Penetration testing tools are applications used to detect network security threats.
Penetration testing, also referred to as “pen test”, is an authorized simulated attack on your system attempted by security experts (white-hat hackers) to evaluate your computer systems’ security. These attacks simulate the real-world attacks carried out by black-hat hackers (criminal hackers).
The tests will detect vulnerabilities including the possibility for unauthorized attackers to get access to the system data. Moreover, the tools can also identify system strengths for executing a full risk assessment. The test results are further used by organizations to make their applications more robust and secure.
Here is our list of the best Penetration Testing software and service:
- CrowdStrike Penetration Testing Services This team of white hat hackers will probe your system inside and out from their remote location, identifying exploits.
- Invicti Security Scanner Web-based and On-Prem security testing tool that automatically checks several security threats for target websites. You can scan 1000+ web applications with this tool.
- Acunetix A vulnerability scanner that can be used during penetration testing exercises to identify weak points in any IT system. Available for Windows, macOS, and Linux.
- Ettercap Open-source security auditing tool that helps you to scan for man-in-the-middle attacks on LAN.
- Intruder Automated Penetration Testing An automated vulnerability scanner used to find cybersecurity threats on the target website.
- Nessus Widely used security tool that scans the target system and alerts if it discovers any vulnerabilities.
- SQLmap Open-source pen-testing tool used to detect and exploit SQL injection attacks.
- Zed Attack Proxy Open-source. One of the most popular web application scanners that can be used to assess web applications for vulnerabilities.
- Wapiti Vulnerability scanner that allows you to audit the security of your websites. It supports both GET and POST HTTP methods for attacks.
- Owasp Open-source and full-featured DAST tool that includes both automated scanning for vulnerabilities and tools to assist expert manual web application.
The Best Penetration Testing Tools
Our methodology for selecting penetration testing tools and software
We reviewed various penetration testing tools and analyzed the options based on the following criteria:
- Support for various attack methods and mediums
- Auditing and reporting capabilities
- Integration support into other cybersecurity and SIEM platforms
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
Every software application listed in this post comes with a unique set of features, ideal for different business niches.
1. CrowdStrike Penetration Testing Services
CrowdStrike is one of the leading cybersecurity operations in the world and the company has its own research team and their flagship product is CrowdStrike Falcon Prevent. As well as keeping technicians on staff to identify, explain, and resolve the latest hacker strategies, CrowdStrike contracts in hackers to work for them. This team of hackers is scattered across the globe, enabling team members to launch attacks from anywhere.
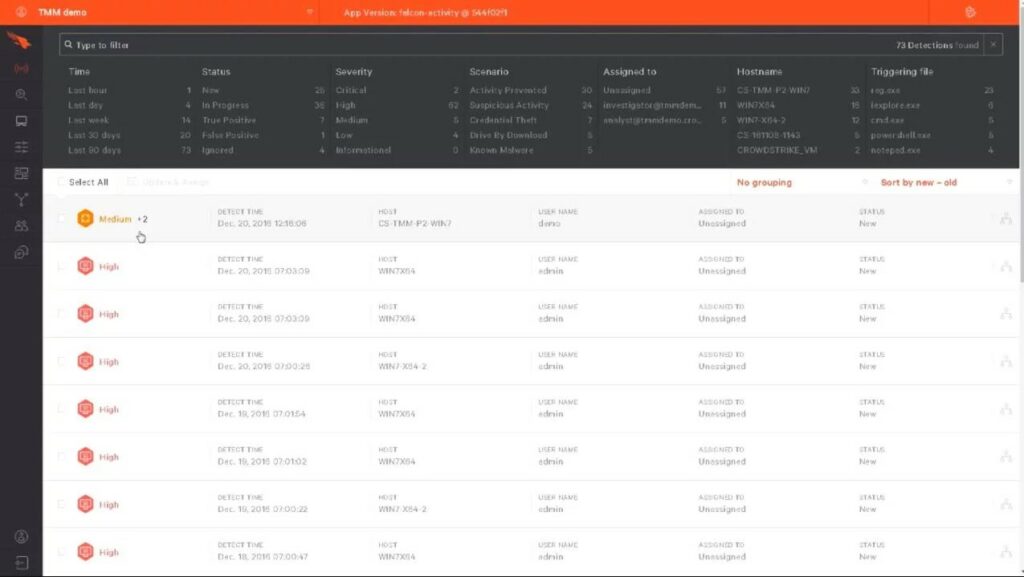
Rather than defending your system from this hacker activity, CrowdStrike charges for the attacks. These are white hat hackers and their attacks on your system highlight system weaknesses that you need to tighten up before real hackers discover them.
Key Features of CrowdStrike Penetration Testing Services:
- A team of real-life hackers who will use well-known hacking techniques to break into your system and probe it
- Internal penetration testing within a network
- Access management probing to break into your system
- External attacks that will be launched from several locations around the world
- Attacks on Web and mobile assets and APIs to identify security weaknesses
- Hijacking of external assets to use them as a method to tunnel into your system
- Insider threat assessments through a hacker, given an account, traveling through your system
- Wireless penetration testing that discovers the weaknesses in your wires systems inside and outside your building
Why do we recommend CrowdStrike Penetration Testing Services?
CrowdStrike Penetration Testing Services are recommended for their unique approach, utilizing a team of skilled hackers to identify and exploit system vulnerabilities. This hands-on, real-world testing strategy ensures that organizations are prepared for actual cyber threats, making these services a vital tool in any robust cybersecurity strategy.
The CrowdStrike option isn’t a package of tools or an automated package that you run yourself. It is the services of real-life people who know how to hack into a system.
Who is it recommended for?
CrowdStrike's services are particularly well-suited for organizations looking for comprehensive, human-led penetration testing. Companies seeking to understand and mitigate potential vulnerabilities from various attack vectors, including internal, external, and wireless threats, will find CrowdStrike's expertise particularly valuable.
Pros:
- Doesn’t rely on only log files to threat detection, uses process scanning to find threats right away
- Combines HIDS, endpoint protection, and vulnerability scanning in a single platform
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Can install either on-premise or directly into a cloud-based architecture
- Lightweight agents won’t slow down servers or end-user devices
Cons:
- Would benefit from a longer 30-day trial period
You will have to contact the CrowdStrike team to discover pricing which will be dependent on your network needs. You can also get access to a 15-day free trial to CrowdStrike Falcon Prevent to figure out your network protection requirements.
https://www.crowdstrike.com/services/penetration-testing/
2. Invicti Security Scanner
Invicti is an extremely easy-to-use web application security testing tool that automatically checks for cross-site scripting (XSS), SQL Injection and other security threats in your websites, web services and applications. It is available as a SaaS solution or even On-Prem.
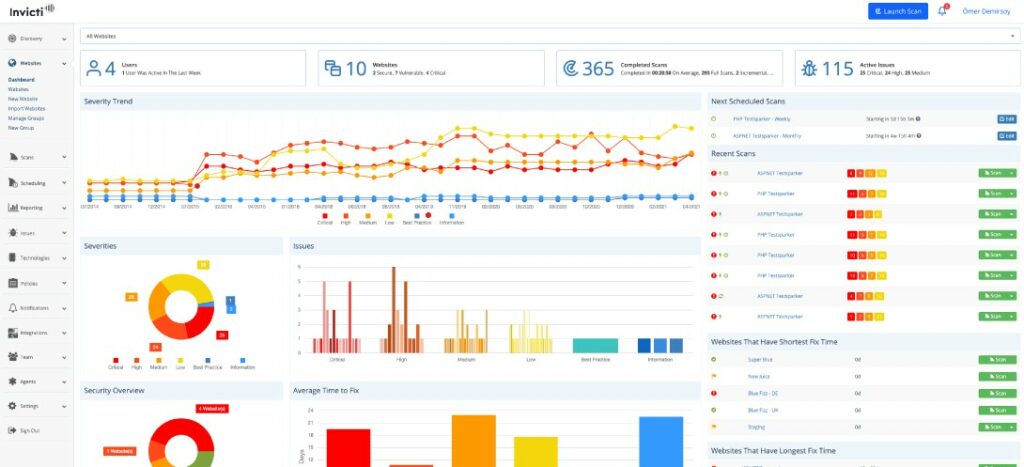
Invicti penetration testing tool is highly robust and is able to scan around 500 to 1000 web applications simultaneously. Plus, it has custom settings for security scan, allowing you to set authentication, attack options and URL rewrite rules. It produces proof of exploitation and you can easily view the impact of security threats.
Key Features:
- Scans 1000+ web applications at the same time
- Automatic scanning requires minimal configuration from the user
- Allows adding multiple team members for seamless collaboration and result sharing
- Proof-based scanning detects accurate vulnerabilities
- Advanced crawling allows for API scanning
- Dedicated JavaScript engine to scan modern websites and single-page application
- Automates scheduled future scans
- Built-in reporting tools with a clear visual dashboard
Why do we recommend Invicti Security Scanner?
Invicti Security Scanner is recommended for its ease of use and the ability to perform comprehensive, automated security testing on web applications. Its capability to scan a large number of applications simultaneously and its advanced crawling features make it a standout choice for thorough web application security testing.

Who is it recommended for?
Invicti is ideal for organizations that manage numerous web applications and require a scalable, robust security testing tool. Its user-friendly interface and minimal configuration requirements make it suitable for both technical and non-technical users.
Pros:
- Features a highly intuitive and insightful admin dashboard
- Supports any web applications, web service, or API, regardless of framework
- Provides streamlined reports with prioritized vulnerabilities and remediation steps
- Eliminates false positives by safely exploiting vulnerabilities via read-only methods
- Integrates into dev ops easily providing quick feedback to prevent future bugs
Cons:
- Would like to see a trial rather than a demo
3. Acunetix Vulnerability Scanner
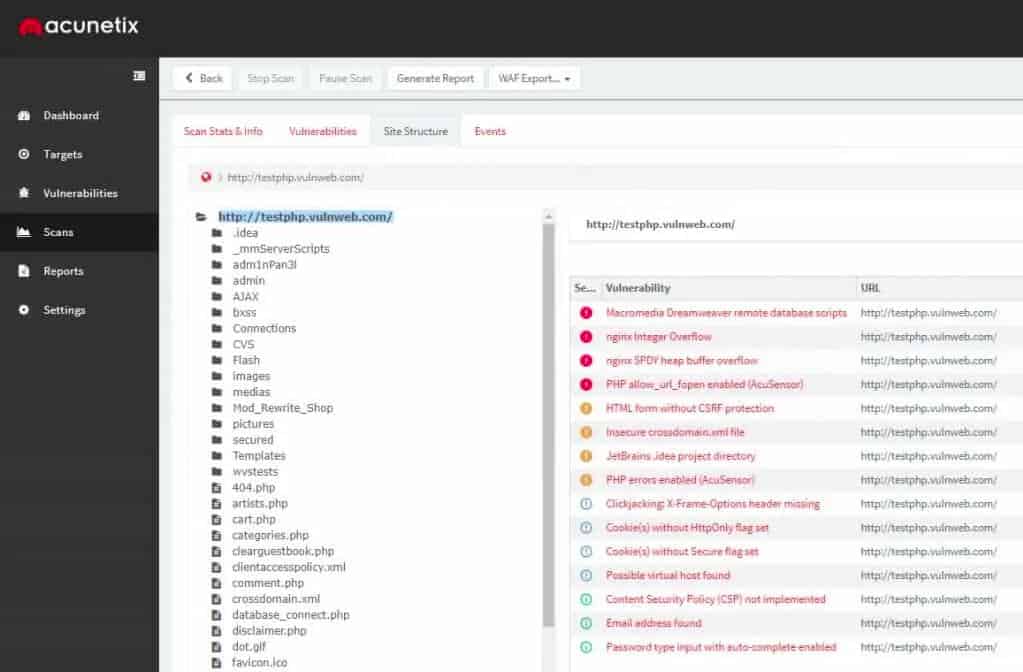
Acunetix offers a vulnerability scanner that you can install on your own site. It scans for Web vulnerabilities and is easy to use – even by non-technical staff. The system offers scans on demand.
Key Features:
- A scanner specifically designed to scrutinize APIs and Web services, such as serverless systems
- A fast scanning performance
- A low false-positive rate
- Configuration and cross-infection checking
- Network security scanning
- Integrations for CI/CD platforms, such a Jenkins for DevOps environment checking
- Coordination with issue trackers, such as Jira and GitLab
Why do we recommend Acunetix Vulnerability Scanner?
Acunetix Vulnerability Scanner is recommended for its specialized focus on web application security, boasting fast scanning performance and a low false-positive rate. Its ability to integrate with various CI/CD platforms and issue trackers makes it a powerful tool for continuous security monitoring in DevOps environments.
The core function of Acunetix is to scan for the OWASP Top 10 vulnerabilities. This system is offered in three editions: Standard, Premium, and Acunetix 360.

Who is it recommended for?
Acunetix is particularly suitable for organizations with a strong focus on application security, including those with serverless systems and complex web services. It is an excellent choice for teams that require seamless integration with other security and development tools.
Pros:
- Designed specifically for application security
- Integrates with a large number of other tools such as OpenVAS
- Can detect and alert when misconfigurations are discovered
- Leverages automation to immediately stop threats and escalate issues based on the severity
Cons:
- Would like to see a trial version for testing
4. Ettercap
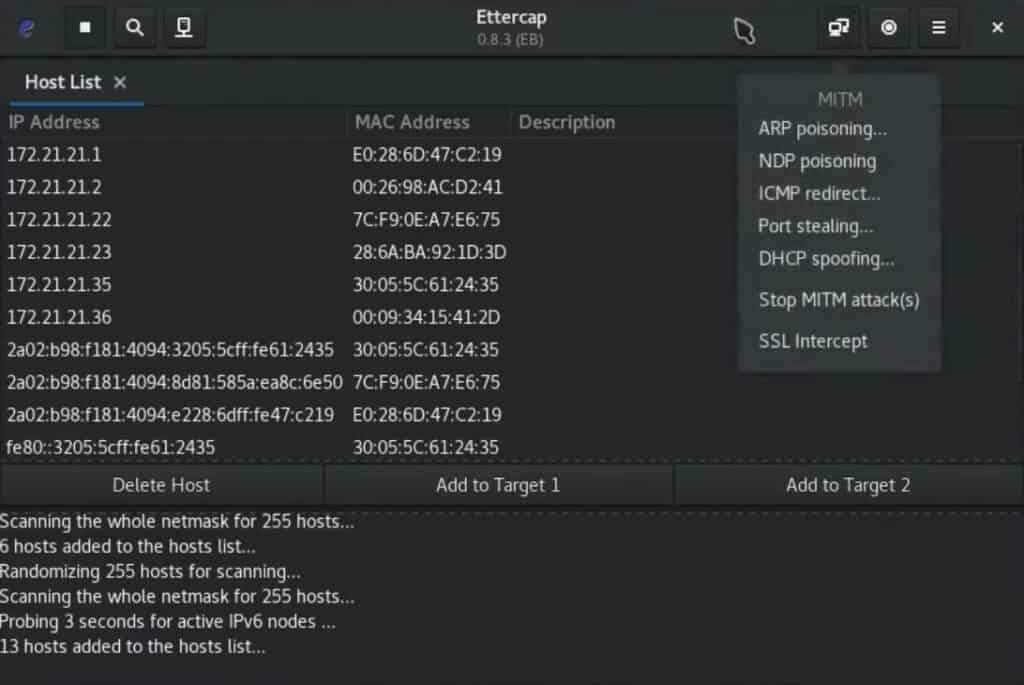
Ettercap is an all-inclusive suite to detect MITM (man-in-the-middle) attacks. It features content filtering on the fly, sniffing live connections, and other such innovative practices. It also has various features dedicated to host and network analysis. Moreover, it offers support for passive and active dissection of numerous protocols.
Key Features:
- Support for passive and active dissection of several protocols
- Sniffs an SSH connection in full-duplex
- Sniffs HTTP SSL secured data even if the connection is established through the proxy
- Features API to create custom plugins
- Allows injection of characters to a client or into a server without hindering a live connection
- ARP poisoning feature allows sniffing on a switched LAN between two hosts
Why do we recommend Ettercap?
Ettercap is recommended for its comprehensive suite of features for detecting man-in-the-middle attacks. Its support for various protocols and content filtering capabilities make it a valuable tool for network analysis and security.
This pen-testing tool is quite easy to use and understand.
Who is it recommended for?
Ettercap is ideal for security professionals and network administrators who need to safeguard networks against man-in-the-middle attacks. Its open-source nature and comprehensive documentation make it accessible for both experienced and aspiring security experts.
Pros:
- Open-source security platform
- Specifically for identifying man-in-the-middle attacks
- Well documented with a large community
- Completely free
Cons:
- Is more of a specialized tool than a complete solution
You can visit their website to learn more or download the binaries on GitHub.
5. Intruder Automated Penetration Testing
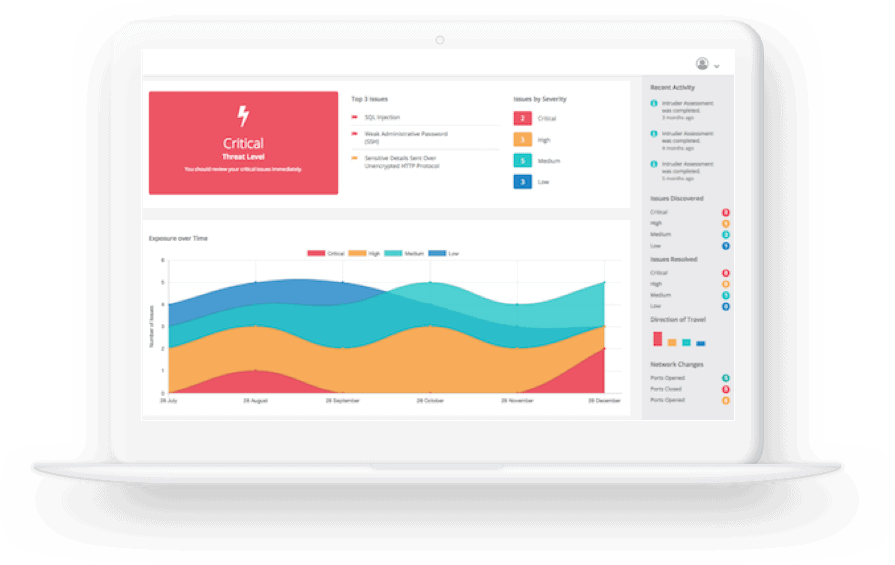
Intruder is a power-packed, automated penetration testing tool that identifies security vulnerabilities across your digital environment to prevent costly data breaches. It features an industry-leading scanning engine to offer in-depth security checks.
Key Features:
- Scans for SQL Injection and cross-site scripting in websites
- Checks common security issues in cloud environments
- Monitors public and private servers
- Provides in-depth network view to detect changes in exposed ports and services
- API Integration with your CI/CD pipeline to automate security processes
- Smart Recon feature lets you pay for only active systems
- Regular quality PDF reporting
Feature distinction
Provides actionable insights to help secure your organization.
Why do we recommend Intruder Automated Penetration Testing?
Intruder Automated Penetration Testing is highly recommended for its ability to comprehensively identify security vulnerabilities across digital environments. Its automated approach, coupled with an advanced scanning engine, makes it adept at detecting a range of threats, including SQL Injection and cross-site scripting. This tool is invaluable for organizations aiming to prevent data breaches and enhance their cybersecurity posture.

Who is it recommended for?
Intruder Automated Penetration Testing is ideal for businesses and IT professionals who require an efficient, automated solution for vulnerability scanning. Its capacity to monitor both public and private servers and to integrate with CI/CD pipelines makes it suitable for a wide range of users, from small businesses to large enterprises with complex digital infrastructures.
Pros:
- Can perform scheduled vulnerability scans automatically
- Can scan all new devices for vulnerabilities and recommended patches for outdated machines
- Excellent UI – great over high-level insights and detailed breakdowns
- Offers human-powered penetration testing as a service
Cons:
- Is an advanced security platform that can take time to fully explore
With more than 140,000+ security checks, Intruder protects your critical systems with best-in-class practices. You can start with a 14-day free trial.
6. Nessus
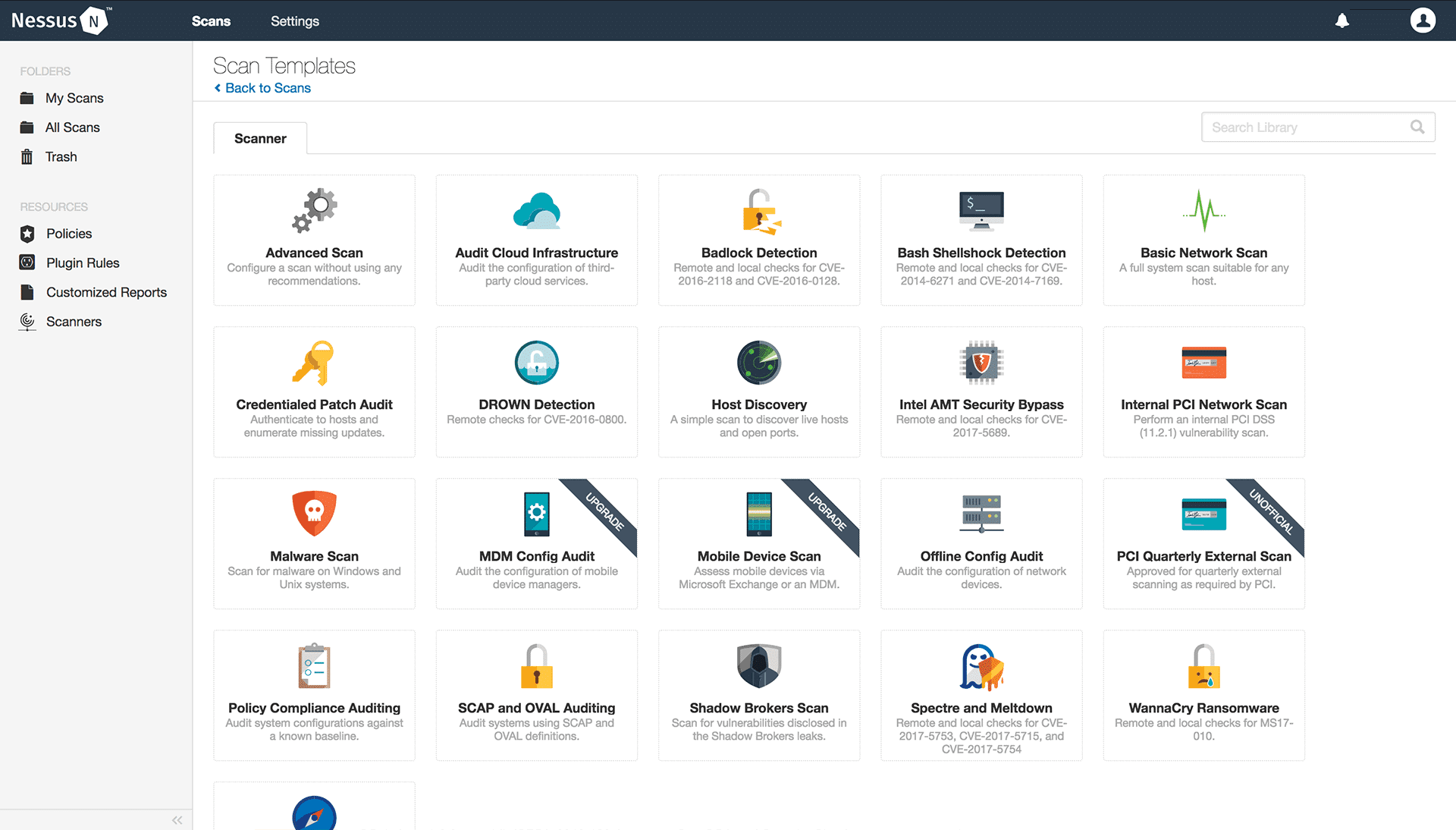
Nessus is a popular vulnerability assessment solution being used in the industry by more than 30, 000 companies now.
It is an exceptionally powerful and comprehensive pen-testing tool featuring deeper vulnerability coverage with over 61,000+ CVEs and over 152,000+ plugins. Besides, it implements six-sigma accuracy to deliver the lowest false positive rate in the market.
Key Features:
- Plugins are updated automatically in real-time to detect the latest malware and vulnerabilities
- Prebuilt templates and policies are available right out of the box
- Over 450+ compliance and configuration templates to help audit configuration compliance against best benchmarks
- Customizable reporting based on the type of vulnerabilities by host or plugin
- Live Results feature automatically assesses vulnerabilities offline with every plugin update, showing results based on your scan history.
- Grouped View feature gathers similar vulnerabilities together and displays them in a single thread to simplify prioritization and remediation
Why do we recommend Nessus?
Nessus is recommended for its extensive vulnerability coverage and accuracy in detecting threats. With over 61,000+ CVEs and 152,000+ plugins, it offers one of the most thorough vulnerability assessments available, making it an essential tool for comprehensive security analysis.
Nessus was meticulously designed by keeping security practitioners and their work in mind. Every single feature in Nessus is built to make vulnerability detection simple and intuitive.

Who is it recommended for?
Nessus is well-suited for organizations of all sizes seeking to perform detailed vulnerability assessments and compliance checks. Its user-friendly interface and minimal configuration requirements make it accessible for a wide range of users, including those new to vulnerability assessment.
Pros:
- Offers a free vulnerability assessment tool
- Simple, easy-to-learn interface
- Little configuration needed, 450+ templates that support a range of devices and network types
- Includes vulnerability prioritization
Cons:
- Offers limited remediation tools and options
- Could benefit from more integrations into other SIEM platforms
Nessus is best suited for compliance checks, sensitive data searches, and scanning websites and IP addresses. Find out more on their website.
7. SQLmap
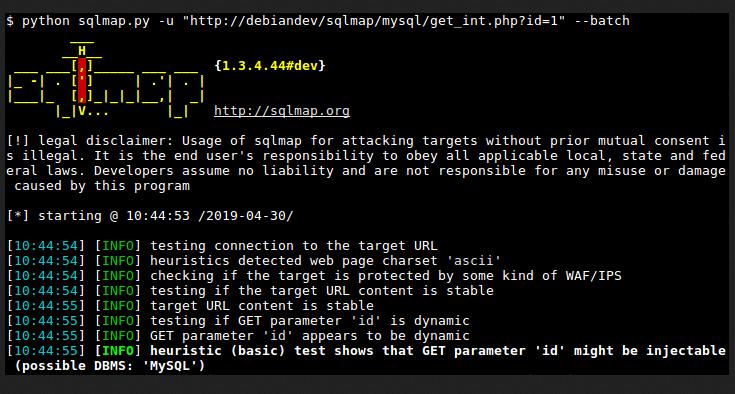
SQLmap is an open-source pen-testing tool that automatically detects and exploits SQL Injection vulnerabilities and takes over database servers.
Key Features:
- Supports Oracle, MySQL, Microsoft SQL Server, Microsoft Access, Presto, SQLite, MemSQL, IBM DB2, and a myriad of other database management systems
- Supports six SQL Injection techniques viz. UNION-based, boolean-based blind, stacked queries, out-of-band, time-based blind and error-based.
- Enumerates users, privileges, password hashes, databases, columns, tables and roles.
- Allows directly connecting to the database without going through a SQL Injection
- Automatically recognizes password hash formats and cracks them via dictionary-based attack.
- Allows to dump database tables completely or specific columns
- Can establish an out-of-band stateful TCP connection between the database server and attacker machine
Why do we recommend SQLmap?
SQLmap is recommended for its specialized ability to detect and exploit SQL Injection vulnerabilities effectively. It's an invaluable tool for database security, supporting a wide range of database management systems and offering comprehensive features for thorough testing.
Who is it recommended for?
SQLmap is particularly suitable for database administrators and security professionals focused on protecting databases from SQL Injection attacks. Its open-source nature and wide platform support make it accessible for a broad audience.
Pros:
- Completely free
- Open source transparent project
- Specifically caters to identifying SQL attacks
- Available for Windows, Linux, Mac OS, Free BSD
Cons:
- Is slightly outdated when compared to other VAPT tools
At the heart of SQLmap, there is a powerful detection engine along with various niche features and switches for over-data fetching from the database, database fingerprinting, accessing underlying files, and execution of commands on OS through out-of-band connections.
8. Zed Attack Proxy
OWASP ZAP is an integral part of the free OWASP community. It is an open-source, free web application scanner that is perfect for newbie developers and pen testers. It automatically finds vulnerabilities in your applications and offers various powerful APIs for security automation via a desktop interface. Developers can automate security regression testing and pen testing of the application in CI/CD pipeline.
Key Features:
- ZAP Marketplace includes numerous ZAP add-ons to enhance its functionalities
- Active and Passive Scanners
- Intercepting Proxy
- Brute Force Scanner
- Web Sockets
- Port Scanner
- Traditional and Ajax Spiders
- 4 modes available with customization
Why do we recommend Zed Attack Proxy (ZAP)?
ZAP is recommended for its comprehensive capabilities in scanning web applications for vulnerabilities. As an open-source tool, it offers extensive add-ons and features, making it a versatile choice for both automated and manual security testing of web applications.
Who is it recommended for?
ZAP is ideal for developers, beginner pen testers, and security professionals who need a free, open-source tool for web application security. Its adaptability makes it suitable for integration into CI/CD pipelines for continuous security testing.
Pros:
- Open-source and transparent project
- Specifically designed to scan web applications
- Can run manually or passively with scheduling scripts
- Completely free
Cons:
- Only for web application penetration testing
ZAP operates in a cross-platform environment and creates a proxy between your website and the client. Learn more on their site.
9. Wapiti
Wapiti is an authoritative security testing tool that helps you audit the security of your web applications and websites.
Key Features:
- Creates vulnerability reports in various formats including TXT, JSON, XML, HTML, and more
- Can suspend and resume scans or an attack
- Supports GET and POST HTTP methods for vulnerability check
- Buster module can brute force directories and file names on the target webserver
- Supports multipart forms and can inject payloads in filenames.
- Easily activate or deactivate attack modules
- Different verbosity levels
- Automatically removes one or more parameters in URLs
- Authentication via Basic, NTLM, Digest, or Kerberos
- Supports HTTP, HTTPS, and SOCKS5 proxies
- Extract URLs from Flash SWF files
- Can activate or deactivate SSL certificates verification
Why do we recommend Wapiti?
Wapiti is recommended for its ability to perform “black-box” scanning of web applications, effectively detecting a wide range of vulnerabilities. Its support for various attack methods and reporting formats make it a versatile tool for web security auditing.
It efficiently performs “black-box” scanning (without studying the source code) of the web application to look for scripts and forms where it can inject data. This is done by crawling into the web pages of the deployed application. As soon as it finds the list of forms, URLs and inputs, the Wapiti tool acts like a fuzzier and injects payloads to check if the scripts are vulnerable.
Who is it recommended for?
Wapiti is suitable for security specialists and web administrators who require a robust tool for auditing the security of web applications. Its command-line interface caters to users who prefer scriptable, customizable security testing.
Pros:
- Completely free tool
- Launches attacks to determine if they succeed – more reliable than proof of concept
- Supports numerous templated scans
- Available for Windows and Linux
Cons:
- No GUI – targeted more toward security specialists
Wapiti can smartly detect file disclosure, XSS injection, database injection, XXE injection, command execution detection, CRLF detection, SSRF (Server Side Request Forgery), Open Redirects, ShellShock (Bash bug), the existence of backup files that give out sensitive information, weak .htaccess configurations and so much more.
10. OWASP
OWASP stands for Open Web Application Security Project. It is a non-profit organization that works to enhance the security of software.
Leading flagship tools of the OWASP project are as follows:
- ZAP (Zed Attack Proxy): It is a free, open-source penetration testing tool with powerful APIs and multiple add-ons.
- OWASP Dependency Check: This SCA (Software Composition Analysis) tool can detect publicly disclosed vulnerabilities within a project’s dependencies. This is done by determining the presence of a CPE (Common Platform Enumeration) identifier for a specific dependency. If detected, the tool generates a report linking to the related CVE entries. The tool has a Maven plugin, command-line interface, a Jenkins plugin, and an Ant task.
- OWASP Web Testing Environment Project: OWASP WTE is a collection of powerful application security tools and documentation present in multiple formats including Linux distributions, VMs, ISO images, and cloud-based installations. The main goal of OWASP WTE is to make application security tools and documentation readily available for testers, developers, and trainers and easy to use. It is completely free.
Key Features:
- Free, open-source penetration testing tool
- Powerful APIs and multiple add-ons
- Software Composition Analysis capabilities
- Available on multiple platforms including Linux, Windows, Mac OS, BSD Unix
Why do we recommend OWASP?
OWASP is recommended for its comprehensive approach to enhancing the security of software through its community-led open-source projects and tools. The range of tools like ZAP and OWASP Dependency Check provide invaluable resources for securing web applications and managing software dependencies.
It comprises community-led open-source software projects, thousands of members, myriads of local chapters worldwide and prominent training conferences. Through these best-in-class practices, OWASP helps developers and technology experts to secure their web.
Who is it recommended for?
OWASP is ideal for developers, security professionals, and organizations committed to implementing best practices in web application security. Its wide range of tools and resources makes it suitable for educational purposes and practical application in securing software.
Pros:
- Open source transparent project
- Makes it easy to crawl lists and prioritize vulnerabilities
- Offers numerous plugins that extend its usability
- Available for Windows, Mac OS, Linux, and BSD Unix
Cons:
- Has a steeper learning curve than consumer-oriented products
This project comes with multiple tools and resources to pen test various protocols and software environments.
Wrap Up
Pen testing tools are a very crucial way of empowering your business’ IT integrity and securing the systems.
With these tools, developers, pen testers and trainers will be able to provide their organizations with the essential forewarning and proof-based information required to secure the IT systems.
Penetration Testing tools FAQs
What are the types of penetration testing?
There are several types of penetration testing, including black-box testing, white-box testing, and gray-box testing. Black-box testing simulates an attack by someone with no prior knowledge of the system, white-box testing simulates an attack by someone with full knowledge of the system, and gray-box testing simulates an attack by someone with partial knowledge of the system.
What are some common tools used in penetration testing?
There are many tools available for penetration testing, ranging from open-source utilities to commercial software packages. Some common tools include Invicti Security Scanner, Metasploit, Nmap, Wireshark, Burp Suite, and Nessus.
What should I expect from a penetration testing report?
A penetration testing report should provide a detailed summary of the testing process, including the tools and techniques used, the vulnerabilities identified, and the recommendations for improving security. The report should also provide an assessment of the risk posed by the identified vulnerabilities and prioritize them according to severity.
How can I prepare for a penetration testing engagement?
To prepare for a penetration testing engagement, you should ensure that your systems and networks are up-to-date with the latest security patches and updates, and that you have a clear understanding of the scope and objectives of the testing. You should also make sure that you have the necessary resources and personnel available to respond to any issues that may be identified during the testing.




