Cybercriminals use innovative ways to hack devices and networks and hence, organizations must examine every data packet that enters their system to avoid ransomware and malware attacks. At the same time, hackers are also learning to work around these loopholes.
In this cat-and-mouse game, encryption has become an important strategy for cybercriminals as they can encrypt malicious content in data packets and send them to the network. To stay one up, organizations are using different strategies to encrypt these data packets to understand their contents. One such strategy is SSL decryption.
In this article, we'll talk a bit about SSL decryption followed by how you can decrypt data packets using a tool called Wireshark.
What is SSL Decryption?
All web traffic today is encrypted using the Secure Sockets Layer protocol that sits on the application layer (Layer 7) of the OSI model. This protocol is known to reduce the chances of breaches unless cybercriminals take explicit steps to work around this encryption. As mentioned earlier, organizations must decrypt this SSL traffic to examine the contents of the incoming data packets for malware and other threats. The process of decrypting the encrypted data packets is called SSL decryption.
Also known as SSL Visibility, the process of SSL decryption starts by routing the data packets to various inspection tools that examine the packets for threats. The routing decisions depend on the configuration and the tools available in your infrastructure.
Before going into how you can decrypt SSL using tools like Wireshark, let's understand the possible challenges that come with this decryption process.
Challenges of SSL Decryption
Decrypting SSL traffic is not easy and depends greatly on how your infrastructure is set up, the available tools, the volume of traffic that passes through your network, and more. Here are some common challenges that come with decrypting SSL traffic.
- Complex Architecture Large organizations tend to have multiple security layers and tools to detect and stop different types of security threats. Not all the security tools in your infrastructure can decrypt SSL traffic, and these variations create a sense of security chaos. It's hard to route traffic not knowing which tool will intercept that data packet. Such a complex setup is one of the biggest roadblocks to implementing SSL decryption.
- Cryptography Limitations Sometimes, the limitations of cryptography also add to the complexity of implementing SSL decryption. For example, let's say, your organization uses forward secrecy ciphers. In such a case, how can you send the encryption key to devices that are outside the inspection band? Such nuances of cryptography require extensive planning and implementation.
- Privacy Concerns Privacy and security regulations restrict how you can handle data packets, especially if it violates users' privacy. This means you can't decrypt data packets from some applications as this can expose the sensitive information of users. Viewing such information is a violation of privacy laws and can also put your organization at risk of data breaches. In turn, this reduces your visibility into some data packets and cybercriminals can use these packets as a conduit for transferring malware to your system.
- Performance Degradation Another potential downside of SSL decryption is its negative impact on performance. Undoubtedly, decryption and inspection will take a few extra seconds and this can degrade network performance, especially if you're grappling with issues such as low bandwidth and heavy traffic surges.
In all, implementing SSL decryption is not easy, and could require additional time and effort. Nevertheless, it is important and can save your organization from ransomware attacks.
One way to strike a balance between the challenges and benefits of SSL decryption is to use tools like WireShark that are built for decrypting data packets and examining their contents. Though this tool doesn't address all problems, especially those related to privacy, it's still a good option to consider.
Next, let's talk about how you can decrypt SSL packets with WireShark.
Decrypting SSL Using Wireshark
Wireshark is a popular packet and protocol analyzer tool that enables you to examine the contents of every data packet that enters your network.
It captures as many details as possible about every data packet and in the process, reduces the chances of a cyber attack. This free and open-source tool works well on individual connections to large networks.
Here's a step-by-step guide on using Wireshark to decrypt SSL packets.
Create an Environment Variable
To set up Wireshark on your Windows 10 device:
- Go to Windows 10 Settings and click on “Advanced Settings”.
- A new window will open. Look for a button called “Environment Variables” and click it.
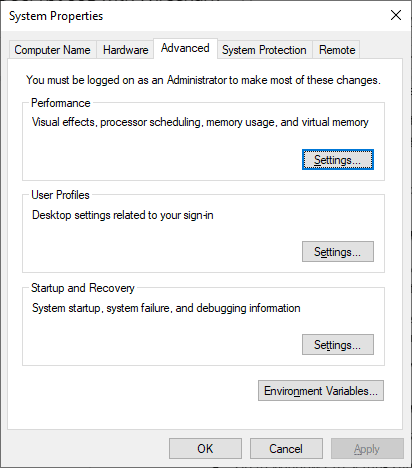
- Create a new environment variable.

- Give the variable name as SSLKEYLOGFILE and choose the location where you want to store the log file. The location can be, for example, C:\Users\Admin\sslkeylogfile.log.
Once you create the environment variable, click OK and exit from Windows settings. To check, navigate to the URL you entered for your log file and see if sslkeylogfile.log exists. Note that you can give any name to the log file, just make sure it ends with the “log” file extension.
Configure Wireshark
Next, download and install Wireshark if you don't already have it.
To configure Wireshark:
- Open Wireshark and navigate to Edit > Preferences.
- In the Preferences window, search for SSL on the left-hand pane, and click it.
- On the corresponding right-hand pane, set the “(Pre)-Master-Secret log filename” to the location you used earlier to create the log file. In the above example, this filename must be C:\Users\Admin\sslkeylogfile.log
With this, you're all set to use Wireshark.
Test the Settings
Head to your browser and type any website. Open your Wireshark in parallel and navigate to Capture > Start.
Soon, you'll see the data packets and the information they contain. At any time, click on the Stop (red square button) on the toolbar to stop the data capture. You'll notice a bunch of data packets, possibly from different websites. You can filter them using IP addresses as well.
Right-click on any data packet and navigate to Follow > SSL Stream. A new window opens and here, you'll see the header and contents of the data packet. Also, open your log file and you'll see a bunch of encryption keys that Wireshark is using to decrypt these data packets.
That's it really and now you can send this log data to a central logging mechanism for further processing and analytics. You can also pipeline this information to a monitoring platform that can raise alerts if the decrypted content matches flagging patterns.
Undoubtedly, Wireshark is efficient and easy to use, and this is why it's so popular. That said, there are also other tools that you can use to get the same results, and next, let's talk about one such tool.
SolarWinds Deep Packet Inspection and Analysis – FREE TRIAL
SolarWinds Deep Packet Inspection tool comes as a part of the Network Performance Monitor and is used to decrypt SSL messages, so you can get instant insights into the traffic passing through your network.
Key Features
- Determines latency and its underlying cause.
- Analyzes more than 1200 different applications.
- Identifies risk levels and restricts access as needed.
- Improves end-user experience.
- Sends customizable alerts.
- Comes with intuitive dashboards for easy understanding of data points.
It examines the contents of every packet and provides a context for the same. Besides the content, you also get other information such as the source of the packet, level of risk, and more.
The biggest advantage of the SolarWinds Deep Packet Inspection tool is the insights you get about applications, their use of your network resources, impact on user experience, and other relevant insights that in turn, can help you better understand what's going on in your network. More importantly, you can make appropriate and well-informed decisions that would positively impact your business.
In all, Solarwinds Deep Packet Inspection and Analysis can be a handy addition to your monitoring and analytics arsenal.
Website Link: https://www.solarwinds.com/network-performance-monitor/use-cases/deep-packet-inspection
Download: Click here for a fully functional 30-day free trial
Summary
To summarize, SSL packets are encrypted, and cyber criminals use these packets as a conduit to transport malware and ransomware. This is why organizations prefer to decrypt these data packets to ensure that there is no malicious content in them. A popular tool used for decrypting these SSL packets is Wireshark. This free and open-source tool can be configured with just a few steps to capture and decrypt the SSL packets, and in this article, we see how you can do this configuration.
Besides Wireshark, other tools also help to inspect and decrypt these data packets. One such tool that we talked about in this article is the SolarWinds Deep packet Inspection and Analysis tool that comes as a part of the Network Performance Monitor suite. It comes with many advanced features that can inspect and analyze data packets from more than 1200 different applications and undoubtedly, add an extra layer of security to your infrastructure.
We hope this was an interesting read. Browse through our site for similar articles and reviews.
Decrypt SSL with Wireshark FAQs
How can I decrypt SSL traffic using Wireshark?
To decrypt SSL traffic using Wireshark, you will need to capture the SSL/TLS encrypted traffic using Wireshark, export the SSL/TLS key, and configure Wireshark to use the key to decrypt the traffic.
What information can be gathered by decrypting SSL traffic?
By decrypting SSL traffic, administrators can gather information such as HTTP requests and responses, authentication credentials, session data, and security vulnerabilities.
Can all SSL traffic be decrypted using Wireshark?
No, SSL traffic can only be decrypted if the administrator has access to the SSL/TLS key used to encrypt the traffic. Without the key, SSL traffic cannot be decrypted.
How can I obtain the SSL/TLS key needed for SSL decryption?
The SSL/TLS key can be obtained from the web server or client that initiated the SSL/TLS encrypted session. The key can be exported in a format that can be used by Wireshark to decrypt the SSL traffic.
What are some best practices for SSL decryption?
Best practices for SSL decryption include ensuring that proper access controls are in place to protect the SSL/TLS key, limiting SSL decryption to authorized personnel, and ensuring compliance with applicable laws and regulations.
What types of SSL certificates can be decrypted using SSL decryption tools?
SSL certificates that can be decrypted using SSL decryption tools include SSL/TLS certificates used for web traffic, email traffic, and other types of encrypted traffic.