The growing work-from-anywhere culture has created a need for remote access to computer systems. For example, employees working from different parts of the world need access to the organization's resources for their work. However, this remote access also comes with inherent security risks. In particular, Remote Access Trojans (RATs) pose a significant threat to the confidentiality, integrity, and availability of an organization's sensitive data and resources. To protect against these malicious tools, organizations require effective RAT scanners and detection tools.
Here is our list of the best Remote Access Trojan Software:
- ManageEngine Malware Protection Plus – EDITOR'S CHOICE A next-gen antivirus tool that uses AI techniques to safeguard your devices from threats like Trojan software. Start a 30-day free trial.
- SolarWinds Security Event Manager An advanced SIEM tool that automatically scans, detects, and reports malicious activity on your device.
- Suricata An open-source engine that acts as both an Intrusion Detection and an Intrusion Prevention system to identify and mitigate threats.
- OSSEC Another open-source and multi-platform Host Intrusion Detection System (HIDS) for customized security.
- Snort An open-source Intrusion Prevention System (IPS) that uses a set of rules to define malicious network activities.
- Zeek A flexible and open-source network security monitoring platform to analyze your traffic patterns.
- Sagan A multithreaded log analysis and correlation engine that provides in-depth insights into potential threats.
Read on, as we delve into the world of RATs, explore their potential dangers, and provide a comprehensive list of the best tools available to safeguard against them.
What is a RAT?
A Remote Access Trojan (RAT) is a type of malware that allows unauthorized users to gain remote control over a compromised system or network. RATs use social engineering techniques like phishing and ransomware to compromise devices and access them. When employees unknowingly open email attachments, download software, or open malicious links, the RAT gets installed in the device. Once installed, a RAT provides attackers with full control over the infected system, enabling them to perform various nefarious activities, including spying, data theft, system manipulation, and launching additional attacks.
As an organization, the best way to counter these RAT software is through proactive scanning and detection.
Why Do Organizations Need RAT Scanners and Detection Tools?
Given the rising sophistication of RATs and their potential to wreak havoc on organizational networks, you must deploy effective scanners and detection tools. Besides protecting your devices, here are more reasons to invest in a RAT scanner and detection tool.
- Threat Identification RAT scanners and detection tools are designed to identify and detect the presence of RATs within an organization's network. These tools use advanced algorithms to analyze network traffic, system processes, and file behavior, to detect RAT activity at the earliest.
- Security Incident Response These RAT detection tools enable organizations to quickly respond to and mitigate potential breaches. Most of them come with real-time alerts and notifications to help security teams identify compromised systems, block malicious activities, and isolate infected machines to prevent their further spread.
- Compliance and Regulatory Requirements Many industries, like finance, healthcare, and government, have strict compliance regulations for the protection of sensitive data. RAT scanners provide proactive measures and real-time data to help organizations meet these requirements. Additionally, such information also protects your data and systems from potential breaches.
Undoubtedly, RAT tools can go a long way in securing your organization's resources, leading to improved trust and brand image.
Let's now look at some of the best RAT detection and scanner tools available in the market today.
The Best Remote Access Trojan Detection Software
Let's take a brief look into each of the best remote access trojan detection tools to understand their ability to scan, detect, and alert you of RAT presence.
1. ManageEngine Malware Protection Plus – FREE TRIAL
ManageEngine Malware Protection Plus is designed to meet the evolving nature of cybersecurity threats like the Remote Access Trojan software. It uses behavioral analysis and machine learning to quickly detect this malware before it causes widespread damage to your infrastructure.
Key Features:
Below are the key features of this tool.
- Memory scanning: It scans the memory to identify fileless malware that is often overlooked by traditional antivirus tools.
- Anti-exploitation techniques: It uses memory hardening and other anti-exploitation techniques to prevent hackers from exploiting known vulnerabilities.
- Real-time containment: This tool isolates infected devices in real time to prevent the malware from laterally spreading across your infrastructure.
- Forensic analysis: Performs in-depth forensic analysis to identify the root cause of incidents.
In all, ManageEngine Malware Protection Plus is an advanced antivirus that offers complete protection against many types of malware and ransomware, including RAT. Its remediation and recovery features also come in handy for handling these threats.
The annual licensing starts at $745 for 50 workstations, while the perpetual licensing is priced at $1,863 for 50 workstations. Start a 30-day free trial.
EDITOR'S CHOICE
ManageEngine malware Protection Plus is our top choice for protecting your devices against RAT attacks because of its advanced scanning and remediation techniques. In particular, it uses memory scanning and behavioral analysis to identify this malware quickly. Also, its automated remediation techniques make sure the infection is contained. It also connects to backup devices to restore infected files and registries to their pre-attack state.
Download: Start a 30-day FREE Trial
Official Site: https://www.manageengine.com/malware-protection/
OS: Windows
2. SolarWinds Security Event Manager

Security Event Manager from SolarWinds is an advanced Security Information and Event Management (SIEM) tool that improves the security of your devices while enabling your organization to meet compliance requirements.
Key Features:
- Identifies Threats Faster: Security Event Manager monitors your devices and networks continuously to identify even the smallest behavioral changes and traffic patterns. Accordingly, this tool will perform the necessary actions in real-time to bring down the impact of this change.
- Eases Compliance: This SIEM tool comes with templates and reports for the most well-known standards like HIPAA and SOX. You can leverage these tools to assess the state of your compliance and to generate the necessary reports that demonstrate your compliance with these standards.
- Provides Contextual Information: SolarWinds Security Event Manager has many pre-built connectors that gather data from various sources, parses them, and puts them into a readable format. As a result, you have the contextual information to quickly analyze threats and fix their root cause.
Overall, this SolarWinds tool provides value for your organization, as you can mitigate threats immediately and maintain the security posture of your organization.
SolarWinds Security Event Manager pricing starts at $2,877. You can schedule a demo and try the tool on a 30-day free trial. For an accurate quote, click here.
3. Suricata

Suricata is an open-source network analysis that works well as an intrusion detection and prevention system. This tool uses a rule set and signature language to identify existing and emerging threats. It also runs well on Windows, Mac, Unix, and Linux devices.
Key Features:
- Advanced Detection Engine: The heart of Suricata is its advanced detection engine that can identify malicious behavior and take action on them. This engine works well for intrusion detection, intrusion prevention, and network security monitoring. It even records traffic through the PCAP logger while supporting the offline analysis of PCAP files.
- Alerts and Notifications: This tool enables you to set rules and filters for alerts. You can even set the global and subnet thresholds to ensure that you get only the relevant notifications and at the same time, reduce false alerts. You can also use these filters to match DNS, URI, and other fields.
- Multi-Platform Support: Suricata is highly versatile and works well across multiple operating systems. In particular, it has a specialized Unix socket for automating PCAP file processing and also, integrates well with Linux Netfilter firewalling.
In all, Suricata is a highly flexible and versatile tool that enables you to customize your security and alerting.
Suricata is 100% free to use. You can download it directly.
4. OSSEC
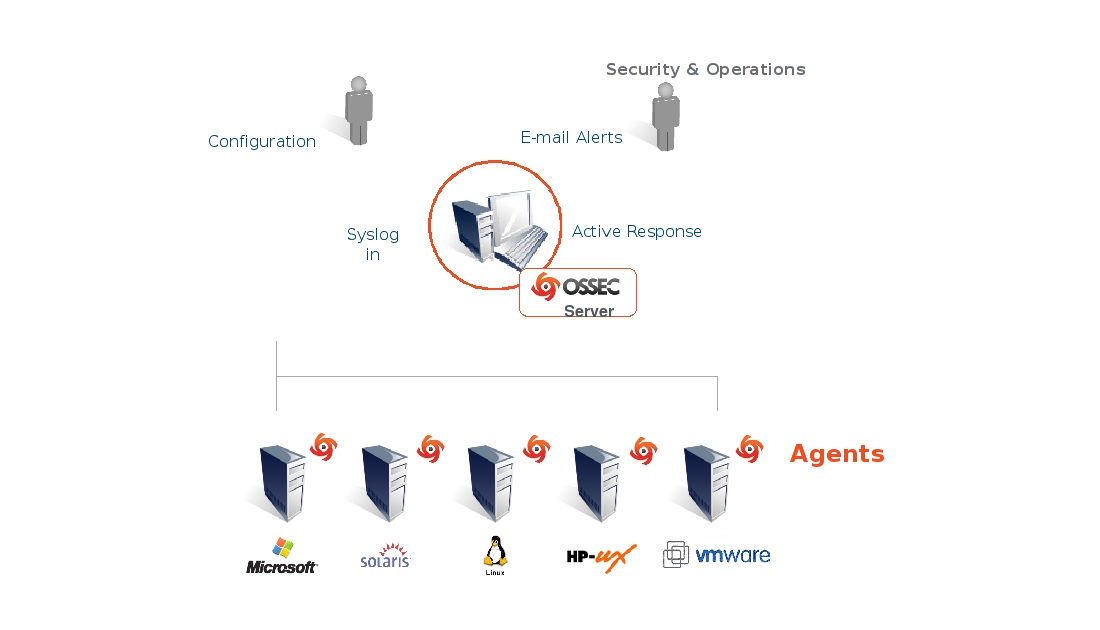
OSSEC is a popular platform for monitoring your devices and controlling the overall network activities. It combines HIDS, log monitoring, and SIEM to offer powerful capabilities to meet your organization's security needs.
Key Features:
- Server Intrusion Detection: OSSEC is an open-source platform that works well on different operating systems including Linux, Solaris, Unix, Mac, Windows, BSD, and more. Additionally, it offers many configurations for server intrusion detection, and you can even add custom rules for alerts and notifications. It also supports the use of scripts that enable the platform to perform specific actions when certain events occur.
- Compliance: With OSSEC, you can easily meet the stringent requirements of standards like NIST and PCI DSS. Besides compliance, this platform continuously monitors your devices to detect any changes and malicious behavior that can lead to non-compliance.
- Advanced Features: Atomic OSSEC, built on the open source, is a paid tool that comes with many advanced features like real-time FIM, software integrations, built-in response for specific events, GUI, compliance monitoring, and more. It also offers comprehensive customer support to ensure that you take advantage of changes.
In all, OSSEC is an open-source platform that you can customize or opt for the Atomic OSSEC for improved intrusion detection and compliance.
You can get a quote for Atomic OSSEC. Start a 14-day free trial, watch a demo, or download the open-source OSSEC platform.
5. Snort
Snort is an open-source Intrusion Prevention System (IPS) that monitors all the traffic that goes in and out of your system in real-time. Accordingly, it sends alerts when it discovers any malicious packet.
Key Features:
- Wide Protection: Snort's flexible rules make it easy for network administrators to identify and prevent a wide range of attacks like the Denial of Service (DoS) and the Distributed Denial of Service (DDoS) attacks. Essentially, Snort enables you to create a series of rules to identify malicious activity and packets, and send alerts to you. With such a mechanism, you can also thwart CGI attacks, buffer overflows, and stealth port scans.
- Real-Time Monitoring: Snort monitors every packet that enters and leaves your network, and this is how it easily identifies and blocks malicious packets from entering your network. Additionally, it also sends alerts, so you can identify the cause and blacklist the sender's device or IP address. Since all this happens in real-time, you can stop attacks before they impact your device.
- Logging and Analysis: The packet logger mode of Snort logs packets to the disk, so you can analyze them when needed. The logging process happens in a hierarchical directory based on the host network's IP address, and this is why it's easy to find malicious packets.
In all, Snort is a highly effective tool for blocking malicious packets and analyzing them to prevent future attacks.
Snort offers three editions: Personal at $29.99 for each rule, Business at $399 per sensor, and Integrators with a custom quote.
6. Zeek

Zeek is a network analysis framework that analyzes high-level semantics at the application level. This flexible and open-source tool observes network traffic and interprets them to create high-fidelity logs for further analysis.
Key Features:
- Detection and Response Workflow: A highlight of Zeek is that it logs both transaction and extracted content data and summarizes protocols. Such extensive logging makes it easy to analyze and detect the root cause of the problem, so that can be addressed at the earliest. Based on the detection, Zeek also allows you to integrate with tools like Suricata to create an appropriate response workflow.
- Live Network Traffic: Zeek monitors live network traffic and sends alerts in real-time. The obvious advantage is that you can catch anomalies and address them before they impact the wider network. Also, it can monitor network interfaces and extract file content to generate relevant insights.
- Specialized Monitoring: Zeek offers many specialized processing tools that enable you to analyze data in many formats. It even ships with specialized storage and review platforms, some of which are available as open source as well.
In all, Zeek is a handy tool for monitoring packets, analyzing them, and taking corrective actions. Zeek is free to use.
7. Sagan
Sagan is a log analysis engine that correlates logs from different sources and in different formats and analyzes them to provide invaluable insights for you. The entire log collection and analysis happens in real-time, so you can fix the issues before they impact the wider network.
Key Features:
- Lightweight and High Performing: A key advantage of Sagan is that it's lightweight and this means, it's going to use minimal CPU and memory resources. At the same time, its multithreaded architecture makes it conducive to leveraging the available CPU and cores for real-time log analysis.
- Rules-based Approach: Like Snort and Suricata, Sagan also takes a rules-based approach to analysis. You can create rules and thresholds for alerts, to reduce false positives and get notifications on the most pressing incidents. These rules can be stored in JSON or unified2 binary data format for easy analysis and management. You can also export rules from other SIEM platforms using Syslog.
- Advanced Insights: With Sagan, you can get advanced insights into the security of your devices and the network at large. Its client tracking feature informs you when machines start or stop logging, and this helps to verify if you're getting the data you want from a device. Plus, Sagan uses “xbits” to correlate data from different for easy tracking. It uses Redis to share data between different Sagan instances within a network.
All these features come together to provide a unified view of the state of your environment, so you can take the necessary action accordingly.
Sagan is free to use; download it here.
Final Thoughts
In today's work-from-anywhere culture, Remote Access Trojans (RATs) can compromise the security of sensitive data and resources. To mitigate these risks, organizations require effective RAT scanners and detection tools to identify malicious programs and threats. These tools use advanced algorithms to analyze network traffic, system processes, and file behavior, and accordingly, detect RAT activity. They also facilitate security incident response by providing real-time alerts and notifications, allowing security teams to quickly identify compromised systems and mitigate potential breaches. Additionally, RAT scanners help organizations meet compliance and regulatory requirements, ensuring the protection of sensitive data and systems.
In this article, we explored the best RAT detection software, including SolarWinds Security Event Manager, Suricata, OSSEC, Snort, Zeek, and Sagan. Each tool offers unique capabilities to scan, detect, and alert RAT presence. Whether it's SolarWinds Security Event Manager's advanced SIEM capabilities, Suricata's flexible network analysis engine, OSSEC's comprehensive monitoring and compliance features, Snort's real-time traffic monitoring and packet analysis, Zeek's high-level semantics analysis, or Sagan's log correlation and real-time analysis, these tools provide the means to effectively protect your devices against RATs.