Cloud security has become an essential part of every organization's infrastructure. Given the nature of cloud operations, you need a comprehensive strategy that's backed by advanced tools to implement the necessary security measures in your cloud infrastructure. This is where Cloud Security Posture Management (CSPM) tools come in.
Here is our list of the best CSPM tools:
- Aikido A SaaS platform of security testing systems for Web applications and SaaS packages that includes a CSPM. Use this service for complete application preventative vulnerability scanning.
- Datadog Continuously scans the configuration across cloud accounts, hosts, and containers to identify any gaps or vulnerabilities. This streamlines deployment and enhances the overall security of your cloud infrastructure.
- CrowdStrike Falcon Horizon This CSPM tool detects misconfigurations as they occur, so you can reduce its security implications. Further, it ensures compliance, eliminates blind spots, and works well across multiple cloud platforms.
- CheckPoint CloudGuard Comes with many features to automate governance across multiple cloud environments, detect misconfigurations, ensure compliance, and more.
- Fugue This enterprise CSPM solution addresses cloud security from a software engineering standpoint and helps engineers to build security into the cloud environment.
- Trend Micro Conformity This platform monitors your cloud infrastructure in real-time and auto remediates the steps needed for compliance, security, and governance of your cloud assets.
- Ermetic This is an identity-first CSPM solution that provides multi-cloud protection for your cloud environment. This easy-to-deploy SaaS solution enables security and DevOps to work seamlessly.
What is CSPM?
CSPM strategies and tools automate cloud security and help to implement a set of best practices across the entire cloud infrastructure. These tools constantly monitor your cloud applications and resources to identify gaps and vulnerabilities in the overall security. It can also identify misconfigurations in the cloud, so you can fix them right away. With all these measures, you're sure to meet the compliance requirements of various standards in your industry.
Next, let's look at some of the best CSPM tools available today. We have analyzed different tools across multiple parameters, and have created a list of the top six tools in this space.
The Best CSPM Tools
1. Aikido

Aikido implements a range of security testing services for the developers of new Web applications and SaaS packages. The list of scanning systems on the platform includes a CSPM. This unit checks that no weaknesses exist in the supporting platform and cloud services on which the new application will run.
Key Features:
- Application security assurance: provides software composition analysis, dynamic application security testing, static application security testing, scanning for Infrastructure-as-Code, containers, and Kubernetes, as well as the CSPM
- Integrations for cloud security scanning: Employs the services of CloudSploit and AWS Inspector to gather configuration details
- Risk de-duplication: Groups together errors with the same cause or errors that are the results of another problem that has already been identified
- Severity scores: Generates a risk score for each discovered problem and compares versions for progress tracking during retesting
- Access rights assurance: Assesses user account structures, groups, and permissions
The Aikido platform lets application developers run final acceptance testing in a copy of the intended live environment. This enables checks to be implemented that ensure no secrets leakage can occur between the application and its supporting infrastructure. The system also ensures that intruders can’t get into the application through its delivery and hosting services.
Pros:
- Provides cloud security testing as part of a CI/CD pipeline release mechanism
- Generates a prioritized list of issues to fix and can resolve some automatically
- Compliance assurance for SOC 2, ISO 27001, CIUS, and NIS 2
- Scans AWS, Azure, Google Cloud Platform, and DigitalOcean
- Can report errors to bug trackers and project management tools
Cons:
- This is part of an application security testing platform and not a standalone CSPM
There are four plans for Aikido, they each have a rate per month and an annual rate:
- Free: $0
- Standard: $349 per month or $3,768 per year
- Pro: $699 per month or $7,548
- Enterprise: Priced by negotiation
Access Aikido on a free trial.
EDITOR'S CHOICE
Aikido is our top pick for a CSPM tool because it implements CSPM in conjunction with the requirements of the applications that are going to run on those cloud platforms and services. DevOps teams can use the entire Aikido platform for security testing throughout the software development lifecycle, The CSPM is assisted by tests of Infrastructure-as-Code, containers, and Kubernetes to get a complete view of the potential security weaknesses of all the systems that will support a new Wen application or SaaS package.
Download: Access a FREE Trial
Official Site: https://app.aikido.dev/login
OS: Cloud-based
2. Datadog
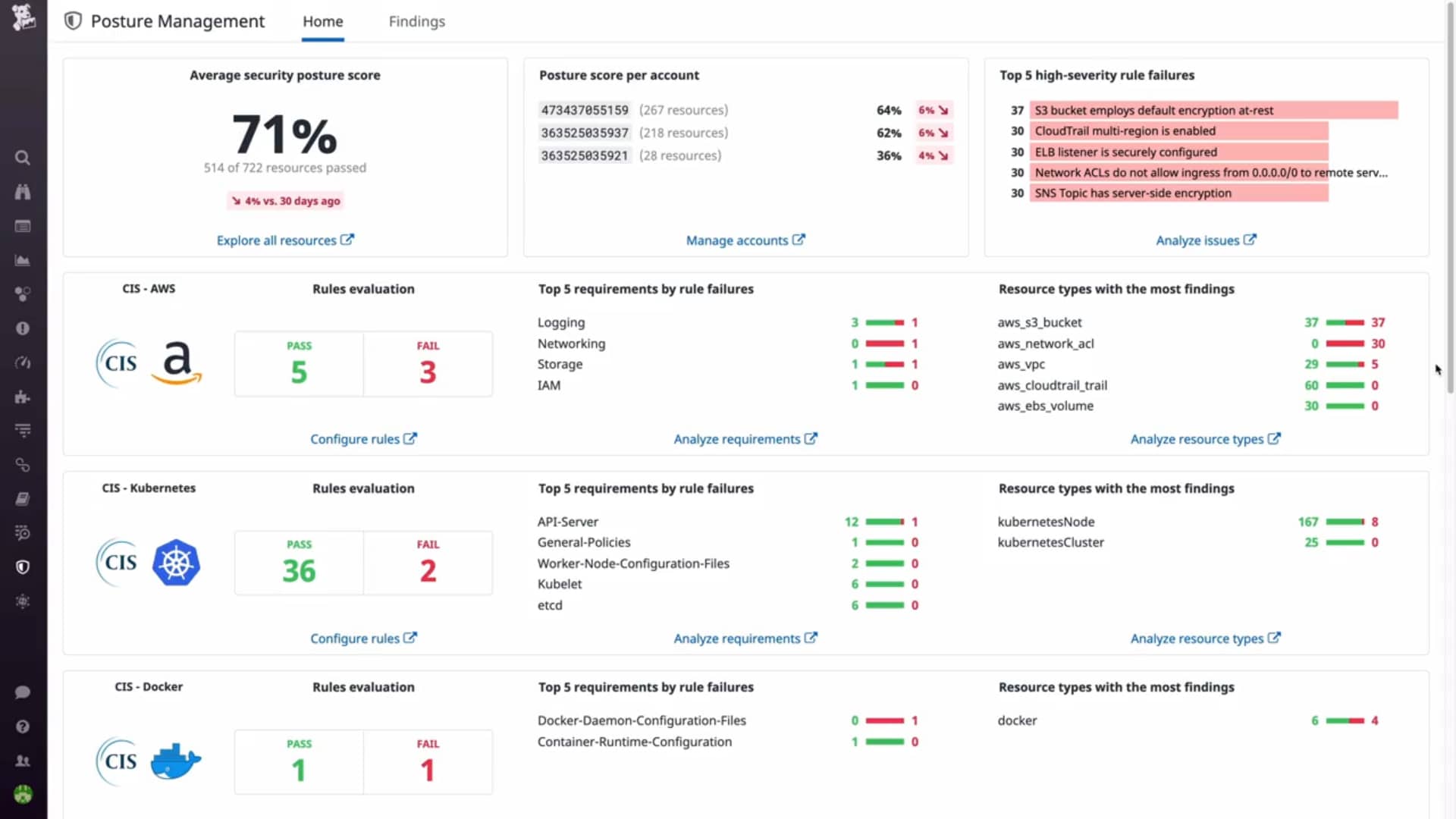
Datadog's CSPM continuously scans your cloud resources including hosts and containers to identify any security gaps or misconfigurations. Since it combines both cloud monitoring and container security, it's easy to deploy and provides a centralized view of all your resources.
Key Features:
- Complete Configuration Visibility This CSPM provides complete visibility of your configuration at any time. This visibility helps you to answer some pertinent questions such as the configuration of your S3 bucket last month, your Kubernetes containers' status, and more. It also provides a better context for your configuration.
- Easy to Use Datadog's CSPM focuses on some of the most pertinent questions related to cloud security such as your posture score, list of vulnerabilities, etc. You can find all this information in an intuitive and centralized dashboard that's easy to use for anyone.
- Compliance Datadog's posture score tracks each compliance criteria, and in the process, ensures that your cloud infrastructure meets the requirements of industry standards such as PCI DSS and SOC 2.
- Reduces False Positives A common problem with monitoring and compliance tools is alert fatigue. With Datadog's CSPM, you can send custom alerts to the right teams in case of serious misconfigurations only. You can even change its settings to send alerts at the account or service level if required.
- Scales Well Another huge advantage of Datadog's CSPM is that it scales well to meet your growing requirements. You can implement it across IaaS, SaaS, and PaaS, regardless of the size of your cloud infrastructure.
In all, Datadog CSPM is a comprehensive cloud security monitoring tool that leverages the underlying technologies to improve your operational efficiency and reduce costs. Besides, it also scales well and is easy to use, thereby providing complete configuration visibility and helping meet compliance standards.
Pros:
- Offers numerous real user monitors via templates and widgets
- Can monitor both internally and externally giving network admins a holistic view of network performance and accessibility
- Changes made to the network are reflected in near real-time
- Allows businesses to scale their monitoring efforts reliably through flexible pricing options
Cons:
- Would like to see a longer trial period for testing
Datadog CSPM starts at $7.50 per host per month when billed annually. Otherwise, it costs $9 per host per month. Click here to start a free trial.
3. CrowdStrike Falcon Horizon
Falcon Horizon from CrowdStrike is a CSPM tool that detects cloud misconfigurations and reduces the chances of the security implications that come with it. This tool also makes it easy to identify and eliminate blind spots and ensure compliance across all leading cloud providers.
Key Features:
- Provides Complete Visibility Into Multi-cloud Environments The salient feature of this tool is that it provides complete visibility into all cloud-native assets across your entire cloud infrastructure, even if it is spread across multiple cloud environments. This provides overall context and visibility to your security decisions and helps you to take appropriate actions to ensure your cloud's security.
- Detects Misconfigurations and Threats Falcon Horizon provides agentless monitoring of all your cloud resources to identify any misconfigurations or threats quickly. It is followed by context-based recommendations to fix these issues. This platform also sends real-time alerts to the concerned people and provides pertinent information to improve the speed of investigation by 88%.
- Simplifies Management You can stay on top of all that's happening across your entire cloud environment through a single console. Also, you can enforce any security policies across accounts and regions as needed.
- Automatic Discovery This CSPM tool automatically discovers devices that are not protected by it and sends alerts for immediate action. With this automated discovery, Falcon Horizon ensures that there are no unmonitored devices and blind spots in your cloud infrastructure.
Overall, Falcon Horizon is a comprehensive CSPM that protects your cloud resources across multiple cloud environments. It continuously monitors your assets to optimize configurations and prevent threats. In the process, it ensures compliance with leading industry standards.
Pros:
- Excels in hybrid environments (Windows, Linux, Cloud, BYOD, etc)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Lightweight agents take up little system resources
Cons:
- Would benefit from a longer trial period
Click here for a free trial and here for a demo.
4. Check Point CloudGuard
Check Point's CloudGuard is an intelligent threat detection CSPM that identifies any vulnerabilities and provides remediation recommendations for the same. It automates governance across multiple cloud environments and helps you to constantly stay on top of cloud security.
Key Features:
- Security and Compliance CloudGuard provides security for all cloud-native environments such as AWS, Google Cloud, Azure, Kubernetes, Alibaba Cloud, and more. With such security controls in place, it helps to quickly identify vulnerabilities and fix the same. In turn, all these help your organization to comply with the leading industry standards.
- Provides Context and Visibility Another salient aspect of this tool is that it provides the context for resolving security vulnerabilities. Armed with this information, you can quickly get to the root cause and fix the problem before it impacts a wider surface area.
- Sends Real-time Alerts This tool sends real-time alerts to the concerned individuals or teams, so they can fix the underlying security loopholes at the earliest. It sends these alerts through its native platform and also, integrates with third-party tools to provide the same.
- Protects Identities CloudGuard enforces privileged access on a need basis. It integrates with your organization's IAM and provides access to critical actions and services based on the individual's role/department. At the same time, it also continuously audits and analyzes the activities of IAM users to prevent insider attacks.
In all, CloudGuard enables organizations to have streamlined cloud security and effective cloud security operations. It provides hassle-free maintenance and best practices for DevOps. Needless to say, all these help with governance and compliance.
Pros:
- Good for companies who want to help educate users as they attempt to access information inappropriately
- Supports major compliance standards
- Supports email scanning that can automatically restrict emails from being sent
Cons:
- Interface be easily be cluttered with an excessive amount of events, making it hard to use at scale
- Warns the user directly, which isn’t always an option sysadmins want to take
Click here to request a demo and here for a free trial.
5. Fugue
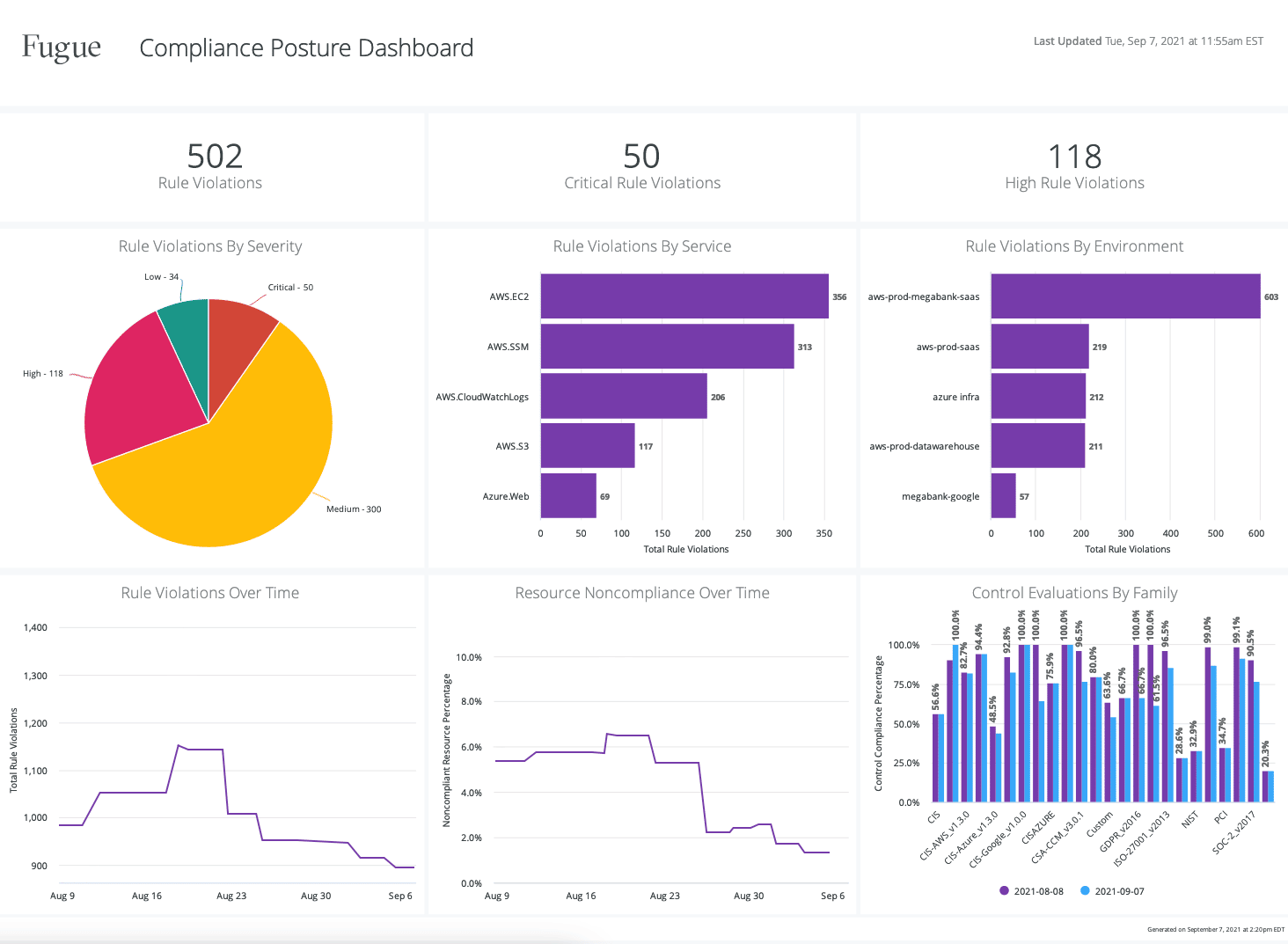
Fugue is a SaaS platform that monitors your complete cloud environment from a software engineering standpoint. It secures your resources through the entire cloud development lifecycle and through this, empowers engineers to build security into their cloud resources. Fugue also helps with compliance.
Key Features:
- Unified Policy Engine Fugue has an open-source policy engine that makes it easy for engineers to apply security and compliance across the entire software development life cycle. Powered by the Open Policy Agent, this platform combines Fugue's pre-built rules with your custom security rules and ensures that every step in your SDLC meets these presets.
- Deep Visualization and Reporting A salient feature of Fugue is its continuous snapshots of your environment, so you can use the same to identify resources, attributes, relationships, and more. This visualization provides deep insights into your cloud environment and its performance. Also, it comes in handy to generate custom reports that can be used for decision-making, internal auditing, and compliance with industry standards.
- Auto Remediation This platform continuously monitors your platform and tracks any configuration changes and vulnerabilities. It even protects sensitive resources with guardrails to prevent unauthorized access to information and data. Fugue also constantly compares performance with established baselines to quickly identify any vulnerabilities.
- Integrations Fugue integrates well with many leading platforms such as Slack, Jira, OpsGenie, ServiceNow, and more. This streamlines ticketing and enterprise messaging.
Overall, Fugue is a CSPM built to monitor cloud development from an SDLC standpoint. It provides all the tools and capabilities that engineers need to build security into their cloud applications, monitor the cloud environments, and take the necessary actions.
Pros:
- Highly customizable interface
- Great reporting dashboards – ideal for NOC teams
- Includes metrics for your cloud development lifecycle
- Supports automated remediation
Cons:
- Better suited for larger cloud networks
Fugue offers two plans:
- Developer This is a free account for individual engineers and small projects. It can have only one cloud account, one code repository, and only one account.
- Enterprise This plan is designed for enterprises and comes with unlimited cloud accounts, code repositories, and users. Reach out to the sales team for a custom quote.
If you'd like to demo the enterprise plan, click here.
6. Trend Micro Conformity
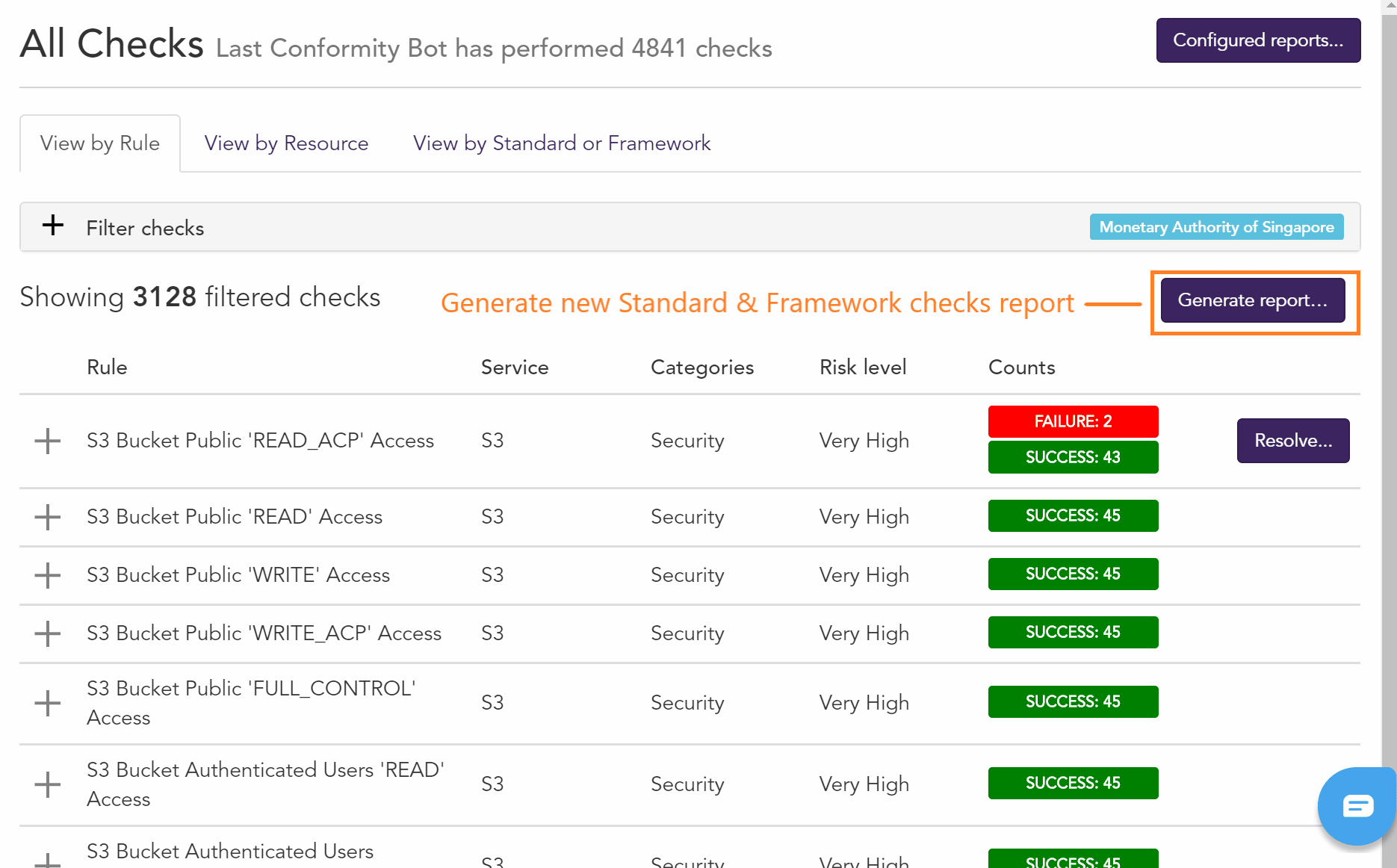
Trend Micro's Conformity is a comprehensive CSPM tool that continuously monitors your cloud environment to provide compliance and governance for your cloud infrastructure. It comes with a slew of features to meet the needs of different groups within your organization.
Key Features:
- Comprehensive Visibility Trend Micro's CSPM offers complete visibility into your entire cloud infrastructure, even if it's spread across multiple cloud environments. You can access all the information you need through a centralized dashboard. Further, you can check against 1,000+ cloud configuration services across AWS, Azure, and the Google Cloud Platform.
- Automated Compliance Checks This tool runs hundreds of automated checks against your cloud infrastructure to ensure that it complies with the leading standards such as PCI DSS, SOC 2, ISO 27001, and more. It also continuously audits your environment for any misconfigurations using an extensive set of filters. All this means that you can always stay on top of security and compliance.
- Supports a DevOps Culture Trend Micro supports Infrastructure-as-a-Code (IaaC) to ensure the deployment of compliant templates that meet the compliance standards as well. It also helps to integrate seamlessly into your existing CI/CD pipelines and comes with powerful APIs to automate the flow of data with your custom applications and third-party tools within your infrastructure.
- Remediates Misconfigurations Trend Micro Conformity specializes in remediating misconfigurations. It continuously monitors your infrastructure and in case of misconfigurations, sends real-time alerts along with contextual information about it. All of this helps the respective teams to address the issues at the earliest.
In all, Trend Micro Conformity comes with many advanced features that enable security, governance, and compliance across your entire cloud infrastructure. It even generates the reports needed for compliance and internal auditing.
Pros:
- Supports a wide range of cloud environments
- Consolidates your view into all your cloud-based networks
- Supports automated compliance checks
- Offers a range of configuration monitoring options and access controls
Cons:
- Can take time to fully explore all features
Trend Micro offers four plans:
- Cloud-Ready – Costs $250/month/account billed annually. Ideal for organizations with less than 25 cloud accounts.
- Cloud-First – $217/month/account billed annually. Works well for 26-50 cloud accounts.
- Cloud-Native. Click here for a custom quote. Ideal for 50+ accounts.
Click here to try it for free.
7. Ermetic
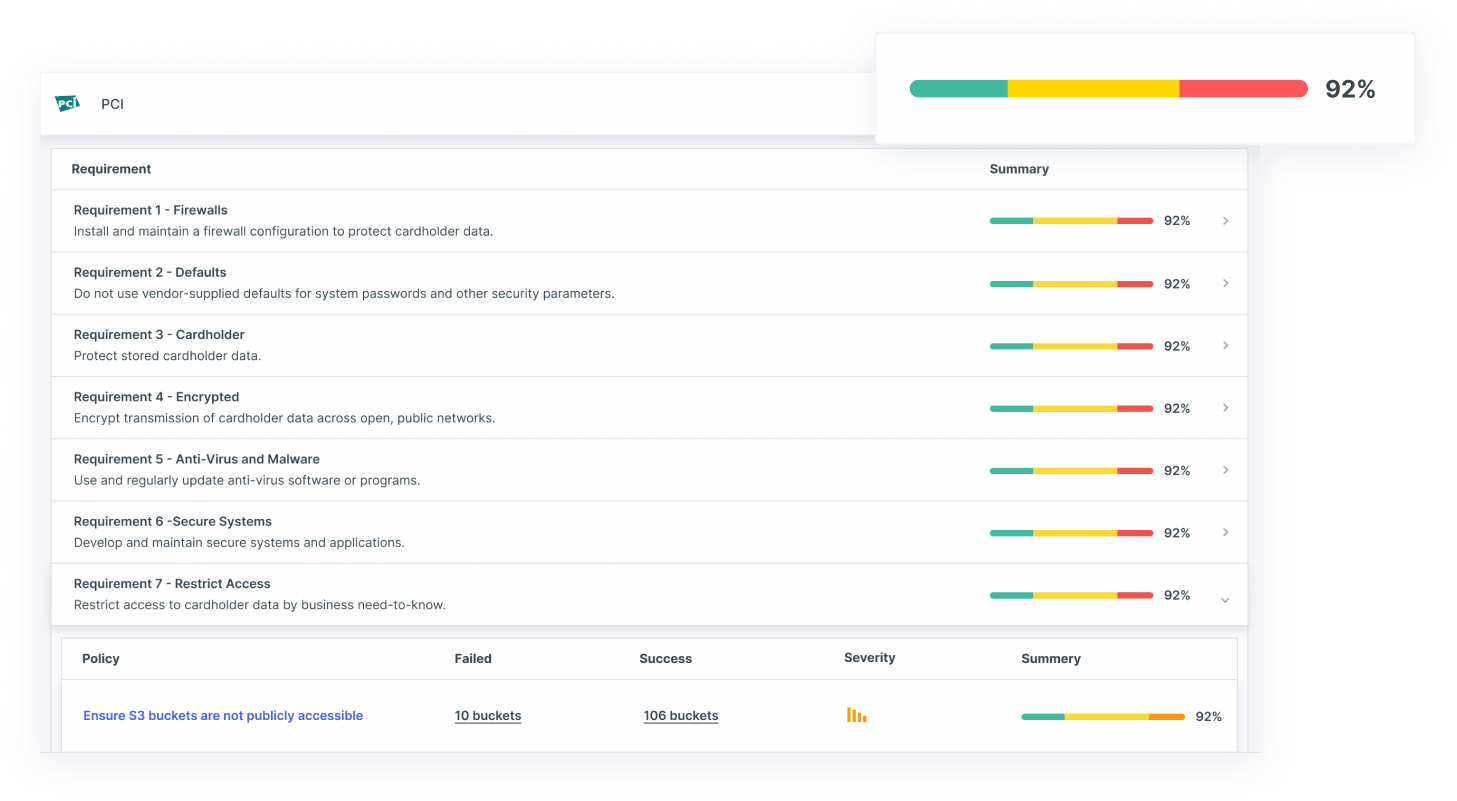
Ermetic is an identity-first CSPM that provides security for your multi-cloud environment. This SaaS solution manages your cloud assets, detects anomalies, identifies misconfigurations, meets compliance, and helps the security and DevOps teams to work together.
Key Features:
- Automates Cloud Compliance Ermetic automates the process of cloud compliance by ensuring that all your assets are configured correctly. It also continuously monitors your data to identify risks and inform the concerned stakeholders, so they can be fixed right away. Ermetic also provides the contextual information required to speed up this process.
- Integrates CIEM and CSPM This is a unique tool that integrates both CIEM and CSPM to provide comprehensive cloud security. Both these tools address security from varying angles. CIEM, for example, provides a deep view of each cloud asset while CSPM provides a broad view of the overall cloud infrastructure. This way, each tool can unearth a different set of vulnerabilities for streamlined cloud security.
- Identity-centric Ermetic is an identity-centric tool that assesses not just compliance risks, but also identity-based risks in your cloud infrastructure. It also analyzes your cloud environment's performance and security across all identities and entitlements in the cloud to provide a comprehensive picture.
Pros:
- Simple yet powerful dashboard and admin console
- Takes an identity-first approach to manage assets and detect anomalies
- Integrates both CIEM and CSPM
Cons:
- Would like to see a free trial versus a demo
In all, Ermetic is a robust CSPM tool that provides comprehensive protection for your cloud assets and identities. It combines the capabilities of CIEM and CSPM to provide new perspectives on security and governance.
Thus, these are our top six choices when it comes to CSPM tools. The exact choice of product depends on your individual requirements and budgets, but we hope this gives you an idea of what to expect from each CSPM.
Conclusion
To conclude, security is an essential part of your cloud infrastructure, and to achieve the highest standards of security and the resulting compliance, you need appropriate strategies and tools. CSPM tools are those that handle your cloud infrastructure's security, governance, and compliance. There are many CSPM tools available today and we have come up with six of the best ones, based on their features and capabilities. We hope you find this information useful to choose a CSPM tool for your cloud security.