What is Active Directory?
Active Directory is a Microsoft product that operates on Windows Server. It is a database and set of services developed to help you with access, management, and permissions for your network resources. The organizational data is stored as an object in the Active Directory, and it can be in the form of devices, files, users, applications, groups, or shared folders. In addition, these objects can be categorized by their name or attribute.
The directory or database stores critical information related to your IT environment, including essential details about users, user permissions, and computers. In short, it helps you control various activities going on in your IT environment. Most importantly, AD also ensures user authentication, generally via user ID and passwords, and allows them to access data they’re authorized to use.
How does Active Directory work?
In the AD, the domain is the primary unit in a logical structure. The objects named under the same directory database, trust relationships, and security policies with other domains are called Domains. Each domain will store data about objects belonging to that domain only.
Settings and security policies, for example, Access Control Lists (ACLs), admin rights, etc., do not pass from one domain to another. In short, the admin can set policies only for the domain they belong to. Domains allow admins to set boundaries for objects and handle security policies for shared network resources.
One of the primary Active Directory services is the AD DS (Active Directory Domain Services), a crucial part of the Windows Server OS. The AD DS runs on servers known as Domain Controllers (DCs). An enterprise usually has multiple DCs, and each of these controllers has a copy of the main directory for the domain. Any changes made to the directory on one DC- for example, deleting a user account or changing a password are all applied to the other DCs in a domain to keep them up-to-date.
Another DC called Global Catalog server stores a copy of all objects within a directory of its domain along with a partial copy of all objects of other domains within a forest. This allows applications and users to find objects in any domain of its forest quickly.
Other laptops, desktops, and devices that run Windows (instead of Windows Server) do not run AD DS, but they can be a part of an Active Directory environment.
AD DS depends upon standards and protocols, such as DNS, Kerberos, and LDAP (Lightweight Directory Access Protocol). An important thing to know is that AD is exclusive to On-prem Microsoft environments. To run it in cloud Microsoft environments, you need to use Azure Active Directory, which works similar to the On-prem variant. Azure AD and AD are different but can run together if an organization has a hybrid deployment (cloud and on-prem).
Why is Active Directory So Important?
To simplify and understand the concept of AD better, consider Active Directory as the “Contacts” application on your mobile phone. The Contacts app itself acts as an Active Directory, while individual contacts in the app would be its “objects”. The values stored in each object, such as phone number, address, email, etc., would be your Active Directory. The only difference is that objects like in the mobile app aren’t just limited to people, but AD may also contain group objects such as printers, computers, devices, etc.
Active Directory is vital for organizations as it helps you efficiently manage company users, computers, devices, and applications. For example, IT managers can leverage Active Directory to systematically organize company data in a hierarchy structure, which states which users or computers belong to which network, or which users have access to which network resources, and so forth.
How to Setup Active Directory Domain Controller?
A domain controller contains many computers on the network and allows the system administrators to manage them from the central place. It is a server or computer used to authenticate other computers throughout the network. It stores the login credentials of all other computers and printers in the network.
This section will show you how to install Active Directory Domain Services and set up a domain controller on Windows server 2019.
Follow the below steps to install Active Directory Domain Services:
Step 1 – Login to Windows server 2019 as an administrator and open the Server Manager as shown below:
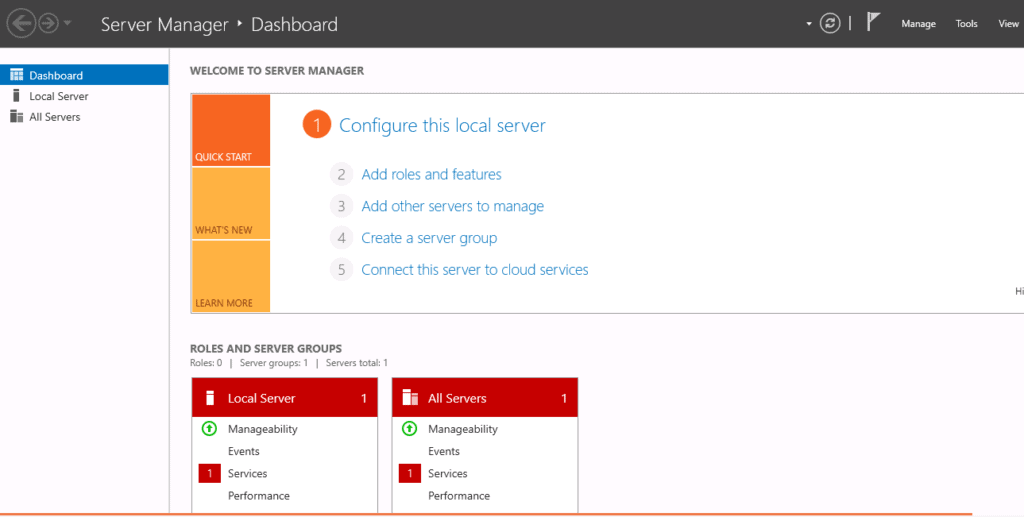
Step 2 – Click on the Add Roles and Features. This will open the Add Roles and Features Wizard as shown below:
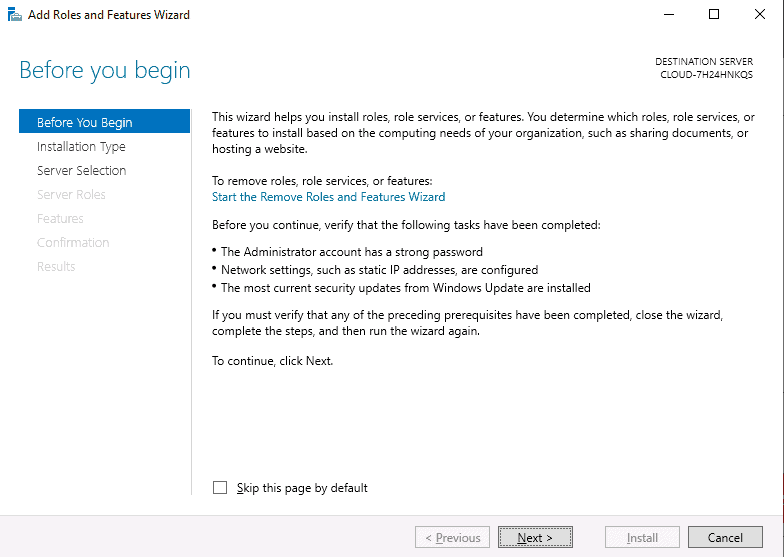
Step 3 – Click on the Next button. You will be asked to select the installation type as shown below:
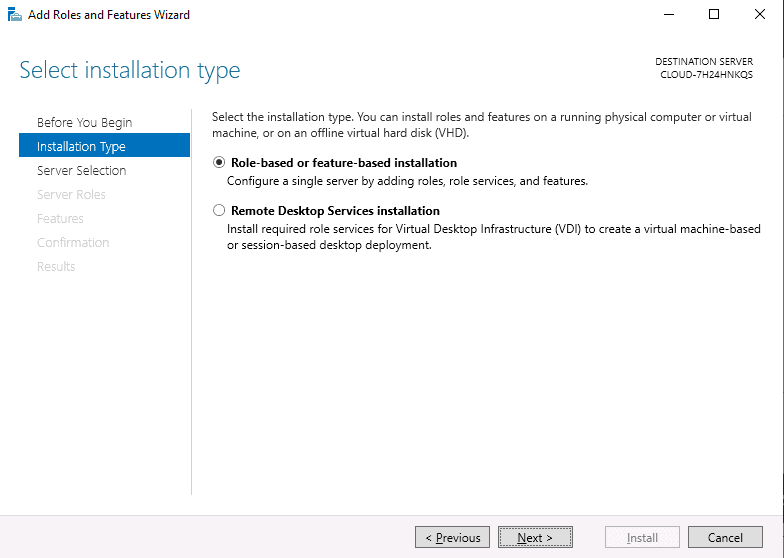
Step 4 – Select Add Roles and Features Wizard and click on the Next button. Next, you will be asked to select a destination server as shown below:
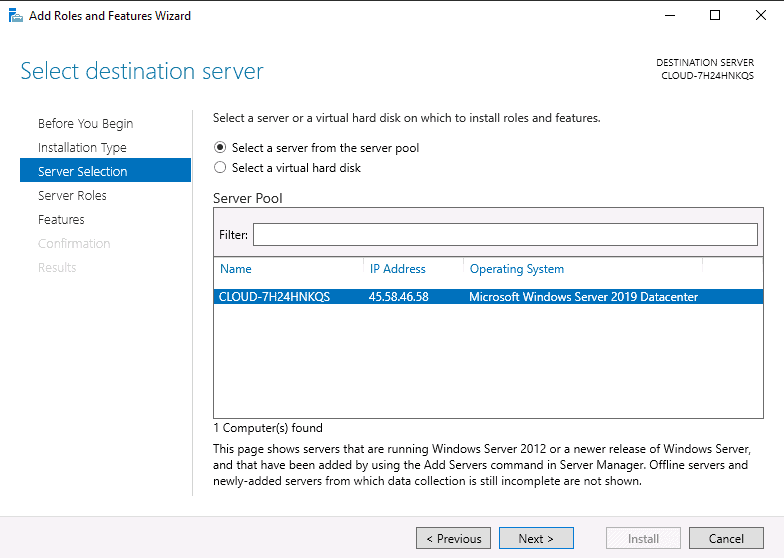
Step 5 – Select “Select a server from the server pool” and click on the Next button. Next, you will be asked to select server roles as shown below:
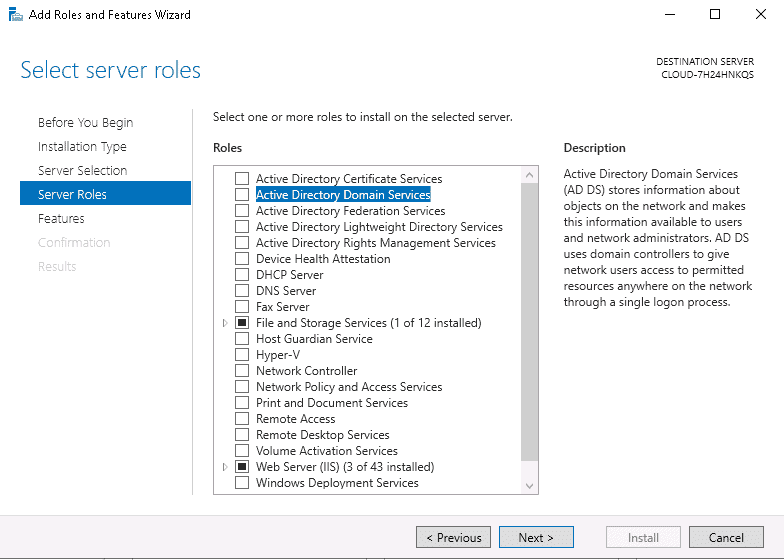
Step 6 – Select Active Directory Domain Services and click on the Next button. You will be asked to select features as shown below:
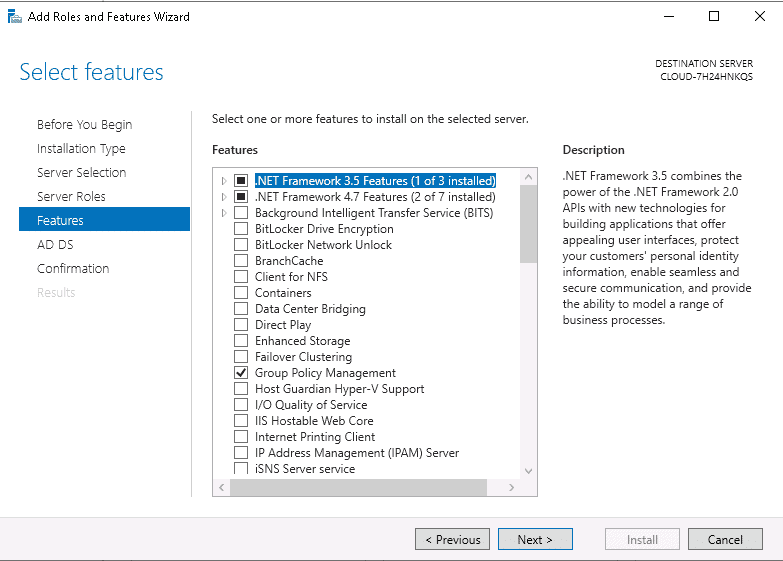
Step 7 – Leave all default settings and click on the Next button. Next, you should see the confirm installations selections page.
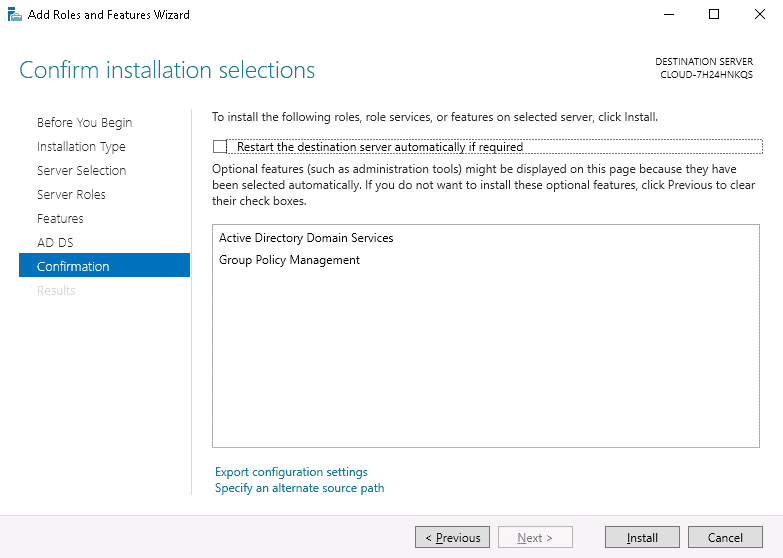
Step 8 – Click on the Install button to start the installation. Once the installation has been finished. You should see the following page.
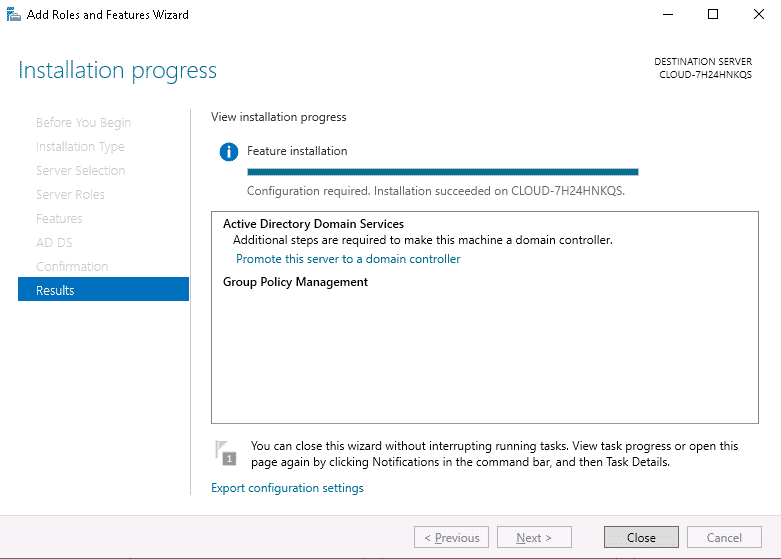
Step 9 – Click on the Close button. You should see the following page.
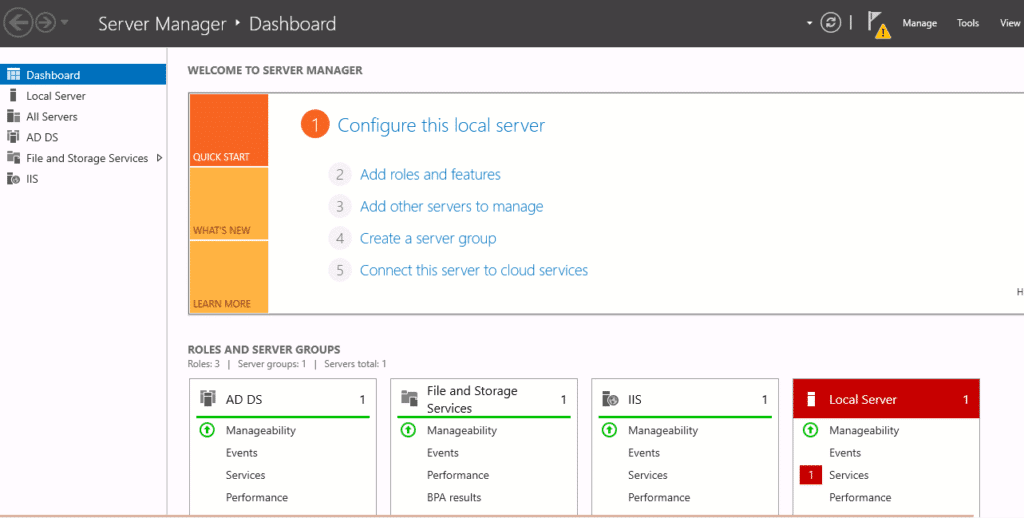
Step 10– Click on the yellow notification icon. You should see the following page:
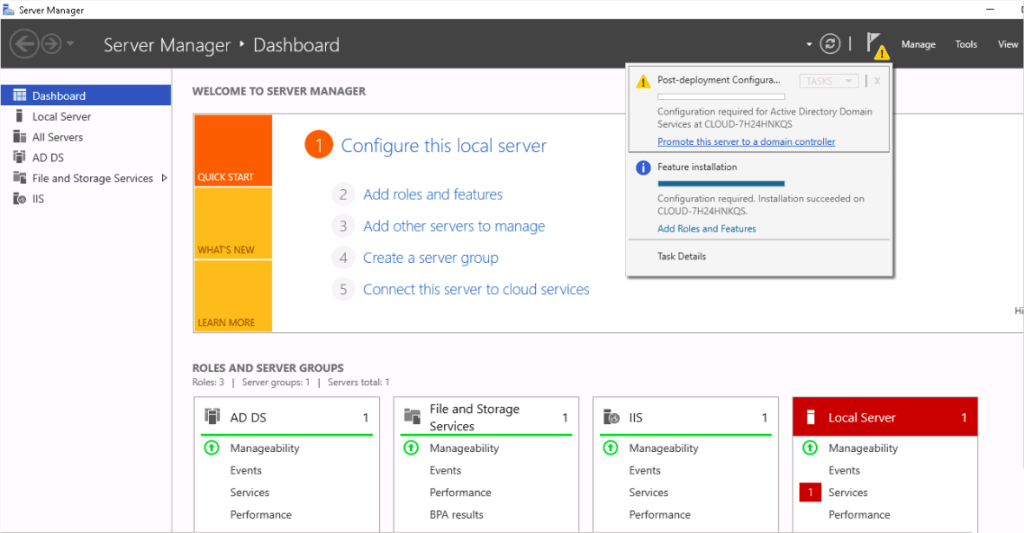
Step 11 – Click on Promote this server to a domain controller. You should see the deployment configuration page:
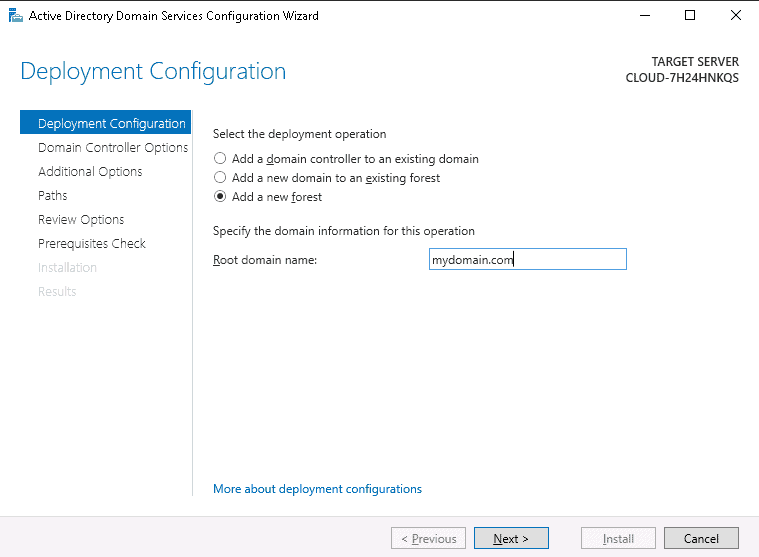
Step 12 – Select add a new forest, define your domain name and click on the Next button. You should see the domain controller options page:
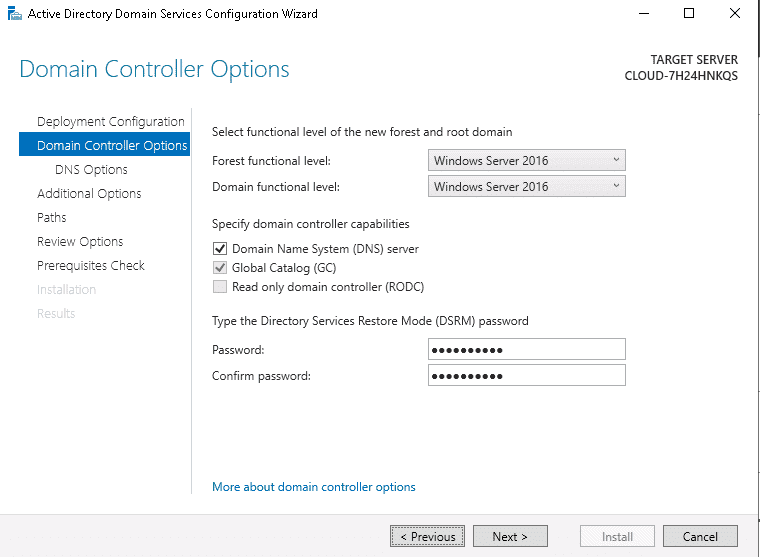
Step 13 – Define your directory service restore mode password and click on the Next button. You should see the DNS options page:
Step 14 – Leave the default configuration and click on the Next button. You will be asked to set a NetBIOS name as shown below:
Step 15 – Set your NetBIOS name and click on the Next button. You will be asked to define AD DS database path location:
Step 16 – Leave the default path as it is and click on the Next button. You should see the review all options page:
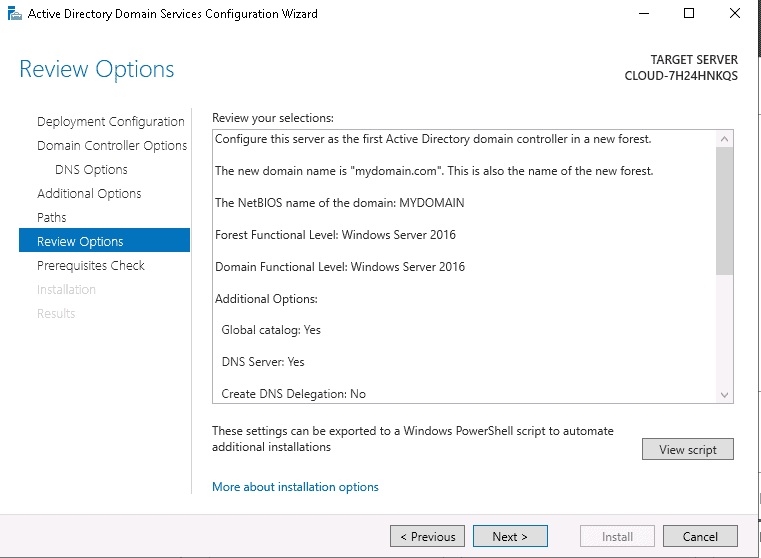
Step 17 – Review all the configurations and click on the Next button. You should see the prerequisites check page:
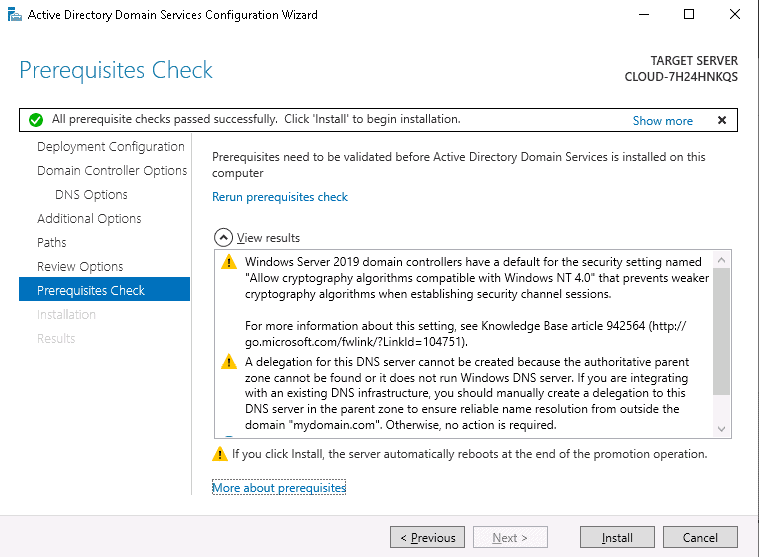
Step 18 – Make sure all prerequisite checks are successfully then click on the Install button. Once the installation has been finished, your system will be restarted automatically.
Verify Domain Controller
Next, you will need to verify whether the Domain Controller is adequately set up or not. Again, you can prove it from PowerShell.
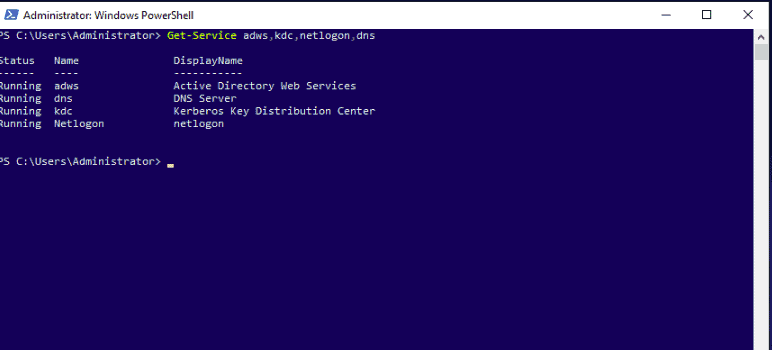
To confirm the successful installation of the services, run the following command on Windows PowerShell.
Get-Service adws,kdc,netlogon,dns
You should see the status of all services on the following screen:
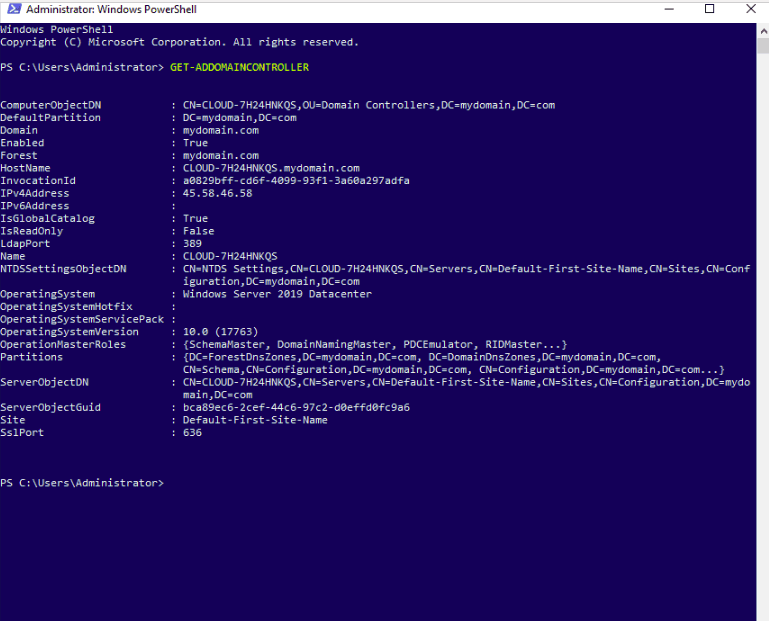
To display all the configuration details of the domain controller, run the following command:
Get-ADDomainController
You should see all the information on the following screen:
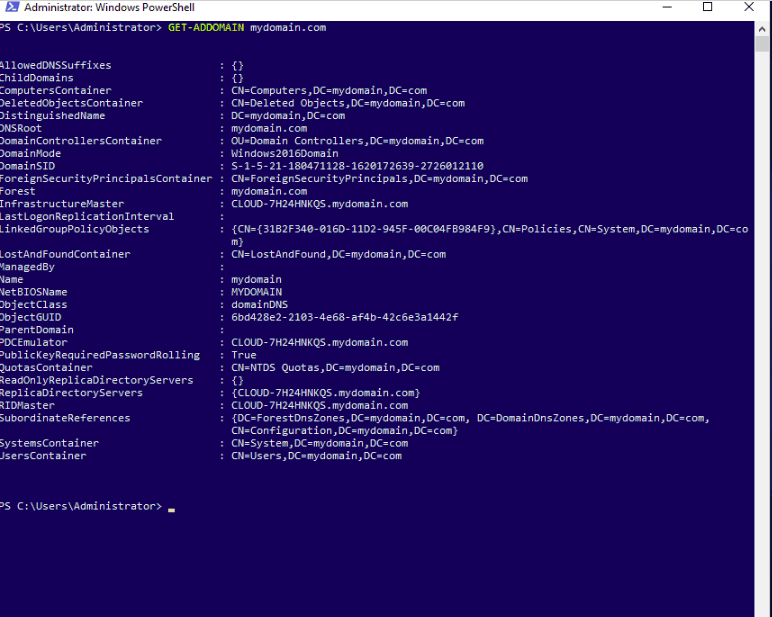
To get detailed information about your domain, run the following command:
Get-ADDomain mydomain.com
You should see the next screen:
To display your Active Directory Forest details, run the following command:
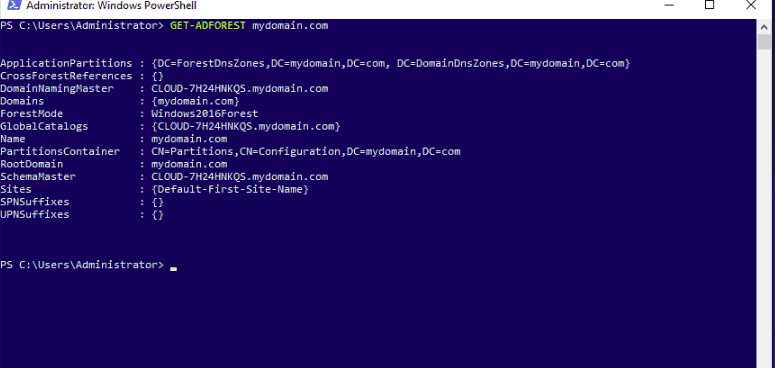
Get-ADForest mydomain.com
You should see the next screen:
Create Active Directory Users
After setting up the Active Directory Domain controller, you must create users for the network computers. So that all users are login to the Active Directory Domain Controller from the network computer. You can create a user, group, and computer using the Active Directory Users and Computer tool.
Follow the below steps to create a new user on Active Directory:
Step 1 – Open the Server Manager, go to the Tools menu and select Active Directory Users and Computers as shown below:
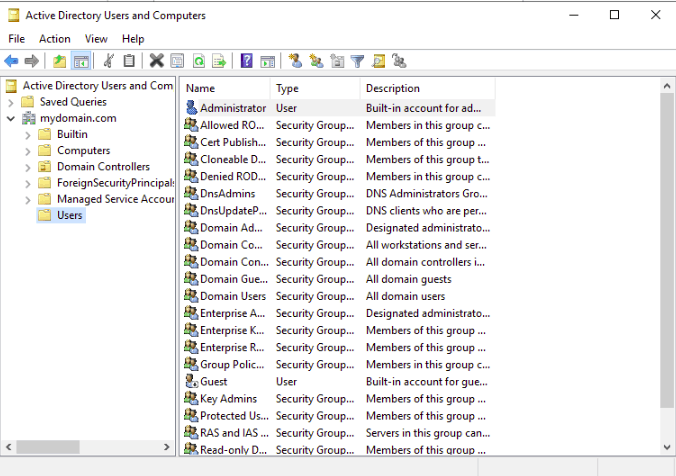
Step 2 – Right-click on the Users. You should see the following page:
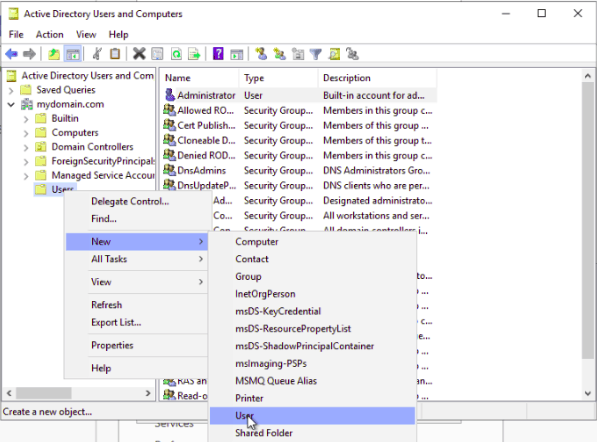
Step 3 – Click on the New => User. You should see the following page:
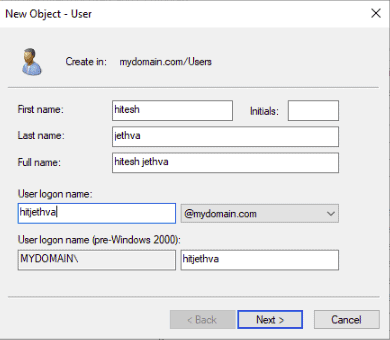
Step 4 – Provide your First name, Last name, Logon name, and click on the Next button. You should see the following page:
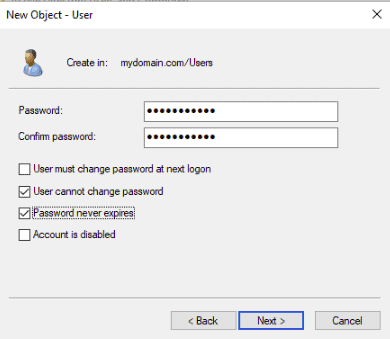
Step 5 – Set your password and click on the Next button. You should see the following page:
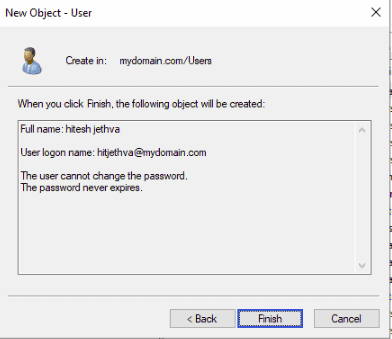
Step 6 – Verify your user information and click on the Finish button.
Install Active Directory Remote Server Administration Tools
Active Directory Remote Server Administration Tools (RSAT) is a handy tool that allows the system administrators to manage Active Directory Domain Controller on a windows server from a computer running Windows 10 or other servers.
RSAT tools set can manage the following service running on the Windows server:
- Server Manager
- Consoles
- Microsoft Management Console (MMC) snap-ins
- Windows PowerShell cmdlets and providers
- Command-line tools to run features on Windows Server
- IP Address Management (IPAM) Tools
- DHCP Tools
- Routing and Remote Access Tools
- Network Policy Server Tools
Follow the below steps to install the RSAT tool on Windows Server 2019:
Step 1 – Open the Server Manager as shown below:
Step 2 – Click on the Add roles and features. You should see the following page:
Step 3 – Select Role-based or feature-based installation and click on the Next button. You should see the following page:
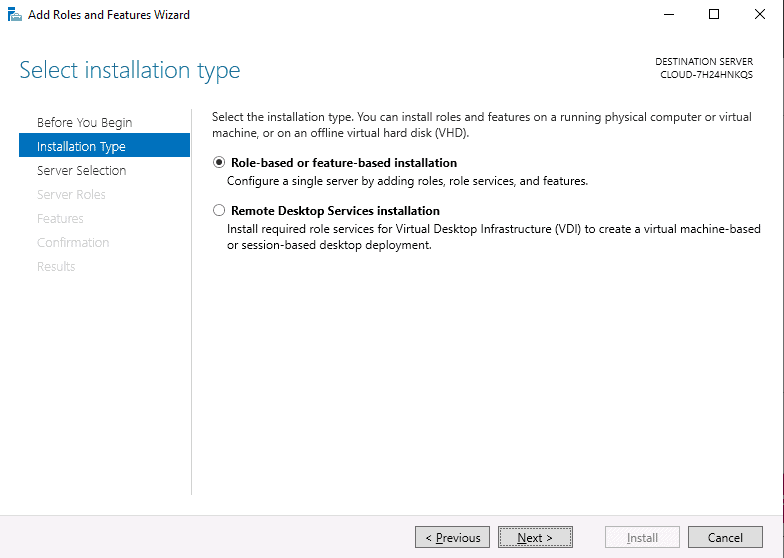
Step 4 – Select “Select a server from the server pool” and click on the Next button. You should see the following page:
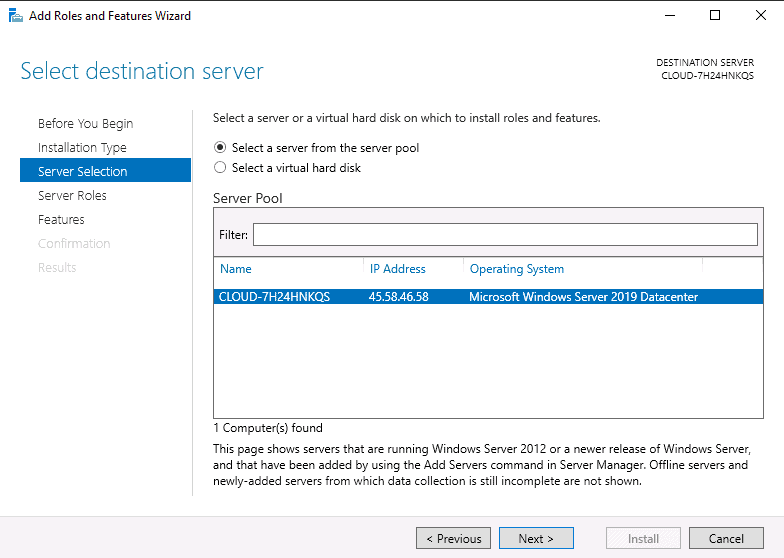
Step 5 – Select “Remote Server Administration Tools” and click on the Next button. You should see the following page:
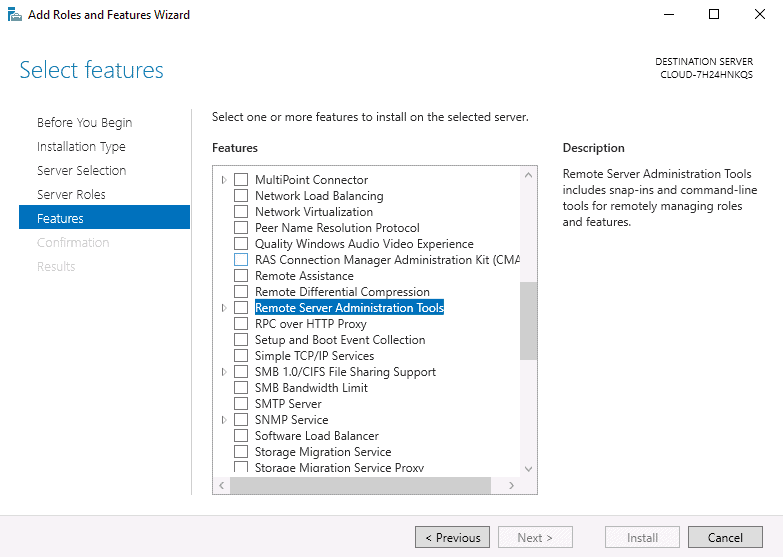
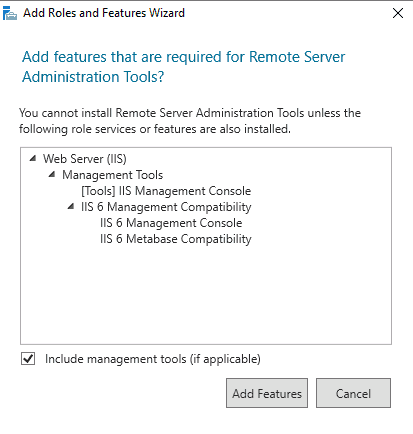
Step 6 – Click on the Add Features. You should see the following page:
Step 7 – Click on the Next button. You should see the following page:
Step 8 – Leave the default settings and click on the Next button. You should see the following page:
Step 9 – Confirm all settings and click on the Install button. Once the installation has been completed, click on the Close button to exit the window.
Step 10 – Now click on the Server Manager => Tools to access the RSAT as shown below:
What Are Active Directory Domain Services?
Active Directory Domain Services (AD DS) is one of the core directory services offered by AD. The main objective of AD DS is to employ authentication and authorization for easier management of access controls for network resources. It is the foundation of your Windows domain network. AD DS will store information about domain members, such as users/devices, verify their credentials and define their rights to access. Domain controller runs this service. Whenever a user logs into a device or tries to access another device in a network, the domain controller is alerted.
Multiple unique services fall under the category of AD DS to manage permissions, identities, and access rights to network resources. These services are as follows:
- Active Directory Certificate Services (AD CS) AD CS is a server role with which you can create a PKI (Public Key Infrastructure) and provide digital certificates for your company. These certificates can be used to authenticate computers and users and encrypt network traffic and application traffic. For example, if you see a browser address with “https”, the “s” stands for security certificate that it uses to encrypt the established communication between server and client.
- Active Directory Federation Services (AD FS) With AD Federation Services, you can employ single sign-on to external systems such as applications and websites. One typical example of the use of AD FS is Office 365. When a user signs in to Office 365, the user ID and password are redirected via the federation server to check whether the entered credentials are authentic against your On-prem AD. This is how it provides authentication to external systems through the local Active Directory.
- Active Directory Lightweight Directory Services (AD LDS) AD LDS offers directory services with the help of LDAP protocol without having to deploy any DCs. The service is used to provide directory service functionally to directory-enabled applications. But, it does not replace AD DS.
- Active Directory Rights Management Services (AD RMS) The service allows you to protect information within digital content. It secures the documents by defining which users can modify, open, view, print, forward, or take similar documents. For enhanced security, you can use local certificates to encrypt documents.
The Hierarchical Structure of Active Directory Domain Services
AD DS systematically organizes company data in a hierarchy that contains domains, trees, and forests. Here’s what the hierarchical structure of AD DS comprises of:
- Domains: A domain contains objects such as devices, groups, and users that fall under the same AD database. Think of a domain as a branch of a tree. A domain will have a structure the same as that of standard domains and subdomains.
- Trees: A tree is formed by grouping one or more domains in a logical hierarchy. All domains within a tree are logically linked; hence they “trust” each other.
- Forest: A forest is a topmost level in the Active Directory of your organization. It contains one or more trees grouped. Trees within a forest are also said to “trust” each other and share catalogs, directory schemas, domain configurations, and application data.
- Organizational units: Organizations Units or OU are used to organize groups, users, computers, and other entities.
- Containers: A container is almost similar to an OU; the only difference is that you cannot link a GPO (Group Policy Object) to a generic container within AD.
Introduction to Active Directory Forests and Trees
An object is a physical element present within a network, and an AD can have multiple objects. Two such objects are Forest and Tree.
Forests
A Forest comprises multiple grouped trees that share a standard global catalog, directory schema, logical structure, and configuration. It features two ways transitive trust relationships by default. The first and foremost domain created within a forest is known as the forest root domain.
In the case of different naming schemas, Forests allows organizations to group their divisions which may need to operate individually. But a company seeks to communicate with their various departments through transitive trusts and share the same schema and configuration container.
Tree
A tree features a group of one or more domains that allow the user to share resources globally. Single or multiple domains exist here in the contiguous namespaces. If you add a domain in the tree, it will become the child of the tree root domain, while the domain it is linked to becomes the parent domain. The child domain utilizes the parent domain’s name and attains the unique DNS (Domain Name System).
For example, if sbs.com is a root domain, you can create one or more child domains to this parent domain, such as sales.sbs.com or transfer.sbs.com. These child domains can also further have sub-child domains such as xyz.sales.sbs.com.
The domains within a tree have a two-way relationship, also known as Kerberos transitive trust relationship. For example, a Kerberos transitive trust implies that if Domain 1 trusts Domain 2, and Domain 2 trusts Domain 3, then Domain 1 trusts Domain 3 as well. In short, it means that a domain added to a tree will immediately establish trust relationships with every other domain inside that tree.
Difference between the Forest and the Tree
The Forest in an Active Directory sits at the highest level and contains multiple trees, while the Tree in an AD includes one or more domains.
Active Directory Trust Relationships and Types
A trust relationship is the formation of a logical link between two domains. One of them is known as the trusting domain, and the other is called the trusted domain. With a trust relationship, the trusting domain will honor the login authentication of the trusted domain.
Usually, the trusted domain stores the users, while the trusting domain comprises network resources. Thus, the users in the trusted domain are trusted and are allowed to access resources stored in the trusting domain.
Trusts can be created manually or automatically. These trusts are further classified into two categories viz—transitive and non-transitive trust. Transitive trust simply implies that if Domain 1 trusts Domain 2 and Domain 2 trusts Domain 3, then Domain 1 trusts Domain 3 as well. Non-transitive trust means that if Domain 1 trusts Domain 2, and Domain 2 trusts Domain 3, then Domain 1 DOES NOT trust Domain 3.
Trusts can further be one-way or two-way. Following are the types of trust relationships that are either one-way or two-way by default:
- Tree-root trust A tree-root trust implicitly forms when a user adds a new tree root domain within a forest. Only the domains at the topmost part of each tree can take part in the tree-root trust. Tree-root trust is a type of two-way transitive trust that is formed automatically.
- Parent-Child trust When a user adds a child domain in a tree, a parent-child trust relationship is implicitly formed. The DCPROMO process will automatically create a parent-child trust relationship in a DNS namespace hierarchy between the new domain and the preceding domain. This type of trust is a two-way transitive trust formed automatically.
- Shortcut trust A system admin manually needs to create a shortcut trust between two domains within a forest. This type of trust is often made in extensive forests to enhance user logon time, specifically for users who logon into computers of other domains within the forest. It is a transitive type of trust, and you can configure it as one-way or two-way.
- External trust A system admin creates an external trust between two domains belonging to different forests or between a domain in an AD forest and a domain in Windows NT 4.0 or earlier version. This type of trust is commonly created when users migrate resources from a Windows NT 4.0 domain to another domain in an AD. It is a non-transitive type of trust, which can be either one-way or two-way.
- Forest Trust A system admin creates a forest trust explicitly between two forest root domains (functional for Windows Server 2003 and later domains). Such a type of trust allows all domains in one forest to trust all domains in another forest. Though it is a transitive trust, it will not be transitive against three or more forests. And it can either be one-way or two-way.
- Realm Trust A system admin may create a realm trust explicitly between a Windows 2003 or later domain and a non-Windows Kerberos realm. This type of trust can be one-way or two-way and transitive or non-transitive.
Those were the core types of trust relationships in an Active Directory. Organizations need to have precise planning in place for trust relationships to ensure users get timely access to network resources they need.
Active Directory setup FAQs
What is Active Directory basics?
Active Directory is a Windows Server utility that controls access rights to system resources. There are two elements to the connection between a user and a resource. The first is credentials management of each user account and the second is a link from each account to a specific resource and the level of access permission granted. Each user will have access rights to many resources. The concept of user groups makes the allocation of access rights a lot easier. Rather than mapping each user account to each resource, the user is allocated to a group and then the permissions of the group to access a list of resources is mapped. Inheritance within the access rights system means that a group member gains all the access rights that are allocated to the group.
What is Active Directory structure?
Active Directory is structured in a hierarchy of three levels. Each collection of access rights definitions is called a Domain. The identity of this package is called a Domain Controller. The Domain Controller is based on a single database instance. Domains can be grouped together in a tree. The tree is like a circle of trust. All of the domains that belong to the same tree share a catalog, so a domain can be thought of a subdivision of the global catalog. For example, each department in a business could be a domain, which contains some of the users that are members of the business. A forest is a collection of trees that use a common catalog be guard different systems. For example, one tree might control on-premises access and the other, a SaaS platform’s accounts that give employees on the site access to the cloud platform’s services.
What are the 4 most important benefits of Active Directory?
Active Directory provides management of four resources:
- Security certificates
- Single Sign-On (SSO)
- Lightweight Directory Access Protocol (LDAP)
- Access rights management (ARM)




