FTP, also known as a File Transfer Protocol, is used to transfer files between multiple systems. SFTP, on the other hand, is part of the SSH protocol, which essentially replaced Telnet and the earlier Rlogin. Create FTP over SSL protocol allows multiple users to access their directory but not other directories. FTPS uses SSL/TLS protocol to transfer all files in a secure channel.
This guide will show you how to set up a secure FTP server using IIS on a Windows server.
Install IIS and FTP Roles
First, you will need to install IIS and FTP roles on your Windows server. Then, follow the below steps to add both roles:
Step 1 – Open the Server Manager as shown below:
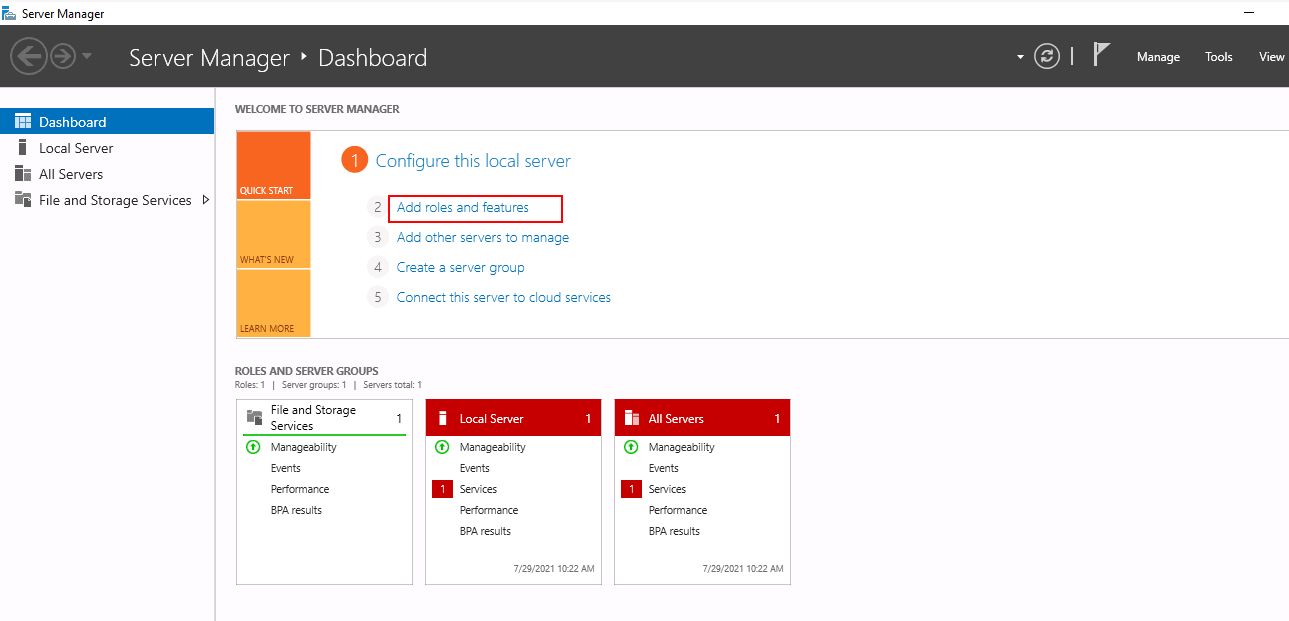
Step 2 – Click on Add roles and features. You should see the following screen:
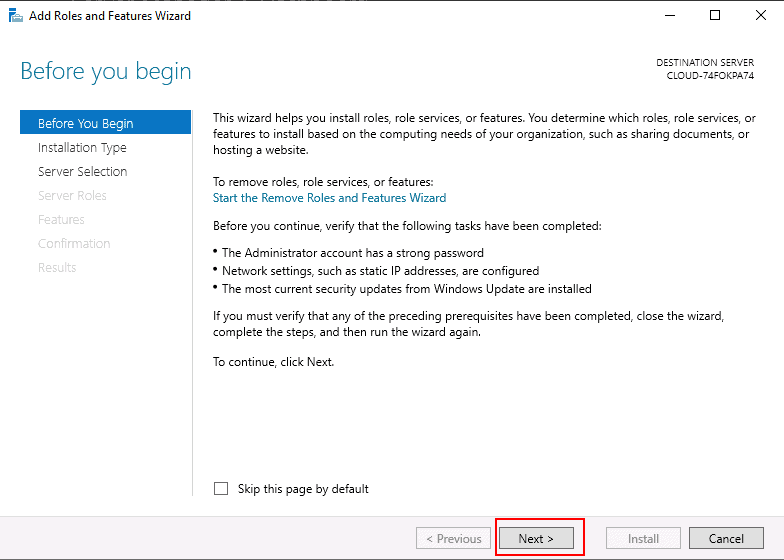
Step 3 – Click on the Next button. You will be asked to select the installation type as shown below:
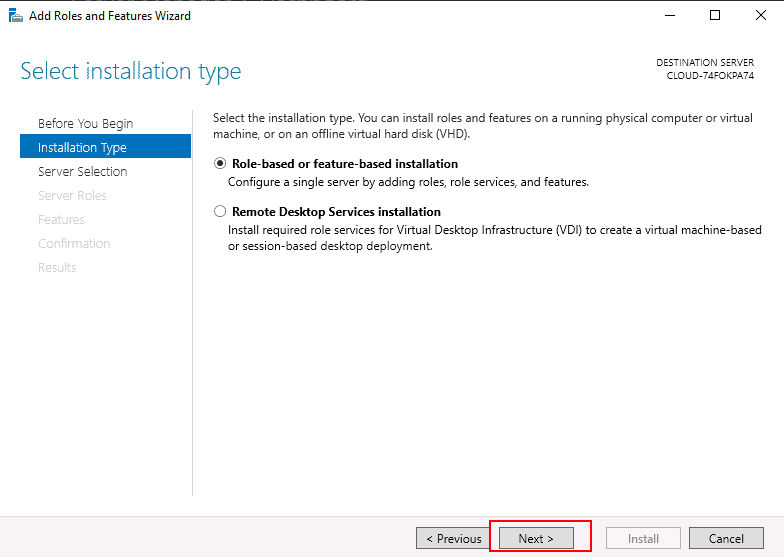
Step 4 – Select Role-based or feature-based installation and click on the Next button. You will be asked to select a destination server as shown below:
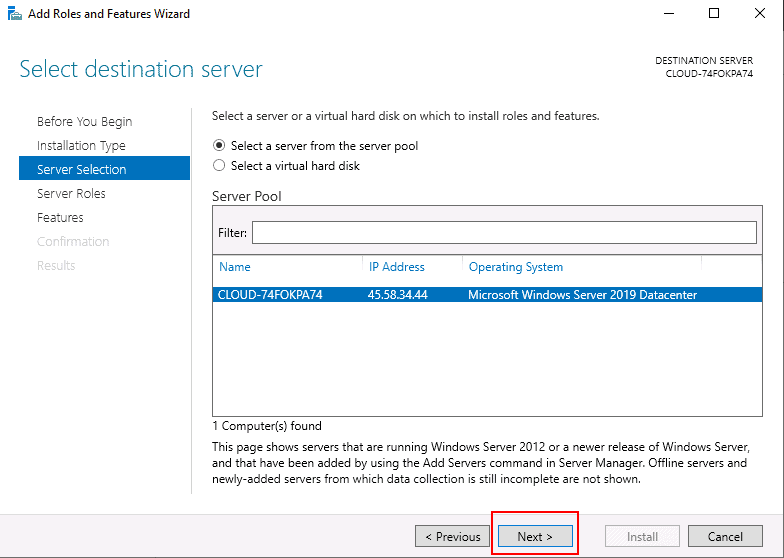
Step 5 – Select the server from the server pool and click on the Next button. You will be asked to select roles as shown below:
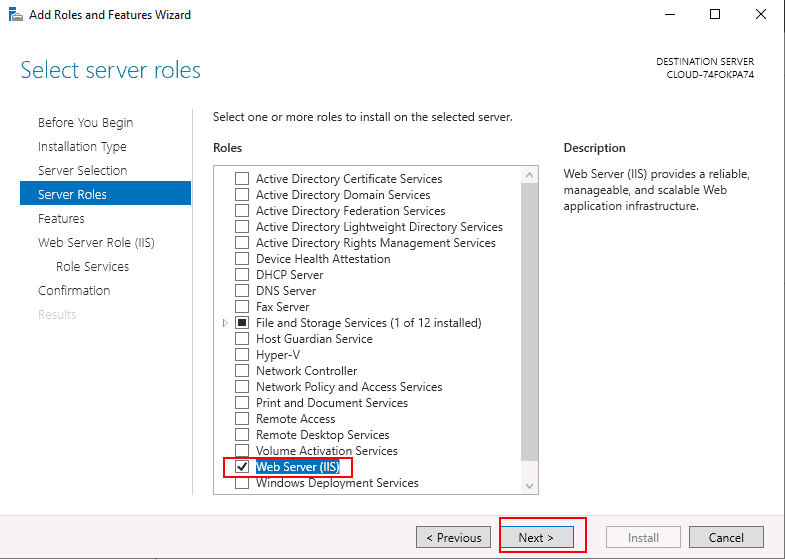
Step 6 – Select IIS and click on the Next button. You will be asked to select roles services as shown below:
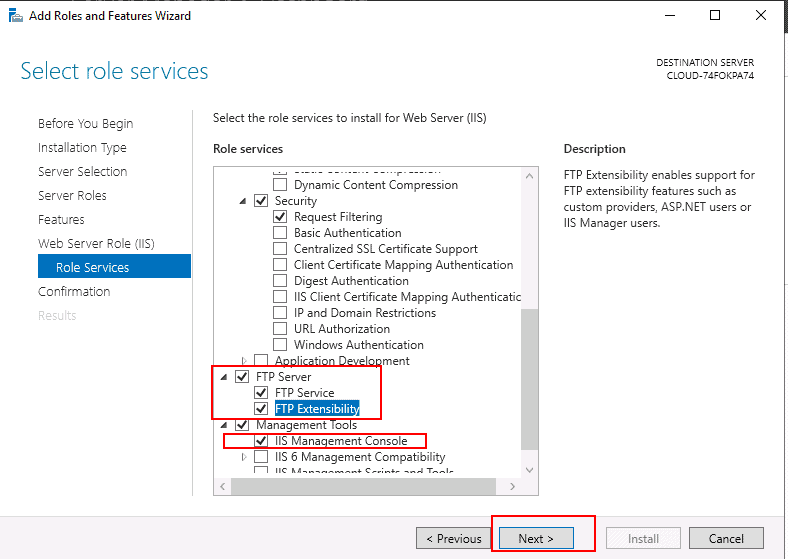
Step 7 – Select FTP service, IIS Management Console, and click on the Next button. You should see the confirmation screen:
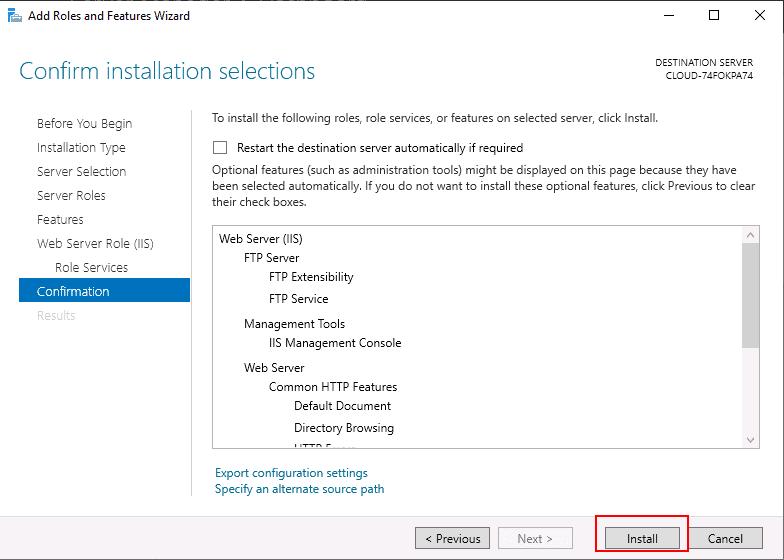
Step 8 – Click on the Install button to start the installation.
This process will take some time to finish the installation.
Create SSL Certificate for the FTPS Server
Next, you will need an SSL/TLS certificate to secure your FTP server. Again, you can either buy a certificate from the certificate authority or create your self-signed certificate.
In this guide, we will create a self-signed certificate.
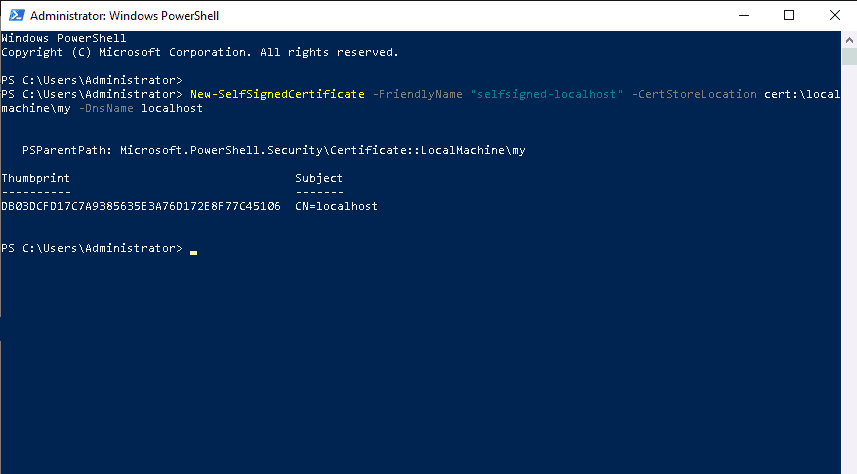
To create a certificate, open PowerShell and run the following command:
New-SelfSignedCertificate -FriendlyName "selfsigned-localhost" -CertStoreLocation cert:\localmachine\my -DnsName localhost
This command will create a self-signed certificate named selfsigned-localhost.
Configure Windows Firewall to Allow Host Process for Windows Services
Next, you will need to allow svchost.exe through the firewall. Follow the below steps to configure the firewall:
Step 1 – Open Windows Firewall from the Control Panel as shown below:
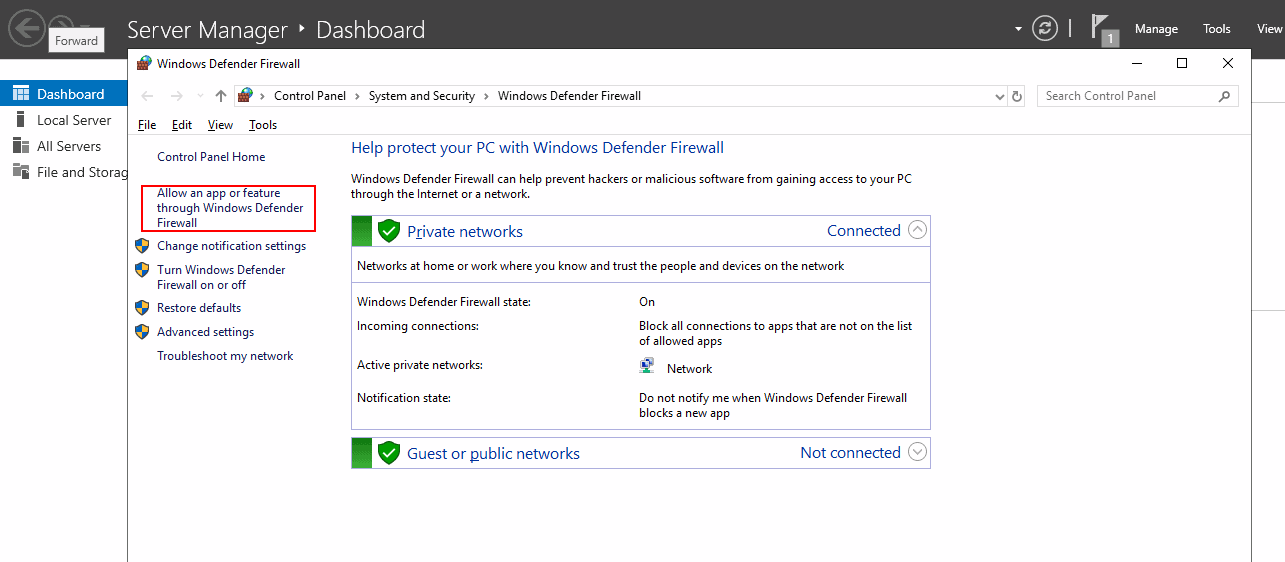
Step 2 – Click on Allow an app or feature through Windows Defender Firewall. You should see the following screen:
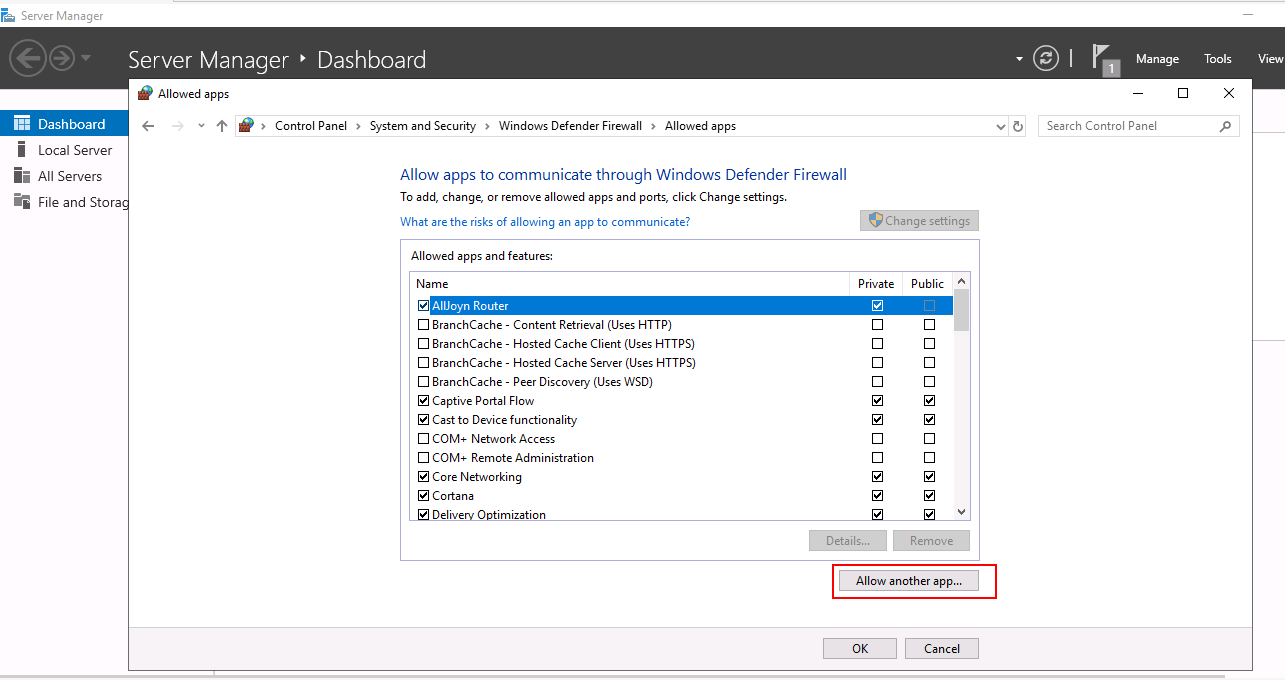
Step 3 – Click on Allow another app. You should see the next screen:
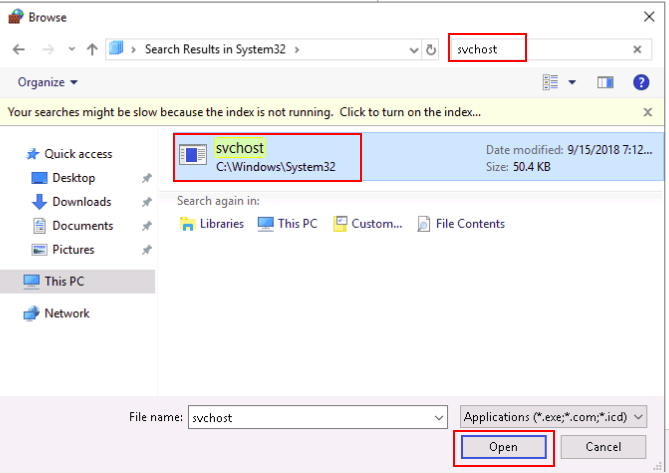
Step 4 – Search for svchost.exe and click on the Open button. You should see the following once screen:
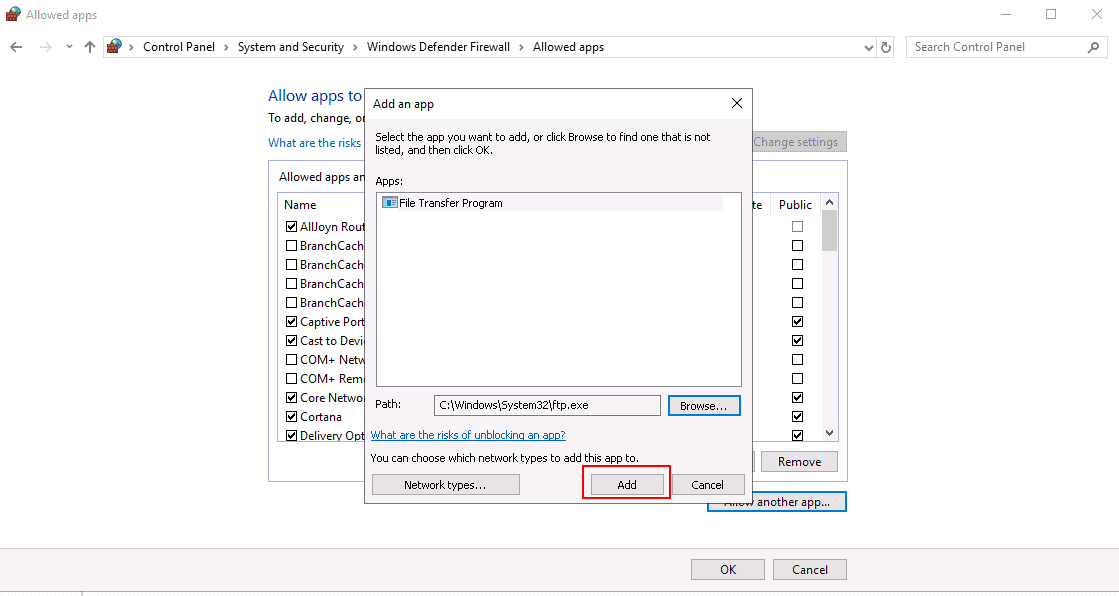
Step 5 – Click on Add button to add svchost.exe to the allowed list.
Create User and Group for FTPS
Next, you will need to create a user who wants to access the FTP server. You will also need to create a separate group for that user.
First, open the Computer management from the control panel as shown below:
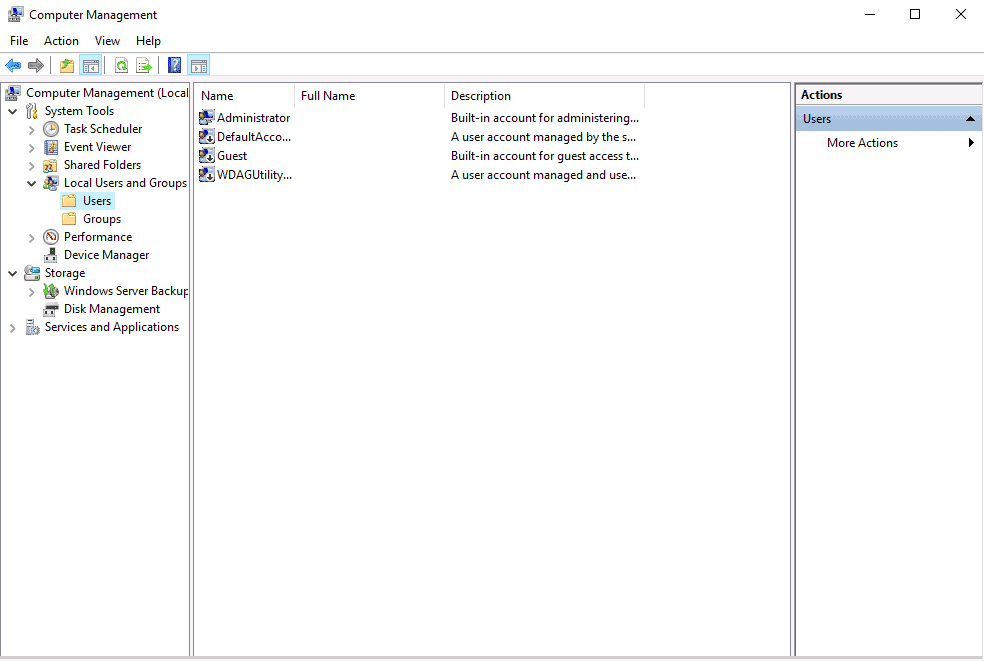
Right-click on Users and create a new user as shown below:
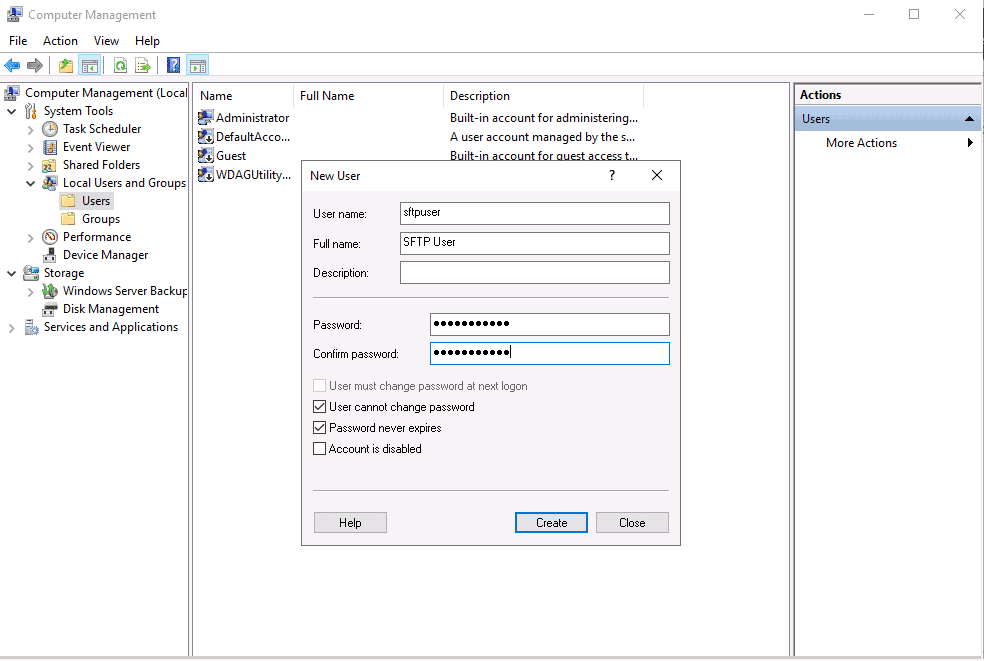
Provide your user information and click on the Create button.
Next, right-click on Groups and create a new group as shown below:
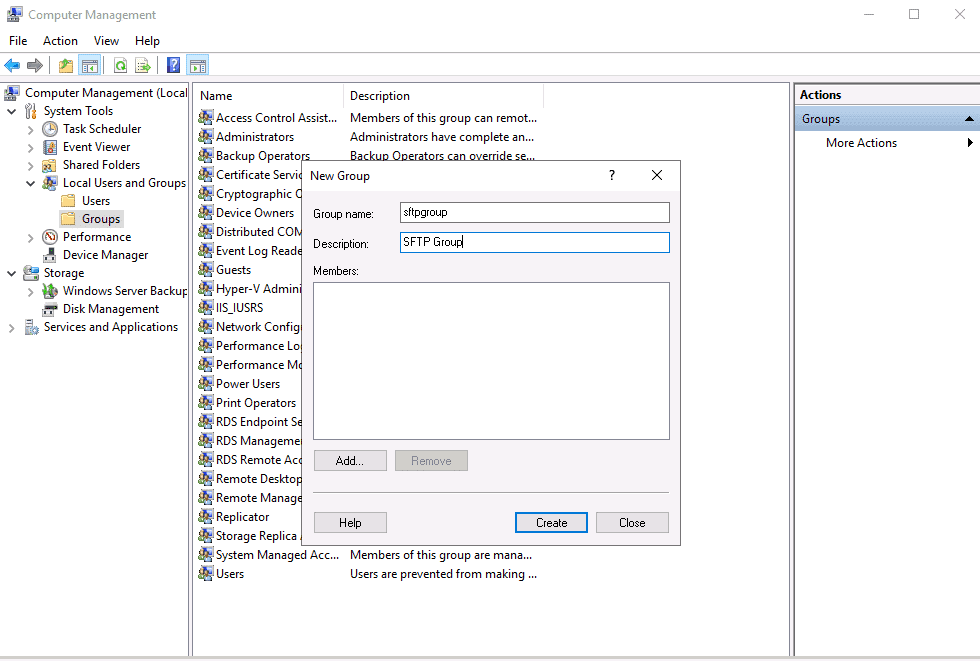
Provide your group information and click on the Create button. Next, add your FTP user to the FTP group.
Configure Firewall for FTP
If your server is behind the firewall, you will need to allow FTP passive mode connections.
Follow the below steps to allow the passive mode connections.
Step 1 – Open the IIS Manager as shown below:
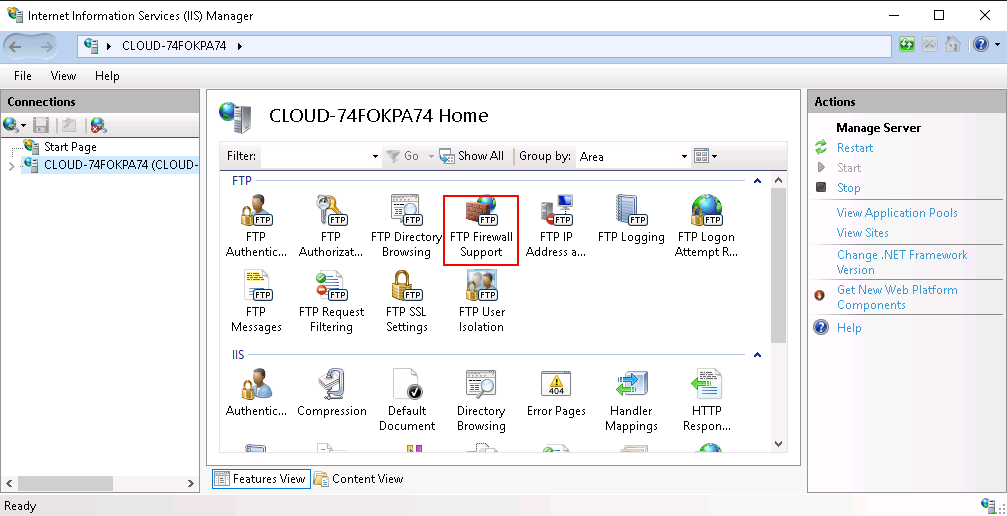
Step 2 – Click on the FTP Firewall Support. You should see the following screen:
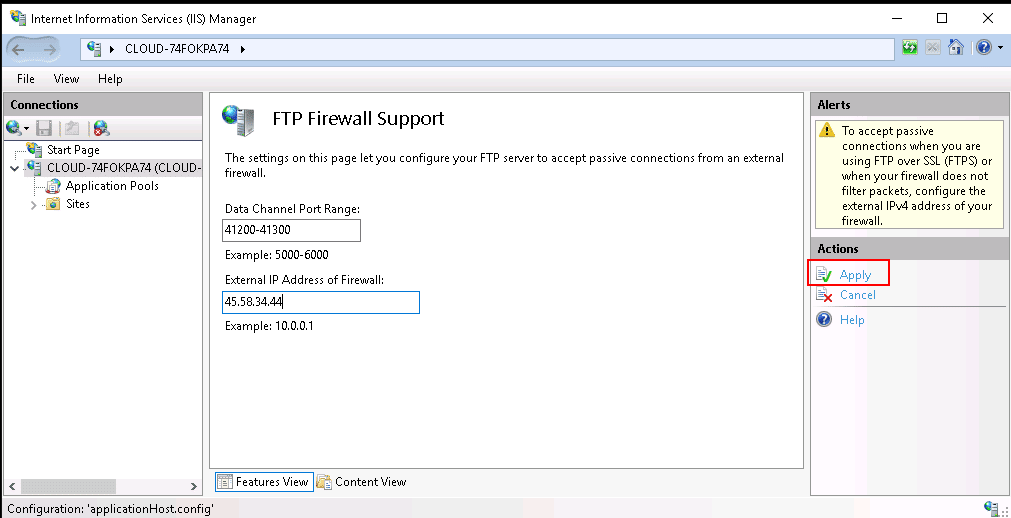
Step 3 – Provide data channel port range 41200-41300, your server public IP address, and click on the Apply button to save the changes.
At this point, your firewall is configured to allow FTP passive connections. You can now proceed to create an FTP site on IIS.
Create FTP Site on IIS
Next, you will need to create an FTP site on the IIS manager.
Open the IIS Manager, right-click on Sites and select Add FTP Site. You should see the following screen:
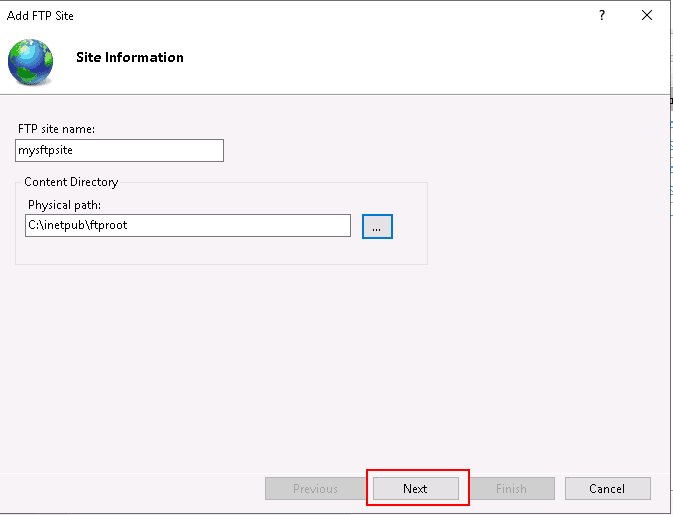
Provide your FTP site name, the FTP directory path, and click on the Next button. You should see the following screen:
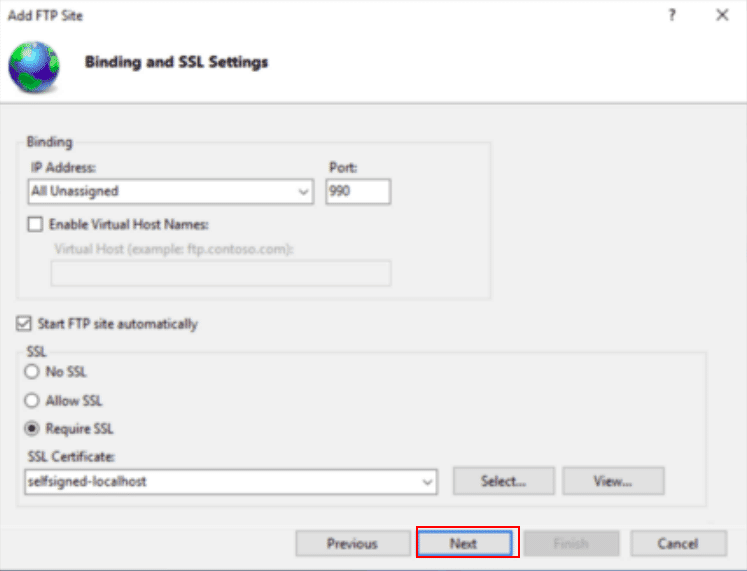
Provide your SSL port, select Start FTP site automatically, select Require SSL, select your SSL certificate and click on the Next button. You should see the following screen:
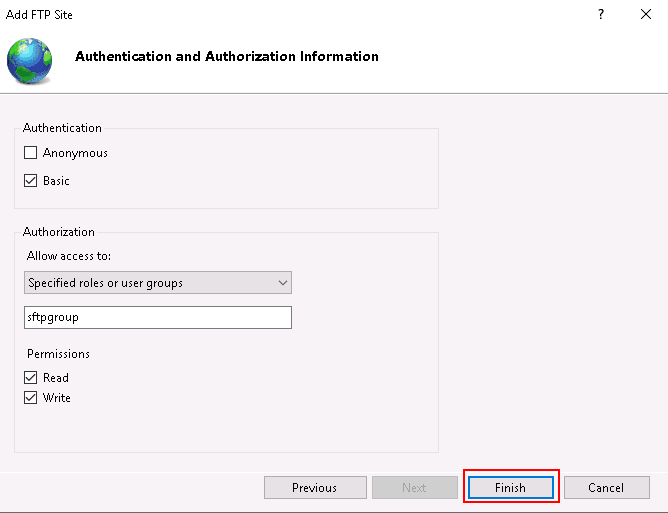
Select basic authentication, define your FTP group, grant Read/Write permission, and click on the Finish button. You should see the following screen:
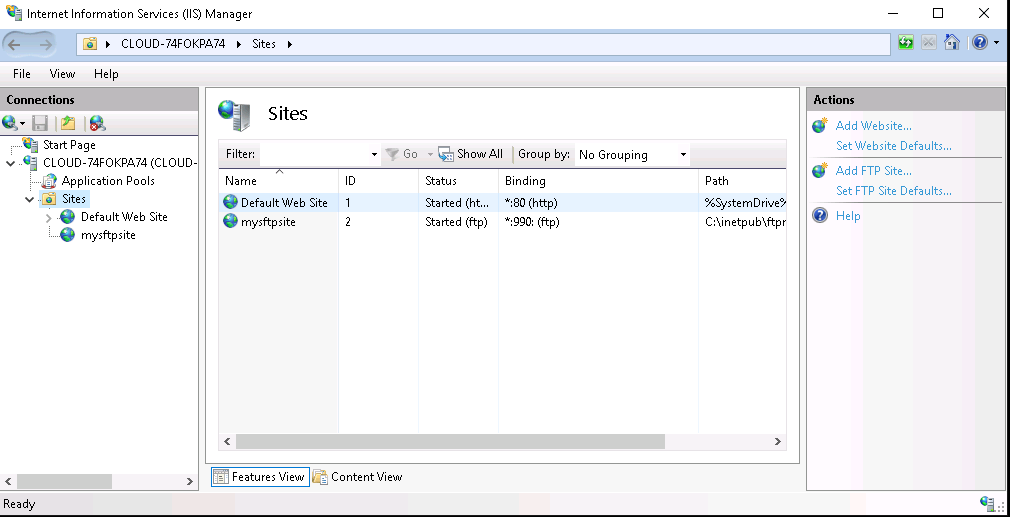
Next, you will need to allow SSL port 990 through the Windows Defender Firewall.
First, open the Windows Defender Firewall and Advanced Security. You should see the following screen:
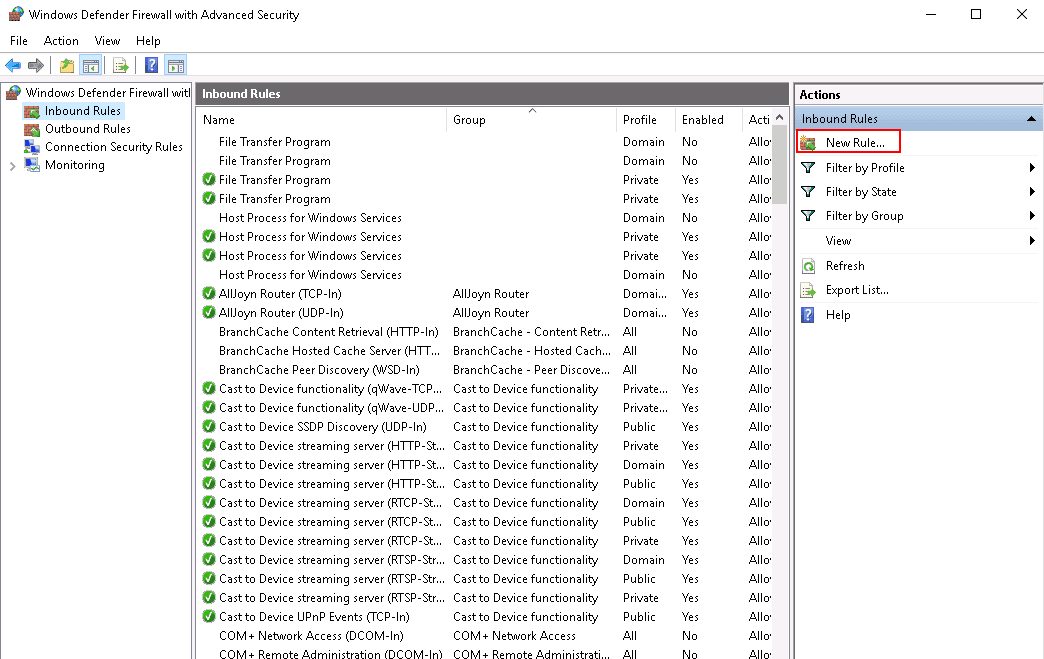
Click on New Rules. You should see the following screen:
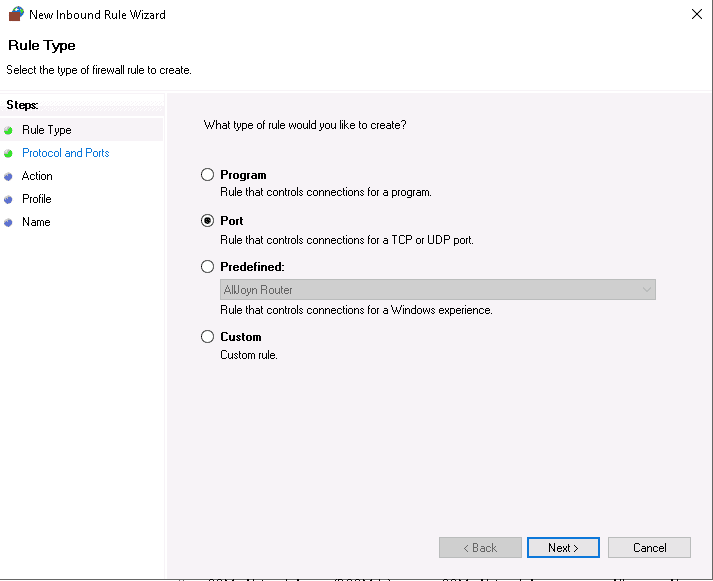
Select Port and click on the Next button. You should see the following screen:
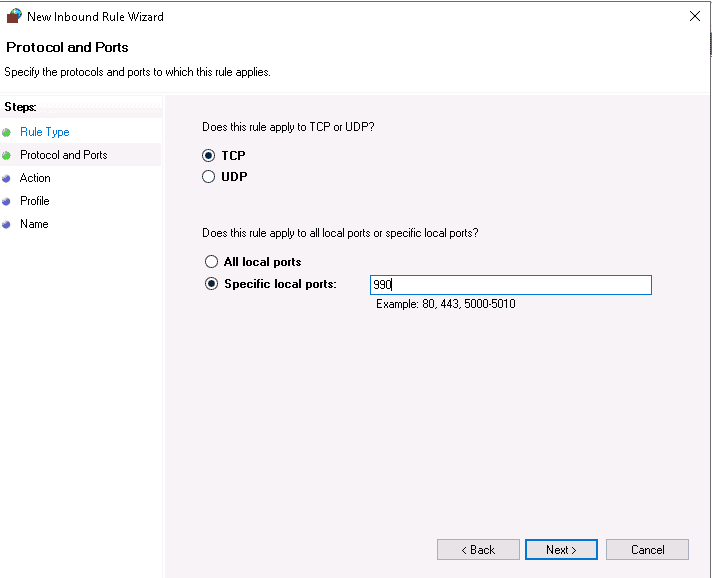
Select TCP and define your port 990, then click on the Next button. You should see the following screen:
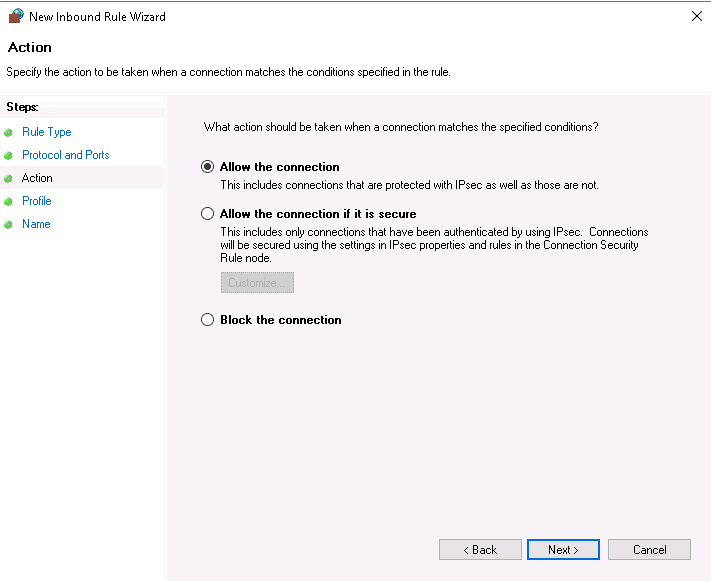
Select Allow the connection and click on the Next button. You should see the following screen:
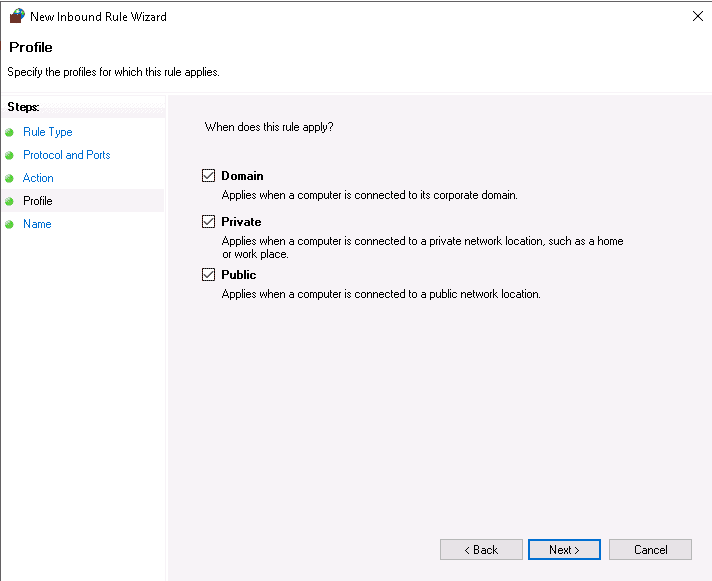
Select all profiles and click on the Next button. You should see the following screen:
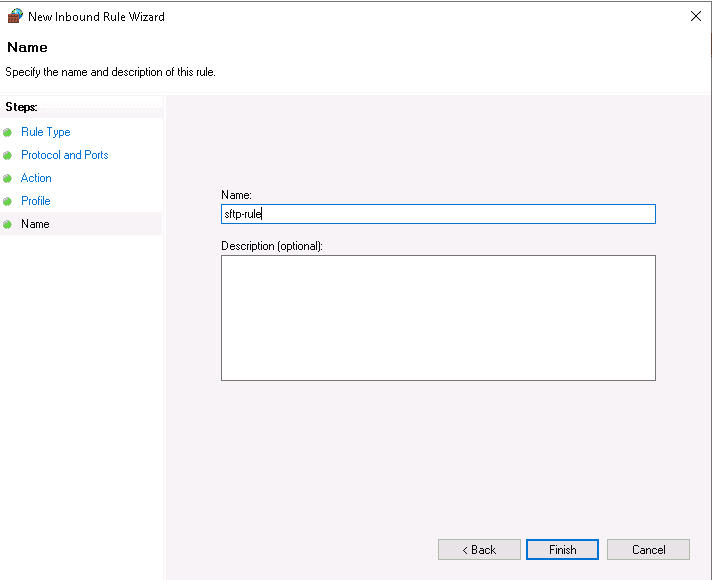
Specify your rules name and click on the Finish button.
Access FTP Server Using Filezilla
At this point, your FTP server is installed on a Windows server. Now, it's time to verify the FTP server from the client machine.
Now, go to the client machine and open the Filezilla. You should see the following screen:
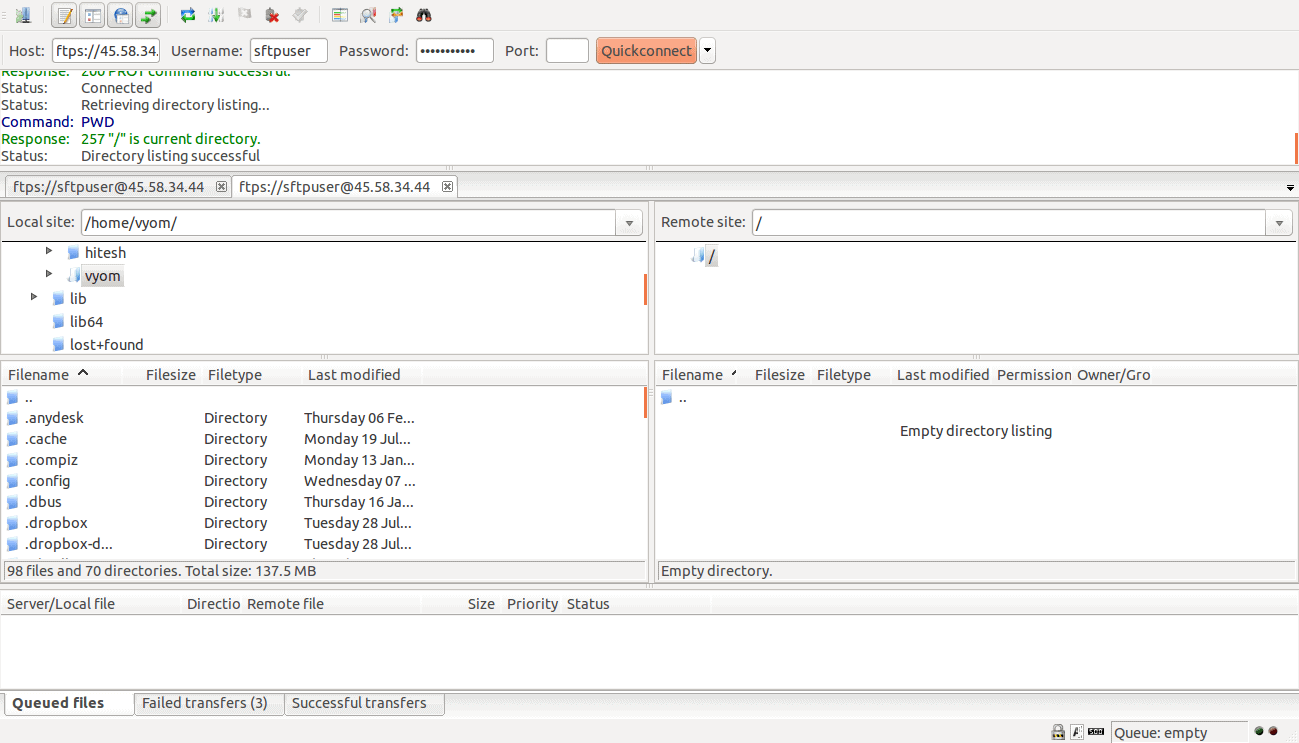
Provide your FTP server IP, username, password, port, and click on the Quickconnect button. You will be asked to trust the certificate as shown below:
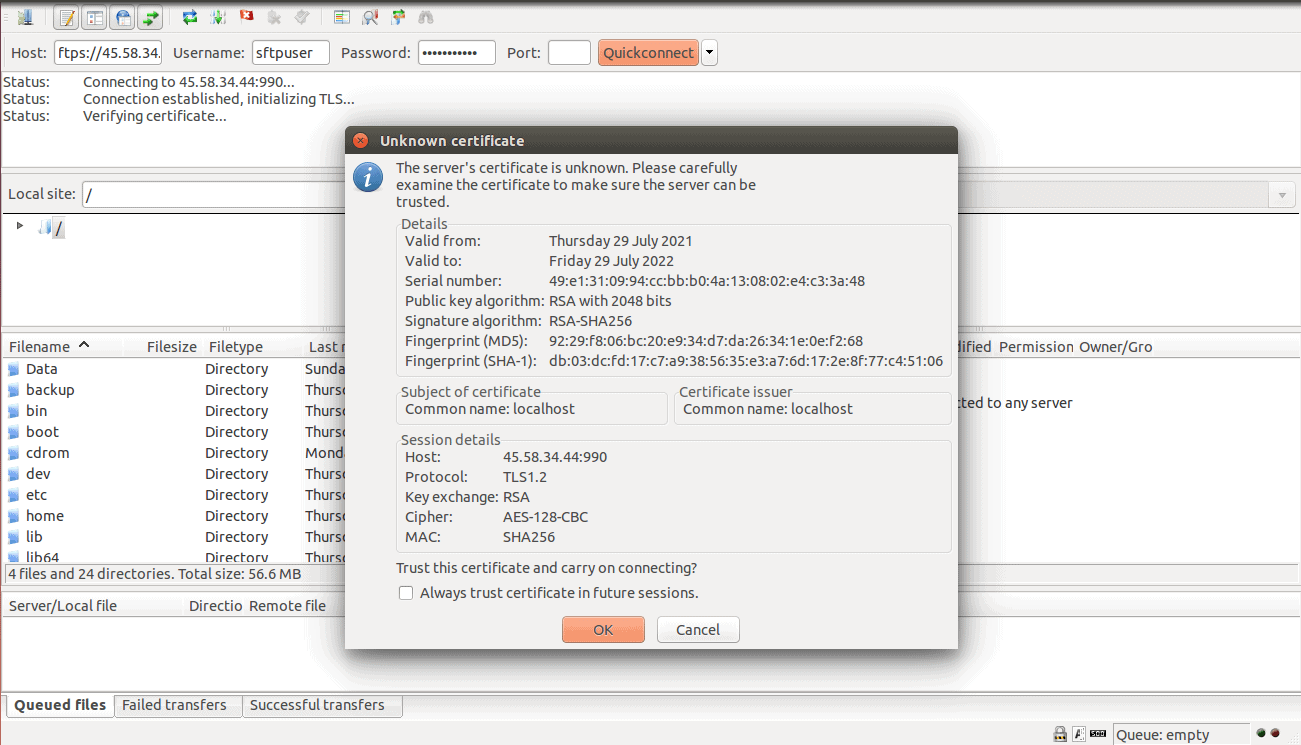
Click on the OK button to trust the certificate. You will be redirected to the SFTP server.
Conclusion
In the above guide, you learned how to set up a secure FTP server using IIS on a Windows server. Your files and directories are now transferred over the secure channel.
Installing SFTP Server using IIS FAQs
How can I install a secure FTP server on Windows using IIS?
To install a secure FTP server on Windows using IIS, you can follow these steps:
- Install the FTP server role in IIS using the Server Manager.
- Configure the FTP server to require SSL/TLS encryption for connections.
- Generate and install a digital certificate on the FTP server.
- Configure user accounts and permissions for accessing the FTP server.
What types of SSL/TLS certificates can be used for securing an FTP server?
Any SSL/TLS certificate issued by a trusted certificate authority (CA) can be used for securing an FTP server. You can either purchase a certificate from a commercial CA, or generate a self-signed certificate.
What are some best practices for securing an FTP server?
Some best practices for securing an FTP server include using SSL/TLS encryption for all connections, enforcing strong password policies, limiting the number of failed login attempts, and configuring access permissions to restrict access to sensitive data.
What types of FTP clients can be used with a secure FTP server?
Any FTP client that supports SSL/TLS encryption can be used with a secure FTP server. Examples of FTP clients that support SSL/TLS encryption include FileZilla and WinSCP.
How do I troubleshoot issues with a secure FTP server?
To troubleshoot issues with a secure FTP server, you can check the server and client logs for error messages, verify that SSL/TLS encryption is enabled, and test connections from different clients and networks.
Can I use IIS to host other types of web applications in addition to an FTP server?
Yes, IIS can be used to host a variety of web applications, including ASP.NET, PHP, and HTML applications, among others.
What are some key features to look for in an FTP server software?
Some key features to look for in an FTP server software include support for SSL/TLS encryption, customizable user accounts and permissions, detailed logging and reporting, and integration with other monitoring and management tools.