You may think your network is secure, but how do you know you’re really safe from certain threats? Network security auditing is key for protecting any business that utilizes networked resources. In this article, we’ll dive into some of the best network security auditing tools that help identify security risks, and get them closed fast.
Here’s our shortlist of the best network security auditing tools:
- N-able N-sight – EDITOR'S CHOICE Multi-platform management system that provides complete control and visibility of all your networks and devices. Start a 30-day free trial.
- ManageEngine Log360 – FREE TRIAL A SIEM system that includes a log manager to funnel source data through to the security analyzer. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine EventLog Analyzer – FREE TRIAL A collector and manager for log messages that includes templates for threat hunting and compliance reporting. Available for Windows Server and Linux. Start a 30-day free trial.
- Site24x7 – FREE TRIAL This cloud-based system monitoring platform includes a network configuration manager that protects network devices against tampering. Start a 30-day free trial.
- SolarWinds Network Configuration Manager This package enables the standardization of network device configurations, which are then backed up to be restored if an unauthorized change occurs. Runs on Windows Server.
- Intruder Cloud-based vulnerability scanner that performs monthly scans that can support multiple networks and clients.
- Nmap Classic security auditing tool that has been a staple among security professionals and hackers since the early 1990s.
- OpenVAS Free and open-source tool that offers detailed security auditing specifically for Linux environments.
- Metasploit One of the most popular open-source penetration testing tools on the market today.
- Netwrix Auditor Monitoring and configuration changes, permissions groups, and risk analysis across large networks.
- Kaseya VSA An RMM software that can run security risk audits as well as perform network discovery and endpoint management.
The Best Network Security Auditing Tools
What should you look for in a network security auditing tool?
We reviewed the market for network security auditing systems and analyzed options based on the following criteria:
- Network device configuration standardization
- Configuration backup and restoration to prevent tampering
- Log message collection, consolidation, and filing
- Searches for indications of intrusion
- Feedback system that can update firewall rules to tighten security
- Free trial or a demo package to enable the system to be assessed before purchase
- Value for money from a competent security tool offered at a fair price
With these selection criteria in mind, we looked for a range of network security services that, when adopted in combination will provide effective network security auditing.
1. N-able N-sight – FREE TRIAL
N-able N-sight is tailored for MSPs who manage multiple clients and want to offer auditing as a service.
Key Features:
- Remote Monitoring & Management (RMM): Provides instruments for problem evaluation related to networks, devices, and applications of clients via remote monitoring and management.
- Patch Management: Automates the process of updating the software of all monitored devices ensuring correct performance and security.
- Integrated Security Features: Antivirus, web guard, and email protection mechanisms to secure from viruses, hackers etc.
- Backup and Disaster Recovery: Cloud-based backup solutions for servers, workstations, and critical business documents.
Unique Feature
A multi-platform management system that provides complete control and visibility of all your networks and devices.
Why do we recommend it?
N-able N-sight is a comprehensive MSP solution that supports remote access, ticketing, and billing. Its many features simplify the complexity of monitoring many endpoints.
This cloud-based tool provides remote monitoring as well as risk management and threat detection across multiple sites or clients simultaneously. From a centralized dashboard, you can view risks on a per company, per facility, or a total view basis.
Details such as the number of problematic devices, backup status, and health checks can all be seen through a simple security overview that the dashboard provides. The entire platform is customizable, allowing you to create unique dashboard views for your network operation center, and other departments as needed.
Auditing templates help keep scans simple and pick up on specific compliance issues as well. For instance, there are built-in tools that can specifically scan and confirm if your network is currently HIPAA or PCI-compliant and provide a supporting report. The risk management section of N-able N-sight can scan and locate all Personal Identifiable Information (PII) and track how and where it moves across the network.
This level of risk management can stop specific information from leaving the network, as well as alerting when information is accessed inappropriately. Security permissions can be scanned on files and folders to uncover incorrect permissions on user accounts based on company records as well.
Lastly, N-able N-sight has a strong patch management system, which allows you to create a template of the patching process. So if there are updates you know that interfere with specific software you can copy these patch templates across to all of your clients in your MSP.
Who is it recommended for?
A good choice for internal IT teams that need a powerful Unified Endpoint Management (UEM) to manage all their end-user touchpoints from a single dashboard.
Pros:
- Unified MSP: Combines remote monitoring and management with professional services automation, offering a unified solution for managed service providers (MSPs).
- Expanded as Per Business Needs: Designed to scale with the growth of your business, accommodating an increasing number of devices and clients without losing performance.
- Amazing Automation Functionalities: Extensive automation capabilities, allowing MSPs to streamline operations and deliver services more efficiently.
- Intuitive and Customizable Dashboards: Customizable dashboards and reporting tools, enabling users to get insights tailored to their specific needs.
Cons:
- Advanced and Complex Features: Breadth of features and customization options can present a steep learning curve for new users.
Since N-able N-sight is a SaaS, installation is simple and billing is done through a subscription-based model. You can test out all of N-able N-sight features through a 30-day free trial.
EDITOR'S CHOICE
N-able N-sight is our top pick for a network security auditing tool as it helps IT professionals and managed service providers (MSPs) assess and strengthen network security. With its centralized platform, N-sight enables teams to monitor and audit networks efficiently, ensuring vulnerabilities are identified and mitigated quickly. The platform implements automated auditing, which allows businesses to continuously scan networks, devices, and systems for potential security gaps. This proactive approach minimizes the risk of unauthorized access and ensures that security policies are being followed. The tool also offers real-time monitoring, providing alerts on suspicious activities and potential threats. These services enhance an organization’s ability to respond swiftly to emerging security issues. N-sight integrates with a wide range of IT management tools, making it a versatile solution for businesses of all sizes. Its reporting functionality allows for easy documentation of security audits, helping companies maintain compliance with industry regulations like PCI DSS, HIPAA, and GDPR. This combination of real-time analysis, proactive auditing, and customizable reporting makes N-able N-sight an ideal choice for network security auditing, ensuring organizations stay secure and compliant.
Download: Get a 30-day FREE Trial
Official Site: https://www.n-able.com/products/n-sight-rmm/trial
OS: Cloud-Based
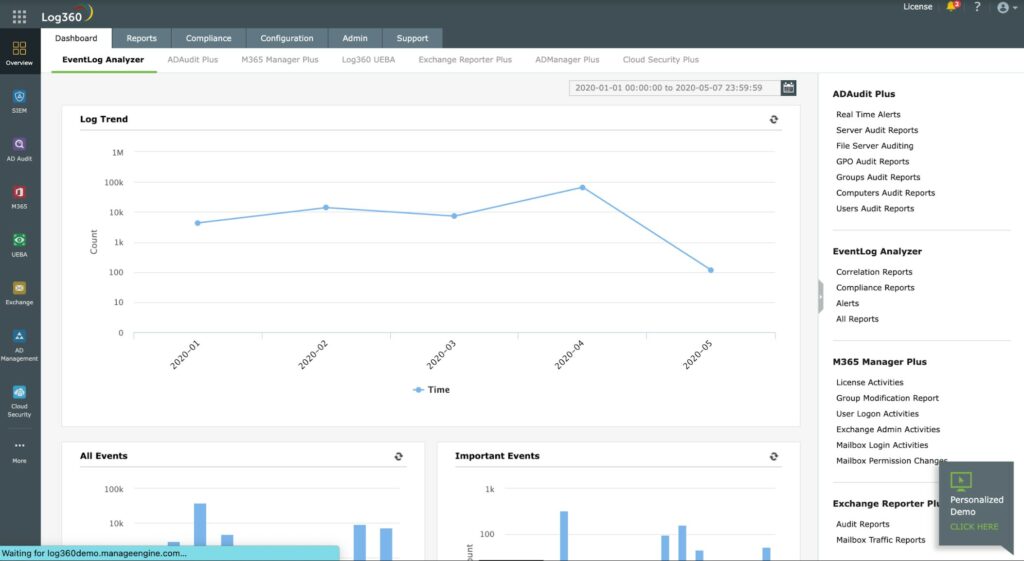
2. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a SIEM package that is bundled with a log management service. SIEMs mine logs for event information and so the quality of the SIEM is very dependent on the thoroughness of the log collection system. ManageEngine makes sure it feeds its SIEM good-quality log data.
Key Features:
- Comprehensive Log Management: Gathers, assembles, makes and analyzes the logs of several sources of inputs such as the servers, applications and security devices.
- Real-Time Event Correlation: Real-time collective assessment of variegated facts with correlation for critical incident identification.
- User and Entity Behavior Analytics (UEBA): Proactive against suspicious behavior based either on user activity or data patterns.
- Compliance Reporting: Provides predefined reports to help meet requirements for various IT compliance standards.
Unique Feature
ManageEngine Log360 comes with integrated DLP and CASB capabilities to enable security centers to quickly identify and respond to threats.
Why do we recommend it?
ManageEngine Log360 helps resolve many IT security challenges in log management, Active Directory auditing, and public cloud log management. Its simple and easy-to-use interface makes monitoring a breeze.
The log collector gathers data from more than 700 systems, including Windows events and Syslog messages from operating systems. Logs are sent to a central server where they are converted into a common format and filed.
The Log360 dashboard includes a data viewer and this displays live tail records as they are processed through the log server. The data viewer includes analytical tools and it is also possible to read in records from log files. It is possible to set up your own automated search rules that can run constantly and trigger alerts. For example, it is easy to use this service for file integrity monitoring.
The main automated data analysis and security research system in the Log360 package is the SIEM. The system identifies each user and device in the system and sets out a database listing each of these and establishing a baseline of normal activity per entity. This strategy is known as user and entity behavior analytics (UEBA). The behavior profiles form the basis for anomaly detection.
When the SIEM detects suspicious activity, it raises an alert, which is shown in the Log360 dashboard. You can also set up the service so that it forwards alerts as notifications through the ManageEngine ServiceDesk Plus, Jira, and Kayoko service desk ticketing systems.
The orderly storage of log files makes this is a good tool for compliance auditing. The package also includes compliance report templates for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.
Who is it recommended for?
Works well for organizations that have to meet stringent compliance requirements.
Pros:
- Centralized Log Management: Offers centralized log management capabilities, collecting, analyzing, and storing logs from various sources.
- Detection and Mitigation: Delivers real-time alerts on suspicious activities, helping to detect and mitigate security threats promptly.
- Meets Security Standards and Compliance: Assists in meeting compliance requirements with predefined reports for various regulations like GDPR, HIPAA, and more.
- Use UEBA: Detects anomalies and potential threats based on deviations from normal behavior patterns.
Cons:
- Steep Learning Curve: Initial setup and configuration can be complex, requiring a good understanding of the IT environment.
The Log360 software bundle installs on Windows Server and you can assess it with a 30-day free trial.
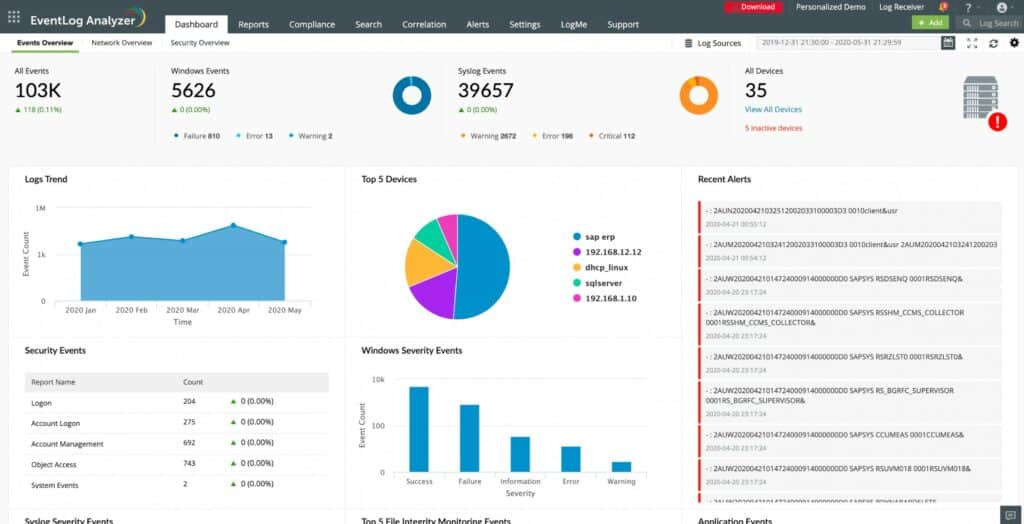
3. ManageEngine EventLog Analyzer – FREE TRIAL
ManageEngine EventLog Analyzer is a log management system that includes analysis tools. There isn’t a full SIEM in this package but you can set up your own queries to run automatically and add on rules to trigger alerts, creating a custom security auditing package. Usages include threat hunting, event correlation, and file integrity monitoring. Alerts can be sent as notifications by email, SMS, PagerDuty, and Slack.
Key Features:
- Event Log Management: Gathers, analyzes, and archives operating system logs of Windows, Unix/Linux servers, network appliances, and application platforms.
- IT Compliance Management: Customizable reports to aid in compliance with regulations like PCI DSS, HIPAA, FISMA, and more.
- Real-Time Alerting: Notifies administrators of critical events or patterns of interest as they occur, enabling rapid response.
- Log Forensics: Helps investigations and troubleshoots with effective search capabilities allowing parsing through log data over time.
Unique Feature
Collects, analyzes, and correlates data from the logs of different devices to provide a unified view.
Why do we recommend it?
ManageEngine EventLog Analyzer enables you to monitor the activities of servers, workstations, applications, and other devices, regardless of their geographical location. It comes with automated workflows for improving the efficiency of monitoring.
The package also includes log collectors and a central log server. The collectors gather data from more than 700 sources, which include operating systems, database management systems, and web servers.
The log server consolidates all logs into a standard format and displays newly-arrived records in a data viewer. This screen includes tools for searching, sorting, and parsing records, which includes a tagging system and a filtering mechanism. The service also has templates of searches that relate to specific types of analysis, such as threat hunting.
The EventLog Analyzer package includes templates for PCI DSS, FISMA, GLBA, SOX, HIPAA, and ISO 27001. The log manager rotates files and stores them in a meaningful directory structure, which facilitates compliance auditing.
Who is it recommended for?
Well-suited for network administrators who want to ensure their organization meets the compliance requirements of standards like SOX, HIPAA, PCI DSS, and more.
Pros:
- Advanced Event Correlation Features: Identifies and responds to complex security incidents.
- Supports Forensic Analysis: Detailed forensic analysis to investigate security incidents and troubleshoot issues.
- Customizable Reports: Highly customizable reports and dashboards for monitoring security and compliance.
- File Integrity: Be sure that your file integrity is not tampered with, includes file integrity monitoring that actively protects all your critical files.
Cons:
- Not Good with Large Volumes: Handling very large volumes of log data can sometimes affect performance.
ManageEngine EventLog Analyzer runs on Windows Server and Linux. The service is available in three editions: Free, Premium, and Distributed. The Free edition is limited to five log sources. The Premium edition will cover one site, and the Distributed system will centralize security tracking for multiple sites. You can access the Standard edition on a 30-day free trial.
4. Site24x7 – FREE TRIAL
Site24x7's Network Configuration Manager (NCM) is a powerful tool designed to help IT teams manage and automate network device configurations efficiently. It allows users to securely backup and restore configurations for network devices such as routers, switches, firewalls, and load balancers. By automating these tasks, Site24x7’s NCM reduces the risk of configuration errors.
Unique Feature
This network configuration manager is part of a wider package of system monitoring tools, so one purchase gets you all of the systems you need to run a network.
Why do we recommend it?
This tool ensures that network devices are always up-to-date with the correct settings. It also provides the ability to version control configurations, which ensures that administrators can easily track changes, roll back to previous versions if needed, and maintain a reliable record of network configurations.
One of the key features of Site24x7's Network Configuration Manager is its ability to automatically detect configuration changes across network devices. This feature is particularly valuable for maintaining consistency across large, distributed networks where manual tracking of changes would be impractical.
When a change is detected, Site24x7 alerts the relevant teams, allowing them to review the modifications and ensure they align with organizational policies and standards. The ability to monitor these changes in real-time also helps in compliance management, ensuring that devices are configured according to internal and external security regulations.
Site24x7 NCM supports automated configuration backups at regular intervals. This backup process ensures that if a device encounters a failure or needs to be replaced, the configuration can quickly be restored to its original state, minimizing downtime. The platform’s scheduled backup feature alleviates the manual burden of remembering to back up configurations and ensures that they are always safely stored for recovery if necessary.
This tool also allows for policy-based configuration management, enabling administrators to define rules for how network devices should be configured. This feature ensures that all devices adhere to predefined configurations, which improves security and operational efficiency.
The service supports both template-based and bulk configuration management, further simplifying the process for large-scale networks. With real-time monitoring, automated backups, policy enforcement, and change tracking, Site24x7's NCM provides an all-in-one solution for network configuration management, improving both network performance and security for businesses.
Who is it recommended for?
Site24x7’s Network Configuration Manager is recommended for IT teams and network administrators managing large or complex network infrastructures. It is particularly beneficial for organizations with multiple network devices, such as routers, switches, firewalls, and load balancers, who need to ensure configuration consistency, security, and compliance across their network.
Pros:
- Automatically backs up device configurations at regular intervals, ensuring that a recent backup is always available for recovery.
- Real-time alerts notify administrators of any configuration changes, helping ensure network consistency and security.
- Keeps track of configuration versions, enabling easy rollback to previous configurations in case of issues.
Cons:
- Not available as a standalone product
You can access the entire Site24x7 package without paying with the 30-day free trial.
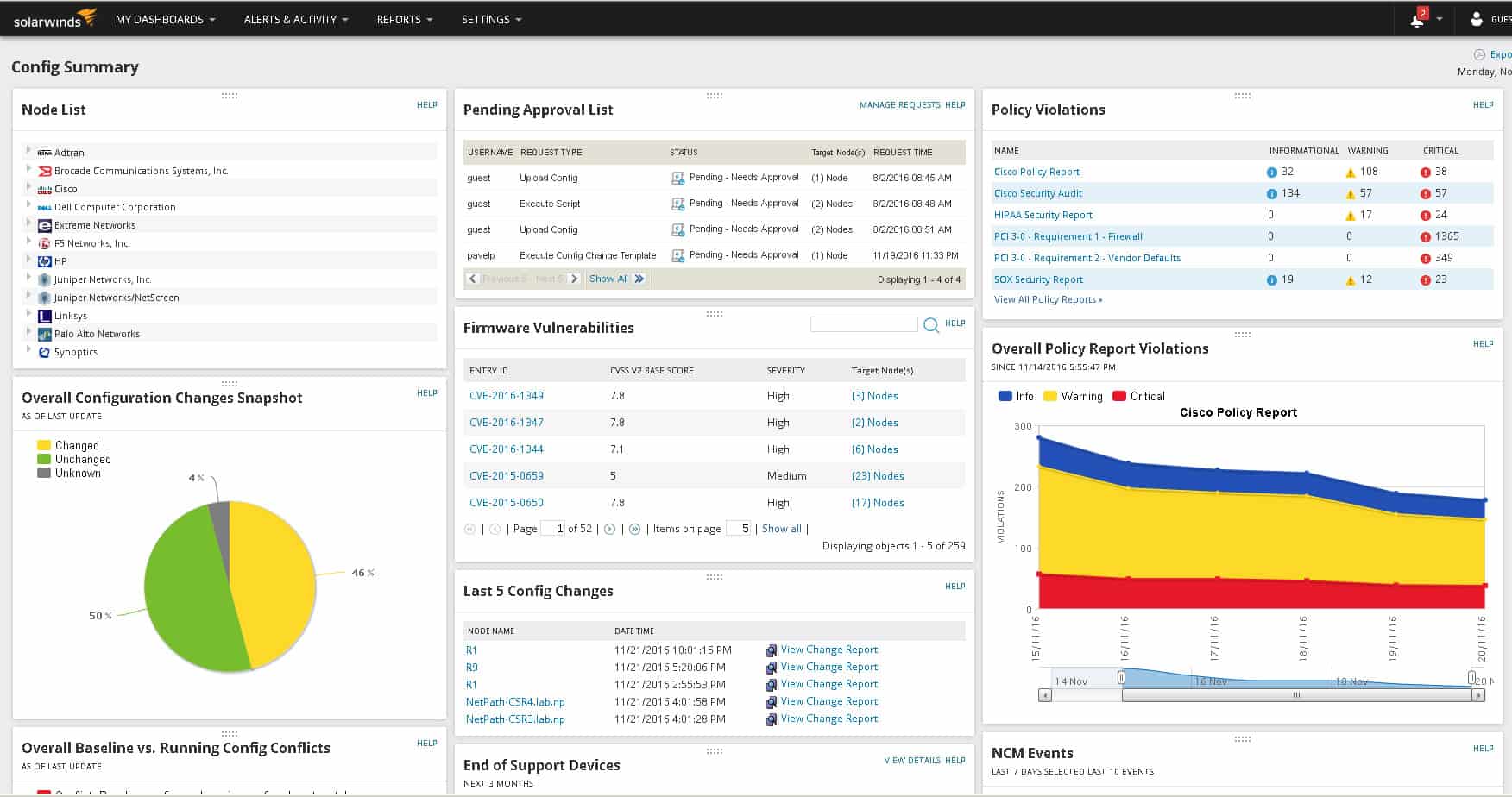
5. SolarWinds Network Configuration Manager
SolarWinds Network Configuration Manager (NCM) is designed for sysadmins to audit their network as well as deploy configuration changes to devices across the network. This combination of features allows you to not only make security-related configuration changes but also monitor for new and unauthorized changes on your devices.
Key Features:
- Automated Configuration Backup & Restore: Automatically maintains the configuration data of your network's devices, and the data will be saved if problems occur.
- Configuration Compliance Monitoring: Assists in ensuring that all network devices adhere to the company’s policies and external rules.
- Real-Time Change Notifications: Unauthorized, erroneous, or dangerous configuration changes are immediately flagged up.
- Bulk Configuration Changes & Rollouts: It is possible to use it to implement the same configuration change in many devices at one time, but it also saves time and prevents mistakes in configuring.
Unique Feature
Provides an in-depth understanding of policy changes and their impact. A highlight is its ability to upgrade obsolete Cisco iOS images.

Why do we recommend it?
SolarWinds Network Configuration Manager simplifies network compliance and saves time while ensuring quick disaster recovery. Also, it streamlines and automates network configuration management.
The tool automatically scans and monitors the network for devices, and allows you to decide how you want to manage the security of your network, and the devices that reside in it. From a centralized dashboard, Network Configuration Manager can detect and alert you to the most pressing security events right away, so there’s no guessing what to prioritize first.
What’s especially great about this tool is that you remain in control of everything. For instance, you can choose to either be alerted when devices are missing firmware updates, or have the updates automatically applied. Oftentimes systems and software can break when trying to apply new updates or security changes, creating additional work. With NCM, you’re completely in control of how each risk is handled.
The platform has a robust alerting feature that allows for alerts on new configuration changes, as well as new risks that are detected. The tool even has a rollback feature which gives you the option to quickly roll back to a certain configuration status of your choosing.
SolarWinds supports dozens of integrations so porting alerts over to your ticketing system is also a viable option if you run a NOC or helpdesk. Lastly, reporting can be set to produce quarterly reports or detail specifics on what a security audit has detected.
SolarWinds Network Configuration Manager is one of the best networking auditing tools in its class. It is truly built for medium size to enterprise-level networks that want to take a proactive approach to security, while still staying in control of how that is done.
Who is it recommended for?
Ideal for enterprises of all sizes.
Pros:
- Quick Recovery Using Automation: Automates the process of taking backups of device configurations, ensuring quick recovery from configuration errors or failures.
- Provides Alerts on Unusual Access: Instant alerts on unauthorized or unintended configuration changes, enhancing security and compliance.
- Detailed Reports and Audits: Detailed reports on compliance with policies and standards, helping organizations pass audits more easily.
- Allows Deployment to Multiple Devices: Enables the deployment of configuration changes to multiple devices simultaneously, saving time and reducing manual errors.
Cons:
- Costly for Small Businesse: While offering a robust set of features, SolarWinds Network Configuration Manager could be too expensive for small to medium-sized enterprises (SMEs).
You can try SolarWinds NCM on your network free through a 30-day trial.
6. Intruder
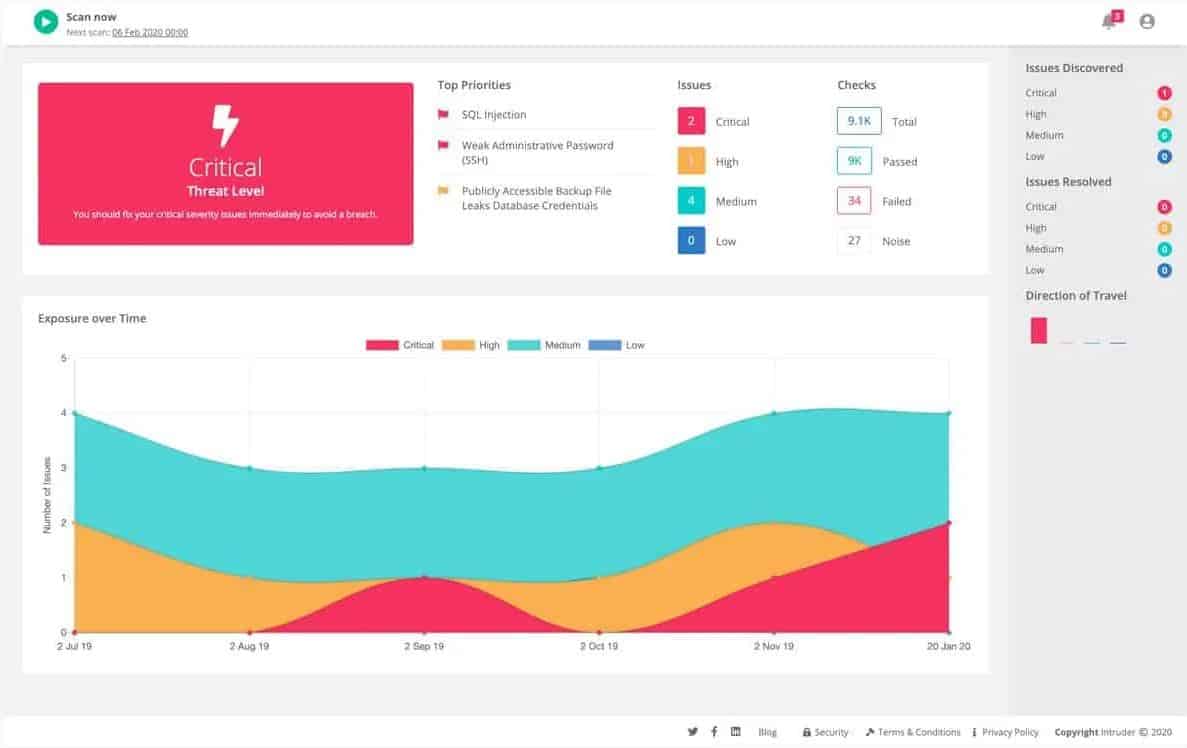
Intruder is another cloud-based vulnerability scanner that performs monthly scans that can support multiple networks and clients. During the initial setup, a full scan is run on the system to check for the latest exploits, vulnerabilities, and misconfigurations. Each scan covers over 10,000 known vulnerabilities and that number continues to grow as Intruder updates its backend database.
Key Features:
- Continuous Vulnerability Scanning: Continuously scans the systems and web applications that integrate to patch up and display regular reports.
- Prioritization of Risks: Risks that are highly critical which need immediate attention due to their threat level and exploitability will be highlighted.
- Compliance Checks: Offers scans and reports tailored to specific standards like PCI DSS, GDPR, and more to help maintain compliance.
- Integration Capabilities: Effortless connection to clouds and other tools work amazingly synchronously in terms of productivity.

Why do we recommend it?
Intruder automatically detects changes to identify new hosts or devices, and the likely vulnerabilities they may open up in your network.
The endpoint agent can also offer a unique look for inside threats, detecting configuration changes, and rogue activity coming from behind the firewall. Once a scan is complete, all of these details are elegantly mapped out through a simple and easy-to-understand dashboard. Threats and risks are automatically prioritized so you can see what needs to be resolved first.
The platform also gives sysadmins a unique overview of their security posture, allowing them to track their progress over time, and see what some of the most common and dangerous threats are to the network through a quick glance at the audit report.
Who is it recommended for?
A good choice for secure and agile IT teams.
Pros:
- Cloud-Based Vulnerability Scanner: Easily accessible and reducing the need for on-premises hardware.
- Proactive Security Scanning: Focuses on proactive security by scanning for new vulnerabilities and alerting users before they are exploited.
- Users can Prioritize Critical Things: Prioritizes vulnerabilities based on their severity, making it easier to address critical issues first.
- User-Friendly Interface: Designed with a user-friendly interface, making it accessible for businesses without extensive cybersecurity expertise.
Cons:
- Pricing Model: May be cost-prohibitive for small businesses or startups with limited budgets.
Intruder is a subscription-based service that comes in three packages, Essentials, Pro, and Verified. All of these plans include an automatic monthly scan, with the Verified plan including a live penetration testing team for additional support. You can try out Intruder free with a 30-day trial.
7. Nmap
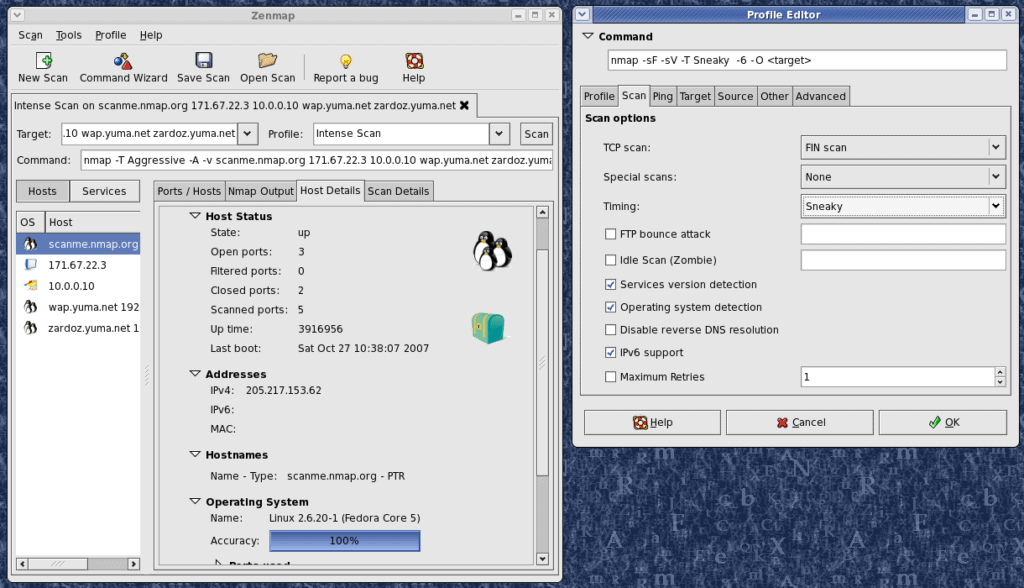
Nmap is a classic security auditing tool that has been a staple among security professionals and hackers since the early 1990s. This open-source tool has been kept alive through a dedicated community that has worked to add new features and eliminate bugs over the years. Unlike the other tools on our list, Nmap is a command-line tool, meaning you’ll have to learn syntax in order to properly use it.
Key Features:
- Network Discovery: Highly adept in identifying networked devices and their services, as well as the operating systems.
- Port Scanning: Scans for open ports on network devices to identify accessible services and potential vulnerabilities.
- Scriptable Scanning: Employs NSE (Nmap Scripting Engine) which could be featured for more customized reasoning as well as automation.
- Network Inventory: Generates a detailed inventory of network assets, helping in network management and security assessments.
Why do we recommend it?
Nmap analyzes packet sending and their responses. This information helps discover hosts and services on your network.
Rather than providing you a report based on what software thinks is a security risk, Nmap gives you raw information about your network’s port status, the type of services you’re running, and what operating system could be behind an IP address. Since Nmap requires you to read between the lines, this tool is more suited for pen-testers and dedicated sysadmins who want to take complete control of their network security auditing.
While the tool can seem primitive, it has powerful applications in the right hands. Lua scripts can be written to build out automatic scans and condition-based reports. Nmap is a great tool to deploy against your network when you already have a firewall in place, but really want to put your security to the test.
With Nmap, you’ll have full control over exactly what range of IP addresses and ports you scan, and even customize exactly how they are scanned in order to avoid detection from your network's security features. If command-line tools are not your preference, Nmap has a clone called Zenmap which offers almost identical features but through a graphical user interface.

Who is it recommended for?
Works well for network administrators of all organizations to gain more insights into the workings of their network and its devices.
Pros:
- Offers Complete Network Scan: Gives users a complete picture of hosts, open ports, and services being used by those connected to the network.
- Robust Port Scanning Options: Supports a variety of port scanning techniques, allowing you to scan TCP, UDP, and many other ports according to your target network and needs.
- Scriptable and Extensible: Nmap scripting engine allows users to create and share scripts to fulfill the network functionality.
- Platform Independent: Supports cross-platform compatibility, flexibly used by network admins and various security professionals to work seamlessly.
Cons:
- False Positives: Users say that due to a firewall, the tool sometimes generates false positives, it also detects open ports inaccurately, which is misleading for users.
The tool remains one of the most popular port scanning software due to its simple syntax and dedicated open-source community. Nmap is completely free and supports Windows, Linux, FreeBSD, and UNIX.
8. OpenVAS
OpenVAS is another free and open-source tool that offers detailed security auditing specifically for Linux environments.
Key Features:
- Vulnerability Scanning: Covers security threats and weaknesses within the users' network infrastructure.
- Open Source: Free and open source, which allows for its use, modulation and distribution by anyone.
- Extensive Plugin Database: Includes a vast database of Network Vulnerability Tests (NVTs), with thousands of tests available to detect known vulnerabilities in various software and systems.
- Regular Updates: Vulnerability feed for OpenVAS is regularly updated, therefore the tool can identify both the newly opening vulnerabilities and the security risks.
Why do we recommend it?
OpenVAS is a comprehensive vulnerability scanner that monitors open ports and services to which it has access. With such monitoring, it can identify known exploits and high-level web threats.
What makes OpenVAS so powerful is that its backend database is updated daily and includes over 80,000 vulnerabilities to test for. This massive open-source project has been maintained since 2009 by Greenbone Network, which also runs its own paid GSM appliances.
Who is it recommended for?
A good choice for organizations of all sizes, as it helps to stay on top of emerging threats.
Pros:
- Open-Source Tool: Being open source, it's freely available for anyone to use, modify, and distribute.
- Regularly Updated Database: Provides thorough vulnerability scanning capabilities with a regularly updated database of tests.
- Good Community Support: Benefits from strong community support, with contributions from security experts worldwide.
- Supports Flexible Customization: Allows for extensive customization to meet specific scanning needs and environments.
Cons:
- Less VCEs and Test Cases: Users notice that the OpenVAS tool supports fewer CVEs and test cases for testing and assessment compared to other network security tools.
Since this tool is open source, it will require a bit more learning and setup than some of the managed tools on this list. While OpenVAS is free, you’ll be on your own to learn how its features are set up, as well as troubleshoot any problems that arise along the way.
9. Metasploit
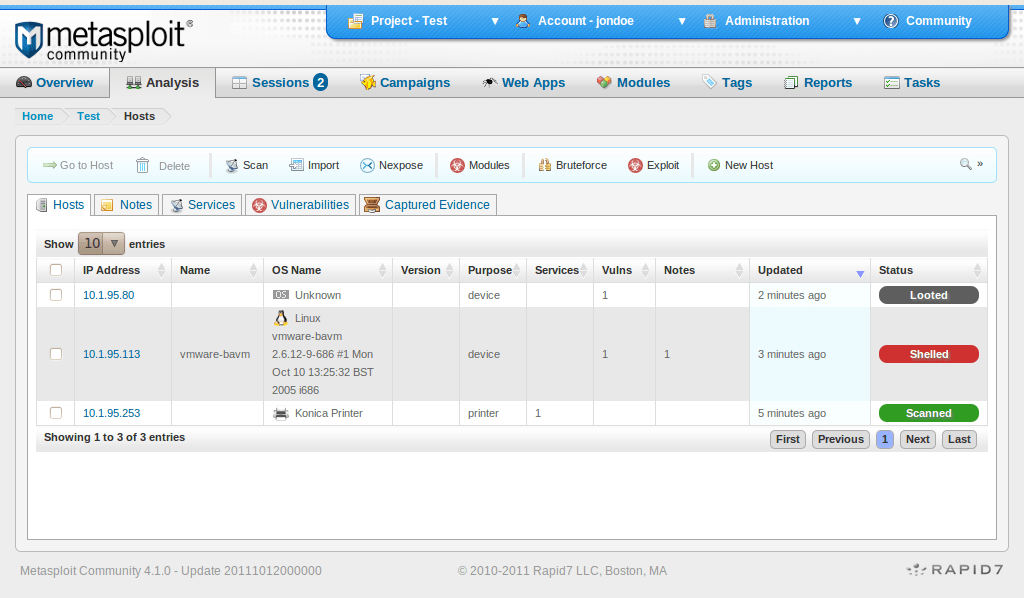
Metasploit is arguably one of the most popular open-source penetration testing software on the market today. The Metasploit framework allows you to attack your network from the perspective of the hacker, giving you a unique perspective into exactly how your security systems respond and handle specific threats.
Key Features:
- Exploit Development: Renowned for its exploit development capabilities, allowing cybersecurity professionals and attackers to develop and execute exploit code against a remote target machine.
- Payload Delivery: Offers various options for creating and delivering payloads to exploit vulnerabilities, including reverse and bind shells, meterpreter sessions, and more, facilitating deep post-exploitation analysis and control.
- Auxiliary Modules: Provides auxiliary functions such as scanning, fuzzing, and sniffing, making it a versatile tool for penetration testers.
- Community and Commercial Versions: Available in both free (Metasploit Framework) and commercial versions (Metasploit Pro), catering to both the open-source community and professional environments requiring advanced features.

Why do we recommend it?
Metasploit is a framework comprising a suite of tools for ethical hackers to assess the security of a network.
The framework comes with over 500 payloads you can use in conjunction with exploits to attack your network and put your systems to the true test. A massive open-source community has kept Metasploit one of the most popular security auditing tools, and now includes integrations into tools such as Nmap and Nessus Pro. This allows you to import results from port scans and other tests directly into Metasploit.
Like Nmap, Metasploit is truly geared towards professionals in their field who would rather analyze raw threat data than receive a summary generated by another piece of software. The great thing about Metasploit is that most dedicated techs can sit down and learn how to use the system in an afternoon if they’re so inclined.
Who is it recommended for?
Often used by security engineers for penetration testing and also to create security tools and exploits.
Pros:
- Variety of Testing Possibilities: Supplied with multiple exploits from various platforms and applications, it's a tool that offers plenty of possibilities for pen testing.
- Easily Accessible Help: Supported by a large user base and teams involved in development, containing many guides and tips.
- Seamless Working with Almost All Security Software: Works smoothly with most other security programs, accelerating its functions and efficiency for security analysis in different settings.
Cons:
- Extensive Features: Diversity of features and options can be confusing for a beginner who is preparing to enter the cybersecurity field.
Metasploit is also available as a paid tool, called Metasploit Pro. This pro version includes features like remote API integrations, OWASP vulnerability testing, automated workflows, and a simple web interface. The Metasploit Framework is completely free, while the pro version can be tested free for 14 days.
10. Netwrix Auditor
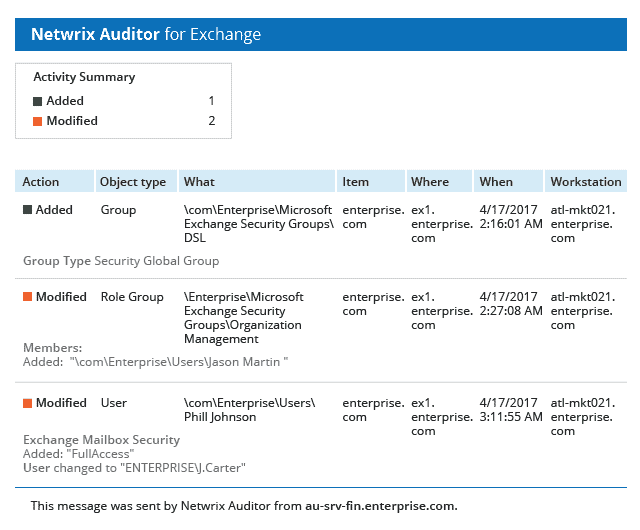
Netwrix Auditor does an excellent job at monitoring and configuration changes, permissions groups, and risk analysis across large networks. What’s unique is you can view a complete audit chain of exactly who changed what, and when that change took place.
Key Features:
- Visibility and Analysis: Provides visibility into changes, configurations, and access in hybrid IT environments to ensure security and compliance.
- Risk Assessment: Identifies and prioritizes security gaps, allowing organizations to focus their efforts on the most critical vulnerabilities.
- Data Classification: Classifies sensitive data across various platforms, enabling organizations to better protect critical information and comply with regulations.
- Alerting and Reporting: Detailed alerting and reporting capabilities, helping organizations to quickly respond to potential threats and meet compliance requirements with detailed audit trails.

Why do we recommend it?
Netwrix Auditor provides greater control over configuration changes. It also analyzes user behavior and mitigates risks in networks.
The system not only detects risks, but also identifies when someone is attempting to scan your network with a port scanner, or attempting logins into an account that continuously fails. These features are both ideal for detecting and stopping outside and insider threats alike.
A simple dashboard can visually alert you to these changes and attempts through a color-coded system and will display red when an alert is triggered. This is great for network operation centers, and can be displayed on a centralized screen. Tickets can also be generated based on events, or email alerts can be sent out to specific groups.
Through the Netwrix Auditor, you can configure automated responses when a certain alert is generated, which is incredibly powerful and effective when done correctly. For example, you can write a script that disables an account automatically if it is behaving abnormally or making configuration changes that fall out of its scope.
If a condition in the automation fails, you can then choose to generate a helpdesk ticket. Automation can drastically reduce the number of tickets generated when implemented and tested over time.
Who is it recommended for?
Ideal for hybrid environments where data protection and visibility are challenging.
Pros:
- Tight Network Security: Studies in-depth reports on changes, settings, and every kind of access in IT environments to tighten security and compliance.
- Effective Risk Assessment: Identifies and prioritizes security gaps.
- Supports Locating and Disposing of Data: Assists in locating and disposing data that is sensitive and ranges from multiple platforms.
- Auto-Generated Reports: Regulates and auto-generates the reports, allowing the company to save time and ensure accuracy.
Cons:
- Unsuitable for Smaller Organizations: Possibly unaffordable and too complex for smaller organizations that may have limited IT supplies to do so.
The entire platform is based on the REST API framework which makes it a great choice for those who need a security auditing tool that can integrate with other platforms and solutions. There is a completely free community-based version of this software, but for more of the robust alerting capabilities, you’ll need to buy the full edition. You can download and test the software through a 20-day free trial.
11. Kaseya VSA
Kaseya VSA is an RMM software that can run security risk audits as well as perform network discovery and endpoint management. The network discovery component automatically stores device and network information alongside security and patching information. Global security and patching policies can be set per client, and deployed at scale, making Kaseya VSA a great option for MSPs and large enterprises with multiple networks.
Key Features:
- Remote Monitoring and Management: Designed for remote monitoring and management of IT infrastructure, enabling IT professionals to manage servers, desktops, and mobile devices from a single console.
- Automation: Powerful automation capabilities that allow IT teams to streamline daily tasks and processes, reducing manual work and improving efficiency.
- Patch Management: Provides comprehensive patch management capabilities to ensure software across the network is up to date and secure against vulnerabilities.
- Integrated Backup and Disaster Recovery: Ensures critical data is protected and can be quickly restored in the event of an incident.

Why do we recommend it?
Kaseya VSA is a centralized tool for managing all IT operations, including ticketing, auditing, monitoring performance, and reporting.
The entire platform is incredibly customizable, which is ideal for sysadmins who like to leverage auditing tools but still have a great deal of control over exactly how audits are run, and where that information is stored. A command and control dashboard allows sysadmins to track deployed agents, devices, and their risk status.
Condition and policy-based automation allow patching and security tasks to be carried out automatically, which again makes Kaseya a great tool to deploy when looking at scaling security services behind a dedicated team of technicians. The platform even has an Automation Exchange which is a community that shares over 500 different scripts and out-of-the-box configurations you can deploy right away.
Who is it recommended for?
Works well for businesses of all sizes and across all industries.
Pros:
- Remote Manage: Allows IT teams to remotely manage a wide range of devices, improving efficiency and response times.
- Automation: Provides automation capabilities for routine IT tasks, reducing manual efforts and potential errors.
- Integrated Solutions: Includes integrated solutions for backup and disaster recovery, ensuring data protection.
- Patch Management: Facilitates effective patch management, helping to keep software up-to-date and secure.
Cons:
- Inconvenience with Mac Users: Mac OS users reported that the tool asked to log in with engineer credentials when they installed it for the first time.
Kaseya VSA is truly tailored for larger organizations and MSPs who plan to offer network security auditing as a part of their core services. With this said, accurate pricing is currently not publicly available. For additional information regarding pricing, contact the Kaseya sales team. You can test out Kaseya VSA in your network for free through a 14-day trial.
Conclusion
For almost any size network, SolarWinds Network Configuration Manager can provide simple yet detailed security auditing along with configuration management in a way that allows organizations to scale with the tool. N-able N-sight is equally as powerful and runs via the cloud.
For more hands-on security tests that require customized and detailed attacks, the Metasploit Framework allows you to switch to the side of the attacker to see how your network truly holds up against different types of attacks.
Lastly, budget-conscious departments can leverage OpenVAS for powerful network auditing if the proper IT staff are in place to learn and become dedicated to the platform.
Do you have a favorite network security auditing tool? Let us know what it is and why you love it in the comments below.
Network Security Auditing Tools FAQs
What is network security auditing?
Network security auditing is a process of assessing and analyzing the security of a network to identify vulnerabilities, risks, and threats.
Why is network security auditing important?
Network security auditing is important because it helps organizations identify and address potential security issues before they can be exploited by attackers. It can also help organizations comply with regulatory requirements and industry standards.
What are the steps involved in a network security audit?
The steps involved in a network security audit may include:
- Planning and scoping the audit
- Conducting a vulnerability assessment
- Analyzing network traffic and logs
- Reviewing security policies and procedures
- Assessing physical security measures
- Identifying and prioritizing security risks
- Developing recommendations for risk mitigation
What is the difference between an internal and external security audit?
An internal security audit is conducted by an organization's own security team or a third-party provider, while an external security audit is conducted by an independent third-party provider. External audits may provide a more objective assessment of an organization's security posture.
Related Posts: