Removable devices are ubiquitous today and used extensively across work environments. But are they safe?
Unfortunately, no, as per the available statistics. A study by the Ponemon Institute shows that 40 percent of the organizations it polled use more than 50,000 USB drives across their environment. Out of this, nearly 20 percent use more than 100,000 USB drives. What's alarming is that the same study estimates that every company loses about 12,000 records on average due to “missing” or lost USB drives. Further, the average cost of each breach is about $214 per record, besides other legal ramifications.
All these numbers point to one aspect – organizations need better control over their flash drives. They must have policies in place to determine who uses them and for what purposes. But this is not easy given the widespread use of these devices and the flexibility they offer for genuine data transfers.
This is where tools like Endpoint Protector help, as it comes with advanced features to control all forms of removable media. Read on as we show you how you can use Endpoint Protector to lock your flash drives to prevent accidental or planned data loss.
What is Endpoint Protector?
Endpoint Protector is a comprehensive Data Loss Prevention (DLP) software that works well on Windows, Linux, and macOS to prevent data loss. It has many advanced features to monitor, lock, and manage endpoint devices and flash drives.
Here's a look at some salient features of Endpoint Protector's device control. With this tool, you can:
- Remotely monitor all USB devices through a single web-based interface.
- Grant USB access remotely, even when computers are offline.
- Access a complete list of log reports at any time.
- Control the use of each device across your network.
- Search or filter based on the type of device, vendor ID, etc. to know which ones are in use.
- Create device whitelists and blacklists.
- Provide role-based access to USB drives.
- Define policies for its use across departments/users/devices.
A mere glance at the above features clearly shows the level of control you can get when you use Endpoint Protector. Next, let's specifically talk about how you can lock flash drives with this tool.
How to Lock Flash Drives with Endpoint Protector?
Before we talk about how you can lock flash drives, let's talk a bit about why you should even lock devices in the first place.
Why Lock Flash Drives?
The biggest reason is accidental or intentional data breaches. For example, an unsuspecting individual may carry sensitive information on a USB drive and can lose it on the way. Likewise, a disgruntled employee could take sensitive information on a drive to sell it to competitors for gain. Though both situations are different, the result is the same, which is data loss.
In today's age of privacy and security, this data loss can have serious consequences for the company. Besides the financial loss, your organization could be faced with legal suits, and you may have to work extensively to rebuild trust and reputation among your customers.
An easier option is to simply lock the flash drives and grant access only when needed to the authorized user. This way, you're always in control of who is accessing data and when, and hence, can be tracked easily.
Why use Endpoint Protector?
While many tools can lock flash drives, Endpoint Protector is considered a good choice because of the above-mentioned features that streamline the access and use of flash drives. In particular, you can have centralized control over all the USB devices and peripheral ports to prevent accidental and intentional data loss through flash drives.
Moving on, let's look at how you can lock these flash drives.
Locking Flash Drives with Endpoint Protector
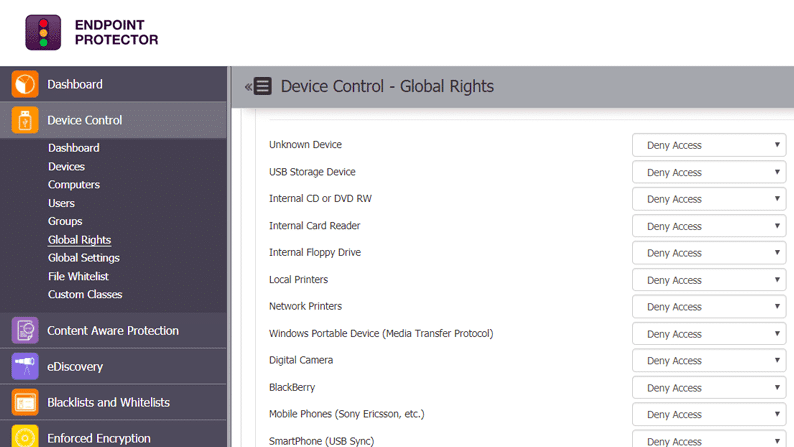
As soon as you open Endpoint Protector, it'll scan your network to identify the broad categories of flash and removable storage devices on your network. This could include USB drives, internal CD/DVD, Bluetooth, Wi-Fi devices, printers, and more.
All that you have to do is to click the drop-down box against each of these devices. The drop-down box will contain options such as deny access/allow access, and you can choose the one you want.
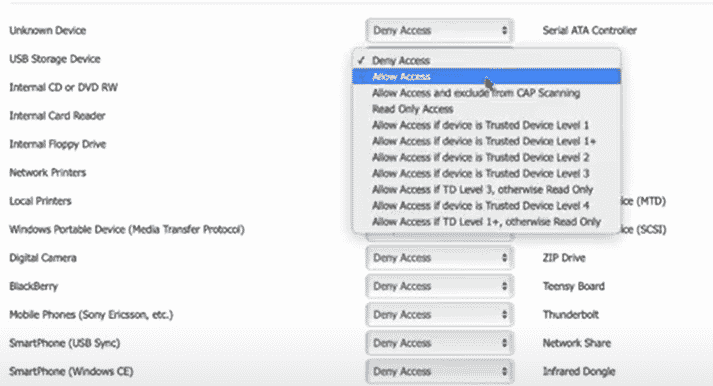
As you can see from the above image, you can also allow limited access, based on the trust tier of each device.
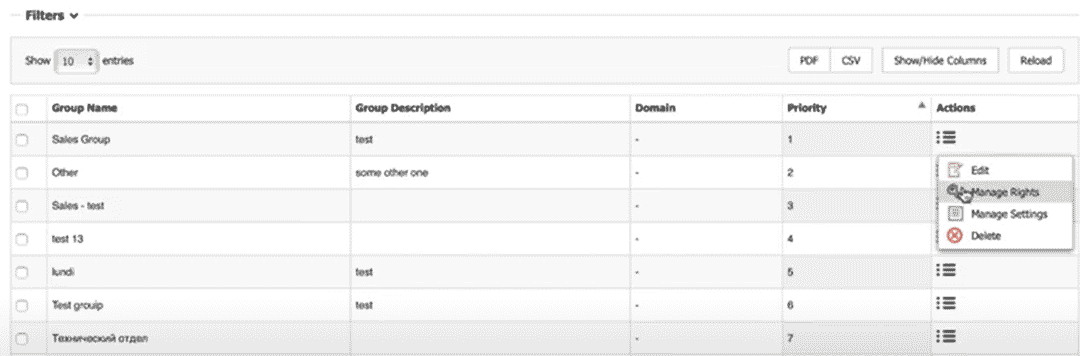
Similarly, you can provide access to USB drives based on users, departments, and roles. You can even choose to have the same option for all users or have a different level of access for different groups/departments.
To do this, simply navigate to the “Groups” option on your left-hand pane and choose from one of the drop-down options against each group.
If you choose to give the same access to all users, navigate to “Global Rights” on the left-hand pane and choose the level of access for everyone within your organization.
Follow the same procedure for “Users”, “Computers”, and “Devices”, all of which you can navigate on the left-hand pane. In case of conflicts, note that Global Rights have the lowest priority while Group rights have a higher one. On the other hand, User or Computer rights have the highest priority and will supersede other rights.
This is also a logical flow from a usability standpoint. Let's say, for example, you don't want to give the entire department access to use USB drives, and the only exception is the manager. So, you give “Deny access” to the Group and “Allow access” only to that particular “User.” Due to the priority hierarchy, the manager alone will have access, despite belonging to the same group for which access is denied.
You can also have granular access at the time of access. For example, you can set that they can't be accessed outside office hours or when connecting from outside a corporate network.

Again, these settings can be set for global rights, groups, users, and computers.
Thus, this is how you can use Endpoint Protector to lock flash drives and have granular control over who has access rights. As you can see, the user interface is intuitive and the entire process is seamless and simple. More importantly, you have complete visibility and control over who has access and when.
Such granular control is sure to add an extra layer of protection against insider threats. Besides, you can also generate reports to see the usage levels when needed. This information can help you to set and implement the appropriate organization-wide security policies.
In all, Endpoint Protector is a comprehensive tool to control access to your flash drives.
Before we end, here's a quick recap of all that we learned in this article.
Conclusion
To conclude, USB flash drives are a convenient way of moving data from one device/location to another. But it is also a potential route for accidental/intentional data loss. Studies show that companies lose thousands of records each year due to USB flash drives. Hence, it becomes necessary to closely monitor and control their access.
Typically, organizations have many devices and users, so it's hard to manually control access to each device. This is why tools like Endpoint Protector are a handy option as it comes with a single web-based interface, using which you can decide which group/user/device has access to flash drives. Moreover, this platform records all access to flash drives, so you can run through the log files to identify insider attacks. Further, you can also generate reports to know the state of security in your organization about flash drives and can formulate security policies accordingly. Undoubtedly, these features are sure to bring down the rate of insider attacks and accidental data loss within your organization.
In all, Endpoint Protector is a must-have tool to lock flash drives and prevent accidental/intentional data loss through them.




