SNMP (Simple Management Network Protocol) is a very useful system that will help you to manage your enterprise’s network devices, as well as anything else that has a NIC (Network Interface Card). The standard has been around for a very long time, and it has evolved.
It has continued to get more sophisticated, and more secure, which is great for system administrators that need to keep an eye on how the network is behaving, and what the devices are doing. All of this added visibility helps keep daily operations running smoothly and can alert your IT team well in advance if there are any looming and impending disasters around the corner.
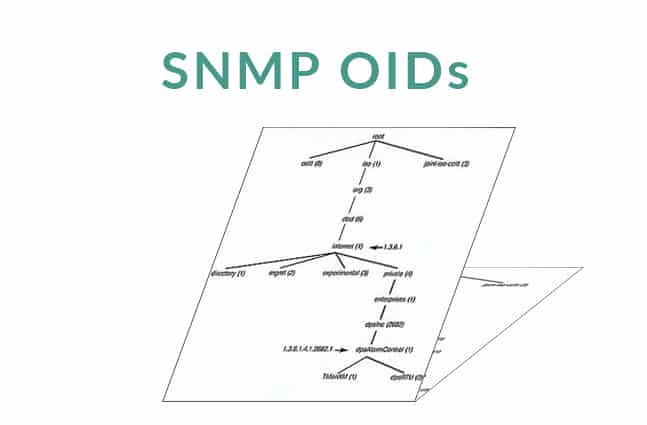
We will look at the inner workings of SNMP and see what shape the data format takes in its daily operations. To do this, the best place for us to start is with SNMP OIDs.
An SNMP OID is an object identifier, which is essentially just a string of numbers. Each of these numbers represents a different value, and SNMP uses these to quickly generate relevant information about the data that it receives in this format.
The below table demonstrates how the different OID numbers represent different values, such as names and descriptions of the devices that they are communicating with.
|
OID Number |
Name |
Description |
|
1 |
ISO |
ISO is the body that helped to establish the standard known as OID |
|
3 |
ORG |
This indicates that an organization will be identified next |
|
6 |
DoD |
The United States Department of Defense |
|
1 |
Internet |
This means that the communication method will occur over the internet or a network |
|
4 |
Private |
This means that the device was created by a nongovernmental organization |
|
1 |
Enterprise |
The device manufacturer has been designated an enterprise status |
There is a lot more to SNMP that we can discuss in greater detail, especially when we need to look at how each component interacts with one another during the communication stages.
But First, some Basics
Before we dive right into the way that OIDs and MIBs interact with one another, we should ground ourselves in some basic SNMP concepts first. If you are wondering how to implement it on your network then take a look at this section and we will discuss what the base requirements are.
Before you can start thinking about SNMP, you need to make sure that you have a place to install your SNMP solution. This is generally referred to as a management station, but it can be a simple computer or a virtualized instance of a computer or server.
All this unit does is collect data from the network and feeds it into the software that is installed on it. This software then applies the Network monitoring and alerting rules to the SNMP messages that it receives, which is what automates your monitoring solution. Just how complicated you need this to be is up to you.
Some organizations have specialized software that they need to monitor, with customized alerts and special API calls that need monitoring, while others just need to know when the toner on their printer is low.
SNMP is flexible enough to do either of these things, or both, depending on the nature of your monitoring requirements. Some SNMP solutions give you more management control of your environment, with powerful reporting and statistical capabilities that will keep the decision makers in your organization apprised of all of the happenings within your various systems.
These reports can be simplified into human readable stats for the non-technical executives, or it can have as much technical information as you need. Inventory control and management is especially useful to most organizations and will help you to monitor and track assets as and when they come and go from the network.
You can also track warranties, licenses and serial numbers all from a single SNMP monitoring station, depending on how you have set it up and what you are trying to measure. The level of detail that you are able to gain from each device on your network will depend entirely on the way that each device has been setup.
Some network appliances have very simple agents preloaded in their firmware, so they can share SNMP information straight out of the box if it is enabled. Computers often need an SNMP agent to be running, depending on the level of detail that you want it to transmit to the management station.
This means that you will need to decide what your requirements are ahead of time if you are to effectively implement a monitoring station on your network.
Some Basic Functionality
Let’s take a closer look at what SNMP can do for your network with a quick list of operations that it can perform if configured correctly.
- SNMP can push and pull data to and from devices. So you can do more than just monitor. In some cases, you can perform basic admin tasks via the SNMP agent and perform basic network and administrative operations without having to physically be in front of the device that you are trying to configure.
- Resource Monitoring is another great feature that SNMP brings to the table. You can monitor important stats such as bandwidth monitoring and identify issues such as poor user discipline or infected units that are using excessive data over the network. This all helps to make for a stronger and more secure environment.
- Error report generation and collection helps to not only keep track of issues, but it very helpful when responding to incidents and for tracking key network metrics within an organization. This can help with trend analysis and even troubleshooting.
- Computer health items such as CPU usage, hard disk space, memory thresholds and much more are quickly and easily monitored from here as well.
- Alerting can be done in almost any way imaginable, from email to text messaging, or even automated phone calls and paging if you have the correct systems in place. You can reach all the correct teams without disturbing teams that are not needed.
- Uptime and status monitoring is also achievable thanks to SNMP. If a host or connection fails, then you will know about it immediately.
- Error alerting is done passively, so you don’t need to do anything when a device fails. Simply monitor your SNMP solution and watch for red flags when a device fails.
Now that we have a rough idea of what SNMP is able to do, we can look at some of the more technical aspects of how it does what it does, thanks in part to OIDs and MIBs.
If you have never heard of those terms before then read on and we will find out what they do and why they are needed for SNMP to operate correctly.
OIDs and MIBs Explained in More Detail
These are arguably some of the most important components of the SNMP system. They are Object Identifiers and Management Information Bases. (OID and MIB respectively) SNMP operates by using objects in the way it interacts over the network.
An object can be anything that contains information relating to a network component or device. This means that a simple OID could be something that measures availability.
The device can be either offline or online and depending on its state it will pass the appropriate value to the SNMP agent. This will then be sent to the management station which will then take further action from there.
OIDs are very ordered and they follow a set scheme. You can think of this as being hierarchical and similar to a tree span that you would find in your operating systems filesystem. Each of these levels of the hierarchy are numbered, as we saw in our above table.
Your SNMP manager will allow you to look at the OID tree span so that you can look at how the structure is formatted in your environment. This isn’t something that you would normally need to do, but it can be educational if you want to look at how the SNMP server in your environment is looking at the layout of your network.
MIBs are different, but they are related to OIDs. You can think of an MIB as a translational layer between the management station and all of the different SNMP responses that it receives. SNMP would not be very useful if the data that it was accumulating was not being properly parsed on the management server’s end, so MIB is very important for the SNMP process to operate correctly.
To complicate things further, all SNMP devices generate something called MIB-2. It is a standardized set of objects that are able to be monitored by the management station. You can think of the previously mentioned interface status object that we looked at earlier as being part of this.
In fact, most system objects such as CPU usage and Memory usage are also found in this group. Additionally, manufacturers are able to store customized information within MIBs that can hold other important information such as system temperatures and fan controller stats, such as fan speed.
This is necessary because you generally will not find this kind of information in the MIB-2 groupings, so manufacturers have to do this themselves.
These customized MIB files give your monitoring solution additional information about how to use them, so that it can query the devices and pull that data in a readable format that allows it to display the information correctly.
Manufacturers therefore need to show their customized object information under a different part of the OID tree found within the MIB-2.
What about Community Strings?
Don’t worry, we haven’t forgotten about community strings! These are a very important part of SNMP and they allow it to work in a much more secure manner. You can think of community strings as something very similar to a password because they limit access only to authorized processes and queries.
It does have some drawbacks though. The defaults are very seldom modified by system admins, which can make your devices a little vulnerable if not configured correctly. There are two ways to setup Community Strings. Either as read only (RO) or read-write (RW).
If the device is set to read only, then no information may be written to the device, although information will be pulled from it. As with any network device, using the read-write option can come with its own set of challenges. Devices are able to be reconfigured and written to if this option is set, so the potential for a bad configuration that knocks the device off the network does exist.
It just means that whoever is administrating the device needs to ensure that they are extra careful when working on it. Another concern is with older versions of SNMP that transmitted strings in plain text.
This means that anyone that intercepted network traffic with a rudimentary packet analyzer could potentially gain access to that device. SNMP 3 is the most secure version of the protocol at present and should be the only version that you use in a production environment with critical systems.
Other Commonly Used Terms
There is a lot more to SMP than meets the eye, so finding out about it is a good idea if you plan on implementing it within your own environment at some point.
If you need to justify a new system to management then it is a good idea for you to understand exactly how your next monitoring system will work, as well as any potential issues that it might cause in your existing environment.
With all of this in mind we need to look at the inner workings of how the protocol interacts with the rest of your environment.
Some general SNMP terminology that you may come across when working with SNMP and monitoring systems are:
- An SNMP Agent:
This is simply a process or more commonly, an application that monitors devices for issues. Once detected it is able to gather information about the problem and it then sends these alerts to a monitoring station which then shows the operator what is going wrong on the network or system. - Available Community Strings:
These are muchlike passwords, but not quite. We went over this and found out about what they do, and how they are sometimes misconfigured on a network. - Get:
When a get request is sent, SNMP sends a get request which is then forwarded to the device it is monitoringso that it is able to retrieve specific information relating to the issue. - Getnext:
Agetnext command is what SNMP uses to get the next message in a sequence – similar to the way a table is structured. - Informs:
These are similar toTraps, but instead they are sent by the agent. This is sent with a request for the management station to confirm receipt so that it can confirm that the transmission was successful. This is only implemented andsupported from v2 and up. - Management Station:
This is the management software that captures the SNMP messages and then feeds them into the alerting and reporting parts of the software on your management computer or server. - MIB:
Management Information Base can be thought of as a codebook for SNMP that helps to define certain parameters within the SNMP messages. - MIB Browser (or MIB Walker):
A tool that can pull data from SNMP enabled devices, helping to identify which objects respond to a query. - Notification:
You can think of this much in the same way as you would think about a “Trap”. Version 2c and abovecall these Notifications when they want to refer to a Trap. - OID:
Object Identifiers are strings of numbers that give the management software all of the information that they need to identify what class of device it is and other important characteristics. - Object:
Items such as CPU and memory alerts, hard drive space and anything else that a system needs to have monitoring. - Polling:
Management systems need to communicate regularly so that they can get messages about important system events. - Set:
This is how devices are setup and configured via the management station. You can set parameters and other important configs through this element. - Trap:
A trap is an unexpected message that is sent straight from the alerting element on the network. Traps are how SNMP is able to manage and handle important system events. - Variable:
Variables are the differential scales of system tolerances like CPU usage and available memory. - Version 1:
Was the first, or original version of SNMP. It still had community strings sent in plain text so it could be intercepted very easily, meaning that it has very weak security. - Version 2c:
SNMP v2c fixed a lot of issues that were discovered in the original v1 of the SNMP suite. There were actually many different versions released in this era of SNMP, although none of them did a particularly good job of actually addressing any of the problems that were discovered in v1. V2c is one of the most common iterations of SNMP, because has great features such as enhanced protocol handling. This is a better solution over v1, which results in slightly improved performance and stability, but it doesn’t really address the security problems that we saw in the protocol. However, security is still an issue because it uses plain-text community strings. - Version 3:
Is the newest version of SNMP and is seen as the only truly secure version of the protocol. We find that in v3 SNMP supports better safety features such as full security and authentication for secure communications across your network and the internet. It is a much easier way too manage your network.
As we can see, there is plenty of different elements that make up the SNMP, so being familiar with each of them is a good idea if you want to implement this technology in your workplace.
Understanding the individual components is also a requirement if you are going to open up all the necessary ports for successful network communications for your monitoring solution.
Conclusion
Finding the right monitoring solution for your organization is critical if you plan on catching issues before they become a big problem. SNMP OID information is one of the methods that is used to help identify elements on the network, and as we have seen, it is essential to the way the SNMP operates.
There are many reasons that you might want to have SNMP installed, it could be for monitoring CPU and memory usage on all of your production servers, or you could be using it to help with hardware discovery on your network. There are many different versions of SNMP as well, but the most secure is seen to be version 3.
Earlier versions, as we discovered, showed off important information as plain text over the network. This means that it could be easily read and looked at by anyone that is on the network. This is not the best practice if you value security on your network so version 3 of SNMP.
SNMP OID Versions Functionality FAQs
What is SNMP OID?
SNMP OID (Object Identifier) is a unique identifier that is used to represent a managed object in a network management system that uses the Simple Network Management Protocol (SNMP).
What types of information can be obtained with SNMP OIDs?
SNMP OIDs can provide a wide range of information about network devices and resources, including device uptime, CPU and memory usage, interface status, and bandwidth utilization.
What are some common use cases for SNMP OIDs?
Common use cases for SNMP OIDs include network monitoring, performance analysis, and capacity planning.
How do I use SNMP OIDs to obtain information about network devices and resources?
To use SNMP OIDs to obtain information about network devices and resources, you can query the SNMP agent on the device using an SNMP management tool, such as an SNMP monitoring tool or a command-line SNMP client.
What types of SNMP OIDs are available?
There are a wide range of SNMP OIDs available, including standard OIDs defined by the Internet Engineering Task Force (IETF), as well as vendor-specific OIDs defined by individual vendors.
What types of data can be returned by an SNMP OID query?
An SNMP OID query can return a range of data types, including integers, strings, and IP addresses.
What are some best practices for using SNMP OIDs?
Some best practices for using SNMP OIDs include identifying the critical data to be monitored, configuring appropriate SNMP settings, and securing SNMP communications to prevent unauthorized access.