Web and mobile apps have become a mainstay in our society today. Right from your email application to advanced CRM and AI tools, everything is an application that runs on a server. This pervasiveness of web and mobile applications has also made them a potential target for attacks because they contain sensitive information like credit card details, date of birth, etc. of customers. Cybercriminals gather this information to perform financial frauds, identity thefts, and more.
Cybercriminals typically hack through a vulnerability in the application. To avoid such attacks, organizations must identify these vulnerabilities, and address them before the app is released to the world. This is where Application Security Testing (AST) comes into play.
Here is our list of the best AST tools:
- Invicti A comprehensive tool that builds security in every step of SDLC to make your applications secure while eliminating additional time and escalating development costs.
- Acunetix An end-to-end web security scanner that provides a 360-degree view of app security to provide complete control and visibility.
- Veracode A software security tool that continuously scans and fixes issues during the entire SDLC.
- Sonar A SAST tool that reviews and offers in-depth explanations and next steps to address the identified vulnerabilities.
- Checkmarx A cloud-native platform that offers the full range of AST tools to create secure applications quickly.
- Synopsys An application security and quality analysis tool that addresses security and quality defects while seamlessly integrating with your DevOps environment.
Read on as we talk about AST and a brief review of the best tools to help you create the most secure apps.
What is Application Security Testing?
Application Security Testing (AST) is the process of rigorously testing applications, often from the developmental stages, to ensure that vulnerabilities are identified and addressed immediately. This proactive approach reduces the chances for malicious actors or programs to attack the app.
Many strategies are a part of this AST. During the development process, Dynamic Application Security Testing (DAST), Interactive Application Security Testing (IAST), and Static Application Security Testing (SAST) are used. Each of these tools examines different aspects of the code to identify potential problems. DAST, for example, is a tool that tests how an application interacts with the outside world and examines if criminals can carry out attacks through certain inputs. Similarly, IAST analyzes the code while the app is running while SAST examines the source code to prevent attacks like SQL injection.
Besides these development testing tools, organizations also use other strategies like penetration testing and vulnerability scanning in the later stages of the development lifecycle.
The DAST, IAST, and SAST tools are being increasingly used by organizations because they catch errors during the development phase itself and can be integrated into the Software Development Life Cycle (SDLC) process. As a result, there are no major delays or cost escalations.
This growing importance has also led to an increase in the number of AST tools available today. Let's look at the best ones.
The Best Application Security Testing Tools
Read on for a quick look into the capabilities of each of these tools.
1. Invicti
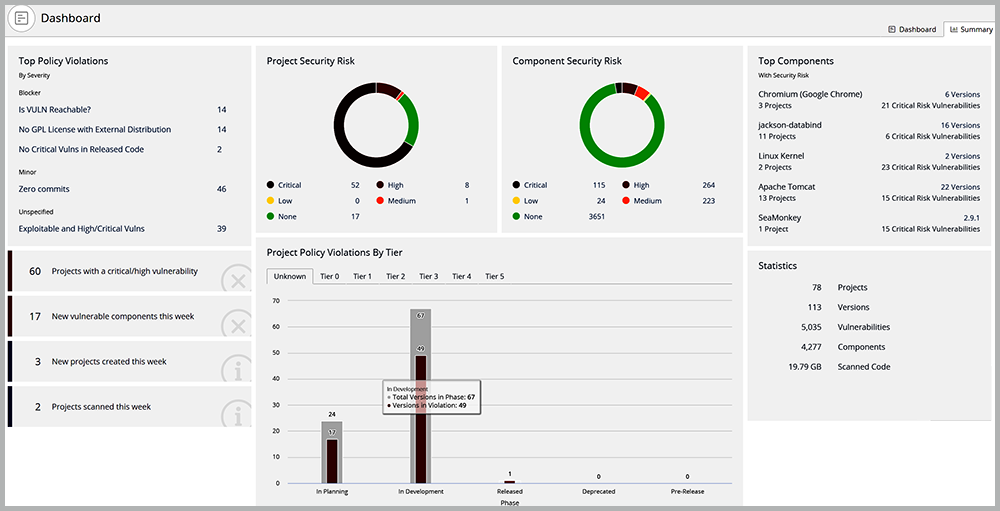
Invicti is a comprehensive AST tool that continuously scans every bit of your app to detect vulnerabilities and report them. Moreover, this tool provides the context and insights to help developers understand the root cause of the problem, so they can be fixed easily.
Key Features:
- Provides Comprehensive Visibility: When organizations have many web apps, it's hard to keep track of all of them. To help you stay on top of all apps, Invicti uses an advanced crawling strategy that's a combination of both DAST and IAST approaches to check for vulnerabilities. It can also scan web APIs and open-source code, regardless of the technology or platform on which they were built. Such extensive scanning makes it easy to identify any potential vulnerabilities.
- Automates Resolution: Invicti comes with automation and predefined workflows to not just identify issues but also resolve the simple ones automatically. Also, its patented proof-based scanning feature reduces false positives, so your team can better prepare and prioritize resources efficiently for fixing the identified issues. Furthermore, Invicti provides detailed documentation and the likely part of the source code causing the problem, so developers can fix the issue quickly. All these aspects can save time, effort, and money for your organization.
- Integrates with Your Development Tools: Another advantage of Invicti is that it seamlessly integrates with many leading tools and platforms like Jenkins, Bugzilla, Azure, and more. As a result, your developers can get feedback while coding. Also, the issues can be raised as tickets and their progress tracked as a part of the SDLC process.
Overall, Invicti is a comprehensive AST tool that uses a structured approach to identify vulnerabilities lurking in any part of your web app.
Invicti offers two editions, Pro and Enterprise. For pricing details, contact the support team for a quote. You can watch a demo and try the product for free for a limited time.
2. Acunetix
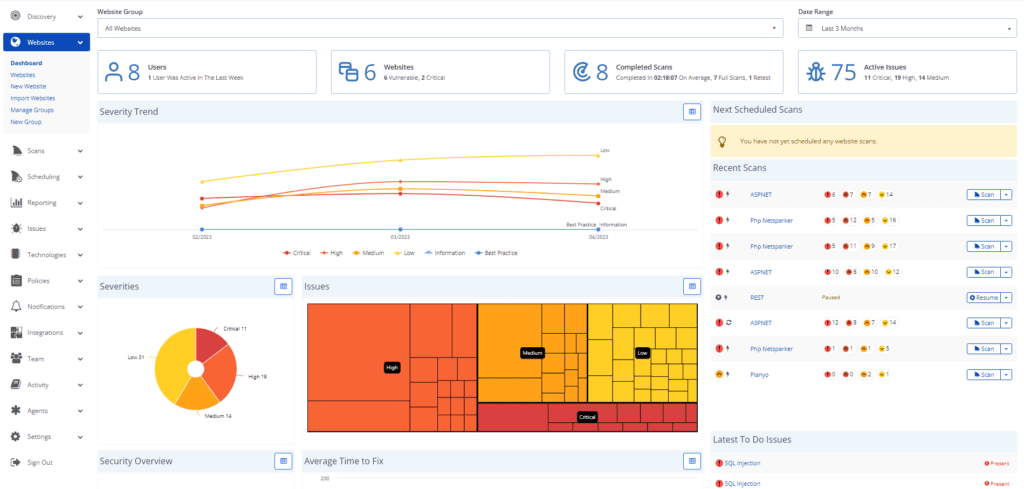
Acunetix is an end-to-end vulnerability scanner that automates your web application security to reduce the attack surface. Though Acunetix is also powered by Invicti, this product is more suited for small businesses that take a more hands-on approach to testing and security.
Key Features:
- Comprehensive Scanning: Like Invicti, Acunetix also scans every part of every web app, so all entry points are scanned. It scans SPAs, script-heavy sites, applications built on JavaScript and HTML5, unlinked files, and other vulnerable aspects that most testing strategies can miss. Needless to say, this approach reduces the attack surface and the resulting vulnerability. Since Acunetix works well with websites, applications, APIs, and mobile apps, it's a one-stop solution for your organization's IT offerings.
- Integrates Security Into Development: Acunetix integrates security into the development process to make it easy for developers to identify the problem-causing source code and fix it. It offers extensive root-cause analysis to improve the overall code quality within your organization. Furthermore, it integrates with ticketing tools like Jira for creating and tracking the progress of each fix. Plus, Acunetix reduces false positives, so your developers can focus on the most pressing issues first.
- Automation Saves Time: Another advantage with Acunetix is that it continuously scans your apps, even during off business hours, and remediates the first level fixes. In case of serious issues, it sends alerts right away, and depending on the priority of the alert, developers are intimated. Such use of automation provides extensive security to your apps at all times while saving time and effort.
In all, Acunetix is a top-notch vulnerability scanner that can identify problems in every corner of your app before they are exploited by cybercriminals.
Acunetix provides pricing details upon request. You can also watch a demo of the product.
3. Veracode

Veracode is a development testing tool that secures code during every phase of development. It can scan over 100 languages and frameworks to find flaws, prioritize, and fix them at the earliest. Veracode also supports contextual learning for developers.
Key Features:
- Extensive Scanning: Veracode offers DAST and SAST tools for your organization, and you can even choose to subscribe to both of them for comprehensive scanning and analysis. The SAST tool is helpful for end-to-end static scanning as it combs through your code at every stage of development. Specifically, it uses IDE, pipeline, and policy scans to find flaws in your code that can open up future vulnerabilities. Its DAST offering, on the other hand, scans hundreds of web apps and APIs simultaneously to find issues in both the production and staging environments. Together, both tools ensure that your code is free of errors.
- Meaningful Insights: Another key aspect of Veracode is the relevance and value of its insights. It reduces false positives, to less than 1.1% as mentioned on its website. Moreover, its DAST tool combines crawling and auditing together in the same scan and even comes with easy-to-configure parameters that save time and effort. You can also have granular control over your scans with its flexible and easily configurable settings. All these scans provide meaningful and relevant insights that developers can use to understand the problem and fix the issue easily.
- Scalable and Extensible: Veracode uses a cloud architecture that can scale well with your growing business. Its scan engine is also cloud-native and this means, it scans hundreds of apps and APIs simultaneously without impacting performance. This tool is also highly extensible as it integrates with 40+ development tools across the IDE and CI/CD areas, to give developers a wide range of options.
Overall, Veracode is a developer-friendly tool that can identify flaws across your SDLC, so they can be fixed during the developmental phases.
For Veracode, contact the sales team for pricing details and request a demo to see how the platform works.
4. Sonar

Sonar is a SAST tool that continuously scans your source code to detect vulnerabilities, explain them to the developers, and even suggest the next steps for easy remediation. By scanning code through the development lifecycle, Sonar ensures your applications run on clean and vulnerability-free code.
Key Features:
- Comprehensive Code Analysis: Sonar comes with extensive SAST capability to identify code violations not just in the app's code, but also issues that originate due to interactions with third-party open-source apps and libraries. The advantage of this capability is you can trace the flow of data as it moves through libraries and your source code, and detect vulnerabilities that are otherwise hard to spot.
- Different Types of Threats: With its ability to detect a wide range of threats, Sonar can identify threats like SQL injection, cross-site scripting, file manipulation, misconfigurations, crypto API misuse, and more. It supports more than 30 programming languages and frameworks and ensures that your code meets standards like PCI DSS, OWASP Top 10, CWE Top 25, and more.
- Sanitizes User Data: Sonar sanitizes all user data before it interacts with critical aspects like databases and file systems. This process ensures that malicious actors can't send infected inputs to compromise your system. Its taint analysis also tracks these inputs across your entire system as it moves from file to file to add another layer of security to user inputs.
In all, Sonar provides maximum protection for your code with its scan, security, and taint analysis.
Sonar offers both self-managed and cloud service options. The self-managed option includes three pricing editions: Developer at $150 per year, Enterprise at $20,000 per year, and Data Center at $130,000 per year. The cloud service starts at 10 Euros per month for 100,000 lines of code. You can try Sonar as both a cloud service and a self-managed platform with a free trial.
5. Checkmarx

Checkmarx is a cloud-native platform that offers comprehensive application security testing capabilities to secure your application across every phase of development and deployment. Also, the platform is intuitive and easy to use and provides valuable insights to both developers and security teams to help stay on top of any vulnerability.
Key Features:
- Offers Comprehensive Protection: Checkmarx protects all aspects of your application and its code through its many offerings like SAST, DAST, API security, infrastructure as code security, supply chain security, and more. All these offerings work together seamlessly to secure your application.
- Quick Identification and Fix: The unique Fusion Engine from Checkmarx correlates the findings from the different tools to easily identify vulnerabilities and prioritize them based on their criticality to your operations. It can also identify issues in open-source software and libraries. All this information is presented on a dashboard to make it easy for your developers to fix and track them.
- Reduces Overheads: Checkmarx's unified dashboards display all the information you need in a single place. You can even automate actions and workflows through this dashboard, and Checkmarx will implement them. You also have the option to rank your applications based on their deadlines and priorities, and Checkmarx will automatically adjust the priorities of vulnerabilities to match your changing preferences and business needs.
In all, Checkmarx helps you to build secure applications quickly and efficiently.
For Checkmarx, you can contact the support team to get a custom quote and request a demo to explore the platform’s features.
6. Synopsys
Synopsys is an application security and quality analysis tool that identifies a wide range of security and quality defects in your proprietary source code and third-party open-source binaries and libraries. It takes a comprehensive approach to identify issues in applications, containers, APIs, and protocols, to ensure that your code is secure.
Key Features:
- Combined Capabilities: Synopsys combines multiple technologies like SAST, IAST, DAST, Software Composition Analysis (SCA) penetration testing, protocol fuzzing, and more to identify potential vulnerabilities in your code. Moreover, you can customize these capabilities to suit your DevOps, developers, and security teams' needs.
- Minimizes Business Risk: Safe and secure code is essential to minimize business risks later on. This is why Synopsys checks your code as it is being developed to identify issues as they emerge. Such a proactive approach can reduce business risks and at the same time, make it easy for developers to fix issues.
- Role-based Security: Every individual in an organization has a role to play in ensuring overall security. Synopsys makes it easy to assign specific responsibilities to each role, so there are clear responsibilities and outcomes.
In all, Synopsys helps to secure your applications and their code, all the way from the first line to code to the eventual deployment.
For Synopsys pricing details, contact the sales team for a custom quote. Additionally, you can download an overview of Synopsys to explore its features and offerings.
Thus, these are some of the best AST tools that can elevate your application's security and code quality to greater heights.
Bottom Line
To conclude, AST tools are an essential part of your development process, as they help identify and fix vulnerabilities as the application is developed. As a result, there's no back-and-forth communication and the entire security process is baked into an application's SDLC. The outcome is secure apps and faster time to market – a win-win combination for any organization. The tools described in this article are some of the best ones today, and we hope this information comes in handy to select the tool that best aligns with your organization's needs.