Why do we want to know about data encryption? The answer is simple, to protect your data. One tool commonly used in the PII tools is the “Endpoint Protector”. Endpoint Protector is a data prevention PII, including a USB encryption system to secure the data transfer.
In this Best USB encryption software tools post, you will learn about the tools overview and their features. Are you more excited? Then let’s get started;
Here’s a quick overview of our top picks for the best USB Encryption tools:
- VeraCrypt – EDITOR’S CHOICE This widely-used system creates a virtual disk, encrypting all contents in a file but making all contents appear to be organized in a normal directory structure. Free to use and available for Windows, macOS, Linux, Unix, and Raspberry Pi.
- AxCrypt Can be used as a simple program to encrypt program files and folders on the USB drive.
- EncryptStick A type of encryption system that allows users to encrypt USB drives and also helps to create virtual folders or files protected with a password.
- Rohos Disk Encryption Packs good features, and the core functionalities of this encryption system are the creation of encrypted volumes.
- Gilisoft USB Stick Encryption Pretty and funky user interface features, a very easy-to-use encryption system.
- DriveCrypt A one-stop solution that guarantees the security of the files. It comes in the form of a handy when you want to encrypt folders or USB drives.
- KakaSoft USB Security A run-of-the-mill type of software that offers minimal features, however, it is a fully self-contained software on the USB flash drives, so it’s straightforward to carry and can be used anywhere.
- Bitlocker A robust and compliant security software that supports Windows operations and is a highly lightweight handy encryption software, easy to carry and use from anywhere.
A Quick Introduction to USB Encryption Software
USB is a flash drive encryption device that ensures your private data is protected as well as secured. Encryption is a method that restricts data access either by software or hardware installed on the hard drive with key locked.
There are two types of USB encryptions available they are:
- Symmetric encryption
- Asymmetric encryption
The most common applications that make use of USB encryption are:
- Wireless security
- Processor security and File encryption
- Wi-Fi security
- Mobile application encryption
- Virtual private network
Why do We Need a USB Encryption Security System?
The following are the reasons why we need a USB encryption security system:
- USB encryption system helps to protect sensitive data on external devices
- USB encryption security system restricts the data flow
- This security system also controls by encrypting valuable data
- The locking system is a useful feature that protects and secures the data
- These encryption devices also provide services like protecting the data from any cyber-attacks or malware attacks, keeping the data safe from data thieves, and securing hardware and software devices and hard drives from any virus attacks
Advantages of USB Encryption Security System
Below are a few benefits of a USB encryption security system:
- USB encryption security system offers improved access to all types of media
- Hardware-encrypted USB drives help users in compliance
- Hardware encryption and password protection are always on
- Zero risk of user mistakes only securely allows storage
- USB encryption security system protest against brute force attacks
- USB malware protection is available, ransomware, and malware over USB are prevalent
- Any lost secure USB drives with sensitive data do not need to be reported and do not expose an organization to GDPR fines
- File encryption and Rohos disk encryption
- Password protection is also an advantage of using a USB encryption security system
The Best USB Encryption Software Tools
Our methodology for selecting the Best USB Encryption Software Tools
We've broken down our analysis for you based on these key criteria:
- We prioritize software with robust encryption algorithms for maximum data security on USB drives
- The user interface and ease of operation are crucial for user-friendliness
- Compatibility with a wide range of operating systems including Windows, macOS, Linux, Unix, and Raspberry Pi
- Additional features like password protection, virtual folders, or encrypted volumes are considered valuable
- Preference for software that is lightweight, portable, and easy to use on different systems without complex installation
Here we have listed the most popular USB encryption software tools used to protect the data on USB drives.
1. VeraCrypt
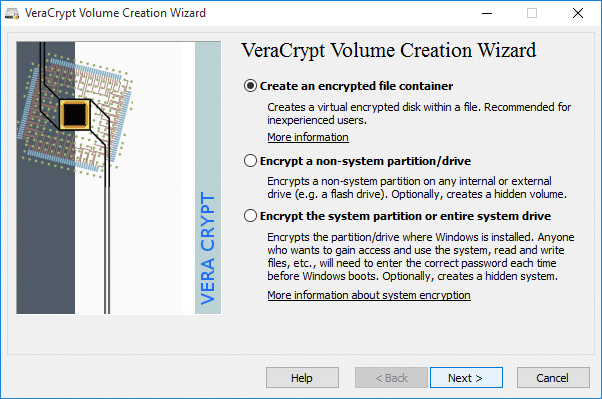
VeraCrypt is a famous and rich USB encryption tool. The main focus is to encrypt the hard disks. VeraCrpyt works well with USB flash drives, and it is one of the best encryption tools available on the market. This type of software creates password-protected disk volumes, and later on, they will be encrypted using industry-standard encrypted algorithms. The algorithms used are Twofish, Serpents, and AES.
Key Features:
- Virtual Encrypted Disk: You can encrypt different assets and disks within a file, and can be mounted as a real disk.
- Encrypts Drive Partition: You can encrypt a particular partition, storage, or drive in real time to read the stored data without any risk.
- Pipelining: This tool uses a pipelining process during encryption and decryption. Hence, the application does not have to load for other portions; it will automatically load other file portions in sequence.
- Hardware Acceleration: This tool uses the system's built-in hardware-accelerated AES, which encrypts files 8 times faster on the same processor.
Unique Feature
A highlight of this tool is its versatility. You can use Veracrypt for encrypting different assets spread across multiple business functions.
Why do we recommend it?
This open-source disk encryption tool works well on Windows, Linux, and macOS, making it ideal for today's multiOS environment. Also, its encryption can be accelerated through hardware.
Who is it recommended for?
Ideal for organizations that are looking to have logical and virtual partitions and want to use algorithms to safeguard these partitions.
Pros:
- Supports Portable Mode: You can also run Veracrypt software without installing it on your system, but you need admin permission to do so.
- Plausible Deniability: This functionality helps preserve the security of the data in case your password is revealed or accessed. It will show hidden volumes or some random cleared data.
- Main Program Window: The main program window helps you perform various file operations, such as mounting Veracrypt partitions/devices and dragging and dropping the volume icon.
- Supports Hotkeys: Veracrypt has hotkeys that can be used to control and manage veracrypt background tasks.
Cons:
- System Hangs: Many users found that while mounting and dismounting volumes on other Windows systems, the system became unresponsive.
EDITOR'S CHOICE
Veracrypt is our top pick for a USB encryption system because it is free to use and can be installed on a long list of operating systems. This tool can be used to compress and encrypt hard drives on computers as well as USB drive contents. The service gives you a choice of encryption ciphers, then encrypts an entire drive, copying it into a hidden file. Access the USB without the password and you see nothing. Entering credentials unlocks the system and you are presented with folders and files as though they were physically on the drive, although this is a virtual presentation.
Download: Download for free
Official Site: https://veracrypt.fr
OS: Windows, macOS, Linux, Unix, and Raspberry Pi
2. AxCrypt
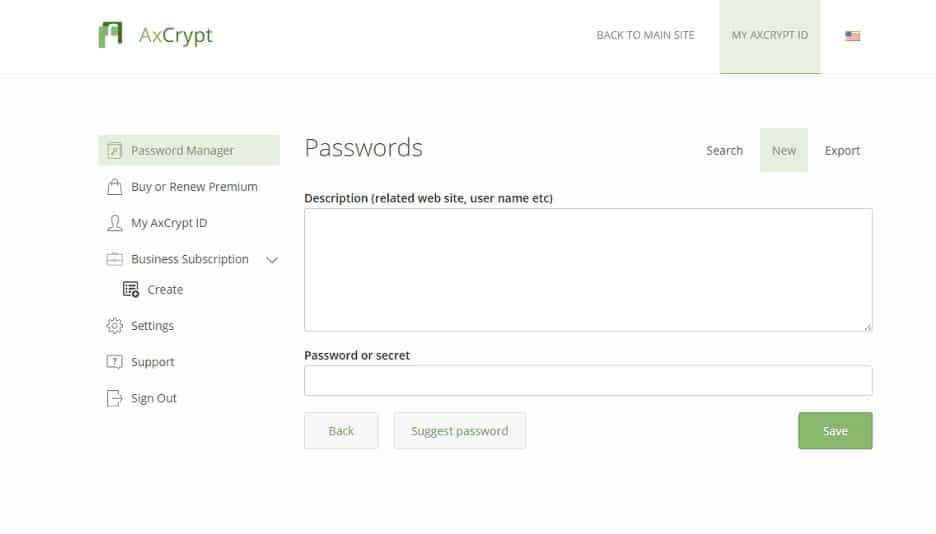
We know that the VeraCrpyt encryption system helps encrypt volumes and external drives. Whereas AxCrypt can be used as a simple program to encrypt program files and folders on the USB drive. More precisely the AxCrypt is the best option to encrypt software programming folders and can be widely used by everyone.
Key Features:
- Wide Compatibility: AXcrypt is compatible with almost all Windows machines, including Vista, 7, 8, and 10, with both 32 and 64 bit versions. Moreover, it also works on Mac, Android, and iOS.
- Open Source and Easy: Open source under a GNU public license that can easily installed by the user with no window integrations.
- Brute Force Resistant: Robust security provides brute force resistance and includes a password wrapping method.
- Unlimited Passwords and Multiple Devices: You can save unlimited passwords and cards and sync this software across unlimited devices and phones.
Why do we recommend it?
AxCrypt uses AES-256-bit encryption, making it hard to crack. Also, you don't need an Internet connection to use this tool.
Who is it recommended for?
A good choice for individuals and organizations that want to protect their business and personal data.
Pros:
- The AxCrypt Offers Standard-Based Cryptography: It only uses well-researched cryptographic algorithms and modes of operations
- Provides Data Integration Verification: The secured files cannot be modified without detection
- Automatic File Updating: Offers automatic of the secured file after opening and saving
- Local Device Security: Shredding of all temporary and encrypted plain text files
- Large File Support: Supports files larger than 4GB
- Metadata Retention: Retains the original file name and the information of the secured file
- Brute Force Resistant: Dynamic brute force counter measures with iterative password wrapping, making attacks even harder
- Open-Source: Under GNU general public license
Cons:
- Don't Protect Local PC: Users find that AXcrypt does not protect the local system if data exposure is due to a third-party application being installed.
3. EncryptStick
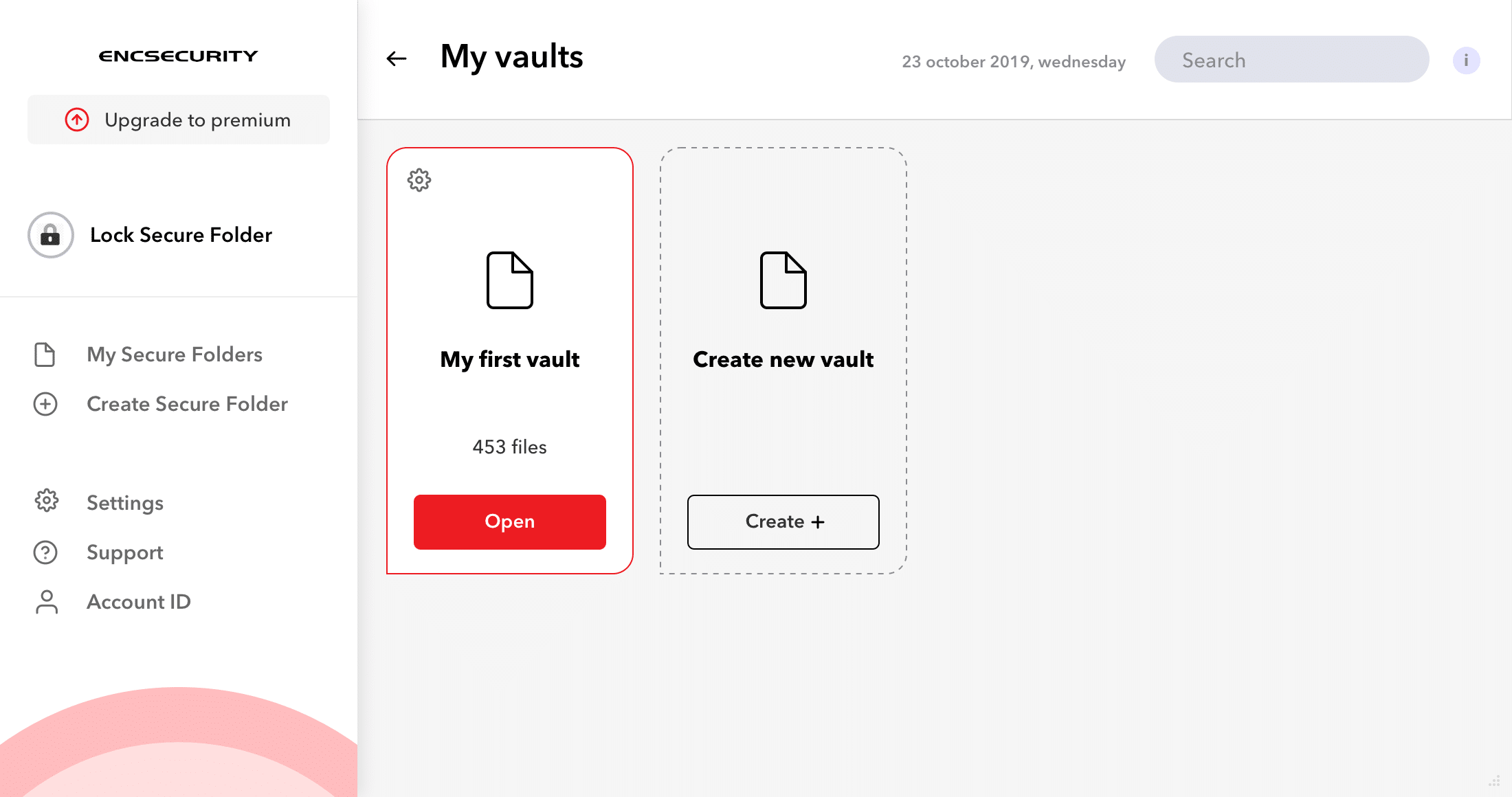
The EncryptStick is a type of encryption system that allows users to encrypt USB drives and also helps to create virtual folders or files protected with a password. The EncryptStick offers one of the most robust encryption mechanisms to encrypt flash USB drives on various operating systems such as Windows, MAC, Linux, etc.
Key Features:
- Encrypt Applications: Helps hide and protect applications like Skype, Google Chrome, and folders
- Create Backups: Backup encrypted disk manually or set up automated backup options
- Encrypted USB Drives: Create a protected partition on your USB flash drive
- Options: Setup disk autostart, disconnect hotkeys, and other options
Why do we recommend it?
It can encrypt not just your sensitive files but also your USB flash drive, desktop vaults, and all your passwords. With such a tool, the chances of data theft and loss are minimal.
Who is it recommended for?
Works well for both individuals and small organizations that want to encrypt their sensitive content.
Pros:
- Manage All Passwords: The password manager stores your password securely in an encrypted format, so you won't have to worry if you forget it.
- Easy File Syncing: You can easily and securely sync your files on your local device flash drive and remote places.
- Various Options: It has many other options, such as setting up disk autostart, disconnecting hotkeys, setting up authentication keys, and more.
Cons:
- Slower Encryption Speed: Some users find that it has a slower encryption speed than hardware encryption.
4. Rohos Disk Encryption
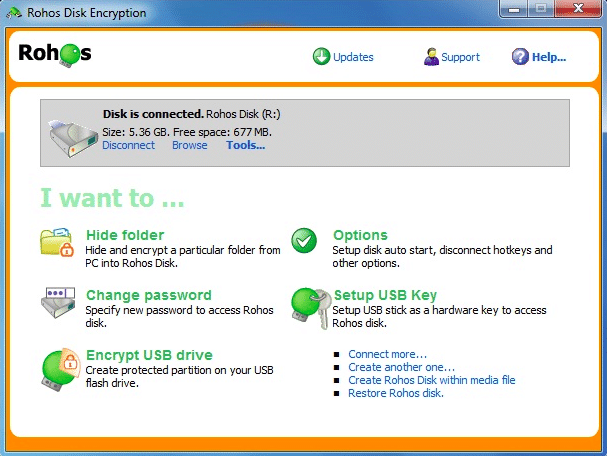
The Rohos Disk Encryption system packs good features, and the core functionalities of this encryption system are the creation of encrypted volumes. The Rohos Disk encryption is straightforward to customize the encrypted volume size and parameters like file locations and mount point letters.
Key Features:
- Strong and On-Fly Disk Encryption: This tool offers automatic and on-the-fly encryption because it uses the NIST-approved AES encryption technique with a 256-bit encryption key length.
- Robust Data Security: There is no data-loss risk because of the partition password reset feature. If you forget your USB key or password, you can access your secured disk by creating a backup file.
- Steganography: Comes with a plausible deniability feature that means your disk is secure inside a media container like AVI, MKV, MP3, OGG, and much more.
- Two-Factor Authentication: With the two-factor authentication method, you can unlock and access your disk through a USB flash drive and smartphone.
Why do we recommend it?
Rohos Disk Encryption is portable and can hide the contents of your USB drive behind an advanced encryption algorithm. Also, the encryption is on-the-fly, which means, there's no residual data in the temp files.
Who is it recommended for?
Works best in situations where you want to password-protect a part of your USB drive or portable HDD.
Pros:
- Suitable for Newbie Users: It is easy to use due to its single-click and automatic system startup functionality. It has a disk-on notification, notifying users when the partition is ready.
- Hide Shortcuts on Desktop: you do not have to worry about shortcuts stored on your desktop; Rohos automatically hides the shortcut when you are offline.
- Expandable Virtual Drives: You can expand your virtual drive partitions according to your needs. However, you need to make sure they are NTFS-format partitions.
- Unlimited Encryption Capacity: The best part is that you can store unlimited encrypted drives hassle-free in your network storage, flash drives, and cloud storage.
Cons:
- Lack of Steganography in Rohos Mini: The steganography functionality is not available in Rohos mini, and some users also noticed the file deletion due to file shredders.
5. Gilisoft USB Stick Encryption
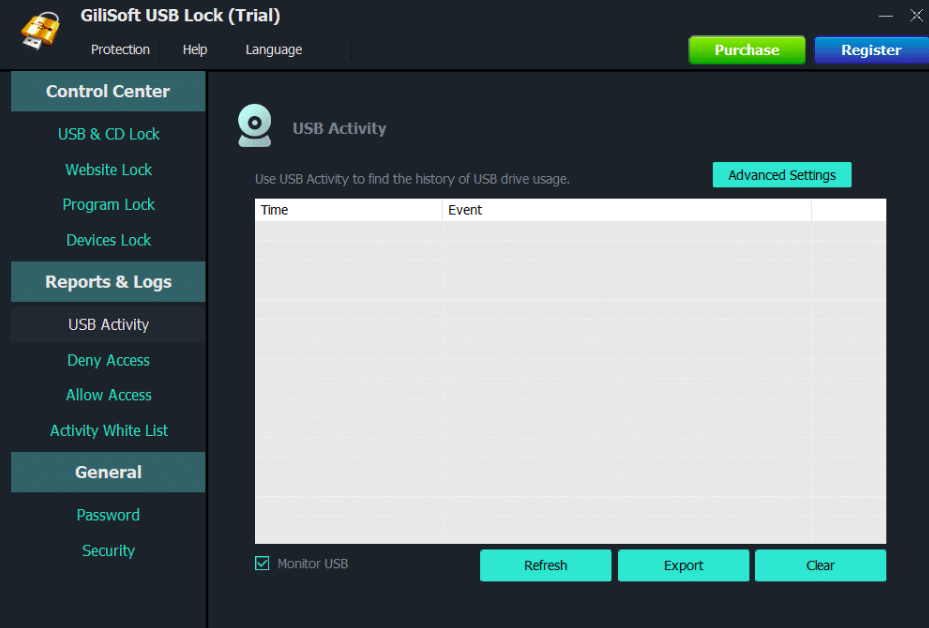
The Gilisoft USB Stick Encryption offers pretty and funky user interface features. However, it’s a very easy-to-use encryption system. All you need to do is just plug in the flash drive, and it detects automatically. Most importantly, you need to specify the disk area where you want to create the file on the drive and the encrypted password.
Key Features:
- Password-Protected USB Flash Drive: You can password-protect your USB flash drive so unauthorized persons will not access the data, even if it's lost.
- Automatic File Encryption: It has automatic file encryption that encrypts the files while they are saved and stored on the host drive.
- Works with Any USB Format: Capable of encrypting any type of USB drive, including flash drives, thumb drives, portable drives, internal drives, and more.
- Trustworthy Security Isolation: Creates a safe space on the drive to store important files safely.
Why do we recommend it?
Protects data across a wide range of portable storage devices in your Windows system. Moreover, it uses AES encryption algorithms for improved protection.
Who is it recommended for?
Ideal for personal, government, and business use to avoid data thefts through USB drives.
Pros:
- Automatically Locks Encrypted Data: When the drive is disconnected, or the system is shut down, the encrypted data is automatically locked. Hence, the user might need to enter the password again to access it.
- Runs on Most Windows Versions: Users can easily install this USB encryption software on Windows desktops from XP to Windows 11. Moreover, it also works fine with tablets, workstations, and other servers.
- User-Friendly: It is easy to use and doesn't cause any complications with other technical programs present in the system.
- Fast Copy Function: Its fast copy feature can back up the whole USB to a particular folder or hard disk.
Cons:
- Slow While Unlocking and Accessing File Access: Users find it difficult to unlock the file and sometimes the system hangs periodically.
6. DriveCrypt
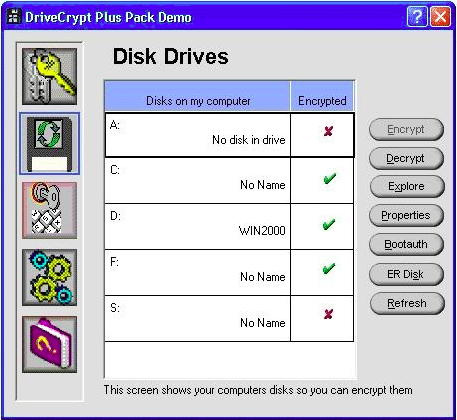
The DriveCrypt is a one-stop solution that guarantees the security of the files. DriveCrypt comes in the form of a handy when you want to encrypt folders or USB drives. It is also possible to encrypt selected files with DriveCrypt. This software also features a password sniffing facility that prevents Trojan files or hackers from trying to access the DriveCrypt passwords.
Key Features:
- Automatic Decryption: Automatically decrypts the file when loaded, and encrypts when stored on disk.
- Volume-Resize Functionality: Allows users to customize the encrypted volume and hard disk space according to their needs.
- Robust Authentication: Strong authentication adds extra security to the file during the ongoing encryption process.
- Various Encryption Algorithms: Users can choose from multiple lists of encryption algorithms according to the requirement to ensure file integrity.
Why do we recommend it?
This security tool is easy to use and at the same time, it can protect the proprietary data on your laptops and desktops. It also gives the option to encrypt an entire hard disk partition if needed.
Who is it recommended for?
Works well for remote employees and those who are always on the move. Most suited for individuals over large organizations.
Pros:
- Authorize Users: Allows you to set access and roles to ensure that the encrypted data is only accessible by legitimate users.
- Pendrive and USB Disk: Users can also encrypt the pen drives and USB disks stored on specific partitions to add an extra layer of safety.
- Smart Hiding: This software hides data in strange locations, such as fake disks or music file folders, that are impossible to guess.
- Invisible Container: Has secret storage space, which is also known as an invisible container that is only known by admins and authorized persons.
Cons:
- Need More Space and Time: Users feel that performing specific encryption requires a lot of space and is also time-consuming.
7. KakaSoft USB Security
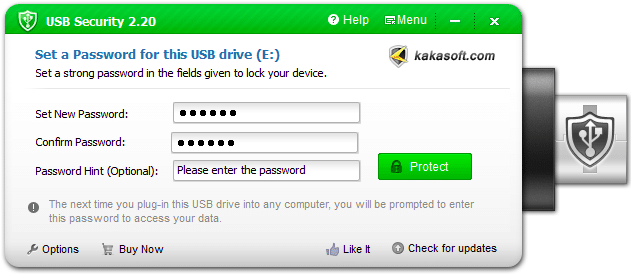
KakaSoft USB security is a run-of-the-mill type of software that offers minimal features. However, this USB security is fully self-contained software on the USB flash drives, so it’s straightforward to carry and can be used anywhere. The Kakasoft USB security utility installs itself on the USB drive and runs automatically whenever you plug it into the drive.
Key Features:
- Instant Protection: Protects your USB when it's connected to your PC, making sure your confidential data and documents are safe and untouched.
- Virtual Drive: Users can mount a USB drive to a virtual drive to make any necessary changes. This also reduces the risk of viruses and malware.
- Zero Malware Violating: Kakasoft protects your data from any cyber threats or malware by blocking unauthorized access and suspicious activity:
- Password Hint: Don't worry if you often forget your password; this tool gives you a special hint to memorize it and reset it successfully.
Why do we recommend it?
Protects the data on different portable devices like USB flash drives, memory sticks, HDD hard drives, and more. Also, it uses the AES-256 algorithm for the highest safety.
Who is it recommended for?
A good choice for small and medium organizations whose employees are likely to use USB sticks to transfer information. Even for organizations that don't use USB sticks for data transfer, this tool can help prevent insider threats.
Pros:
- Reliable: Utilizes advanced encryption techniques and has multiple layers of protection to manage multiple USB devices.
- USB Copy Protection: Automatically detects screen recording activities and makes copying media files and data secure.
- Folder Lock: It supports a folder lock feature that allows you to lock a specific folder, which means you cannot move, delete, or access the locked folder.
- Reset Window Password: Also allows you to reset or delete windows in case you forget the admin password. You can create new windows within minutes and recover passwords.
Cons:
- Not for Files and Folders: This tool is not for encrypting specific files or folders. It only encrypts USB security.
8. BitLocker
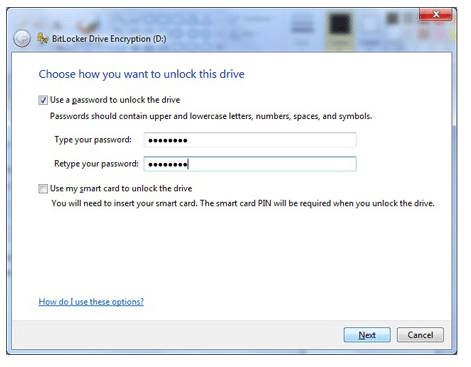
If you don’t want to use third-party software, then this is the perfect software to go with it. The Bitlocker to go is a robust and compliant security software. This software configuration supports Windows operations and is a highly lightweight handy encryption software, easy to carry and use from anywhere. Users can configure this software in a mere second by using the Bitlocker Drive encryption applet on the control panel.
Key Features:
- Pre-Boot Authentication: Protects the data with pre-boot authentication. Even if another person has your physical access, they won't be able to access files.
- Portable Storage Protection: Also preserves data security while it's shared between different locations and devices.
- AES Encryption Algorithm: Uses 128 or 256-bit encryption algorithms to hide sensitive data such as financial data, personal identity, and much more.
Why do we recommend it?
Bitlocker is a Windows utility that encrypts all user and system files to prevent unauthorized access to lost and stolen computers. It can also check the integrity of boot configuration data to reduce the chances of a device takeover.
Who is it recommended for?
This tool is well-suited for organizations that have to comply with stringent guidelines like HIPAA. This includes companies in healthcare, law enforcement, banks, law and accounting firms, and other financial services.
Pros:
- Mitigates Unauthorized Data: BitLocker has an enhanced file system that protects data from accessing when it gets into the wrong hands.
- Helps to Automate Tasks and Scripting: Users can turn BitLocker into a drive and set their desired unlocking and authentication method.
- Encrypt Removable Data: Users can also encrypt removable data quickly when needed.
- Best for Remote Work: BitLocker is the best option for remote workers because it keeps sensitive data confidential and prevents threats.
Cons:
- Unsatisfied Support: Users find that the BitLocker community does not provide proper support, so it might not be suitable if you are using this tool for self-encryption.
Final Thoughts
Why do we need a USB security system? Here is the answer; If you use sensitive data, then the encryption method must securely transfer large files through USB drives. One more benefit of using a USB security system is that it will add a complex layer of security that can’t be brute-forced by anyone. This Best USB security tool post explains the top security tools available, their features, advantages, and drawbacks. If you are looking for a free USB device, go for the VeraCrypt device; it’s free, open-source, and encrypts external volumes on USB drives. We hope this post might help a few security, and networking engineers, large security communities, and experts around the globe.
USB Encryption Software FAQs
How do I encrypt a USB stick?
In order to encrypt your USB stick, you need to install an encryption system. You can download such a service onto your computer and then encrypt multiple USB sticks. These systems usually block access to the contents of the memory stick to all but those with access credentials.
What type of encryption is used for USB?
There are many encryption ciphers that can be used to encrypt a USB memory stick. The strongest cipher available is the Advanced Encryption Standard with a 256-bit key. You will see this written as AES-256.




