Protecting a company’s intellectual property is very important to avoid any data leakage to the outer world
Business emails are also a main part of organizations as they are used to send or receive important data or conversations over the chat. You know sometimes due to third-party malicious attacks these emails get hacked. Malware, ransom virus attacks, Emotet, phishing, middle man, password attacks, and many more are the malicious attacks that take place. How to secure business email? Here we come up with a few solutions which will help you to get rid of these problems. In this email security best practices post, we are going to explain methods to solve this problem. Let’s dive into the topic.
A Quick Introduction to Email Security
Email security is a term that describes the different methods, or procedures used to protect emails accounts, contents, and communication against unauthorized access, malware attacks, and spam attacks. When it comes to security, various networking protocols are available to secure email accounts. Some of the protocols are SSL, STARTTLS, TLS, and many more used to secure email transmission. Both SSL (secured socket layer) and TLS (transport layer security) provide an encryption type of communication between the two devices over the internet.
Importance of Email Security
Below are a few factors that explain the benefits of email security thoroughly:
- Comprehensive email security includes protection from malware-less social engineering attacks, weaponized attachments, and malicious URLs.
- Highly secure and resilient offsite, cloud-based perpetual email archive.
- Continuity service with RPO/RTO close to zero and 100% service availability.
- Full email and attachment scanning to control or block sending sensitive information.
- All features are managed through a single, and web-based console.
Business Email Security Best Practices
Below are the primary email security practices that can go a long way to protect your email services.
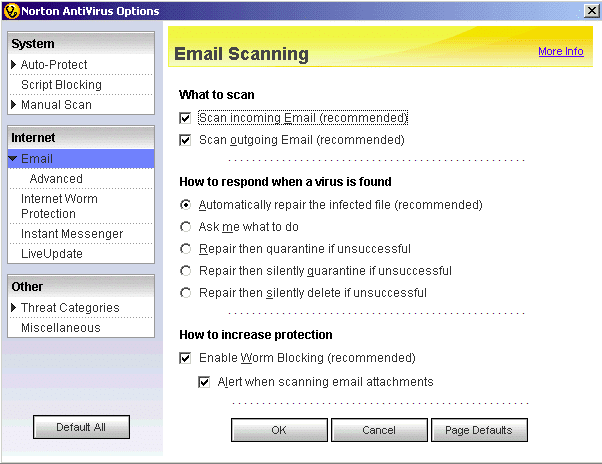
1. Using a Strong Email Password
We know that most people prefer to set their password as “123456” or lengthy passwords like “123456789”. You know that more than 3 million people use these two passwords to access their email services. Forget about email security, what about banking auto billing? Then your personal account is in danger. So this is the easiest way to welcome attackers to your doorstep. Always remember one thing “easier passwords are, they are more likely to breach your account”.
Below are some tips which will help while creating your password:
- Always try to use shuffle both lower as well as upper case letters
- Try to include numbers and special characters
- Use phrases instead of words
- Try to avoid using birth dates, student-IDs numbers, and anything personal which is easily available on social media platforms.
The image below illustrates this scenario:

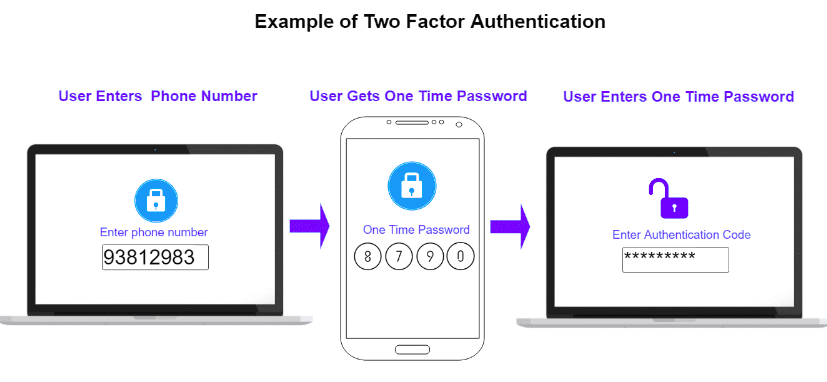
2. Using Two Factor Authentication
Now, most professional computers can do these tasks. Why not us? This is considered to be a second shield to secure the data/ password. Thankfully, now almost every email generation platform provides two-way authentication factors that enable you to use one more reference email while creating a new email.
For example, even if a hacker tries to access your email using the password “123456”, two-ways authentication factors stop it. This is because there will be code or OTP will be sent to your mobile number, SMS, emails, or any time-based-one-time-password (TOTP) applications.
The below image is an example, that gives some idea on two-way authentications:
3. Monitoring the Email Habits
This step is nothing but training your fundamentals, it may sound crazy or simple to most of us. But trust me this is a long-term solution. Every day we use our business emails for our day-to-day activities. So it is important to keep track of your business mail about your activities.
Tips to follow this step:
- Check with how many newsletters you are subscribed to?
- How often through the day you are sending emails or messages or vice versa?
- Are you spending most of your time on email threading from outside of your organization?
In recent times, a popular email analyzer tool has become the talk of the IT town, that is called “ EmailAnalytics”. Click on this link to know more on this tool: https://emailanalytics.com/
4. Look Out for Any “Phishing Email”
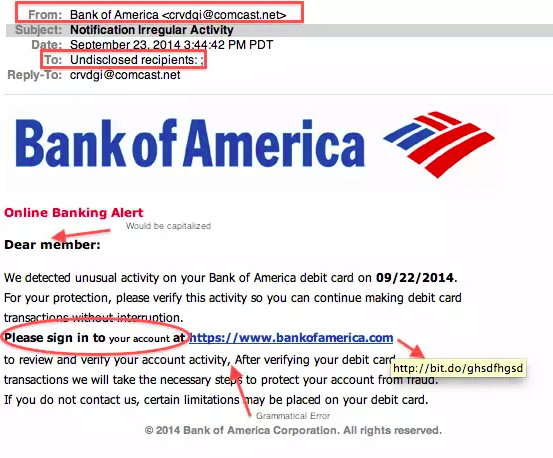
“Phishing email” is one of the many ways hackers steal account information. Once you create your email, all the log-in information will be stored in the system. There might be a greater chance that hackers may steal all information from account manager settings.
The most common phishing emails are ones where they call you or email you by saying they are the service providers such as banks (insurance, credit cards, or any gift vouchers-related mails) and Paypal (this is regarding cashback offers). All these service provider emails will be stored in “SPAM”. If you might not be aware of these emails, then start looking into them at least now.
This is an example of phishing mail, where you can see grammatical errors, spellings, and fake bank URLs. So beware of such emails.
5. Don’t Open an Email without Scanning Them
This is not a much-stressed task if you are using your solo business account to send or receive information, and many a time you might receive junk mail with files attached to them from unknown sources. This type of email builds your curiosity, and you can't even put them into the trash bin without checking them. There are a lot of tools used to improve email security measures, for example, antivirus or antimalware tools used to scan attachments. While scanning these attachments if you found any problem then it must be a scam message, don't hesitate to delete those messages.
6. Never Access Your Personal Emails using Public WiFi
Let me explain with an example, suppose you visit a mall, and you do a lot of purchases. When the time of billing comes, you may ask shop owners to switch ON their wifi to pay the bills. This might be a risky way because you never know who the hackers are? These types of cybercriminal activities need just simple software to hack all your account details. To avoid such scenarios, suggest your peers and fellow employees access their private details using mobile internet instead of using public wifi.
7. Change Your Passwords as Often as Possible
Few of you might not prefer this step, because they got adjusted to their old passwords and it is very convenient to use them. But this is a myth, most of us have. The professional side of the world suggests that it is better to change the passwords frequently.
The main advantages of changing passwords regularly help you to avoid any type of data leakage and it’s impossible for any cybercriminal to attack your accounts. Remember one thing always changing passwords regularly is the first defense against cybercrime activities and after all, it requires minimal effort.
8. Be Careful with the Devices You Use
Nowadays, most of the companies come up with some regularities such as “bring your own device policy” as the name suggests that companies allow their employees to bring laptops or any personal devices to access the professional kinds of stuff. We feel that this type of measure won’t give too many advantages if you have not yet rebooted your personal devices with security tools or services. You can't login into your business or professional accounts using public devices, because a few devices store the details of the last typed or they might decrypt all the details. So be cautious of public laptops or the internet.
9. Avoid Giving Your Email Address Away
You know not every business deserves to know your email address. If any website is asking for your email address try to avoid accessing such websites as long as possible. Always remember one thing, your personal email address should be allowed to subscribe to internal newsletters and updates. In recent times, a lot of cybercrime threats have been registered because they even crossed their limits by selling all the information to third-party vendors. We believe that “precaution is better than cure”, so this is not a tech-savvy thing to take action, and it is common sense for everyone to follow it.
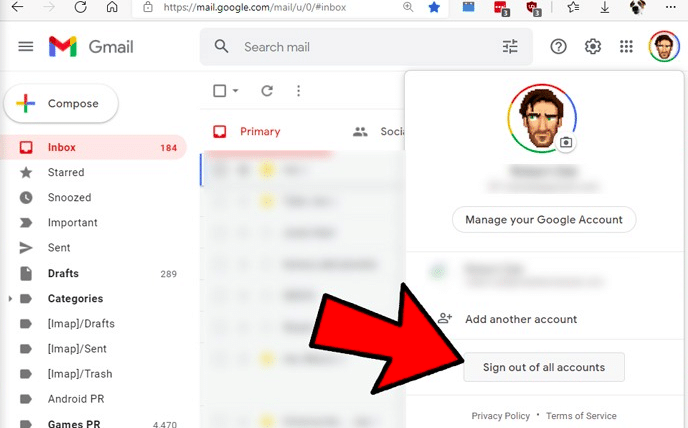
10. Log Out of Your Mail When You are Finished
We think this is the best way to keep your data more secure without being threatened by any cybercriminals. Once you finish all your work don't forget to log out from all the email accounts which you have used during your productive hours.
11. Visualize Your Team’s Email Activity
It may seem a very simple step, but trust me it is an important measure that you will take to secure the data. It helps you to keep track of how many emails you have sent or received per day? And how much time do you spend on email threads? To answer all these questions, visualizing your team’s email activity is the best way and also enables you to lessen the email security risk.
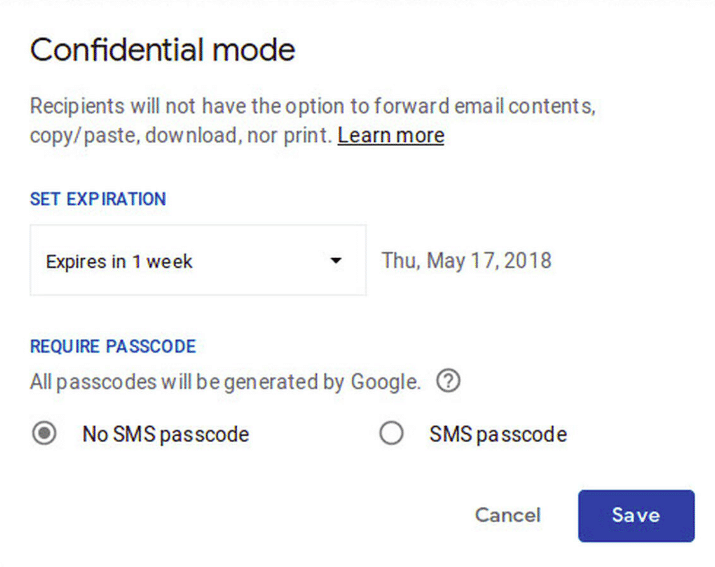
12. Use Gmail’s Confidential Mode
Did you notice that Gmail has a built-in “confidential” mode that allows you to send your emails more securely? To navigate this option follow the below steps:
Open a compose window to draft a message, click on the lock and clock icon located in the bottom row. Once it gets enabled, your email recipients will be prevented from copying, forwarding, downloading, or printing the message contents. This step helps by preventing confidential information from spreading outside the world. There are two options available to secure your emails even better.
The first option is to set an expiration date setting the message to self-destruct so the emails will not be sitting in the inbox for a longer period.
The second is the SMS option if you want to unlock your email with a unique SMS passcode option that will be sent to the recipient’s mobile devices
13. Avoid Replying to Spammers or Scammers
Suppose if you have identified a scammer, you will start abusing them by giving away your peace of mind. So it’s better to avoid such mail without replying to them. Sending a response indicates that you are using a valid email id, there might be a chance of welcoming more intruders or cybercriminals.
14. Educate Your Employees About Email Security
Are you following all these tips to secure your email? What about your employees or co-workers? It’s time to educate them about email security best practices. If you want your organization to be secured as long as possible, then spend some time exploring all these tips. If your organization runs on Gmail or G Suite, the check-out security checking options available, try to configure the things to complete Gmail security settings.
Final Words
Nowadays security plays a vital role in every aspect of life (from business operations to finance). It’s a tricky one too because it costs your time as well as you need some education to adopt all the best practices to secure your professional as well as personal operations. Email security is the most important thing to do when you talk about business because everything depends on the email, we can also say that it’s a bridge that establishes the communication between two people. In this email security best practices post we have tried to list out very important tips and tricks to help our readers to know about email security and its importance. Here we have listed 14 main best practices; just explore them and secure your emails using the above tips and tricks. Share this post as much as possible to reach out to more communities, and educate people about email security benefits to prevent them from spammers, intruders, or ransom viruses.