As an organization’s footprint expands, the risk of digital breaches increases as well.
Research suggests that 30% of breaches take place due to vulnerabilities or shadow IT assets within the cloud that the IT security team fails to identify.
Here’s our list of the best Attack Surface Monitoring Tools:
- ManageEngine Vulnerability Manager Plus – EDITOR'S CHOICE A comprehensive vulnerability discovery and remediation tool for medium to enterprise-level businesses. Download a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL An attack surface analyzer that can spot identity risks, misconfigurations, and other Indicators of Compromise (IoC) before they impact your organization. Start a 30-day free trial.
- Rapid7 InsightVM A leader in vulnerability remediation with a wide range of integrations into other SIEM tools
- Bugcrowd Asset Inventory Offers continuous asset management and vulnerability discovery – best for internal security teams
- Intruder Access this service through a Web page and get regular scheduled external vulnerability scans, on-demand attack surface scans, or internal vulnerability scans.
- Digital Shadows SearchLight Provides highly visual reports of vulnerable assets and network configurations across your environments
- Burp Suite Enterprise Edition A highly technical suite of tools used by professionals for automated and manual vulnerability discovery
- CoalFire Attack Surface Management Provides simple yet powerful vulnerability discovery and remediation
- OWASP Zed Attack Proxy Highly configurable tools best for security experts and in-depth audits
- CyCognito Attack Surface Management Offers enterprise asset management with combined vulnerability discovery, monitoring, and remediation
- ImmuniWeb Discovery Leverages the OSINT framework and AI to find vulnerable targets quickly before they’re exploited
New cloud services, large mobile workforce, work-from-home network topologies, etc. have become the main culprits to enlarge the size of your attack surface. Besides, such remote nature is what makes it challenging to secure and protect. To prevent cyber security attacks, you need to be armed with the right tools that can map and monitor your attack surface and help you mitigate risks.
Some of the main risks that may occur without Attack Surface Monitoring Tools include:
- Poor visibility into exposed databases, unknown apps, and APIs
- Lack of attack surface visibility on hackable entry channels
- Increase in Shadow IT Risks
Attack Surface Monitoring tools offer Attack Surface Analytics to monitor security performance, offer visibility into digital assets, and prevent cyber threats by identifying high-risk areas.
What is Attack Surface Monitoring?
Before we get into Attack Surface Monitoring, let’s first understand what an attack surface is. Attack Surface is all your software, hardware, cloud assets, and SaaS that is open to the Internet that stores or processes your data. These act as the entry points that hackers may use to access a system or network to manipulate your data.
Attack Surface Monitoring is a data security practice of monitoring the software you depend upon to look for entry points that hackers may use to access your sensitive organizational data. It helps you identify high exposure risk areas and prevent cyber threats.
Attack surface protection and analysis is software for vulnerability management that focuses on OS exploits and system settings. Attack Surface Monitoring tools provide all-inclusive Attack Surface Management (ASM). It is a continuous procedure of discovery, inventory, analysis, prioritization, and security monitoring of cloud assets that store, process, or transfer sensitive data.
DevOps environments must integrate ASM into their CI/CD pipeline to mitigate potential risks within new features and functionalities.
Attack Surface Monitoring Strategies
To protect your attack surface, IT security leaders must be following these 3 crucial attack surface monitoring strategies:
- Assess endpoints Leverage an individual monitoring process to continuously monitor endpoints such as tablets, desktops, mobile phones, laptops along with virtual environments like services and networks. Monitoring network topologies can help you identify security risks and vulnerabilities before they get serious. It increases visibility into your internal system to mitigate risks and attacks, as it detects which endpoints are more exposed and allows entry to your attack surface.
- Identify vulnerabilities Forecasting and simulation tools help you identify security vulnerabilities within the attack surface even before hackers could get access. Advanced tools can run scenarios within your network to mimic malicious attacks and visualize areas where vulnerabilities lie.
- Prevent human errors It is extremely important to train the IT teams in avoiding falling prey to malicious attacks and phishing scams often caused due to human error. That’s because even the most advanced attack surface monitoring tools won’t be able to prevent human errors. Enterprises also need to limit the devices IT employees use to reduce security risks. Further, organizations need to employ critical security measures such as frequent password changes, two-factor authentication, etc. to prevent attackers from penetrating your security systems.
The Best Attack Surface Monitoring Tools
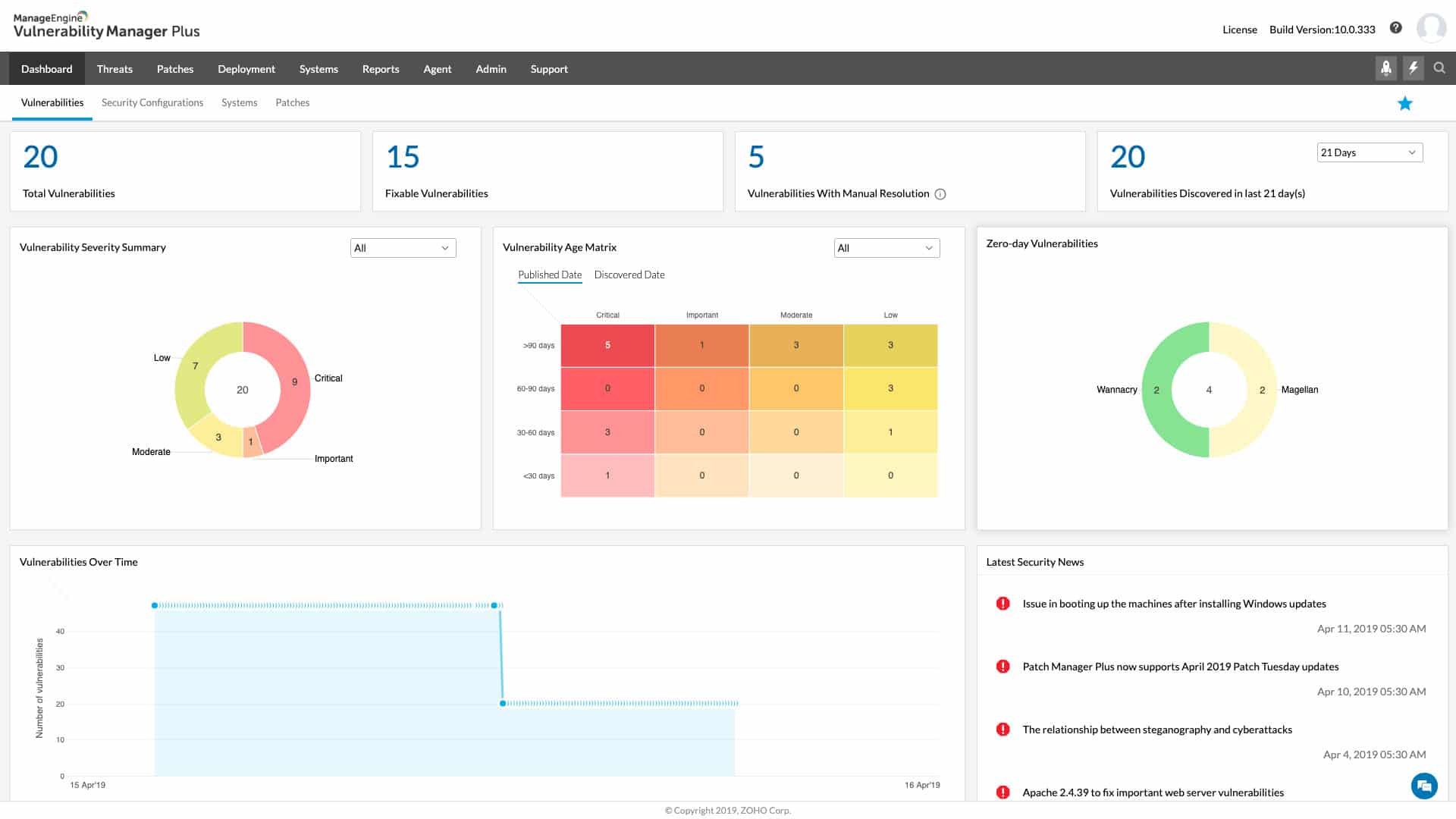
1. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus combines asset management, vulnerability discovery, and vulnerability remediation into a single platform. The platform scans the network for different assets and then probes them to find vulnerabilities. The platform can also find network vulnerabilities as well through similar scanning methods.
Key Features
- Takes a holistic approach to network security and vulnerability remediation
- Prioritizes vulnerabilities for remediation
- Offers steps to solve vulnerabilities
Unique Feature
A single tool that handles all aspects of attack surface monitoring, auditing, and compliance.
Why do we recommend it?
Its reports are insightful and have helped us quickly identify many vulnerabilities. Its antivirus and port audits are helpful too.
Each vulnerability is categorized and given a severity rating, allowing teams to prioritize patching accordingly. Along with this categorization, each vulnerability is paired with remediation steps, helping reduce exposure time.
Who is it recommended for?
Helps businesses of all sizes to identify security issues and fix them at the earliest. Also, well-suited for organizations that have to meet strict compliance standards.
Pros:
- Excellent for continual scanning and patching throughout the life of any device
- Robust reporting can help demonstrate changes following correction
- Runs on Windows, Linux, and Mac
- The most recent threats and vulnerabilities are continuously updated in backend threat intelligence
- Has a free version, which is excellent for small firms
Cons:
- ManageEngine Vulnerability Manager Plus can take time to explore fully
Whether you have a small internal team, or outsource your network security, VMP offers one of the best tools to stay ahead of threats and prioritize the vulnerabilities that would impact your businesses the most. Get a 30-day free trial.
EDITOR'S CHOICE
Our editors have selected ManageEngine Vulnerability Manager Plus as their top pick, given its comprehensive coverage of attack surfaces. It can scan all the exposed attack surface areas across local and remote office endpoints. Moreover, it works well across Windows, Linux, and Mac environments. While scanning, it looks for a wide range of vulnerabilities related to operating systems, servers, credentials, third-party software, and more. It collates and analyzes information across these sources and provides the required insights to help prioritize and resolve issues quickly. All these features make it the best attack surface monitoring tool in our analysis.
Download: Start a 30-day FREE Trial
Official Site: https://www.manageengine.com/vulnerability-management/
OS: Windows, Linux, and Mac
2. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus works well across a wide range of IT systems. It gathers and analyzes data from different systems to help identify issues in your network. It continuously audits your security posture and provides visibility into threats as they occur, so you can remediate them before they impact your organization.
Key Features:
- Supports automated incident response to an imminent threat or attack.
- Backs up all AD objects and restores them when needed.
- Leverages machine learning to identify risks that can otherwise go undetected, like an anomalous logon or a user exercising privilege access for the first time.
Unique Feature
A unique feature of this tool is that it can identify 25+ attacks related to Active Directory, like brute force attacks and privilege misuse, thereby improving your overall security.
Why do we recommend it?
We recommend this tool because of its comprehensive approach to security. Specifically, it analyzes the attack surface area to identify misconfigurations that can open up security vulnerabilities for hackers. It can also identify risks across your AD and cloud environments.
The threat mitigation capabilities of this tool are excellent, as it can identify attacks like Kerberoasting, credential and privilege misuse, identity threats, and lateral movement attacks like ransomware. It can also detect Indicators of Exposure (IoE) that occur due to your environment’s public exposure. Additionally, it can spot 15+ network attacks and 20+ process attacks. Such a comprehensive coverage helps maintain your security posture.
Who is it recommended for?
This tool is recommended for businesses that run AD environments. It is also a good choice for organizations that need a wider SIEM solution. Works well for MSPs as well.
Pros:
- Provides automated incident response.
- Comes with AD backup and recovery.
- Identifies IoC and IoE to improve your overall security.
- Generates extensive reports.
- Leverages machine learning to gain deep visibility into potential risks.
Cons:
- It may involve a learning curve for some users, especially to understand the advanced features.
The annual price of ADAudit Plus starts at $595. Download a 30-day free trial to explore its features.
3. Rapid7 InsightVM
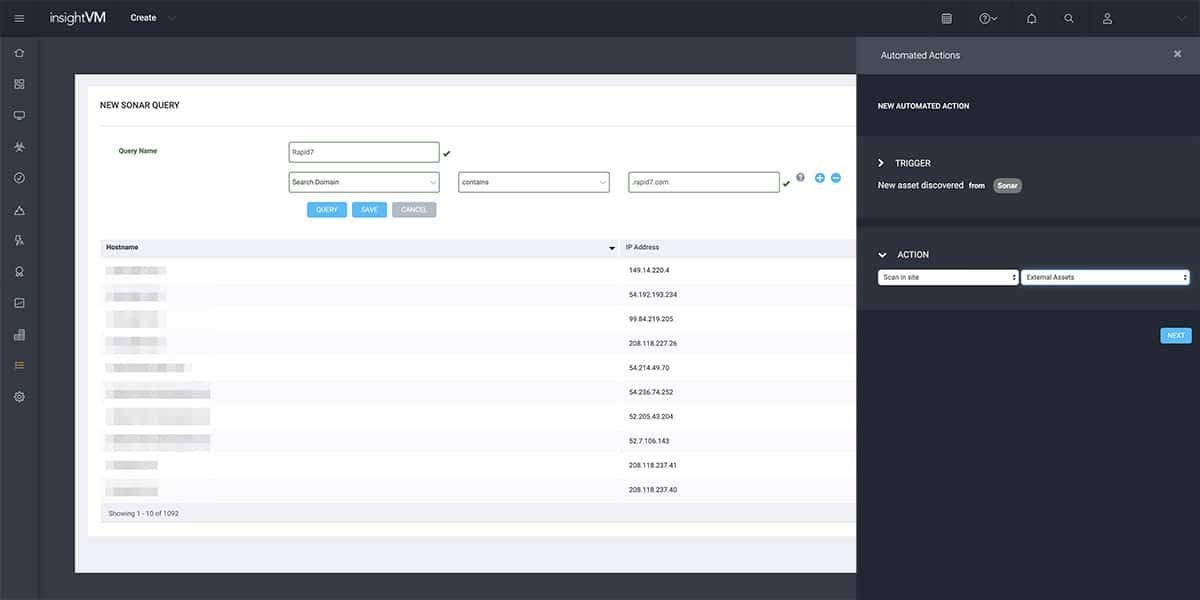
InsightVM tops the list with its potential features and robust analytics abilities. Rapid7 Insight platform was launched back in 2015 and it houses an exploit KB (knowledge base), vulnerability research, internet-wide scanning data, global attacker behavior patterns, real-time reporting, and exposure analytics. With these features, it offers a highly scalable, available, and efficient means of gathering vulnerability data and converting it into valuable insights.
Why do we recommend it?
It assesses your entire infrastructure and identifies vulnerabilities. You can even address the first-level issues by integrating with different third-party apps.
Rather than an attack surface monitor, Rapid7 InsightVM is more like a vulnerability manager. It scans virtual and cloud stacks along with network devices and endpoints. This cloud-based tool can scan remote sites to look for external endpoints. To enhance its capabilities, it features Project Sonar that collects data loss event notifications and other security-related data across various companies. This data can be used to set up a third-party risk assessment to a vulnerability scanner.
InsightVM offers comprehensive endpoint analytics and live vulnerability detection. Deploy lightweight and universal Insight Agent once and it will provide live intel on user and network risks across all endpoints.
The main highlights of the platform include live dashboards, automation-based patching, lightweight endpoint agent, real risk prioritization, integrated threat feeds and so much more.
With InsightVM, you can leverage shared views and common language to bridge the gap between siloed teams and boost impact for remediation. It also features metrics and tracking to provide a proactive approach for vulnerability management.
Lastly, InsightVM seamlessly integrates with over 40 leading technologies to enhance other solutions within your tech stack- right from ITSM/ITOM, ticketing systems, containers to SIEMs. It also leverages an open RESTful API to offer deeper visibility into your vulnerability data.

Who is it recommended for?
A good choice for large enterprises that tend to have a wide attack surface.
Pros:
- Leverages behavioral analytics to detect threats that bypass signature-based detection
- Uses multiple data streams to have the most up-to-date threat analysis methodologies
- Allows for robust automated remediation
Cons:
- Pricing is higher than similar tools on the market
- Some features may require paid plugins
Website Link: https://www.rapid7.com/products/insightvm/
4. Bugcrowd Asset Inventory
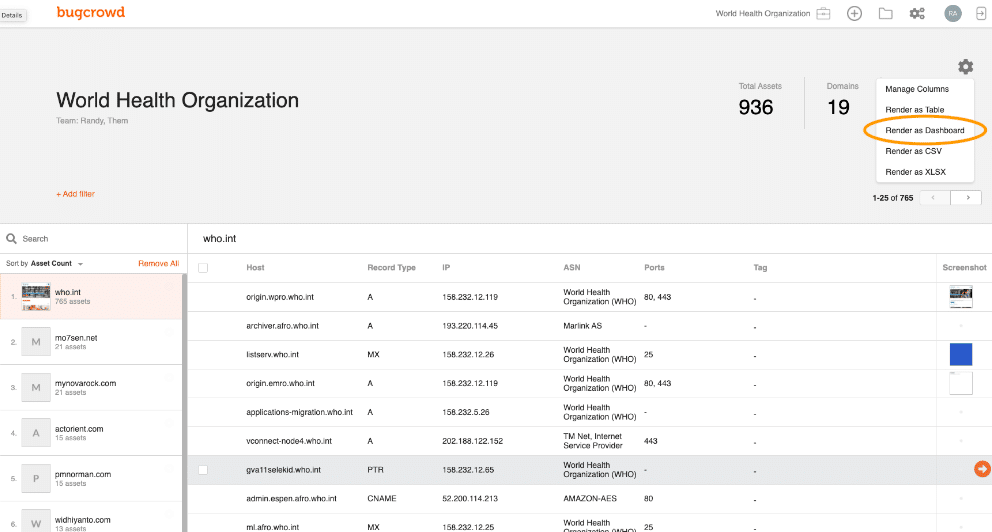
Bugcrowd offers a power-packed Attack Surface Management (ASM) solution in two formats – Asset Risk and Asset Inventory. Here we are going to focus on Asset Inventory as it is a software-based continuous asset discovery, alerting, and management solution.
Why do we recommend it?
A highlight of this tool is that it scans shadow apps and forgotten devices that are easy to miss. It discovers and manages unknown or unused assets, and in the process, reduces vulnerabilities.
Asset Inventory is an automated tool developed by skilled white hat hackers. It crawls through linked software packages and acts as a pen-testing tool to discover the web services and software used by the client. It examines all microservices and APIs that offer plug-in services for web functionalities.
With Asset Inventory, you can find real risks, prioritize them and take actions to prevent attacks on dynamic attack surfaces. Activate “smart folder” and set up alerts to quickly view, interact and manage changes in the endpoints to mitigate digital risks.
With Bugcrowd ASM, organizations can quickly detect and take actions for unknown assets before malicious attackers can even discover them. The platform selects ideal security researchers from a global network of pro-white hat hackers who will help you find missed or forgotten assets. Further, the ASM features intelligent mapping and attribution to reduce noise and only see assets that are truly yours.
For precise risk-based prioritization, the ASM collects data from more than 1200 programs to detect real exploitation risks. To provide insights, organizations can leverage detailed risk-ranked reporting with the full risk profile, attribution method, and recommendations to secure detected assets.

Who is it recommended for?
Best suited for organizations that have multiple digital ecosystems.
Pros:
- A total attack surface management platform
- Includes automated inventory collections
- Includes tools to streamline risk assessments
- Can automatically take actions against threats
Cons:
- Can take time to fully configure and use
Website Link: https://www.bugcrowd.com/products/attack-surface-management/
5. Intruder
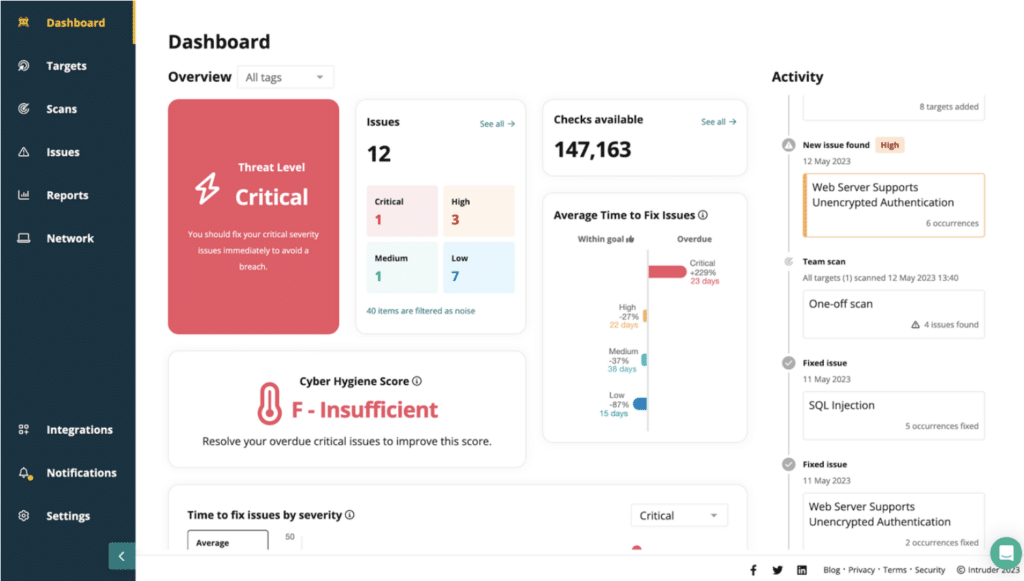
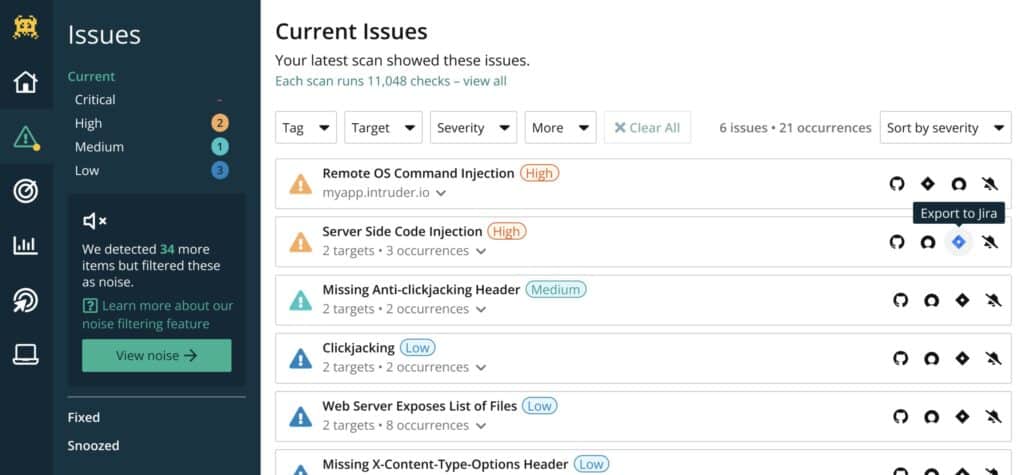
Intruder is a powerful security solution designed for effortless vulnerability and attack surface management. Continuously monitoring your attack surface, it uncovers potential issues and entry points, so you’re always a step ahead of threats. Running over 140,000 checks, it seamlessly integrates with leading scanning technologies like OpenVAS and Tenable, so you can zero in on critical vulnerabilities like an exposed database.
Key Features
- Choice of OpenVAS or Tenable vulnerability scanners
- Optional add-ons for Web application and API security testing
- Cyber hygiene score
Unique Feature
Provides a real-time view of your attack surface to help you address issues as they emerge.
Why do we recommend it?
We love its automated scanning feature, as it takes a lot of work from our shoulders. Plus, its proactive threat response completes the security process.
Intruder offers dynamic perimeter monitoring, which scans for vulnerabilities whenever a system changes. With the Network View function, you can monitor and track any changes to your network, filtering through open ports and services. Real-time updates show what’s changed in your IT environment, such as recently opened ports and unexpected deployments.
The capabilities of these scanners cover your on-premises systems and also your cloud accounts on AWS, GCP, or Azure. The service also verifies your SSL certificates and warns you if one is about to expire.
Who is it recommended for?
Ideal for large organizations that want 24×7 visibility into their networks and the perimeter.
Pros:
- Plan levels to suit all budgets
- Easy-to-use Web interface
- Monthly, frequent, continuous, or on-demand scans
- Integration with project management and team collaboration systems
Cons:
- Top end features are available on the higher plans
Intruder also offers a dynamic application security testing (DAST) system for Web application and API assurance and they have a penetration team, called Vanguard that you can hire for an in-depth investigation of your system security. The attack surface monitoring system is available for a free trial.
6. Digital Shadows SearchLight
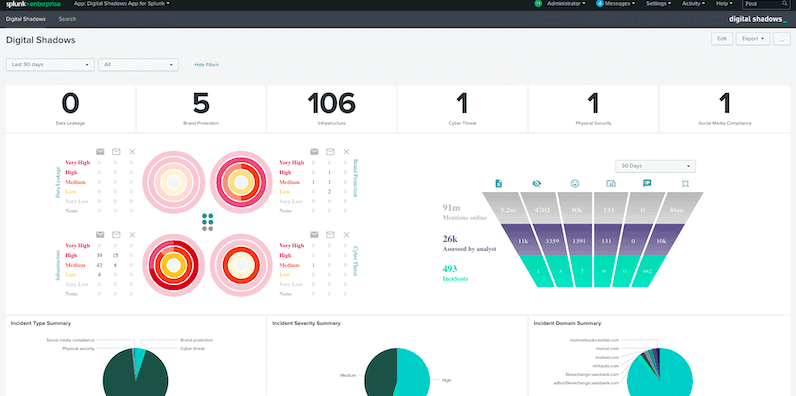
SearchLight reduces the noise of traditional threat intelligence and seamlessly conforms to the threat profile and unique needs of your organization. With the SearchLight platform, security teams can quickly detect and analyze critical risks and take actions accordingly. It provides access to wide-ranging data sources along with the required expertise to convert that data into intelligence.
Why do we recommend it?
This tool examines your network from the perspective of hackers and identifies vulnerabilities. By fixing the identified issues, you can safeguard your organization from most attacks.
SearchLight threat model seamlessly conforms to align its intelligence with your threat profile and risk appetite. It features built-in playbooks and automation functionalities to take actions immediately and reduce time-to-triage. It will examine your software assets to look for circulated intel shared by known hackers.
The platform works in 4 stages and it acts as an organization’s expanded team to set up key assets, gathers data from hard-to-reach sources, analyzes risks, and mitigate the impact. It can collect data from a wide range of sources across dark, open and deep web such as websites, social media, dark web markets, remote workers, app stores, criminal forums, cloud storage, paste sites, code repos, and more.
For precise risk detection and analysis, it leverages a combination of automation and human analysis to discard 95% of noise. Lastly, for effective mitigation of impact, SearchLight features pre-built context, integrations, and playbooks to instigate an immediate response.
Who is it recommended for?
A good choice for organizations that are heavily exposed to the Internet.
Pros:
- Can protect image copyright and trade secrets
- Looks for usernames, passwords, and other indicators of compromise
- Uses visualizations to help highlight key insights
Cons:
- Only offers a seven-day trial
Website Link: https://www.digitalshadows.com/searchlight/
7. Burp Suite Enterprise Edition
Driven by PortSwigger’s top-class cybersecurity research team, Burp Suite Enterprise Edition is a sophisticated package of pen-testing tools. It is available in 3 different editions – Free Community Edition paid Burp Suite Professional Edition, and lastly Burp Suite Enterprise Edition which is an automated web vulnerability scanner.
Why do we recommend it?
This is a web-based application that integrates with the software development process to uncover the likely vulnerabilities in your organization.
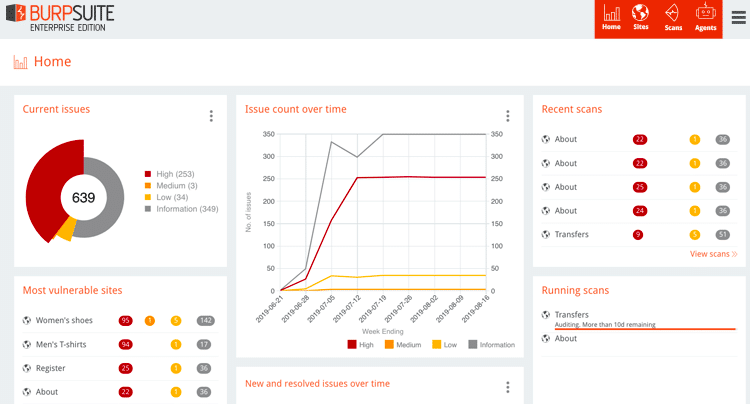
Burp Suite Enterprise is targeted towards DevOps processes and software development companies. It runs automated dynamic scans across your entire web portfolio and thousands of applications without any resource limitations and false positives.
Organizations can run recurring dynamic scans and gain full visibility into the security of your enterprise attack surface. It features intuitive dashboards, report scanning by email, and role-based access control.
To aid DevSecOps processes, Burp Suite Enterprise comes with out-of-the-box integration with CI plugins, a rich API, bug-tracking systems, and native Jira support to seamlessly adapt security into your workflows.
Always-on scanning and smart prioritization save time as they automatically eliminate vulnerabilities when threats are detected. The platform embraces a dynamic (DAST) approach for maximum coverage and minimal false positives without needing instrument code.
Who is it recommended for?
Best suited for large enterprises involved in extensive software development.
Pros:
- A collection of security tools designed specifically for security professionals
- The Community Edition is free – great for small businesses
- Available cross-platform for Windows, Linux, and Mac operating systems
Cons:
- Takes time to explore all the tools available in the suite
Website Link: https://portswigger.net/burp/enterprise/trial
8. CoalFire Attack Surface Management
CoalFire Attack Surface Management (ASM) solution is a pretty robust tool as it helps organizations detect those risks within plug-ins and integration APIs that offer quick functionality.
Why do we recommend it?
It uses extensive penetration testing to discover weaknesses in your networks. It also offers continuous discovery and remediation of first-level attacks.
When IT teams develop a web service or website, companies often overlook where these functionalities run or whether they are secure. Remediation, once the damage is done, becomes expensive and difficult. That’s when CoalFire comes in!
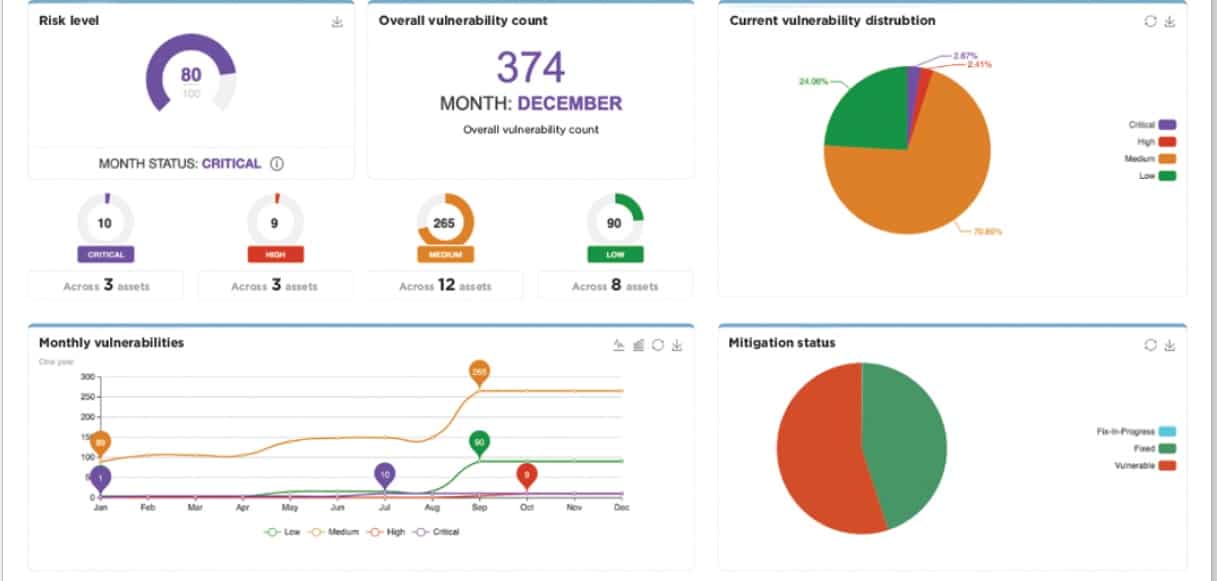
CoalFire ASM crawls across web services and websites to analyze all integrated external services. It uses automated processes to discover all the key assets that make up a client’s tech stack, whereas human analysts verify these discoveries.
It offers a full asset inventory to help enterprises develop a powerful defense system. The platform guides you on how to set up precise defense software as per your threat profile and unique business needs.
CoalFire detects risks within the connections between your network and remote workforces, new devices, external apps, and remote sites. It offers wide-ranging asset inventory and runs risk assessment to delineate a detailed attack surface.
Who is it recommended for?
Works well for organizations that have a hyper-scale multi-cloud environment and need continuous attack surface monitoring.
Pros:
- Great interface – excellent reporting and live data visualizations
- Does an excellent job at detecting vulnerabilities across APIs and plugins
- Provides recommended remediation actions
- Can automatically scan the network for new API connections
Cons:
- Better suited for larger organizations
Website Link: https://www.coalfire.com/solutions/threat-and-vulnerability-management/attack-surface-management
9. OWASP Zed Attack Proxy
OWASP Zed Attack Proxy (ZAP) is an open-source, free web security tool actively managed by an expert team of international volunteers. It scrutinizes a website to look for OWASP's top 10 threats which are like industry touchstones.
Why do we recommend it?
This is a popular open-source web application scanner used for scanning web applications.
ZAP can be seamlessly plugged with Attack Surface Detector- another project of OWASP to make it an attack surface monitor. Together it examines web services and APIs to discover risks through attack surface analysis.
Attack Surface Detector identifies hosts for discovered web applications and stores the code along with parameters for the call and its data types. Companies can use this system to regularly scan the discovered functions and compare its code with the stored version to detect new vulnerabilities in changes.
Overall, ZAP is an extensible and flexible tool that acts as a middle-man between the web application and the tester’s browser to intercept and examine sent messages. Further, it modifies packet contents as per the needs and sends these packets forward to the destination. It acts as a daemon processor can also be used as a stand-alone app. If you already use a network proxy, ZAP can seamlessly connect to it.
Who is it recommended for?
Mostly used by professional penetration testers and application security specialists.
Pros:
- Open-source and transparent project
- Specifically designed to scan web applications
- Can run manually or passively with scheduling scripts
- Completely free
Cons:
- Only for web application penetration testing
Website Link: https://www.zaproxy.org/
10. CyCognito Attack Surface Management
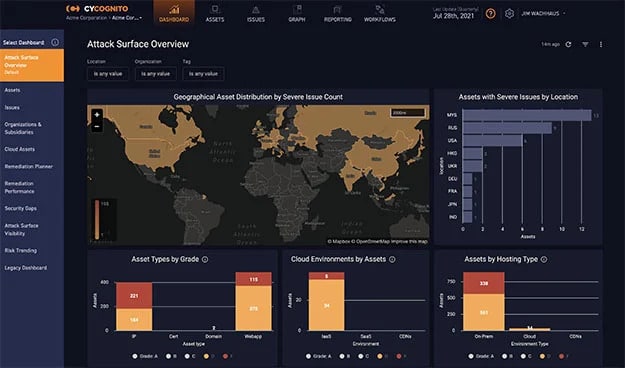
CyCognito is a SaaS platform that deals with external attack surface management. It automates and runs attacker techniques to test and safeguard companies. The SaaS tool works in five stages – Mapping Business-Asset Relationships, Defining Business Context, Automated Security Testing, Prioritizing Risks, and Accelerating Remediation.
Why do we recommend it?
It provides a comprehensive view into an organization's structure, network, and all the assets associated with them. It is also known for its easy scalability.
To map your external attack surface, it uses natural language processing, ML, and graph data models. With this, it reveals all your business-asset relationships related to cloud environments, joint ventures, and acquired companies. After this, it automatically classifies and attributes attack surface assets by using iterative analysis.
Automated security testing will not only identify CVEs (Common Vulnerabilities and Exposures) but also reveal all endpoints hackers commonly use to attack your IT assets.
The tool offers complete visibility into your entire extended IT stack and derives the top 10 security gaps that contribute to 90% of your risks. Once it prioritizes risks, it offers detailed and actionable guidance and exploits intelligence to help your IT teams. It also offers workflow integrations to function with popular IT technologies such as CMDBs, SIEMs, ITSM, and other software.
Overall, CyCognito is a powerful tool as it helps companies know exactly which code is leading to vulnerabilities within your website and which company is causing them.
Who is it recommended for?
Ideal for large enterprises with distributed operations and a large remote workforce.
Pros:
- Excellent threat visualization – great for global companies
- Includes a robust workflow for vulnerability identification and remediation
- Can automatically collect new assets and asses risk levels if needed
- Can act as a full SIEM solution
Cons:
- Better suited for enterprises and larger networks
Website Link: https://www.cycognito.com/attack-surface-management
11. ImmuniWeb Discovery
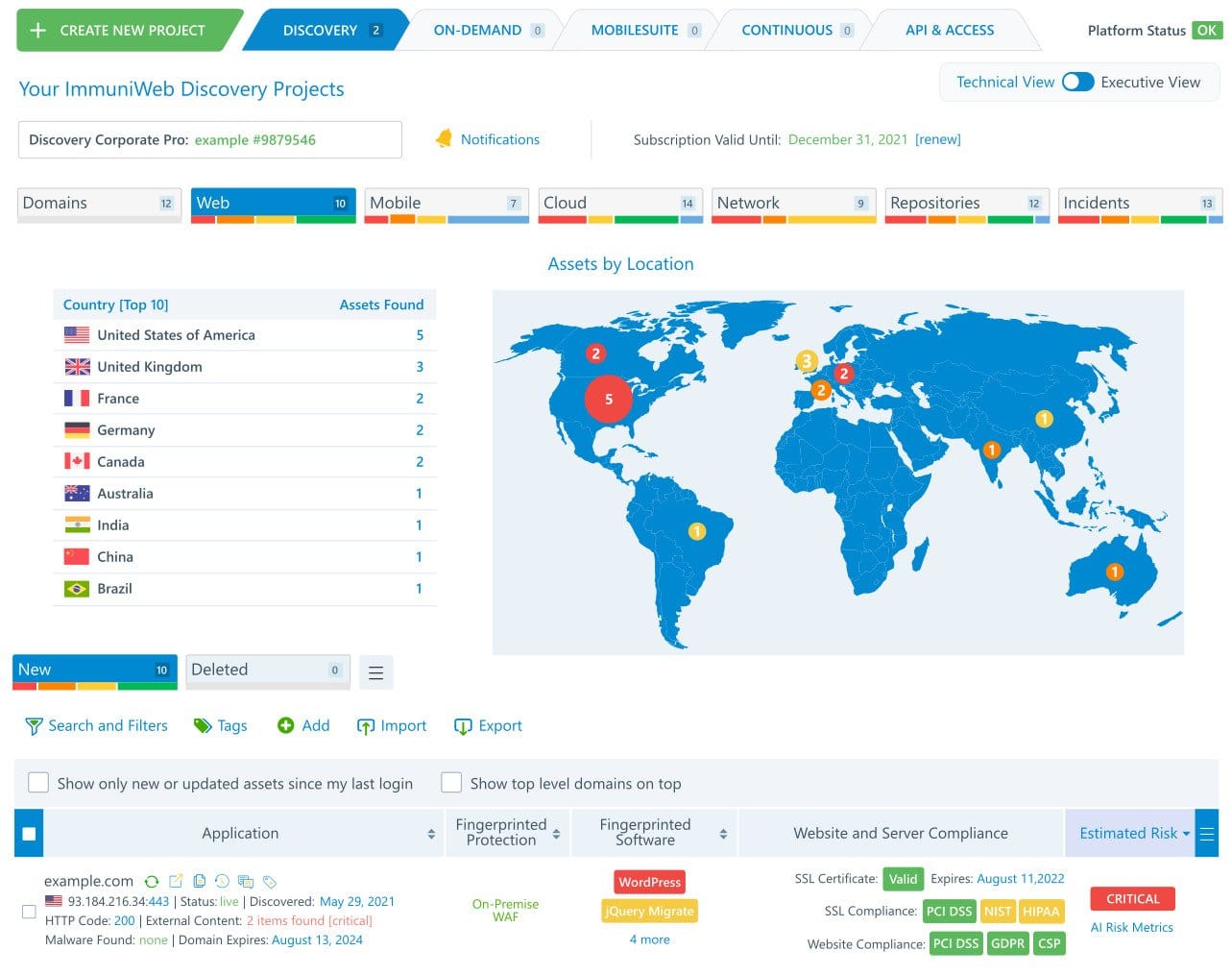
ImmuniWeb Discovery comprises features and functionalities that make it an attack surface monitor as well as a vulnerability scanner. It maps, examines, and classifies all digital assets- be it across cloud IT services or on-premises. It looks for code hosts by scanning the APIs.
Why do we recommend it?
ImmuniWeb Discovery dynamically catalogs all assets and monitors the surrounding cyber landscape to protect your organization's assets.
The platform leverages OSINT and AI technology to detect a company’s attack surface and dark web exposure. It is an ideal platform for vendor risk scoring and continuous self-assessment to prevent supply chain attacks.
For third-party and internal risk management, ImmuniWeb Discovery offers continuous security monitoring to identify vulnerable or misconfigured IT assets. Moreover, it also runs dark and deep web monitoring to detect stolen credentials, stolen data, brand misuse, phishing, and compromised systems. In case of risk detection, forgotten assets or shadow IT, it instantly sends alerts to relevant team members for immediate response.
The ASM tool uses OSINT technology which is quite non-intrusive and production-safe, perfect for vendor risk scoring. It provides a bird’s eye view into your IT assets to effectively execute risk-based penetration testing and patching.
All in all, ImmuniWeb is a reliable tool that deals with external as well as internal vulnerabilities. The service is offered in four levels – Ultimate, Corporate, Corporate Pro, and Express Pro; each package varies in its features and capabilities. Express Pro has the lowest price and covers basic attack surface monitoring features, whereas Ultimate is the full feature-packed edition with the highest price covering all top-class ASM capabilities.
Who is it recommended for?
Well-suited for organizations in the financial and healthcare verticals, as it specializes in compliance management.
Pros:
- Uses the OSINT framework combined with AI to proactively stop threats
- Includes features that are production safe and place a minimal impact on your network
- Includes supply chain attack tools
Cons:
- Not the best fit for smaller networks
Website Link: https://www.immuniweb.com/technology/demo/
Conclusion
Today, myriads of hacking attacks and data breaches take place due to minor security gaps and basic software vulnerabilities present in IT stacks. Most of these attacks are caused due to human errors, absence of attack surface monitoring, overlooking unknown digital assets, and negligence of security teams.
To prevent malicious attacks and data breaches, organizations must employ good cybersecurity measures and practices to continuously discover and monitor their IT assets and protect their attack surface.
The very first step to protect your attack surface is to map known/unknown assets, detect vulnerabilities, prioritize risks and mitigate their impact. Companies won’t be able to prevent their attack surface if they don’t know their exposed endpoints.
A good Attack Surface Monitoring tool will help you discover, monitor, and manage your attack surface to prevent cyber security risks. It offers a helicopter view into your entire risk landscape and systems to detect vulnerabilities and stop attacks before they even occur.
Attack Surface Monitoring Tools FAQs
What should you look for in an Attack Surface Monitoring tool?
There’s a thin line between an attack surface monitoring tool and a vulnerability scanner. Both are NOT the same. Although various vulnerability managers advertise themselves as Attack Surface Monitoring tools, they may lack the required capabilities of an ASM tool.
After thorough research, here are some of the key highlights you need to look for in attack surface monitoring tools:
- Ability to check entire software for security vulnerabilities
- Logging data access by software
- Identify out-of-date software versions
- Reduce the risk of sensitive data exposure or data loss
- Reduce false positives by distinguishing between suspicious and valid user activity
- Protect sensitive data by detecting software vulnerabilities
- Offer risk scoring and security ratings
- Offer Continuous discovery and Continuous security monitoring
- Include Asset Inventory and Classification
What are some tools used for attack surface monitoring?
Some popular tools used for attack surface monitoring include ManageEngine Vulnerability Manager Plus, Rapid7, and Bugcrowd Asset Inventory.
What are some common attack surface areas that should be monitored?
Common attack surface areas that should be monitored include web applications, APIs, network devices, and third-party vendors.
How often should attack surface monitoring be performed?
Attack surface monitoring should be performed on a regular basis, ideally daily or weekly, to ensure that any new vulnerabilities are identified and addressed in a timely manner.
What are the benefits of using automated tools for attack surface monitoring?
Automated tools can help to increase the efficiency and accuracy of attack surface monitoring, allowing organizations to identify potential vulnerabilities and threats more quickly and easily.
What are some best practices for effective attack surface monitoring?
Some best practices for effective attack surface monitoring include having a clear understanding of the organization's attack surface, prioritizing vulnerabilities based on risk, and regularly reviewing and updating monitoring processes.
How can organizations ensure that they have full visibility into their attack surface?
Organizations can ensure that they have full visibility into their attack surface by using a combination of manual and automated monitoring tools, and by regularly reviewing and updating their monitoring processes.
What are some common challenges associated with attack surface monitoring?
Common challenges associated with attack surface monitoring include the complexity of modern IT environments, the sheer volume of potential vulnerabilities, and the need to balance security with business needs.
What are some key metrics that organizations can use to measure the effectiveness of their attack surface monitoring efforts?
Some key metrics that organizations can use to measure the effectiveness of their attack surface monitoring efforts include the number of vulnerabilities identified and addressed, the speed at which vulnerabilities are remediated, and the overall reduction in risk over time.
How can organizations integrate attack surface monitoring into their overall security strategy?
Organizations can integrate attack surface monitoring into their overall security strategy by making it a key component of their risk management program, and by regularly reviewing and updating their monitoring processes to ensure that they are effective and up-to-date.
What role does threat intelligence play in attack surface monitoring?
Threat intelligence can help organizations to identify potential threats and vulnerabilities more quickly and accurately, allowing them to take proactive measures to protect their assets.
How can organizations prioritize vulnerabilities identified through attack surface monitoring?
Organizations can prioritize vulnerabilities based on their potential impact on the organization, the likelihood of exploitation, and the resources required to remediate the vulnerability.
Can attack surface monitoring be outsourced to third-party providers?
Yes, many organizations choose to outsource their attack surface monitoring to third-party providers who specialize in this area, allowing them to benefit from specialized expertise and more cost-effective solutions. However, it's important to choose a reputable and trustworthy provider with a track record of success.