Protecting your organization's and customers' sensitive data has become more imperative today than ever before. The increasing number of regulations and laws surrounding data privacy coupled with the growing ability of cybercriminals to perform data breaches and thefts have made data protection a critical and challenging activity today. Almost every organization has formulated policies to protect data, regardless of where it is stored and how it is used.
All organizational policies related to data privacy consider the three states of data:
- Data in Use When the data is used actively within an application or by users.
- Data in Transit When the data is transferred or shared within and outside the network, typically to third-party service providers.
- Data at Rest When the data is stored in a hard drive or any other storage device.
In this article, we'll focus on protecting the data at rest. Read on to learn some tips and tricks for protecting your data while it's at rest and a bunch of tools that can come in handy.
Here is our list of the best tools to protect data at rest:
- ManageEngine Device Control Plus – EDITOR'S CHOICE Exceptional in protecting data at rest with its zero-trust model and smart auditing capabilities.
- CoSoSys Endpoint Protector Advanced DLP with content-aware protection and automatic USB encryption.
- Forcepoint DLP Offers comprehensive data leak prevention, high-risk incident analytics.
- Digital Guardian DLP SaaS-based, supports scalability, advanced monitoring tools for data protection.
Why Focus on Protecting Data at Rest
Now, you may wonder why we're talking specifically about protecting data at rest. That's because this state of data is the most vulnerable when compared to others, and here's why.
- Insider Attacks Insider attacks are a real threat to the data that's stored in a hard drive. Typically, employees who are disgruntled with the organization and want to take revenge steal this data and sell it to competitors. Sometimes, employees also do it for money or other gains. These insider threats are hard to detect and prevent because they are done by people who are authorized to access this data. It requires extensive checking of logs and the implementation of other security measures such as port locking, and more.
- Prized Possession The data that's stored in your hard drive is considered a prized possession by cybercriminals because they get access to large amounts of data in one go. This is probably why most data breaches that have happened so far relate to data at rest. Needless to say, such data breaches lead to a loss of revenue and reputation, and it can take considerable time and effort to overcome these implications.
- Easy to Steal When the data is at rest, it's easier to steal when compared to data in other states. This is because employees tend to be careless, so it's relatively easy to look for a compromised password or open access. Further, there are many ways to access this data, such as, through USB flash drives, unsecured endpoints, including the personal devices of employees, and more.
Due to the above reasons, data is more likely to be stolen when it's stored, and this is why you must take additional steps and precautions to secure it.
Let's now see some strategies to protect the data at rest.
Six Tips and Tricks to Protect Data at Rest
Here are some strategies that can come in handy to protect data at rest.
1. Build Lists
A good starting point is to build lists of trusted devices and users. Trusted devices are those that are connected to your network and are verified by your IT department. These devices also contain the necessary protection such as antivirus software and firewalls that act as the first line of defense against an attack. Moreover, the IT admins know who uses these devices and what's accessed through them.
Such devices reduce the chances of an insider attack because of the transparency and visibility it provides to the IT admins. Also, this is an easy way to ensure that the users access only authorized content/applications.
2. Classify Data
Along with building lists, make sure to also classify data, so you can isolate the most sensitive records and provide extra security for them.
From an organization's standpoint, protecting every single piece of information is difficult because it entails considerable resources. Moreover, not all data needs to be protected. This is why it's a good idea to classify data and identify the most sensitive ones so you can spend resources to protect them.
Remember, this classification is dynamic, so you'll have to visit your classification strategy periodically to make changes when needed.
3. Streamline Access
Ensure that your IT admin has granular control over the access of every piece of data on your storage. Also, this access should be visible to the security team at any time. Such fine control reduces unauthorized access to resources and through it, reduces the chances of insider attacks.
4. Encrypt Data at Rest
Encryption tools encrypt your data and ensure that it is meaningless, even if someone manages to steal it. Windows BitLocker and FileVault in macOS come with the corresponding operating system and they encrypt the entire hard drive of users, thereby making it worthless for anyone other than the user. While this may not be effective against insider attacks, it protects your data from external cybercriminals.
An important part of encryption is to manage the encryption keys, so they're not stolen or lost.
5. Conduct Security Audits
Security audits are an essential but often overlooked strategy. These security audits can provide insights into the gaps and vulnerabilities within your network, so you can take steps to address them. Further, these audits assess whether your existing security policies protect your organization, and based on these findings, you can make the necessary changes.
6. Third-Party Tools
Consider using third-party monitoring tools that come with a slew of features to address every aspect of data protection. These tools streamline access, generate reports, provide insights into user behavior, auto-discover devices on your network, and more.
There are many third-party monitoring tools available today, and this can make it overwhelming for you to pick the one that best suits your needs. We have identified a few such tools with wide-arching capabilities that cater well to almost every organization.
Our methodology for selecting data at rest protection tools:
We've broken down our analysis for you based on these key criteria:
- The effectiveness of the tool in protecting data at rest.
- The ability to integrate with existing systems and manage user access.
- Advanced reporting and auditing capabilities.
- Use of innovative technologies like AI and machine learning for enhanced security.
- The tool's flexibility and scalability to adapt to organizational changes.
The Best Tools to Protect Data at Rest
We have come up with a list of popular tools that protect your data at rest. Here's a brief description and a concise list of the capabilities of each of these tools.
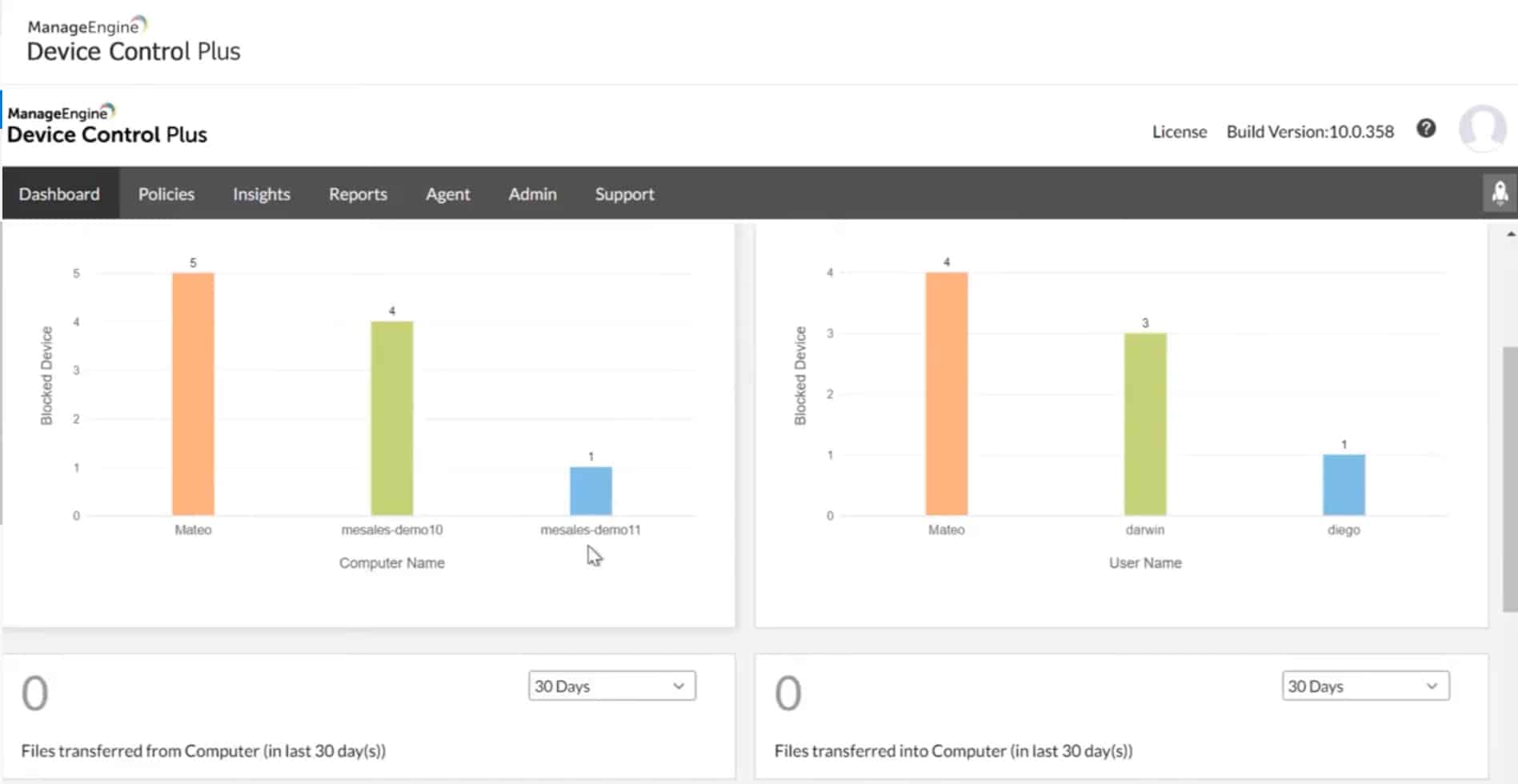
1. ManageEngine Device Control Plus – FREE TRIAL
Device Control Plus from ManageEngine is a flexible and versatile tool that comes with many features to protect your data at rest. Its zero trust-centric model ensures that it treats every device and user with caution until the device/user displays authorization proof. Such an approach can greatly reduce the chances of unauthorized access to sensitive information, and through it, reduces insider attacks. Further, it also protects against external attacks that emanate from unknown devices. Its smart auditing and reporting capabilities also enhance its value to your business.
Key Features:
- Zero trust-centric model
- Smart auditing and reporting
- Protects against external attacks
Why do we recommend it?
ManageEngine Device Control Plus is recommended for its strong zero-trust approach, significantly reducing unauthorized access and insider threats while offering comprehensive auditing and reporting capabilities.
Who is it recommended for?
Ideal for organizations seeking a robust solution to protect sensitive data from both internal and external threats, particularly those needing detailed auditing and reporting.
Pros:
- Effective zero-trust model for security.
- Advanced auditing and reporting features.
- Protection against internal and external threats.
Cons:
- Might require a learning curve for new users.
EDITOR'S CHOICE
ManageEngine Device Control Plus stands out as our Editor's Choice for its comprehensive approach to protecting data at rest. Its zero-trust-centric model is particularly effective in minimizing unauthorized access and insider attacks. The tool's strength lies in its capacity to monitor and control device access meticulously, thereby safeguarding sensitive information against both internal and external threats.
Its robust auditing and reporting features add another layer of security, offering valuable insights into device and user activities. These capabilities, combined with its ease of deployment and compatibility with various systems, make ManageEngine Device Control Plus an excellent choice for organizations aiming to strengthen their data protection strategies.
Download: Download a 30-Day Free Trial
Official Site: https://www.manageengine.com/device-control/data-at-rest.html
OS: Compatible with multiple operating systems; Cloud-based options available
2. CoSoSys Endpoint Protector
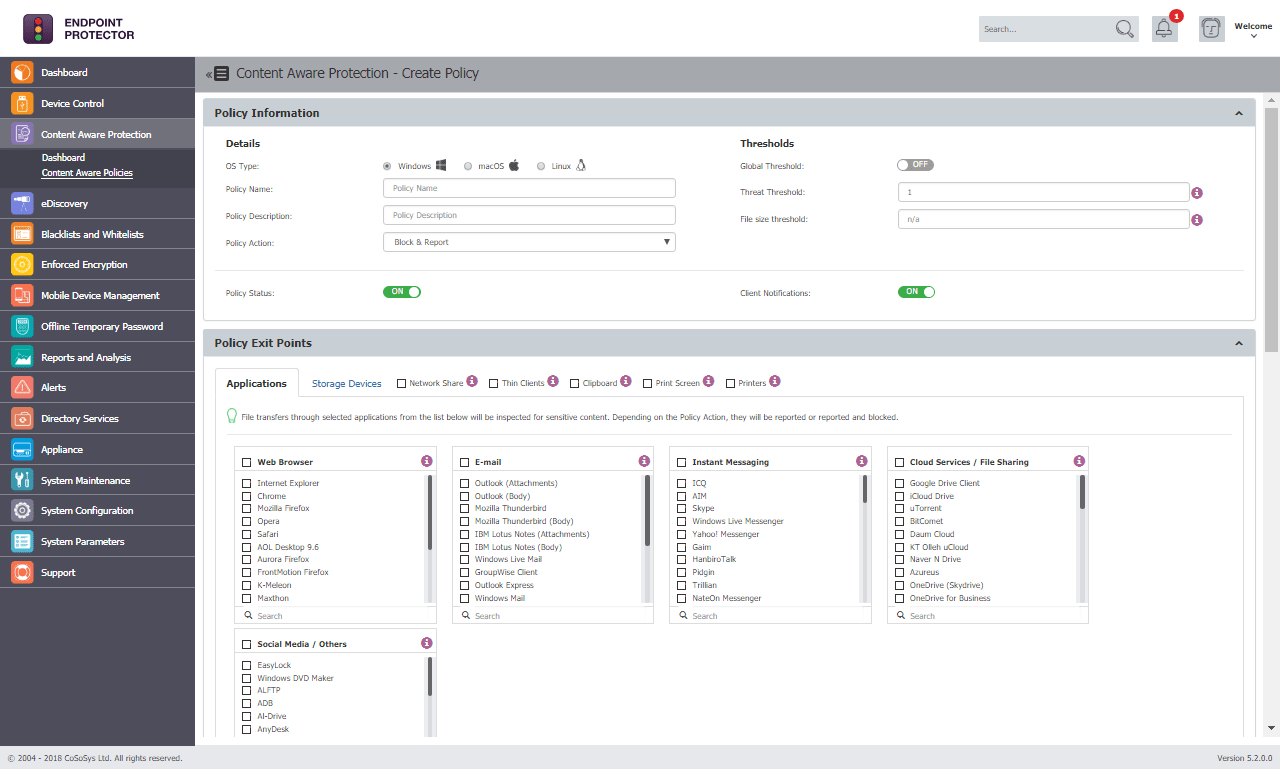
Endpoint Protector from CoSoSys is an advanced Data Loss Prevention (DLP) software that protects your computer from possible data theft and loss. It comes with extensive features that detect, monitor and protect your sensitive data by streamlining access across user endpoints. Further, it gives complete control over USBs and peripheral ports to reduce the chances of insider thefts.
Key Features:
- Advanced DLP software
- Content-aware protection
- Automatic USB encryption
Why do we recommend it?
CoSoSys Endpoint Protector is recommended for its advanced DLP capabilities, particularly its content-aware protection that utilizes AI and ML to identify and secure sensitive data.
A unique feature of this tool is its content-aware protection that scans your data and uses advanced machine learning and AI to identify sensitive data, so an additional layer of protection can be given to it. All of these actions happen automatically with CO So Sys' Endpoint Protector.
Automatic USB encryption, extensive report generation, and ease of deployment are some of the other salient aspects of this tool.
Who is it recommended for?
Best suited for businesses needing extensive control over data access and protection, especially those concerned with preventing insider data theft.
Pros:
- Comprehensive DLP features.
- Content-aware protection with AI/ML.
- Controls over USBs and peripheral ports.
Cons:
- Can be complex to fully configure.
3. Forcepoint DLP
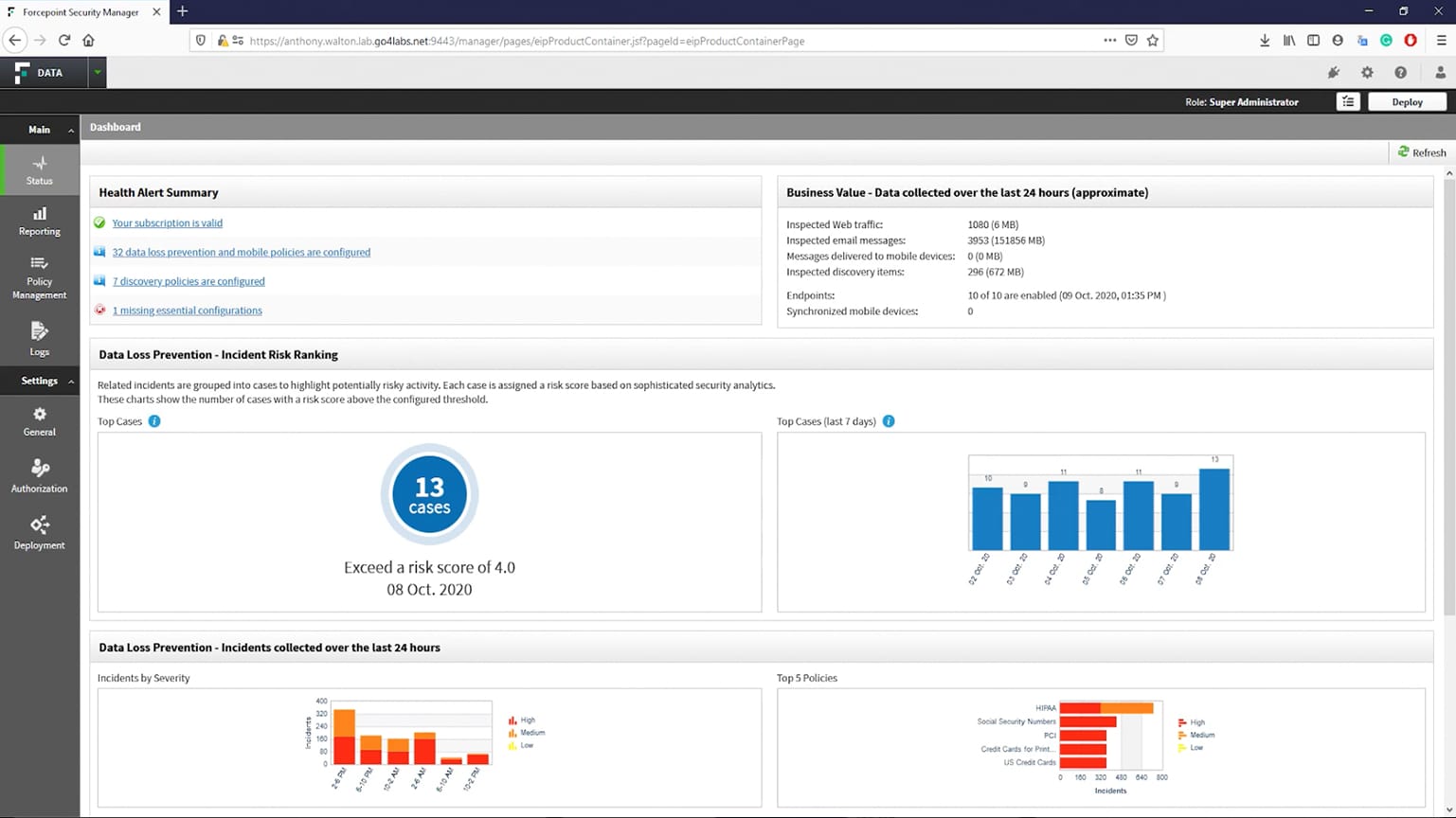
Forcepoint DLP is a comprehensive platform for protecting data leaks and loss from an organization. It uses a combination of features to prevent data loss through email, FTP, and HTTP(S). With Forcepoint, you can also lock your USB and peripheral devices to prevent employees from stealing your data.
Key Features:
- Data loss prevention
- High-risk incident analytics
- Peripheral device locking
Why do we recommend it?
Forcepoint DLP is recommended for its holistic approach to preventing data loss, including email and peripheral control, coupled with an analytics engine that identifies high-risk vulnerabilities.
A unique feature of this platform is its analytics engine that quickly identifies and even ranks high-risk vulnerabilities and incidents. This will help you to fix the root cause and mitigate its impact at the earliest. Further, this tool also stays on top of the location of your sensitive data, and hence, can track who accessed it and when. All these together can offer an extra security layer for your sensitive data.
Who is it recommended for?
Ideal for organizations that need a comprehensive solution for protecting against data leaks, including email, FTP, and HTTP(S) security.
Pros:
- Comprehensive data loss prevention.
- Analyzes and ranks high-risk incidents.
- Peripheral control to prevent data theft.
Cons:
- May require advanced user knowledge.
4. Digital Guardian DLP
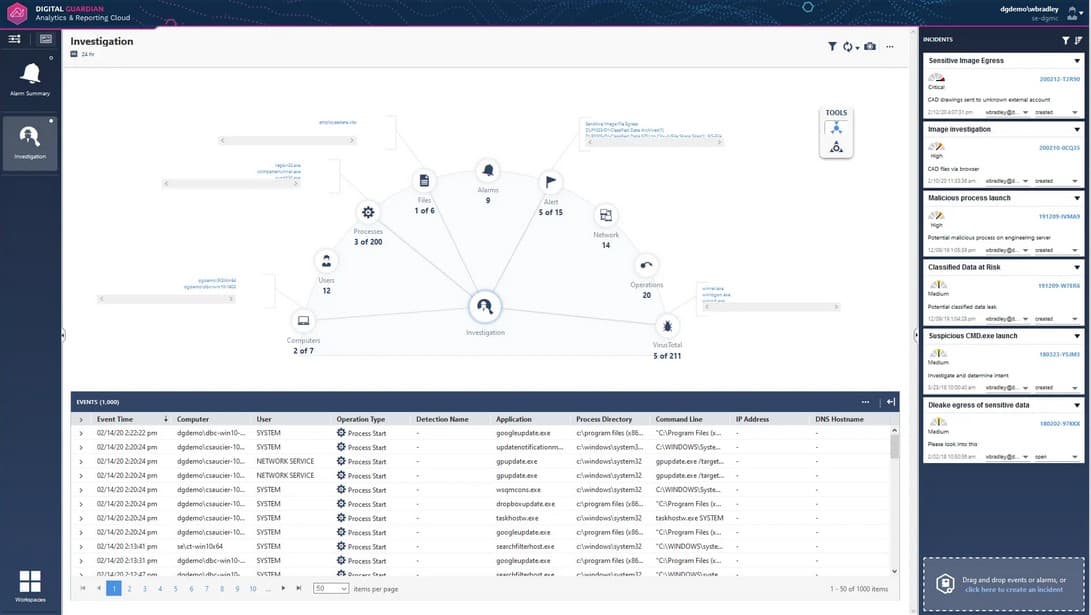
Digital Guardian DLP is a SaaS solution that supports on-demand scalability and fast deployment. As it is powered by AWS, there's little overhead and maintenance for you and at the same time, it's flexible to meet your changing demands. It also works well across many applications and operating systems such as Windows, macOS, and Linux.
Key Features:
- SaaS solution
- On-demand scalability
- Advanced monitoring tools
Why do we recommend it?
Digital Guardian DLP is recommended for its cloud-based, scalable approach, offering advanced tools for monitoring and protecting sensitive data, suitable for diverse IT environments.
This platform comes with many advanced tools such as log monitoring, automated blocking, and more that provide fine-grained control to protect your data from unauthorized access. At the same time, it also provides in-depth visibility into your sensitive data, so you know its state and use at all times. Its detailed data classification policies also add to its appeal.
Thus, these are some good tools for protecting your data at rest.
Who is it recommended for?
This platform is particularly beneficial for organizations looking for a flexible, scalable data protection solution with minimal overhead.
Pros:
- Scalable SaaS solution.
- Minimal overhead and maintenance.
- Advanced data protection tools.
Cons:
- May not suit all budget sizes.
Conclusion
To summarize, protecting your data is essential from a legal, regulatory, and business standpoint, as a loss can have serious financial ramifications for your business. The strategies you use and monitor depend to a large extent on the state of the data, which can be data in transit, data at rest, and data in use. Out of the three, data at rest is the most vulnerable as it can be accessed by both internal and external malicious actors. Further, many loose ends can provide access to this data when it's stored in a device. Due to these reasons, we recommended some strategies to better protect your data.
Also, we came up with a bunch of tools that have the capabilities to provide comprehensive protection to your data and prevent it from being misused.
We hope all this information helps you to formulate the appropriate strategies and tools for protecting your data that's stored in a device.