Bill Gates once said having advanced technology in the organization would create a risk-free environment. Don’t you think this is true in any business? Today, we will discuss one such tool that has been helping organizations improve their management for so many years, popularly called “ITIL” (Information Technology Infrastructure Library). In this ITIL guides and […]
ITIL Guide and Best Tools
The Best Small Business Firewalls
Firewalls act as a shield to protect your system and network against cyber attackers. They are the first line of defense that prevents any malicious software or unnecessary network traffic from entering your system via the Internet. It also helps monitor overall traffic and blocks data coming from a few suspicious locations. Here is our […]
How to Troubleshoot Network Connectivity
A single network fault may ruin your whole day; if this problem occurs in large-scale industries, you couldn’t expect what it causes. A network problem is a common everyday issue, and I can’t sit silently without solving it. In this troubleshoot network connectivity post, we will guide you through some valuable concepts that include troubleshooting […]
How to Use GPResult Command to Check Group Policy
Microsoft’s Group Policy is a feature that offers various advanced settings that can be used by network administrators to control the working environment of users and computer accounts in Active Directory (AD). It provides administrators a centralized place to manage and configure operating systems, applications, and user settings. When it is used correctly, it enables […]
The Best Enterprise Password Management Solutions
In the beginning, people had a handful of passwords to unlock web applications. But with time and new web applications, the need for more passwords emerged, and people started finding it difficult to remember them. For most people, it is really hard to remember each credential. Thus, they started reusing the same password for multiple […]
The Best Attack Surface Monitoring Tools
As an organization’s footprint expands, the risk of digital breaches increases as well. Research suggests that 30% of breaches take place due to vulnerabilities or shadow IT assets within the cloud that the IT security team fails to identify. Here’s our list of the best Attack Surface Monitoring Tools: Intruder – EDITOR’S CHOICE Access this […]
Best Secure Web Gateways
Are you looking for the best Secure Web Gateway (SWG) for your enterprise? Multiple SWG solutions can help you secure your enterprise network from malware, ransomware, and other unwanted threats on the internet. A secure web gateway can assist you in shielding your internal company network by preventing and monitoring malicious traffic from different sites […]
Attack Surface Analysis Guide
With the advancements in the digital ecosystem, the risk and complexity of modern-day online attacks and threats have also increased. According to reports, half of the Fortune 500 companies had their employee passwords and email addresses exposed in top hacker forms. The exposure of the employee credentials can provide direct access to vital company information […]
Best Citrix ShareFile Alternatives
File Transfer Protocol (FTP) software is an eminent technology many users across the globe use today to securely and quickly transfer files from one location to another. Sharing files seamlessly with one another via different file communication methods allows you to amass business data and keep it ready for optimization. Citrix ShareFile is a very […]
Best SharePoint Tools
SharePoint is Microsoft’s collaborative platform used for creating websites and sharing data. It is a highly secure portal that helps store documents and files, organizes them, and shares with team members to work together and deliver the best results. One can access data from any device and operate on web browsers like Chrome, Internet Explorer, […]
The Best Service Request Management Software
Over the last few decades, there has been a huge rise in the use of digital services, devices, and applications all across the globe. As a result, the role of IT experts and infrastructure supporting these digital platforms has become more complex. At the same time, the IT experts have been continuously receiving complaints, alerts, […]
The Best Email Security Software
The concept of Email was brought into practice to help people and businesses communicate faster and at a cheaper rate. Over the past many years, emails have been used by every organization. Almost every employee has a personal and professional account to communicate. It has become one of the best sources to transmit all types […]
Business Email Security Best Practices
Protecting a company’s intellectual property is very important to avoid any data leakage to the outer world Business emails are also a main part of organizations as they are used to send or receive important data or conversations over the chat. You know sometimes due to third-party malicious attacks these emails get hacked. Malware, ransom […]
Azure Solutions: IaaS vs. PaaS
With the advancement in technology, many small and large-scale sectors are moving to use cloud services. Using cloud computing services helps users access information and applications whenever and wherever they want to over the Internet. Also, it can add more flexibility and efficiency to various organizations and on-premises IT environments. Microsoft Azure is one such […]
The Best SCCM Alternatives
SCCM is a great system management solution with many advantages. If, however, you are looking for a better alternative, read this post.
The Best JMX Monitoring Tools
If you have to manage and monitor Java applications, the provisions you would need for the activities are Java Management Extensions (JMX). JMX allows a comprehensive management system to track your applications, raise alarms in the form of notifications when the application needs monitoring, and change the status of the application to correct the problem. […]
The Best PII Scanning Tools
In today’s world, identifying an individual personality using the data has become a challenging and quite exciting task. We thought why not provide information on this for our readers to be aware of current trending technologies. Today, we will discuss a more exciting topic: PIII (Personally Identifiable Information), and the best PII scanning tools available. […]
The Best USB Encryption Software Tools
Why do we want to know about data encryption? The answer is simple, to protect your data. One tool commonly used in the PII tools is the “Endpoint Protector”. Endpoint Protector is a data prevention PII, including a USB encryption system to secure the data transfer. In this Best USB encryption software tools post, you […]
The Best USB Port Locking Tools
USB flash drives are considered the handiest and most reliable solution for digitally storing data. They keep all the data secured with the help of USB Port Blocker Software. It is convenient, agile, and can be carried anywhere around the world hassle-free. They are the most light-weighted storage medium that can be used for saving […]
Best Endpoint Encryption Software Solutions
With the rapid increase in data and devices, enterprises need to protect confidential data and prevent expensive data breaches. We often share files with clients and other team members in an enterprise for better communication and proper functioning. What if some unauthorized person tries to hack your data or steal information from your system when […]
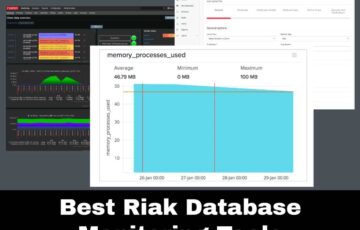
The Best Tools for Riak Database Monitoring
The non-relational database has become relatively very popular today. It has become an essential tool for the enterprise world. Riak is that one database that has always been a fundamental part of the NoSQL database environment. This article will provide you with detailed information on Riak database monitoring and a list of the best tools […]
The Best USB Lockdown Software Tools
USB Lockdown Software is also known as Device control software. These applications protect data against insider threats by controlling and managing data transfers across different removable storage devices. Removable storage devices, such as USBs, smartphones, WiFi network cards, printers, etc., are often used in organizations to easily supply and access information in various formats. However, […]
What is Share and Storage Management for Windows Servers?
Businesses take modern business operations relatively seriously and, for this purpose, implement numerous services or tools for these servers. Earlier, file serving introduced networking to several organizations and continues to remain on the top in the list of business requirements. However, the file server is only the core function handled by the server. There are […]
What Is Cisco Prime Infrastructure?
As an IT professional, you know how daunting it is to simplify your ongoing online responsibility. Also, scaling networks across wired, wireless, and virtual IT environments makes network management more complex by asking network admins to get as much help as possible. Since networks play a pivotal role in serving the employees for administrative purposes […]
The Best Backup as a Service (BaaS) Tools
Data is considered one of the greatest assets of any business. When data is misplaced or disappears from the system, the whole workflow gets devastated. It shows that data is the only thing that no one should ever mess up within the organization. However, one way to secure your data includes Backup as a Service […]
Best AWS EC2 Backup Tools
In the last decade, the world has seen exponential growth in the amount of data. Such is the volume that it has become difficult for some organizations to store and manage critical pieces of information on a regular basis. Here is our list of the best AWS EC2 Backup Tools: Vembu BDR Suite – FREE […]
The Best Database Backup Tools
Database backup tools help companies backup their critical databases to restore them as and when needed. Database backup tools are beneficial for organizations regardless of their size, as it helps mitigate employee errors, corrupted data, and broken hardware. In addition, it ensures your data is always available, even in case of primary database failure. Here […]
The Best MySQL Backup Tools
The MySQL database server has a unique storage-engine architecture, compatible with all major hosting providers, and carries many features that make it a top choice for many companies. For example, MySQL involves efficient management of deeply embedded applications, quick-start capability, robust transactional support, and more such features. In addition, MySQL Database helps deploy cloud-native applications […]
The Best Azure Backup Tools
Microsoft Azure offers amazing products and cloud computing services to run and manage applications on a better level and create the future. Azure Backup is one of the services that include backup options for on-premises and cloud-based workloads, further preventing accidental damage to your data and helping to restore it in the Microsoft cloud. Here […]
Find Device or IP Address Using MAC Address
Every device connected to the network including, printer, switch, router, computer, tablets, and smartphones, has an IP address and Mac address that identify it on a network. Finding a Mac address is very easy if you know the IP address. But what if you don’t see the IP address of a device in a local […]