USB Lockdown Software is also known as Device control software. These applications protect data against insider threats by controlling and managing data transfers across different removable storage devices. Removable storage devices, such as USBs, smartphones, WiFi network cards, printers, etc., are often used in organizations to easily supply and access information in various formats. However, the data transfer through these applications may increase the chance of insider and external threats. Thus, to avoid any data loss, organizations install USB Lockdown Software. As a result, the software helps detect and prevent your data. In addition, installing the software allows or block access to external devices and maintains the confidentiality of your sensitive business information.
Here is our list of the best USB lockdown software tools:
- ThreatLocker Storage Control – EDITOR'S CHOICE This SaaS package provides system management tools for managed service providers and IT departments including IT asset inventories and patch management. Get a free demo.
- ManageEngine Device Control Plus – FREE TRIAL Protects, controls, monitors, and performs an audit on USB and peripheral devices against any unauthorized device access. Start a 30-day free trial.
- Acronis DeviceLock – FREE TRIAL A popular USB Lockdown Software Tool that provides an end-to-end solution and fully-featured Security Management services. Start a 30-day free trial.
- Endpoint Protector by CoSoSys The Company's flagship product that helps discover, monitor, and protect sensitive information against data theft when connected with removable storage devices.
- Symantec DLP (now Broadcom) The tool helps protect your information from insider theft and ex-filtrating sensitive records.
- SolarWinds Security Event Manager (SEM) A virtual appliance that protects the network and increases efficiency to manage and monitor security policies.
- DriveLock Device Control Keeps your confidential data safe from cyberattacks as it provides end-device protection from hackers.
- MacAfee DLP Highly advantageous for network security teams as it supports various virtual data protection policies that help safeguard your intellectual property or financial records from data theft.
- GFI An Endpoint Security Software that provides end-to-end solutions and reduces the risk of data leakage.
- Ivanti Device Control A trusted monitoring and controlling tool of Endpoint Security that qualifies users to enforce security policies on portable storage devices.
- Gilisoft USB Another widespread data leak prevention (DLP) software that protects your data from getting copied on connected portable storage devices like optical disks, Android or iOS, USB drives, or any other external device.
Why Do We Need USB Lockdown Software?
USB Lockdown Software tools are mainly used to protect your confidential data against any loss, theft, or damage. There are many removable storage devices, flash drives, and other sources that we connect to the systems for transferring files or enhancing productivity. Unknown to the fact, using Wifi and other portable storage devices with the system can also be risky. Therefore, most companies switch to utilizing USB Lockdown Software tools that work as a gateway and control all external data sources. Adding these tools will protect your Intellectual Property and other Personally Identifiable Information.
Apart from preventing data loss, USB Lockdown Software restricts unauthorized devices or users from signing in to a physical workstation. The user must have a valid admin password to access any file or folder.
Benefits of USB Lockdown Software
- It keeps your confidential data safe from unauthorized devices. As a result, any untrusted removable device cannot copy or access your data without your permission.
- USB lockdown software controls and monitors all data that is moving from one device to the other. Also, you can access data only if the gateway grants permission to transfer data to USB and Peripheral ports.
- Features like transfer limit, password restriction, etc., provide granular control over applications.
Features of USB Lockdown Software
Content Filtering: Many newly introduced device control applications practice techniques that provide more than just contextual safety. Nowadays, many device control alternatives manage data filtering module that helps in performing analysis and filtering out any binary and textual content copied to a portable storage device or flash drives.
Network Communications Control: These USB Lockdown Software devices have a feature that controls communication. Be it communicating with web programs, instant messenger applications, network protocols, or other Windows endpoint network communications, the USB Lockdown Software tools contain all. Apart from this, it also monitors and controls routine and SSL-tunneled email communications.
Trust Feature: This feature adds a high level of security and builds confidence among companies that often connect devices to endpoints.
Time and Network-based policies: This feature is best suitable for businesses that follow BYOD policies. It helps generate reports for auditing purposes based on device usage.
Device Access Control: USB Lockdown Software tools provide superior control. As a result, it allows you to manage users who can access the external devices and control them. For example, these tools can discover, monitor, and control who can access FireWire, USB, and COM interfaces. With the help of these tools, you can also monitor other organizational devices, such as printers, WiFi, Bluetooth adapters.
Best USB LockDown Software
We have listed some of the best USB Lockdown software or Device control solutions in this post. These USB Lockdown software tools limit your screen time, reduce the risk of theft or malware attacks from such risky applications, block unauthorized users/devices, and more. Endpoint Protector by CoSoSys, SolarWinds Security Event Manager (SEM), McAfee DLP, DriveLock, GFI Endpoint Security Software, Ivanti Device Control, DeviceLock, Gilisoft USB Lock are a few best USB Lockdown Software tools with their features. Have a look at the list of the best Device Control Tools.
Our methodology for selecting the Best USB Lockdown Software tool:
We've broken down our analysis for you based on these key criteria:
- Effectiveness in preventing data loss and theft.
- Ability to monitor and control data transfer across removable devices.
- Features for granular control, such as transfer limits and password restrictions.
- Comprehensive network communication control capabilities.
- Flexible policies adaptable for various business environments and BYOD policies.
1. ThreatLocker Storage Control – GET DEMO
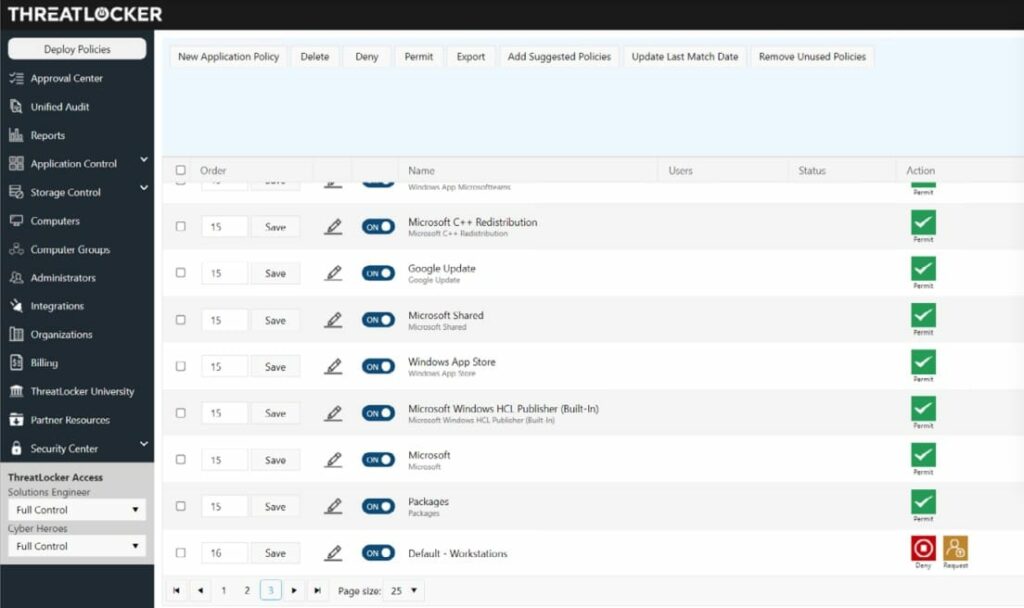
ThreatLocker Storage Control operates from a cloud platform and reaches across the internet to control the USB ports of all endpoints on a protected network. This system starts off by preventing all USB devices from attaching. The administrator is then able to allow specific devices to connect – identified by their serial numbers. The console for the service is resident in the cloud and so it can be accessed from anywhere through a Web browser.
Key Features
- Implements a block in all USB devices by default
- The system administrator can authorize specific USB devices
- Allow USB devices for a user or group of users
- Provides activity logging for file movements
- Community templates and tips to ease security policy creation
- Compliance reporting
Why do we recommend it?
ThreatLocker Storage Control is highly recommended for its effective approach in managing USB device access. By blocking all USB devices by default and allowing only authorized ones, it provides a robust security layer against data theft and malware infiltration.
The Storage Control service is one module on a cloud platform of system security tools. Other units in the package provide the same deny-all and whitelisting system for software, which eradicates the risk of malware. The system provides all of the building blocks for a Zero Trust Access strategy.
Who is it recommended for?
This solution is ideal for organizations seeking a cloud-based, comprehensive USB lockdown solution. It's particularly suitable for businesses that require granular control over USB device access and wish to implement a Zero Trust Access strategy.
Pros:
- Options to permit specific USB drives
- Also blocks other USB peripherals, such as cameras and external disks
- Implements Zero Trust Access
- Can include endpoints anywhere in one plan
Cons:
- No free trial
Access a free demo account.
EDITOR'S CHOICE
ThreatLocker Storage Control is our top pick for USB lockdown software because it immediately prevents any device from attaching to any port on the computers in the protected business’s fleet. This removes the threat of virus infection and shuts down data theft attempts. The ban doesn’t disable USB ports completely, they can still be contacted across the network and this enables the central management console to be used to approve specific devices for use. USB devices all have a serial number and this enables them to be approved for use. That approval can be tied to a specific user account and/or a specific endpoint.
Download: Get FREE Demo Account
Official Site: https://threatlocker.com/platform/storage-control
OS: Cloud-based
2. ManageEngine Device Control Plus – FREE TRIAL
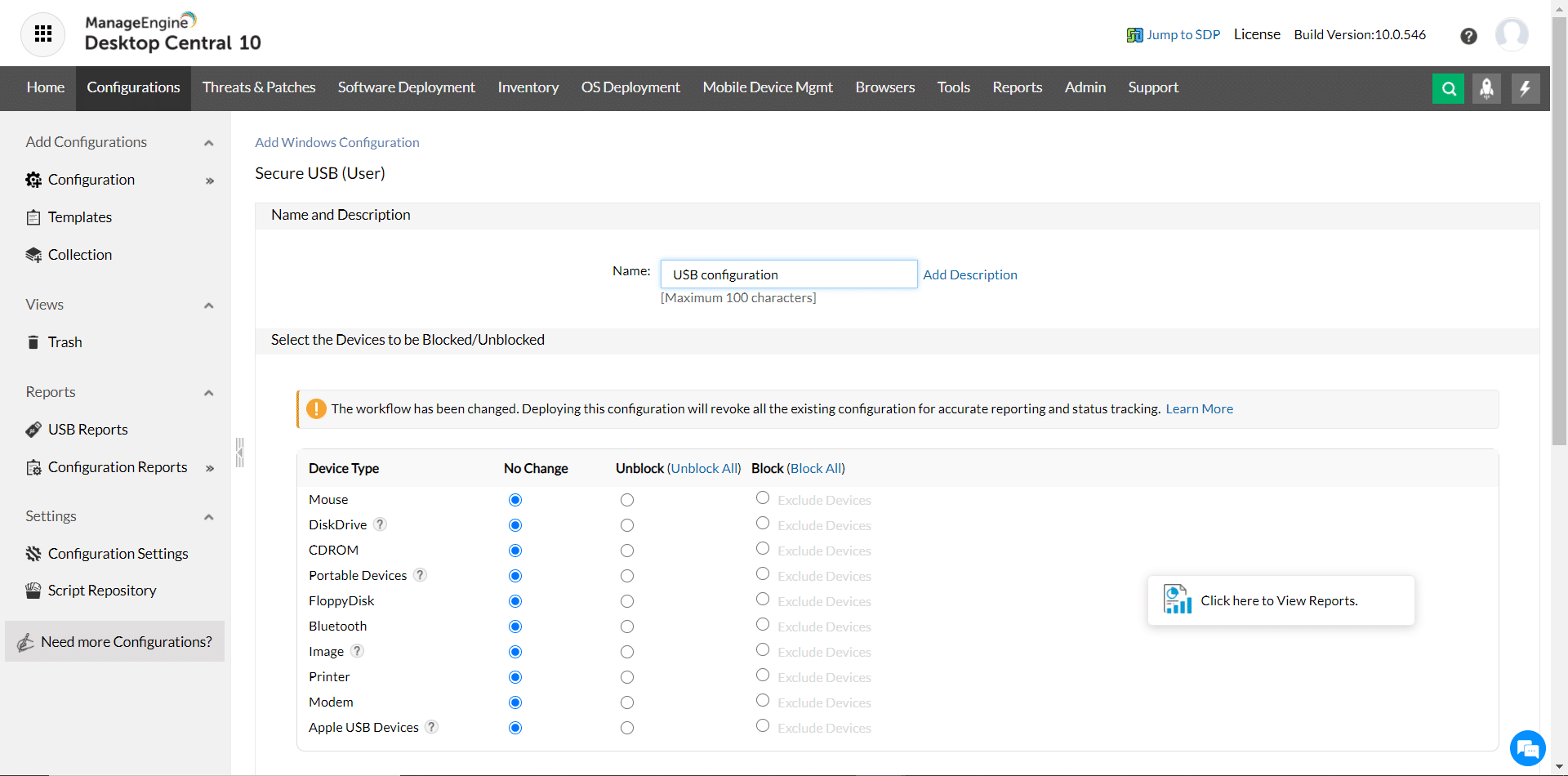
ManageEngine Device Control Plus is another DLP solution suitable for all business sizes. The software protects, controls, monitors, and performs an audit on USB and peripheral devices against any unauthorized device access. In addition, ManageEngine Device Control Plus safeguards sensitive data and can manage multiple device controls and plugged-in external devices from any place.
Key Features
- The role-based access feature restricts or blocks the other sources to copy sensitive data without their permission. For example, to avoid rewriting data, you can authorize read-only permission to specific users.
- You can control and monitor file actions of all vents and plugged-in external devices.
- You have access to regulate file transfers and set a maximum allowable document size for transfers.
- You can create backup copies with password-protection accessible only to the administrators.
- It allows users to spot any malicious insider activity quickly.
Why do we recommend it?
ManageEngine Device Control Plus is recommended for its comprehensive control and monitoring of USB and peripheral devices. Its role-based access features an ability to regulate file transfers provide a robust defense against unauthorized data access.
The software supports role-based access control features, file transfer control, file access permission, meticulous on-demand reports, and more. ManageEngine Device Control Plus is a leading tool that saves all your sensitive data from being lost, stolen, or corrupted.
You are unknown to most external devices and how badly they can damage your system or steal your files. With ManageEngine, you don't need to worry much. The software can stop data leakage and handle multiple peripheral devices remotely. It also creates a backup of your files (accessible to only authorized users) in case of accidental deletion or misplaced devices. The software is practiced commonly by healthcare centers, Government, Technical services, financial institutions, Telecommunication, and Industrial organization.
Who is it recommended for?
This tool is ideal for businesses of all sizes looking for a data loss prevention (DLP) solution that offers extensive device control capabilities. It's particularly well-suited for environments where sensitive data needs to be protected from insider threats.
Pros:
- Designed to work right away, features over 200 customizable widgets to build unique dashboards and reports
- Leverages autodiscovery to find, inventory, and map new devices
- Uses intelligent alerting to reduce false positives and eliminate alert fatigue across larger networks
- Supports email, SMS, and webhook for numerous alerting channels
- Integrates well in the ManageEngine ecosystem with their other products
Cons:
- Is a feature-rich tool that will require a time investment to properly learn
3. Acronis DeviceLock – FREE TRIAL
Acronis DeviceLock is another popular USB Lockdown Software Tool that provides an end-to-end solution and fully-featured Security Management services. It supports contextual and content-based control to prevent leakage. It is highly compatible with the Windows platform and suitable for various businesses, agencies, and startups. It comprises multiple features and functionalities, including content filtering and discovery, network communications control, device access control, etc.
Key Features
- DeviceLock DLP uses Windows endpoints and context-aware controls to prevent maximum data leakage.
- Enforces control of SSL-encrypted traffic.
- Make sure no leakage happens via local channels.
- DeviceLock DLP maintains complete control over access ports, peripherals, and storage devices.
- Content detection feature monitors and controls any moved or accessed content.
- At the initial file transfer stage, DeviceLock DLP blocks data leaks and filters all the copied textual data with content-aware DLP policies for security purposes.
- Uses Windows PrintScreen feature to block screenshot operations and prevent data theft.
- It is an easy-to-deploy on-premises tool.
- The tool is compatible with platforms, like Windows and Mac.
Why do we recommend it?
Acronis DeviceLock stands out for its end-to-end security management, and strong contextual and content-based control features. Its ability to enforce control over SSL-encrypted traffic and prevent data leakage through local channels is particularly noteworthy.
DeviceLock is a complete Security Management system that manages your policy, provides Compliance Reporting and Audit Trail, supports Sensitive Data Identification, Web Threat Management all under one roof. The software protects your sensitive data from unauthorized information access and controls data leakage pathways.
Who is it recommended for?
This software is well-suited for organizations that prioritize strong data leakage prevention, especially on the Windows platform. It's ideal for various business types, including agencies and startups, seeking a robust USB lockdown solution.
Pros:
- Covers all recovery scenarios including DBR, file-level recovery, and cloud-storage backup
- Offers products for both home users as well as enterprise businesses
- Offers data shadowing and incremental backups for quick recovery
- Supports virtual environment backups with bare metal recovery options
Cons:
- Would like to see an automated way to test virtual backup integrity
Start on a 30-day free trial.
4. Endpoint Protector by CoSoSys
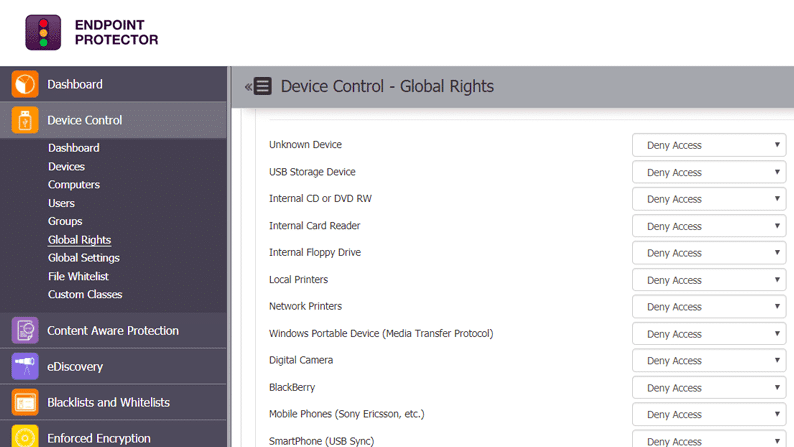
CoSoSys provides the best Data Loss Prevention (DLP) solutions and security software for small-medium-sized businesses. Endpoint Protector is the Company's flagship product that helps discover, monitor, and protect sensitive information against data theft when connected with removable storage devices. The software is compatible with various operating systems, including Windows, macOS, and Linux.
Key Features
- It has an easy-to-use web interface with fast deployment options.
- Supports flexible deployment methods.
- The user-friendly interface makes it simple for employees to understand and utilize the software.
- Supports Windows, Mac, and Linux platforms.
- Automatically enforces data encryption.
- Monitors. controls, and scans data in motion and at rest.
- The software requires no multiple accounts or management panels.
Why do we recommend it?
Endpoint Protector by CoSoSys is recommended for its cross-platform compatibility and ease of use. Its capabilities in automatic data encryption and comprehensive monitoring of device activities make it an effective DLP solution.
The software performs in compliance with data security regulations and allows automatic USB encryption to safeguard data in transit. It is an easy-to-use software solution that controls and manages USB and Peripheral ports. As the software detects the execution of any malicious program, it instantly notifies the end-user. Once activated, the software will provide complete protection to your personal or corporate data from any online attack.
Endpoint Protector monitors device activities and file transfers when connected through portable storage devices to prevent data loss or theft. It also supports multiple deployment options with Virtual appliances, Cloud services, SaaS. The cross-platform DLP solution is an excellent tool for any business that runs hybrid OS networks.
Who is it recommended for?
This software is suitable for small to medium-sized businesses requiring a user-friendly, efficient tool to protect sensitive information against data theft via removable storage devices. It's also beneficial for businesses operating in hybrid OS environments.
Pros:
- Custom security policies can be based on the user rather than the machine
- Automatically assesses risk based on vulnerabilities found on the endpoint
- Can alert to improper file access or insider threats (Acts as a DLP solution)
- Prevents data theft and BadUSB attacks through device control settings
Cons:
- Would like to see a trial version available for testing
5. Symantec DLP (now Broadcom)
Many small to large businesses prefer Symantec DLP software solutions to discover, monitor, and protect sensitive data. In addition, the complete visibility and control feature available in the software further helps reduce the possibility of data breaches and compliance risks. As a result, the tool helps protect your information from insider theft and ex-filtrating sensitive records.
Key Features
- It allows continuous monitoring of policy violations.
- Symantec DLP stops any data leakage through real-time blocking and alert features.
- Supports automated remediation features and one-click SmartResponses that update end-users on any unknown activity.
- It comprises an agent that allows DLP Endpoint Discover and DLP Endpoint Prevent features.
- Supports digitally signed intelligent cards.
Why do we recommend it?
Symantec DLP is recommended for its robust and scalable features that offer comprehensive protection against data breaches and compliance risks. Its continuous monitoring of policy violations and automated remediation features make it a reliable choice for data protection.
Be it accidental risks, malicious attacks, legal liability, data theft, unauthorized destruction, compliance breaches, or environmental hazards, Symantec DLP software is an all-in-one solution and provides comprehensive protection. In addition, it allows controlling deployment and policy enforcement management.
Symantec DLP is a robust, flexible, and scalable software that offers a high level of security and safeguards your confidential data and corporate assets at all times.
Who is it recommended for?
This tool is ideal for businesses of various sizes that need a high level of security to protect sensitive data from insider threats and accidental breaches. It's especially beneficial for organizations using multiple cloud services.
Pros:
- Leverages a global intelligence network to keep client databases up to date
- Offers automatic threat remediation
- A good option for businesses that use multiple cloud services
- Includes extensive Data Loss Prevention and BDR tools
Cons:
- Must contact sales for pricing
6. SolarWinds SEM
The SolarWinds Security Event Manager (SEM) is a virtual appliance that protects the network and increases efficiency in managing and monitoring security policies. The tool helps keep an eye on suspicious activities 24/7 and alerts in real-time to save information from malware attacks or theft. Its intuitive User interface allows bringing in data from logs in minimum time and with less expertise.
Key Features
- Supports automated threat detection functionality.
- The SolarWinds Security Event Manager (SEM) gathers logs at a central place to perform an audit and improve security posture.
- SEM is easy to install and deploy with an intuitive user interface.
- It has an affordable licensing feature.
- Supports file integrity monitoring.
- It flags any suspicious authentications.
Why do we recommend it?
SolarWinds SEM is recommended for its efficient automated threat detection and centralized log management, which significantly enhances network security. Its user-friendly interface and comprehensive security event management make it a standout choice.
It comprises pre-built connectors that collect logs from different sources and create a central place for the teams to discover the threat, prepare reports, and store logs safely. SolarWinds Security Event Manager (SEM) is an easy-to-install USB Lockdown Software Tools.
Who is it recommended for?
This tool is best suited for enterprise-level organizations that need a robust, scalable security information and event management (SIEM) system. It's particularly beneficial for IT professionals who require an in-depth analysis of network behavior to identify and mitigate security threats.
Pros:
- Enterprise-focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Historical analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product built for professionals, and requires time to fully learn the platform
Click here for a fully functional 30-day free trial.
7. DriveLock
Most minor to large businesses choose DriveLock Device Control to keep your confidential data safe from cyberattacks. The software provides end-device protection from hackers. It comprises scalable security functions that protect your IT systems from unauthorized data access. In addition, Microsoft Azure's DriveLock Device Control is GDPR-compliant offered as a cloud service.
Key Features
- It completely controls and monitors which files are copied from one place to the other.
- Automatically encrypts external USB data carriers.
- It provides training to the employees on using external data carriers and managing data security.
- Supports extensive forensic analysis.
- It provides Security standards as per the individual need.
- With DriveLock, you can manage and configure security profiles at the time of cloud hosting.
- DriveLock Device Control helps generate reports.
- Maintains integrity of personal data.
- You do not require individual infrastructure or third-party software for DriveLock.
Why do we recommend it?
DriveLock is recommended for its multi-layered endpoint security and scalable security functions. Its capabilities in controlling and monitoring file transfers and automatically encrypting external USB data carriers are key benefits.
It provides multi-layered endpoint security that helps monitor all internal and external connected devices. It is an excellent solution for any business that wants to keep sensitive data safe from malware, ransomware, etc. It follows the ‘Never trust, always verify' approach and the latest technologies to protect its data and systems. This low-investment cost tool provides holistic security service.
Who is it recommended for?
DriveLock is suitable for businesses of all sizes looking for comprehensive IT system protection from unauthorized data access. It's also beneficial for companies that require GDPR-compliant security solutions offered as cloud services.
Pros:
- Combines device control with DLP and anti-malware features
- Common Criteria EAL 3+ certified.
- Highly scalable – ideal for larger environments
- Offers disk encryption
Cons:
- Not ideal for a non-technical audience
8. McAfee DLP
MacAfee DLP is highly advantageous for network security teams. It supports various virtual data protection policies that help safeguard your intellectual property or financial records from data theft. In addition, it is one of the best USB Lockdown Software for on-premise tools. McAfee DLP controls create duplicating copies and block the transfer of any confidential data to removable storage devices.
Key Features
- The software supports the McAfee ePolicy Orchestrator feature. This feature keeps your confidential data safe from any loss or theft.
- Create reports and alert on real-time occurrences.
- Regulate data transfer to removable storage devices even if not linked to the network.
- It allows protection and security to removable devices and USB data.
- It allows blocking removable storage devices with the ‘Lock Down Devices' feature.
- It allows content-based filtering and blocking of sensitive data on any portable storage device.
Why do we recommend it?
McAfee DLP is advantageous for its ability to support various virtual data protection policies, thereby safeguarding intellectual property or financial records. Its real-time blocking and alert features effectively prevent data leakage to removable storage devices.
The software uses email alerts and cloud applications to update end-users on discovering unauthorized access. Also, it keeps your system safe from unwanted malware attacks and viruses. The tool ensures daily protection of your system and its confidential data against spam and phishing attacks. With the proper protection tool, you can keep your data safe and the system free from any damage at all times.
Who is it recommended for?
This tool is ideal for network security teams in organizations that need daily protection of their systems and confidential data against various threats, including spam and phishing attacks.
Pros:
- Supports Windows, Linux, and Mac OS
- Offers roll-back points for infected endpoints
- Monitors network traffic to stop DDoS attacks, botnets, and rouge mail servers
- Allows sysadmins to orchestrate security policies across their environment
Cons:
- McAfee can use a lot of system resources while scanning (not ideal for older endpoints)
9. GFI
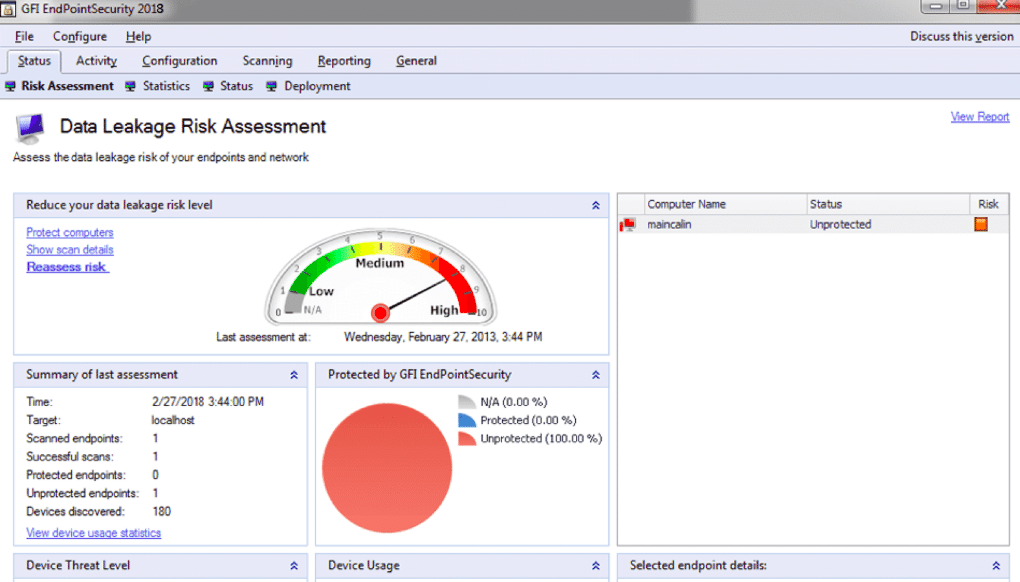
GFI is an Endpoint Security Software that provides end-to-end solutions and reduces the risk of data leakage. This USB Lockdown software is best suitable for small-medium-sized enterprises and startup companies. The full-featured EndPointSecurity is compatible with only the Windows platform. It is an all-in-one software and comprises features like Whitelisting or Blacklisting, Device Management, Encryption, and Activity log.
Key Features
- The software comprises risk assessment capabilities that discover and prevents information leaks.
- It has a database that provides data, security tasks shortcuts, and suggestions for boosting protection.
- It is easy to control and protect data transferred through endpoints with GFI EndPointSecurity.
- IT is a great contributor to DLP and compliance solutions.
- GFI is compatible with only the Windows platform.
- Supports detailed reporting.
- Supports centralized monitoring.
- Supports file control feature.
- Supports auto-discovery functionality.
Why do we recommend it?
GFI is recommended for its comprehensive endpoint security solutions, particularly its ability to reduce the risk of data leakage. Its detailed reporting and centralized monitoring features, combined with auto-discovery functionality, make it a strong choice for data protection.
If you want a high-level security system, go for GFI EndPointSecurity. The software protects your confidential information against cyber attacks and hackers. These professional attackers know to infiltrate your device and transfer all the crucial data. Thus, the tool comprises a device-blocking access feature that stops intruders from accessing any valuable data to safeguard your data. Furthermore, it blocks the intruders from the network and denies the installation of malicious software to the system.
The tool comprises various features that protect and control your crucial data. It also makes sure only authorized users can access the information on the network. Furthermore, users can control the blocked systems based on class, physical port, device ID, etc. It runs a default blocking policy and supports centralized monitoring, detailed reporting, file control features, and more.
Who is it recommended for?
GFI is best suited for small to medium-sized enterprises and startups that require an all-in-one software solution for endpoint security on the Windows platform.
Pros:
- Multi-platform support for Microsoft, Linux, and Mac
- Includes support for patching other popular third-party applications like Adobe, Java, and Runtime
- Simple, yet effective interface
- Built-in vulnerabilities assessment uses patch information to help gauge risk for security teams
Cons:
- Would like to see more features for scheduling patches
- Could use more up-to-date support for newer third-party applications
10. Ivanti
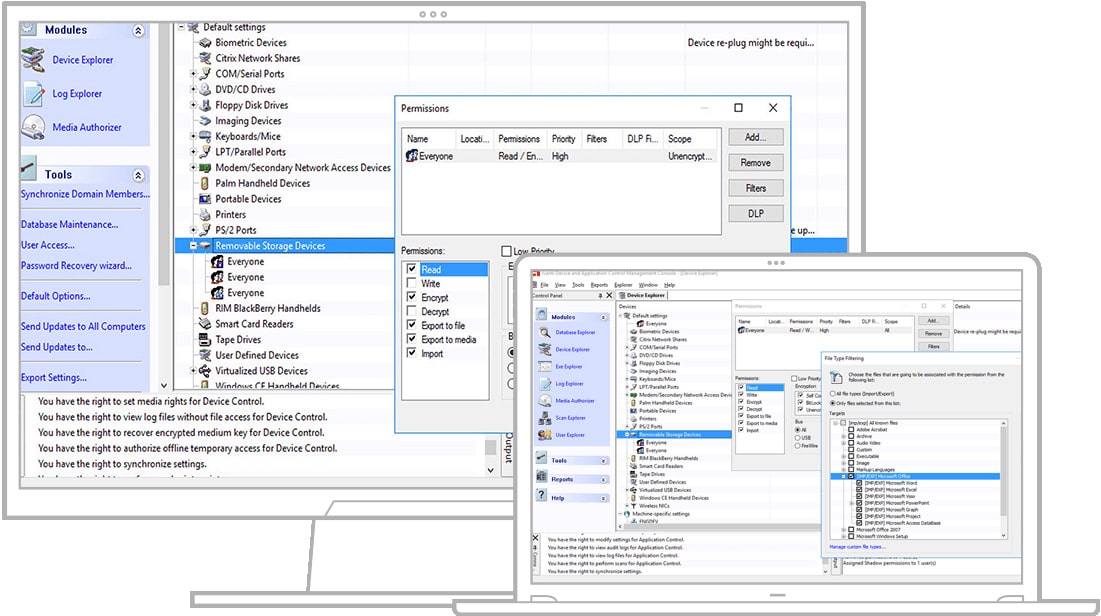
Ivanti Device Control is a trusted monitoring and controlling tool. The software solution is a vital component of Endpoint Security that qualifies users to enforce security policies on portable storage devices. Also, to safeguard your confidential information, the tool secures all the encrypted information on hard drives.
Key Features
- Once you have access to endpoints (for example, USB sticks, keyloggers, and printers), the tool will help control and manage these connected devices.
- It follows a “default deny” approach to managing information and devices from a central location.
- All your productivity tools and are kept safe without denying users access.
- On moving data from one device to the other, the user can implement file type filtering and forced encryption policies with the help of Ivanti Device Control.
- Supports role-based access control.
- Ivanti Device Control restricts access for I/O devices.
- No unauthorized device can copy data from the system with this software solution.
- It has a flexible architecture and provides actionable insights.
Why do we recommend it?
Ivanti Device Control is recommended for its robust monitoring and control capabilities. It enforces security policies on portable storage devices and ensures that encrypted information on hard drives is secure, adhering to a “default deny” approach.
In Ivanti Device Control software, you can grant permission only to authorized users with a simple configuration. No matter how many external devices are connected to your system, no other employee can copy your confidential information as per the tool. It is an endpoint policy enforcement solution that protects your data from malware and ransomware attacks.
It is a potent and secure tool for servers and thin-client. Its features do not allow the installation or implementation of an anonymous app. As a result, your chances of data loss or damage reduce exponentially.
Who is it recommended for?
This tool is ideal for organizations seeking a comprehensive endpoint policy enforcement solution that protects data from malware and ransomware attacks. It's particularly useful for environments with diverse networks, including Linux, Mac, and Unix systems.
Pros:
- Multi-platform support for Linux, Mac, and Unix gives the tool flexibility in diverse networks
- Patch scheduling works well out of the box
- Applies a zero trust model out of the box
- Offers simple graphical reporting which is easy to setup
Cons:
- Must contact company for exact pricing
11. Gilisoft USB Lock
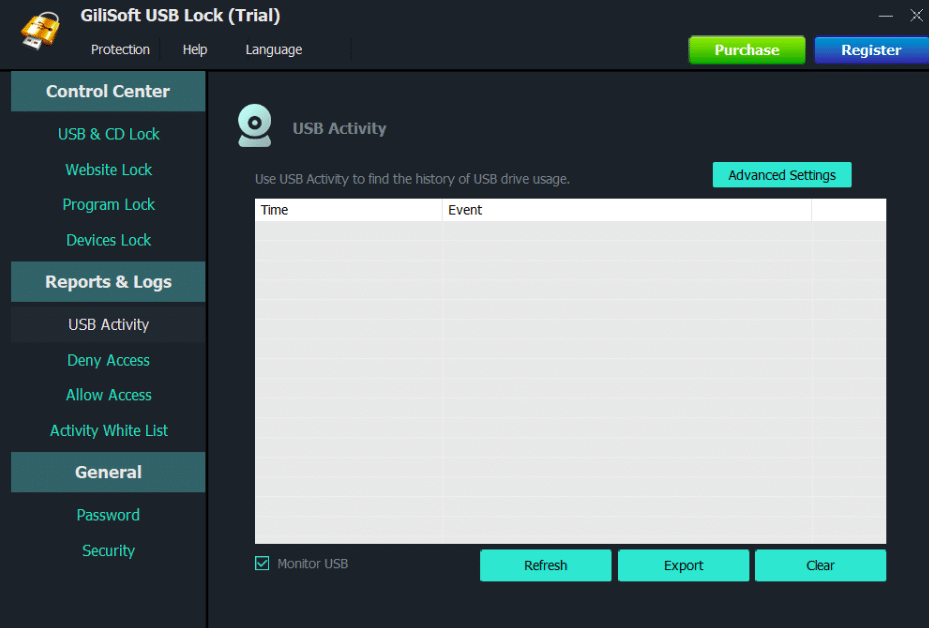
Gilisoft USB Lock is another widespread data leak prevention (DLP) software that protects your data from getting copied on connected portable storage devices like optical disks, Android or iOS, USB drives, or any other external device. No person can uninstall the tool without the administrator’s password. And, after five failed attempts, an alert or email is sent to the administrators if someone tries to crack it.
Key Features
- Disables access to read/write from or to removable storage and media devices like USB drives, DVDs, CDs, non-system drive partitions, SD card readers, and more.
- Supports creation of whitelist for approved devices. This implies that the rest devices not added to the list will get blocked.
- It has the authority to disable the connection with printers, modems, COM LPT ports, Bluetooth, or 1394 ports.
- Serves as a proxy to block prohibited websites, i.e., any unsafe website or the one that stores data like Google Drive, Dropbox.
- Without an administrator’s password, no one can uninstall it.
- Gilisoft USB is an easy-to-install and deploy software solution.
Why do we recommend it?
Gilisoft USB Lock is a comprehensive data leak prevention software that excels in protecting data from being copied to portable storage devices. Its ability to disable access to various devices and block unauthorized websites enhances its security capabilities.
The tool monitors, controls, and blocks the unauthorized outflow of confidential data. Also, after installation, the user can configure and block such drives, which will pause hacking or data leakage. It is easy to deploy or integrate the command-line application into enterprise environments.
Who is it recommended for?
This tool is suitable for environments where there is a need to control a wide range of external device connections, including USB drives, optical disks, and online storage services. It’s particularly useful for larger environments that require a high level of data security.
Pros:
- Great user interface
- Blocks both USB ports as well as disk drives
- Offers password protection as well as full USB denial
- Can also block websites
Cons:
- Better suited for larger environments
Final Thoughts
USB Lockdown Software tools help monitor and control data from theft or leakage when transferring from endpoints to removable storage devices. In addition, these tools protect sensitive information against malware and cyber-attacks. In this post, we have listed some of the best device control software available on the market. Look at the various options and compare tools along with their features.
The primary purpose of installing these tools in an organization is to protect your confidential data against any loss, theft, or damage. Further, they restrict any unauthorized device or user from signing in to any workstation without valid credentials. Attaching removable storage devices directly to the system may increase the chance of theft, damage, insider or external threats. To keep your organization's confidential data, most companies install USB Lockdown Software.
SolarWinds Security Event Manager (SEM), Endpoint Protector by CoSoSys, McAfee DLP, DriveLock, GFI Endpoint Security Software, DeviceLock, Gilisoft USB Lock are a few best USB Lockdown Software tools. Scroll through the complete list and choose the best tool per your requirement.