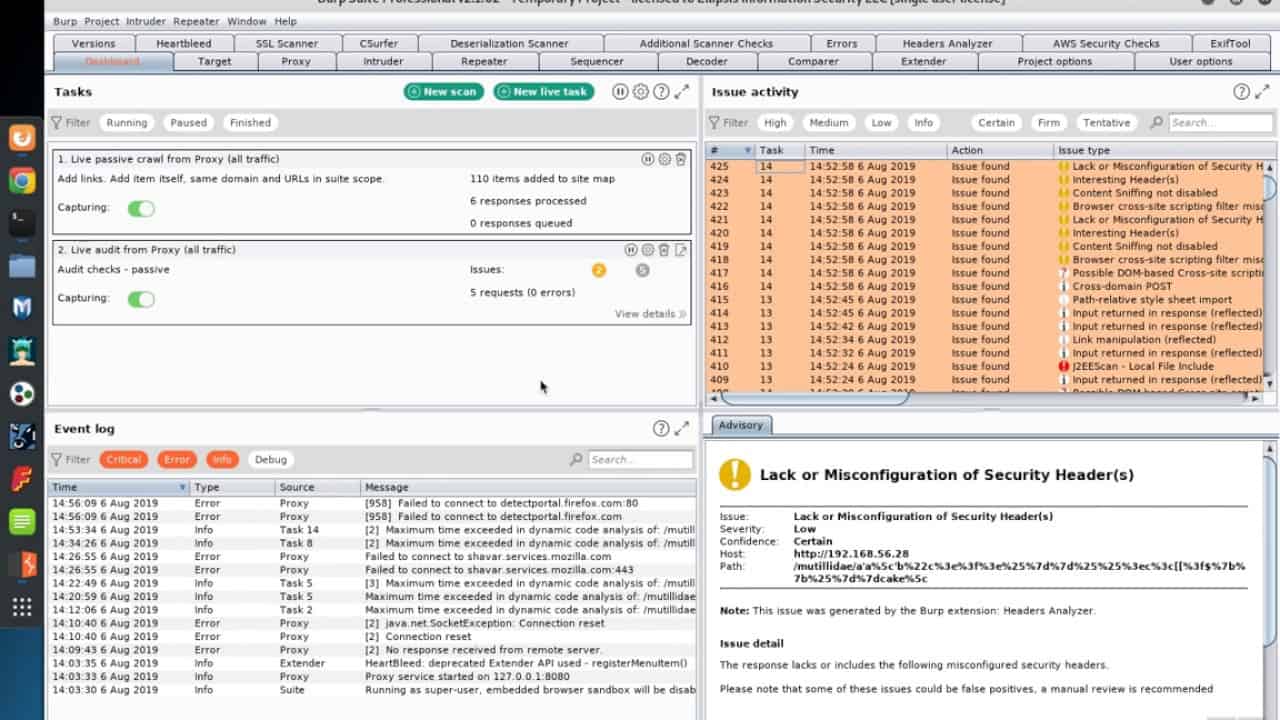
Burp Suite is a tool that accelerates application security testing with its automated penetration testing and scanning. It uses the latest research in cybersecurity to beef up its offerings and to ensure that its tools are up-to-date with the latest vulnerabilities.
Key Features:
- Its powerful proxy makes it easy to modify any HTTP(S) communication that passes through your browser.
- Manages recon data well
- Supports manual testing and human-guided automation testing
- Exposes hidden vulnerabilities that are hard to spot
- Speeds up the granular workflows
- Checks vulnerable websites and applications with clickjacking tools
- Auto enumerates dynamic URLs and their parameters to understand the size of your target application
- Works well with web sockets
- Tests the quality and strength of random tokens to strengthen their efficacy
Why do we recommend it?
Burp Suite is acclaimed for its advanced penetration testing capabilities and automated scanning, aiding in efficient application security testing.
Who is it recommended for?
Recommended for security professionals and small businesses, it’s an excellent choice for those requiring a comprehensive suite of tools to identify and address application vulnerabilities.
Pros:
- A collection of security tools designed specifically for security professionals
- The Community Edition is free – great for small businesses
- Available cross-platform for Windows, Linux, and Mac operating systems
Cons:
- Takes time to explore all the tools available in the suite
Pricing: There are two versions – Burp Suite Professional priced at $399 per user per year and the Burp Suite Enterprise.
This Enterprise version comes in three flavors,
- Launch ($9,585/year) – 15 concurrent scans and scans 105+ websites a week
- Grow ($17,565/year) – 35 concurrent scans and more than 245 websites a week
- Accelerate ($23,550/year) – 50+ concurrent scans and 350+ websites a week
Besides these two plans, it also has a Community Edition that comes with limited features and a bunch of manual tools for exploring your HTTPS traffic. It is FREE.
Download: Click here to download the latest version of the Community Edition.
6. Metasploit
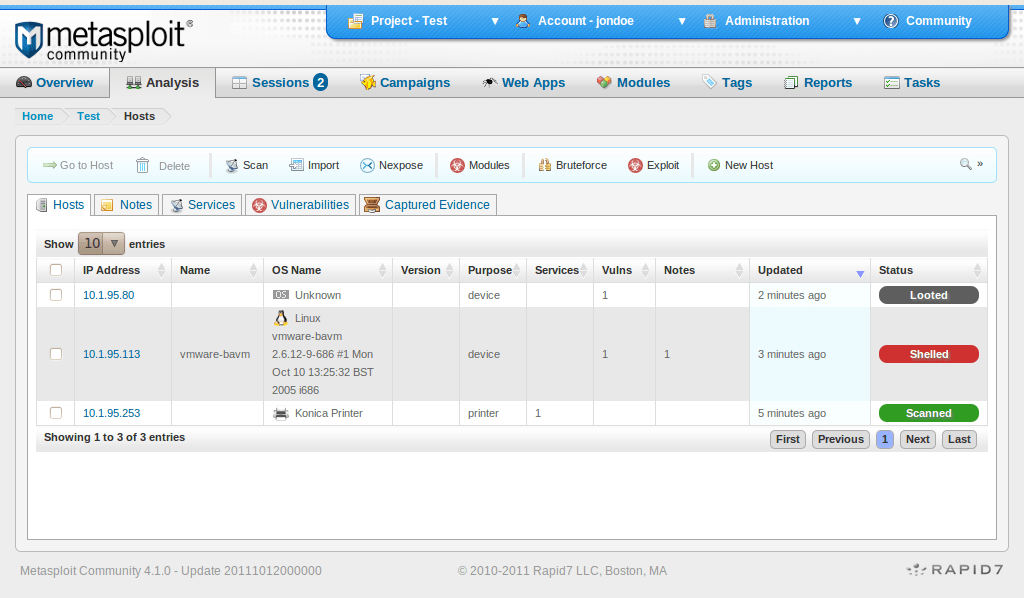
Metasploit has advanced tools for penetration testing through which it provides detailed information about the security vulnerabilities in a web application or website. It also supports IDS Signature development and is widely being used to develop and execute exploit code against a remote target device.
Key Features:
- Easy to install and highly reliable, regardless of the platform or programming language used.
- Includes about 1700 exploits spread across 25+ platforms, so most vulnerabilities are recognized quickly.
- Provides modules for 500+ payloads including dynamic payloads, meterpreter payloads, and command shell payloads.
- Its post-exploitation code feature helps test multiple layers of deep penetration
- The framework is made of many models and interfaces to support remote pen testing
- Enables port forwarding and communication across networks
Why do we recommend it?
Metasploit is highly recommended for its comprehensive range of exploits and payloads, making it an exceptionally versatile tool for in-depth penetration testing and security vulnerability analysis.
Who is it recommended for?
This tool is particularly suited for experienced security professionals and organizations that require an advanced, reliable framework for rigorous penetration testing and security assessment.
Pros:
- One of the most popular security frameworks in use today
- Has over of the largest communities – great for continuous support and up-to-date additions
- Available for free and commercial use
- Highly customizable with many open-source applications
Cons:
- Metasploit caters to more technical users, which increases the learning curve for beginners in the security space
Pricing: Metasploit comes in two editions – the OpenSource Metasploit Framework that's available for FREE and the Metasploit Pro if you're a part of an IT security team or a penetration tester, as the latter edition comes with commercial support and more advanced features. Contact the sales team for custom pricing of the Metasploit Pro version.
Download: Click here to download the Metasploit Framework and click here to try the Metasploit Pro version for 14 days.
Choosing a VAPT Tool
To conclude, VAPT Tools are an essential part of your organization's security as it helps to identify threats and vulnerabilities before they create a profound impact. These tools come with advanced features that not just identify threats but also analyze, and prioritize them, so they can be fixed right away. All these features help to greatly mitigate threats and boost the overall security of your websites and applications.