With the rapid increase in data and devices, enterprises need to protect confidential data and prevent expensive data breaches. We often share files with clients and other team members in an enterprise for better communication and proper functioning. What if some unauthorized person tries to hack your data or steal information from your system when transmitting data.
To protect your confidential data from such theft and malware practices, we use data encryption tools that convert all the readable data into an encoded form. This encrypted information enhances communication security and is hard for anyone to crack. Also, no unauthorized person can access these folders or files without valid credentials. The endpoint encryption supports monitoring endpoints and protects all sensitive information at various network endpoints. It also helps store and create backs up encryption keys for security purposes.
In this post, we're going to define data encryption, its benefits, and the best tools to protect and encrypt your data. Then, check out some of the best endpoint encryption tools available in the market and how they can save your information against cyber-attacks and theft.
Here is our list of the best endpoint encryption software solutions:
- McAfee Complete Data Protection One of the most popular and powerful endpoint encryption software that helps prevent data loss and theft.
- Sophos SafeGuard A trusted encryption software solution that keeps your data secure against data breaches and unauthorized access.
- Microsoft BitLocker A simple and easy to set up encryption tool that allows access to only users with the correct encryption key.
- Trend Micro Endpoint Encryption Another powerful software solution that encrypts devices, USB drives, and other removable media information and keeps data safe from unauthorized users.
- Check Point Full Disk Encryption Software Blade is a Windows and Mac OS compatible tool that provides 256-bit AES encryption and supports multi-factor pre-boot authentication.
- NordLocker is one of the trusted that protects both your computer files as well as cloud storage.
- Dell Data Protection A comprehensive solution that enforces encryption policies for multiple endpoints without end-user intervention.
- IBM Security Guardium Data Encryption A complete suite of security tools that provides encryption and decryption without affecting performance.
What Is Data Encryption?
Data encryption is a security method where confidential information is converted into an encoded piece of knowledge accessible only by an authorized user. This technique keeps your data secure at all times. Also, only the user with the correct encryption key can decrypt the data and find the information. These encrypted data are also called ciphertext or encryption algorithms, unreadable to any person without permission. The only purpose of keeping data encrypted is to secure sensitive data and keep it protected from any malicious or negligent party. It is not easy to break the code and convert data into readable format. You will require large amounts of computing power to crack the encoded information.
It adds security and ensures no file can be stolen from your device. Many individual users and large corporations use data encryption methods to protect sensitive data. We, as users, share information daily via the Internet. Thus, there are high chances of data stealing by hackers. To prevent this, the data encryption method converts readable data into incomprehensible text accessible only by users having a cryptographic key.
Benefits of Encryption Software
Every organization manages a massive amount of data, including PII or financial data, that must be kept secure. However, transferring sensitive data from one location to another over a network can be risky. This is where the data encryption method comes into practice. It saves your data from leakage or hackers. Here are a few more benefits of using the encryption software for storing and transmitting data:
- Data Encryption Tools can be applied across multiple devices.
- It allows more secure communication.
- It helps protect your data from getting lost, intercepted, or stolen
- The software supports data integrity and protects intellectual property.
- The encryption software ensures compliance.
- It helps maintain data privacy.
What to look for in Encryption Software?
One must look for various features when purchasing data encryption software. However, make sure to primarily check on the Password strength indicator as it helps reduce vulnerabilities led by weak passwords. This feature also stores your information securely and suggests strong passwords automatically. Often many employees choose an easy-to-remember and specific password for applications. However, it can be easy for hackers to crack the code. This is why make Password strength indicators your priority.
Also, do not miss the virtual document shredding functions. This feature ensures that the deleted information cannot be scraped from the disk.
Further, can the encryption software manage your data or transfer large files? Is it possible to encrypt files from a central location? Finally, is the encryption software compatible with popular on-premises and cloud platforms?
Check some of these essential features and factors before buying an encryption solution.
The Best Endpoint Encryption Software Solutions
Sharing and receiving data via different channels can lead to data breaches. Thus, the best way to protect your confidential files is to convert them into an encoded form. Encrypting information will help protect all your data in transit or at rest. Only an authorized user can access this information using a password. Thus, to help you with it, we have penned out some of the best Encryption software solutions to secure your data.
1. McAfee Complete Data Protection
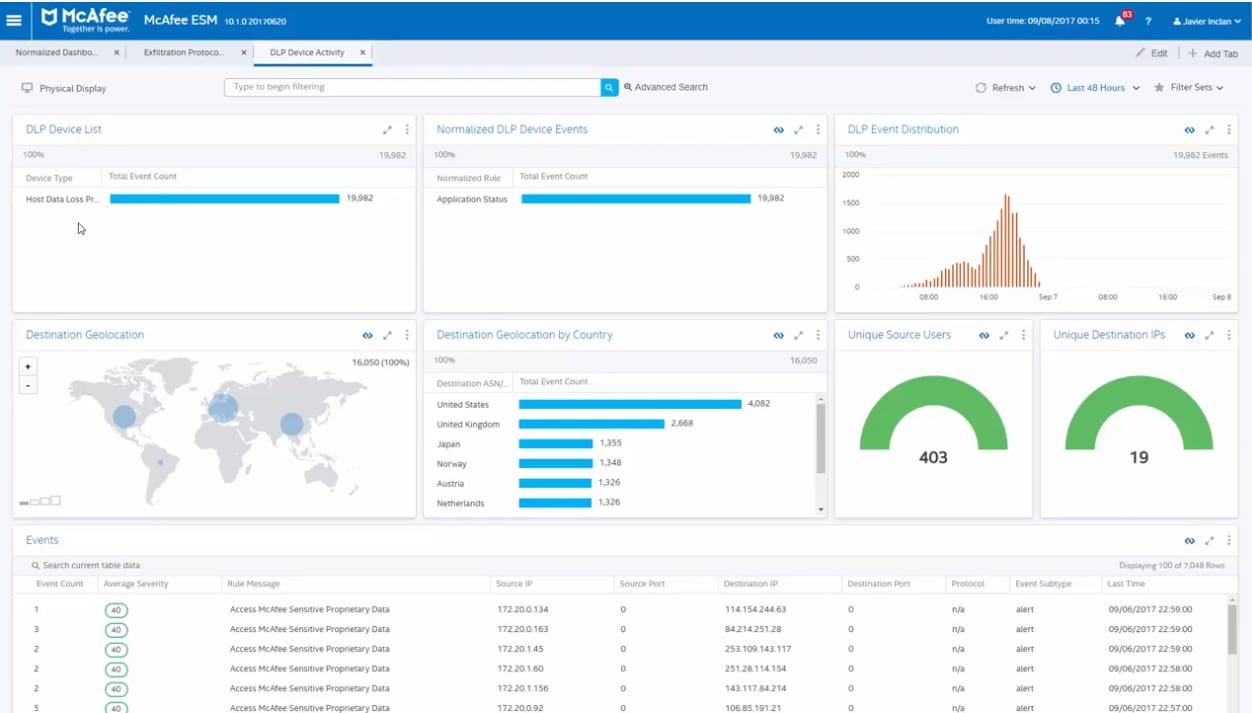
McAfee Complete Data Protection is a robust endpoint encryption software that prevents data loss and theft. The software comprises full-disk encryption and device control features that add more visibility and control over your data. The Endpoint Encryption Software Solution supports centralized policy management for remote access. It also enforces and implements policies that restrict the way employees transfer sensitive data through various channels, such as USB drives. You require no additional software to access the files from any location with McAfee Complete Data Protection. In addition, the software always keeps data encrypted and secure.
Key Features
- It allows you to monitor and regulate how the staff uses and transfers data.
- It keeps all the confidential secure and encrypted.
- No requirement for additional software to access encrypted data from any location.
It allows you to monitor real-time events compiled via various advanced reporting tools. It does not matter where you made edits or saved the data McAfee Complete Data Protection helps keep all your files encrypted.
Pros:
- Excellent interface – highly customizable
- Designed for enterprise use
- Can work well with existing data loss protection systems
- Automatically encrypts data as it moves through the network
Cons:
- Designed specifically for businesses. Not created for non-technical users
Website Link: https://www.mcafee.com/enterprise/en-in/products/complete-data-protection.html
2. Sophos SafeGuard
Sophos SafeGuard is another trusted encryption product that centrally manages full disk encryption. The software is highly compatible with platforms, such as Windows and macOS. Sophos SafeGuard Enterprise keeps your data secure against data breaches and unauthorized access. It comprises various features, including granting encrypted file access depending on the endpoint's security state, BitLocker mobile recovery, or FileVault recovery keys.
Key Features
- It instantly denies key access from any unauthorized device or user.
- It helps manage keys and recovery functions of Windows and macOS.
- It protects your data from any location.
Sophos SafeGuard Encryption Solution requires no deployment or configuration. Sophos SafeGuard has a password-protected HTML wrapper that allows only authorized users to access confidential files. It also can provide compliance monitoring and reporting. One can secure their devices in minutes with Sophos SafeGuard as it is easy to set up and run.
Pros:
- Simple yet powerful admin console
- Ideal for large enterprise networks
- Quick onboarding – only takes a few minutes
- Can manage keys across multiple operating systems
Cons:
- Can take time to fully explore all options
Website Link: https://www.sophos.com/en-us/products/sophos-central
3. Microsoft BitLocker
Microsoft BitLocker is a native security tool compatible with Windows platforms. It supports full-volume encryption and allows only users with the correct encryption key. Microsoft BitLocker uses Trusted Platform Module (TPM) to create a recovery key. This key or pin allows only valid users to access the device. One can encrypt the entire drive with Microsoft BitLocker and save keys to Active Directory.
Key Features
- It is available on the Windows platform and removable storage drives.
- It encrypts your entire drive using the TPM module
- The initial setup of Microsoft BitLocker is straightforward for encryption.
- It is one of the highly stable endpoint encryption tools.
- Microsoft BitLocker is an easy-to-setup encryption tool with no additional licensing cost.
Microsoft BitLocker is an easy-to-set-up encryption tool that uses a 128-bit or 256-bit key to protect data. Also, the encryption tool includes no additional licensing cost.
Pros:
- Already built into modern Windows operating systems
- Highly convenient for full disc encryption
- A great solution for home users and small networks
Cons:
- Lacks enterprise features, not the best choice for larger networks
Website Link: https://docs.microsoft.com/en-us/windows/security/information-protection/bitlocker/bitlocker-overview
4. Trend Micro Endpoint Encryption
Trend Micro Endpoint Encryption, is another software that encrypts all information and keeps data safe from unauthorized users. It encrypts devices, USB drives, and other removable media information. Also, the software solution centrally manages full disk encryption, removable media, folder, and file encryption with a single management console and additional security products. In addition, trend Micro Endpoint Encryption prevents unauthorized access and provides activity monitoring. It also provides reports with a detailed view of how malicious attackers act and access the system.
Key Features
- It provides data encryption on various devices, removable media, and mobile devices.
- It provides automatic and transparent encryption without impacting the performance.
- Trend Micro Endpoint Encryption provides policy-based encryption and maintains compliance.
- Trend Micro Endpoint Encryption makes it easy to deploy and configure encryptions.
- It provides advanced Reporting and Auditing features.
- Supports Pre-Boot Authentication
- Secures your data with certifications, including FIPS 140-2 certification.
Pros:
- Can encrypt virtually all hard drives and removable media
- Centralized management for a simple view of your device security
- Offers advanced reporting capabilities as well as automated audits
- Is FIPS 140-2 Certified
Cons:
- Better suited for larger networks
Website Link: https://www.trendmicro.com/en_in/business/products/user-protection/sps/endpoint/endpoint-encryption.html
5. Check Point Full Disk Encryption Software Blade
The Check Point Full Disk Encryption Software Blade is a trusted endpoint encryption tool that encrypts all readable data on a hard drive. As a result, even if the device is off, attackers cannot tamper with the OS or recover confidential information. The tool is compatible with Windows and Mac OS X platforms. In addition, it provides 256-bit AES encryption and supports multi-factor pre-boot authentication.
Key Features
- The software protects data from unauthorized access if the device is lost or stolen.
- It provides security certifications for compliance.
- The encryption software is compatible with platforms like Windows and Mac OS X.
- It proves fast and quick deployments.
- It centrally manages endpoint solutions via a single console.
- It has an intuitive user interface and provides Full Disk Encryption
- The tool provides multi-factor authentication and, as a result, card support.
The tool allows easy and quick execution of encryption and decryption operations with its deployment process. The Check Point Full Disk Encryption Software Blade allows restoring files to their original folders. It is an excellent tool for enterprises. With its reporting feature, one can detect malware and analyze its work. It keeps your data secure and supports Disc Encryption, Anti-Malware, and a VPN Blade.
Pros:
- Simple interface – easy to use
- Compatible with both Windows and Mac operating systems
- Offers full disk encryption
- Includes one-click file restoration
Cons:
- Better suited for SMBs
Website Link: https://www.checkpoint.com/products/media-encryption/
6. NordLocker
NordLocker is one of the latest encryption tools with cloud storage that uses state-of-the-art ciphers and algorithms to deliver end-to-end encryption. NordVPN's latest design is a file encryption software providing 256-bit AES encryption enough to secure large sets of data. If 256-bit AES encryption is not enough, NordLocker delivers the addition of 4096-bit encryption. NordLocker is one of the trusted and best endpoint encryption software solutions as it protects both your computer files as well as the cloud.
Key Features
- It is easy to add or remove files with its drag-and-drop features.
- It is easy to access files from any location with Nordlocker.
- NordLocker supports a zero-knowledge policy.
- It works best with macOS and Windows platforms.
Nordlocker has an intuitive user interface, drag-and-drop features, synchronizes files via a private cloud, automatically creates a backup, supports zero-knowledge policy, and more. In addition, it is highly compatible with macOS and Windows platforms.
Pros:
- Offers end-to-end encryption for files and devices
- Easy to use – drag-and-drop files for encryption
- Supports both Windows and Mac operating systems
- Leverages powerful 4096-bit encryption
Cons:
- Can take time to explore all features on the platform
Website Link: https://nordlocker.com/
7. Dell Data Protection
Dell Data Protection is a comprehensive solution that detects and protects data on various endpoints, devices, external media, and operating systems. It comprises robust manageability and centralized management capabilities. In addition, Dell Data Protection Encryption uses a single management console to enforce encryption policies for multiple endpoints without end-user intervention.
Key Features
- It supports quick and easy deploy encryption across multiple OS.
- It provides a fast and efficient path to compliance.
- Dell Data Protection allows users to easily access and share data without disruption.
Dell Data Protection Enterprise version supports multifactor authentication and smart cards. In addition, it allows central management of data for full-disk encryption (FDE).
Pros:
- Highly enterprise-focused platform
- Includes both manual BDR and automated backups
- Offers replication for both VMDK and RDM
- Includes a suite of BDR tools for practically any configuration
Cons:
- Specifically caters to enterprises – not ideal for smaller networks
Website Link: https://www.dell.com/support/home/en-in/product-support/product/dell-data-protection-encryption/drivers
8. IBM Security Guardium Data Encryption
IBM Security Guardium Data Encryption is a highly scalable solution that performs encryption and decryption without affecting the performance. It is a complete suite of security tools that monitors operations, provides compliance reporting, data discovery, and more to protect and manage data. The software also comprises data masking and centralized key management capabilities. It also includes critical rotation features, granular encryption of files and folders. It is an all-in-one solution for enterprises that need a data security solution.
Key Features
- Its intuitive web-based interface helps lessen administrative effort.
- It allows you to protect and manage data across various environments.
It is easy to secure your data from any location with IBM Security Guardium Data Encryption. The software solution saves operations and is deployable across on-premise and hybrid multi-cloud environments.
Pros:
- Highly customizable encryption options that support multiple algorithms
- Supports both structured and unstructured data
- Cross compatible with Linux, Windows, and MacOS
- Features built-in compliance management tools
Cons:
- The platform comes with many different options that take time to discover and learn
Website Link: https://www.ibm.com/in-en/products/guardium-data-encryption
Final Thoughts
Endpoint encryption software helps protect sensitive data within or outside the network. It encrypts all information to protect against cyber-attacks and reduces administrative overhead. Nowadays, many encryption software solutions are available that enterprises can use to safeguard vital information. McAfee Complete Data Protection, Microsoft BitLocker, Check Point Full Disk Encryption Software Blade, NordLocker, IBM Security Guardium Data Encryption are a few popular and trusted endpoint encryption software solutions. This software makes your information unreadable for unauthorized users. They also provide better reporting to ensure compliance and detect how malware performs. It further assists with encryption key management and monitoring endpoints.