In today’s world, identifying an individual personality using the data has become a challenging and quite exciting task. We thought why not provide information on this for our readers to be aware of current trending technologies. Today, we will discuss a more exciting topic: PIII (Personally Identifiable Information), and the best PII scanning tools available. From this Best PII scanning tools post, you will be learning their features, advantages, and disadvantages. I know you people are more excited then let’s get started;
Here’s our list of the best PII Scanning tools:
- Manage Engine Data Security Plus – FREE TRIAL Α popular PII scanning tool. It is agent-based, monitoring, data compliance, server auditing, and prevents data loss tools. Start a 30-day free trial.
- ManageEngine Endpoint DLP Plus – FREE TRIAL A bundle of discovery, protection, and detection services for sensitive data management. Available for Windows Server. Get a 30-day free trial.
- Endpoint Protector A Data loss prevention PII tool that offers all possible functions that we are looking out for in a PII, and most important, threat detection is also possible.
- Digital Guardian DLP A tool used as a Software-as-a-service (SaaS) cloud platform that also helps to reduce data leaks and offers threat detection.
- Teramind A system that prevents data loss from employee productivity and provides insider threat detection.
- Varonis A PII scanning tool that uses various machine learning techniques to prevent data loss, detects suspicious user behavior/characters, identifies the location where the data get over-exposed and reduces the risk of breach.
- Nightfall Security A type of PII scanning tool that uses machine learning to solve business-critical data problems which also is a cloud-based security platform to prevent data loss.
- PII Tools Developed to perform data audits and regulatory compliance operations. These tools are generated based on AI-driven technologies so that the detection accuracy will be 99%.
- Egnyte Security Framework A hybrid infrastructure that offers users a highly secure environment to create cloud-based storage platforms.
First, we would like to give a quick introduction to the PII.
A Quick Introduction to PII
PII stands for personally identifiable information that defines the collection of data fields to identify the individual person. Nowadays, companies hold PII for specific purposes and we assume that data must be kept confidential and secured. Failure to follow the PII guidelines can result in a huge fine and even if your company is unable to protect individual data, there might be a chance of suing the company. PII failure may also cause financial consequences.
To understand the concept of the data field in a better way, consider a table that consists of the following customer details:
- First name
- Last name
- Credit Card number
- CVV
- Card Expiry date
- Social security number
- Address line1
- Address line2
- City
- Postal code
- Email address
- Telephone number
The following are the best scenarios where we need to have PII:
- To protect the data from hackers.
- Credit card scammers use your first name, last name, credit card number, expiry date, and CVV. To protect your credit card, using the PII tool is a must.
- Data theft who stole the data through online mediums.
- To avoid all these consequences, PII has developed various scanning tools, OCR, and fingerprint options.
What are the benefits of using PII?
PII offers enormous benefits over data security and protection. We list a few of them below:
- PII provides deep insight into sensitive data.
- PII is a powerful search tool to identify sensitive data.
- Information tagging is also possible with the PII.
- Predefined and custom discovery rules.
- PII offers statistical concept-based analysis.
- Automated sensitive data remediations.
- High precision with PII data security process.
- Reusable and incremental data indexing.
- PII is designed in a non-intrusive architecture format.
- Easy to deploy in the organizations.
- Language detection and keyphrase extraction are also possible.
- Topic modeling and custom classification.
- Entity detection and custom entity tasks can be performed using the PII.
What are PII scanning tools and their benefits?
The PII scanning tools are the tools that are used to protect the data and avoid any security consequences that occur in the organizations.
All the PII scanning tools should perform the following operations:
- They should search for all the endpoints, and the devices are used to identify the data locations.
- Searching of the data location using an Indicator that signals the PII.
- I classified the PII based on sensitivity and the type of data content.
The following are the benefits of using PII scanning tools:
- PII scanning tools offer data discovery and classification services.
- Supports access to the right auditor.
- A security policy management system of PII scanning tools is able to preset the data template with the specific data privacy standard.
- PII tools provide file integrity monitoring benefits with file encryption.
- They help monitor the peripheral devices, emails, file transfer, and data movements constantly.
- Provide a free data assessment and demo.
- These tools help combine all the data protection functions or systems at a fair price.
Now let’s talk about the best PII scanning tools.
The Best PII Scanning Tools
Here we will give you a complete idea of the tools, their advantages, and disadvantages. Let’s begin:
1. ManageEngine Data Security Plus – FREE TRIAL
The ManageEngine Data Security Plus is a popular PII scanning tool. It is agent-based, monitoring, data compliance, server auditing, and prevents data loss tools. The purpose of using Manage Engine Data Security Plus PII tools is to deliver complete visible data access on the Windows managed file server environments.
Features of ManageEngine Data Security Plus
- Multi-factor authentication
- Block websites
- Inventory management
- Role-based access
- Patch devices
- Data encryption
Pros:
- This tool offers a high -level of PII discovery and classifications.
- Controlling of extensive data access in the enterprises.
- Improves Access right management.
Cons:
- No cloud version is available.
- Data risk occurs.
You can start with a 30-day free trial.
2. ManageEngine Endpoint DLP Plus – FREE TRIAL
ManageEngine Endpoint DLP Plus provides a sensitive data management service. The package discovers and classifies data in a continuous process. When the system first starts its service, it provides a sweep that generates a system-wide data profile. This process needs to be tailored for specific data types, such as bank card data or personally identifiable information, such as names, addresses, and social security numbers. After that initial sweep, the tool will keep vigilant and add new instances of sensitive data to the register as they are created.
Features of Endpoint DLP Plus
- Templates for data security policies
- Data discovery and classification
- Limits data access to trusted applications
- Data containerization
- Scans data movement channels
- Controls USB ports and USB drives
- Watches file shadowing
- Monitors cloud uploads
- Provides levels of permissions
- Permissions linked to files rather than users
- User activity tracking
- Logging for security analysis
- A Free edition monitors 25 endpoints
- Runs on Windows Server
Pros:
- Continuous discovery and classification of data
- Limits access to sensitive data to only trusted applications
- USB management with permission levels
- Email scanning for Outlook
- Data transfer scans
Cons:
- Email controls only operate on Outlook
You can start with a 30-day free trial download.
3. Endpoint Protector
The Endpoint Protector is a Data loss prevention PII tool. It offers all the possible functions that we are looking out for in a PII, and most important, threat detection is also possible. The endpoint protector also helps implement the data security policy (including identifying the sensitive data) and monitoring the information constantly. With the help of Endpoint Protector, data encryption is also possible and allows any business to maintain compliance with data privacy standards.
Features of Endpoint Protector
- Policy management
- Patch management
- Configuration management
- Application control
- Live security updates
- Encrypted algorithms
- Offline support and Forensics
- Blended threat protection
- HTTPS malware detection
- Web filtering and exploit blockers
- Server security
Pros:
- It provides discovery and classification services.
- Access right auditions.
- Controlling of data with exfiltration channels.
- File integrity function with monitoring through processes like encryptions and logging.
- It also provides standard enforcement compliances.
Cons:
- Sometimes, it’s impossible to add security information and event management in organizations.
The Endpoint protector can be accessed with Azure, Google cloud platform, and AWS as a paid tool.
4. Digital Guardian DLP
The Digital Guardian DLP tool is used as a Software-as-a-service (SaaS) cloud platform. It also helps to reduce data leaks and offers threat detection. All operating systems (Windows, IOS, Linux) can implement this type of PII scanning tool. The digital guardian DLP provides data access right management that can access the sensitive data via various security policies. This type of PII service help to improve user access permissions and operates e-discovery sweeps continuously.
Features of Digital Γuardian DLP
- Management console
- Data visibility and control
- Advanced threat protection
- Data discovery and classification
- Endpoint data loss prevention
- Network data loss prevention
- Cloud data protection
- Application whitelisting
Pros:
- Offers sensitive data discovery and classification of data based on specific functions.
- Provides additional threat detection methods.
- Helps to control the data movement.
- It also provides secured intellectual property.
Cons:
- It is impossible to get the price list.
- Account takeover and insider threat also occur sometimes.
5. Teramind DLP
The Teramind is a system that prevents data loss from employee productivity and provides insider threat detection. This type of PII tool requires the following requirement to configure they are:
- GDPR, ISO 27001, PCI DSS, and HIPAA requirements.
- The main task performed by Teramind is discovery and data classifications in PII.
Features of Teramind DLP
- Cloud computing systems can also adopt this PII tool. (primarily SaaS).
- It is available for all the operating system platforms such as Windows, MAC, but not for Linux or Unix.
- Data user analysis and risk assessment features.
- Users can run the endpoint over the Virtual machines.
Pros:
- This tool includes insider threat detection and employee productivity data assessments.
- Helps to discover and categorize the data.
- Adds the pre-set templates for the company standard compliance.
Cons:
- The Teramind DLP’s endpoint does not support the Linux operating systems.
- It is available as a paid service with no free subscription.
6. Varonis Data Security Platform
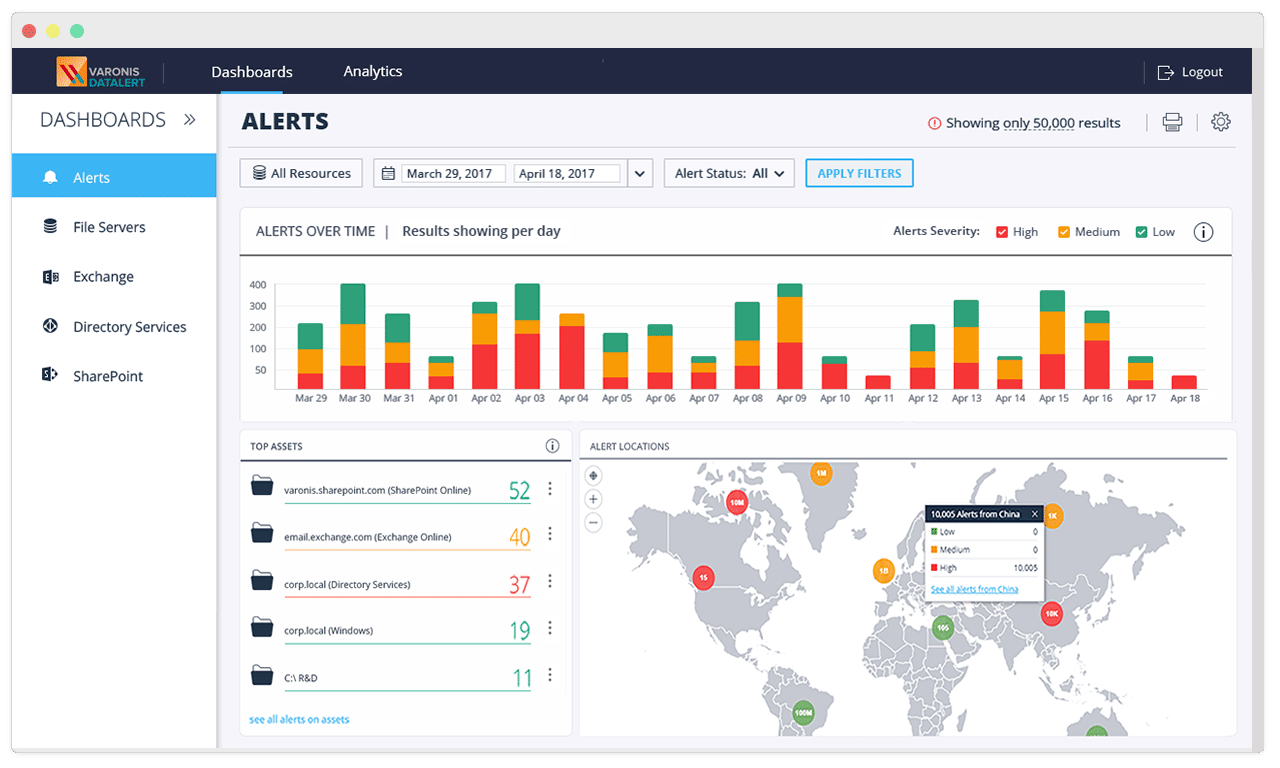
Varonis is a PII scanning tool that uses various machine learning techniques to prevent data loss, detects suspicious user behavior/characters, identifies the location where the data get over-exposed, and reduces the risk of breach. This software security system headquarter is in New York, and the primary operations include tracking the malicious data, visualizing, data analyzing, and protecting the unstructured data.
Features of Varonis
- Restrict access to only the people who need it.
- Safely remediate the millions of exposed folders in a few clicks.
- Rapidly detect and contain insider threats and cyber attacks.
- Eliminates the common pathways and prevents credential threats.
- Archive or delete stale, unused data with automated workflow.
- Provides brute force attack.
- Modifications: critical GPOs.
- It helps in failed privilege escalation detected.
- The service account attempted to access a personal device for the first time.
Pros:
- The Varonis system offers abnormal DNS reverse lookup requests.
- DNS Exfilterations and DNS tunneling.
- Detection: Active directory containers.
- Executes account looked out.
Cons:
- First, to access Varonis, you need to pay upfront and recurring charges.
- Sometimes it requires ample storage space to store data files.
- Finally, it involves Machine learning knowledge to use.
7. Nightfall Security
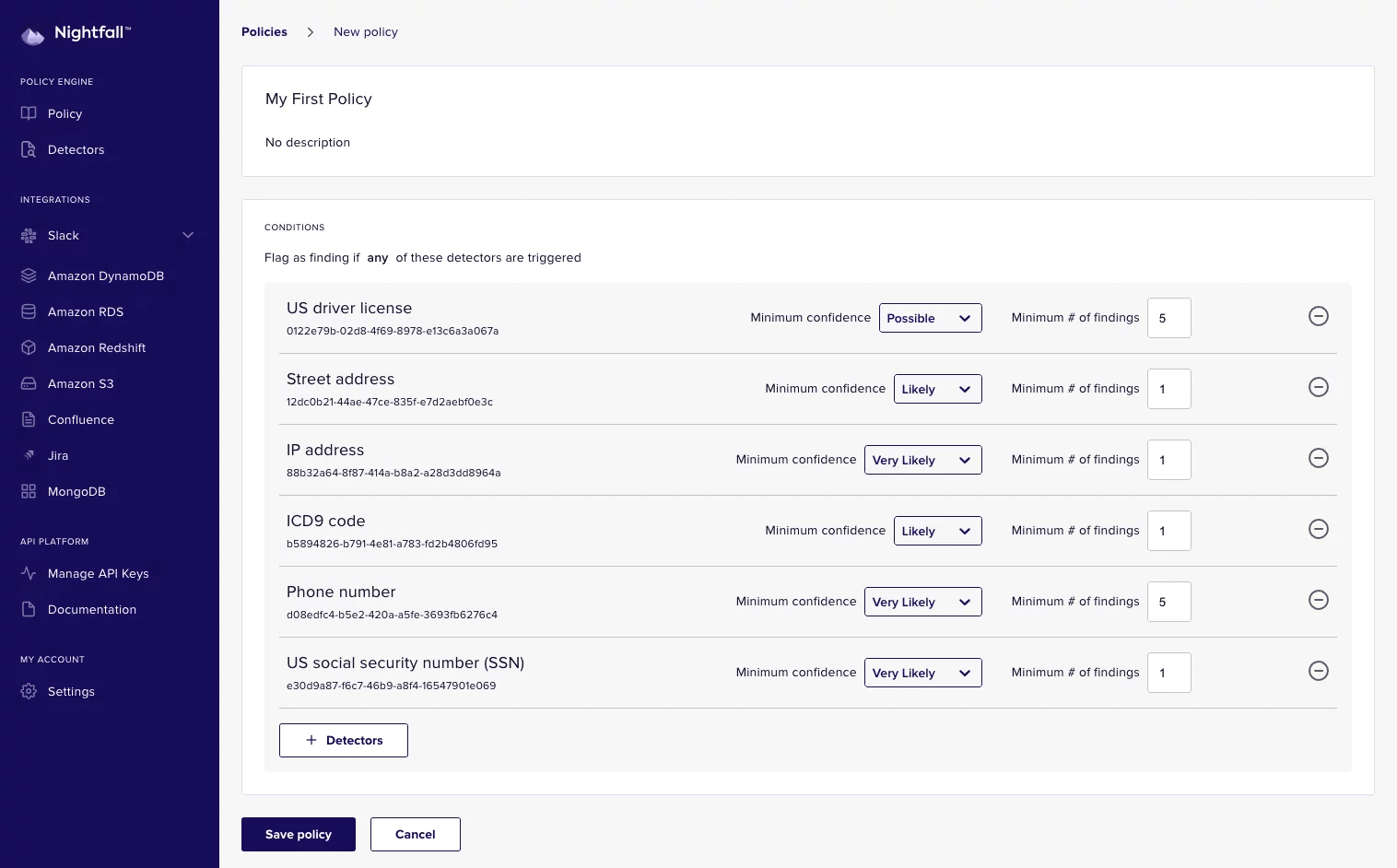
Nightfall Security is also a type of PII scanning tool that uses machine learning to solve business-critical data problems. Nightfall security is also a cloud-based security platform to prevent data loss. It uses the Application programming interface (APIs) to classify and protect sensitive data. This security platform uses various deep learning concepts to retrieve structured data, including API keys, credit card number details, and CVV.
Features of Nightfall Security
- It is developed based on AI and machine learning techniques.
- High-level data protection.
- Data loss prevention is also possible.
- Nightfall is considered a developer platform.
- Cloud-based security system.
- It is a cloud-native software system.
- The Nightfall system automates data discovery.
- Data classification is also possible.
Pros:
- Offers high-level data security.
- It is wholly designed using Machine learning and AI techniques.
- The biggies like Tesla, Facebook meta, Google, and many more adapt the nightfall security system to protect their data.
- System analytics.
- It uses raw data to detect data loss.
Cons:
- The data breach is a challenging task.
- A lot of security issues.
- The risk of using unstructured data might also be a challenging task.
- To access this security system, it is mandatory to have Artificial intelligence and Machine learning knowledge.
Website Link: https://nightfall.ai/solutions/use-cases/secure-pii
8. PII Tools
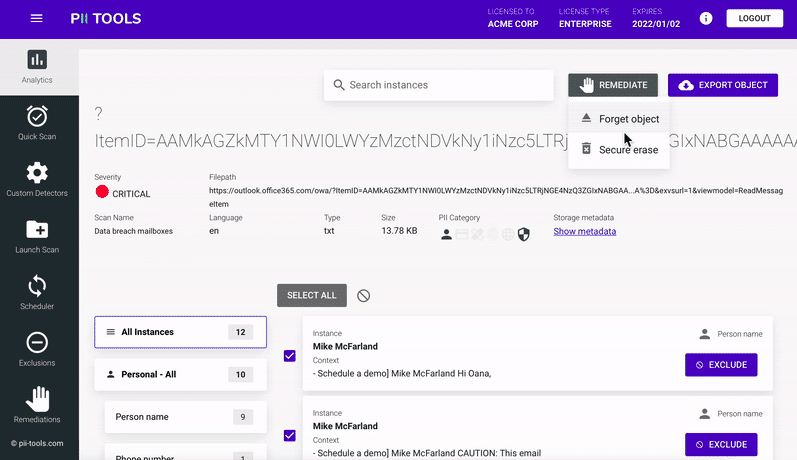
The PII Tools are developed to perform data audits and regulatory compliance operations. These tools are generated based on AI-driven technologies so that the detection accuracy will be 99%. PII tools help to discover data, Analyze, and data recovery. In addition, PII (personal identify an individual) helps manage the data to identify an individual.
Features of PII Tools
- Identifies the data location.
- Online identifiers (that include the IP address).
- An identification number.
- Adds physical attributes.
- Health information is also provided.
- The economic, cultural, or social identity of a person.
Pros:
- Integrate training on data privacy into your general training program and onboarding for new staff.
- Encrypted storage solutions, password managers, and virtual private networks.
- Monitor your network for suspicious activity to detect an attack early enough to reduce the damage.
- Implement the zero trust model by restricting access to the entire network.
Cons:
- The lack of result transparency.
- Sensitive to the initial data.
- Inadequate utilization of the resources.
- Less accuracy with high-dimensional data.
9. Egnyte Security Framework
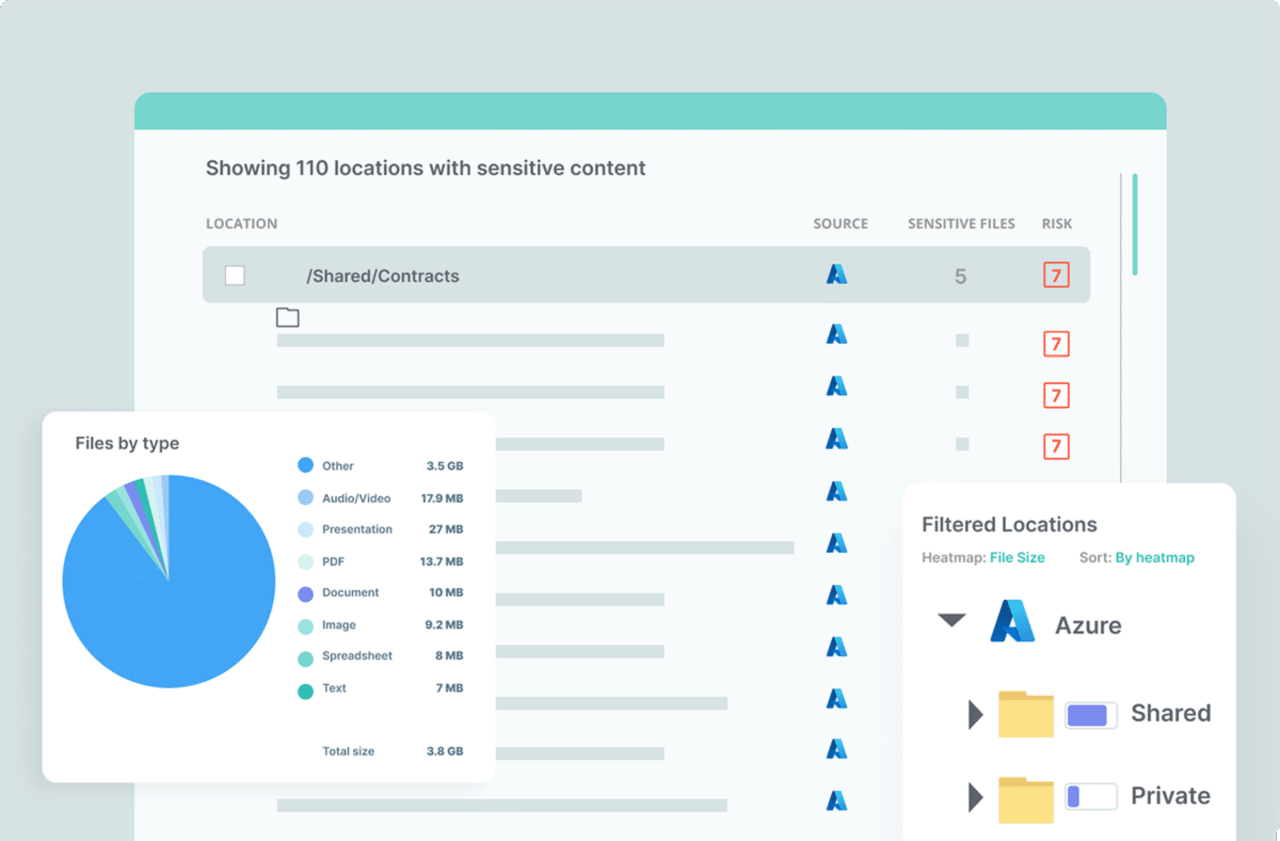
Egnyte Security Framework is a hybrid infrastructure that offers users a highly secure environment to create cloud-based storage platforms. Egnyte framework is built in such a way that it enables users to share the content with internal and external groups. This framework is widely used in a client-facing organization to create a secured customer portal. Furthermore, the Egnyte framework uses data encryption techniques on all the data access routes. One more important benefit of using Egnyte is solving the problems related to data storage. In the future sections, you will see the features, pros, and cons of the Egnyte security framework.
Features of the Egnyte Security Framework
- Unified multi-cloud content
- Provides information governance
- Employee productivity
- Cloud-data storage
- Data encryption techniques
- Secured customer portals
Pros:
- First, this framework helps locate sensitive and valuable data in the company content.
- Controls risk and automate compliance.
- Protect against internal and external security threats.
- Helps to access the most relevant and recent data files from the devices.
- Shares security with confidence and ease.
- Work faster and collaborate seamlessly online and offline.
Cons:
- Greater risk of viruses or malware while sharing large files.
- Needed data bandwidth is expensive.
- It is tough to keep track of the public files in Egnyte.
Final Words
In recent times, we feel that knowing more about data security and protection is crucial. Every day, we encounter problems like data hacking, credit card scammers, and cyber threats. These PII scanning tools play a vital role in organizations and everyone’s lives to avoid such issues. This Best PII scanning tools post helps readers across the globe to explore more into security. Here we have explained the top PII scanning tools and their features, pros, and cons. We hope this post may help a few of you, large PII communities, and online portals to share the knowledge.
PII Scanning Tools FAQs
What is PII scanning?
PII scanning is the process of searching for and identifying personally identifiable information (PII) in digital data. This can include information such as social security numbers, credit card numbers, and other sensitive information.
Why is PII scanning important?
PII scanning is important because it helps prevent data breaches and identity theft. By identifying and securing sensitive information, organizations can reduce the risk of unauthorized access or disclosure, which can result in financial loss or damage to reputation.
What are some common types of PII that may be scanned for?
Common types of PII that may be scanned for include social security numbers, credit card numbers, bank account numbers, driver's license numbers, passport numbers, and email addresses.
What tools can be used for PII scanning?
There are many tools available for PII scanning, including commercial software solutions and open-source tools. Some examples of commercial PII scanning tools include SecureTrust, Identity Finder, and PII Tools. Open-source tools include PIIscan and PII Tools Suite.
How does PII scanning work?
PII scanning works by searching for specific patterns or combinations of characters that are associated with sensitive information. This can be done using algorithms or regular expressions, which are applied to digital data such as files or databases. When PII is identified, the scanning tool can take action, such as flagging the data for review, redacting the sensitive information, or quarantining the data for further analysis.
What are some best practices for PII scanning?
Some best practices for PII scanning include developing a clear policy on what constitutes PII and how it should be handled, using automated scanning tools to reduce the risk of human error, regularly reviewing and updating scanning criteria to ensure they are effective and up-to-date, and providing training and awareness programs for employees to ensure they understand the importance of protecting PII. It's also important to have a clear plan in place for responding to any PII breaches or incidents that may occur.