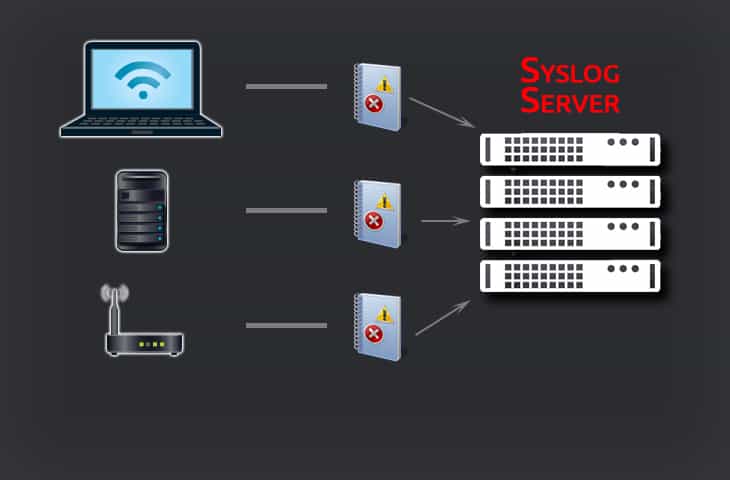
To describe “What is Syslog” in the most simple sense, Syslog is a Message Logging Standard by which almost any device or application can send data about status, events, diagnostics, and more.
Syslog messages have a built-in severity level, facilitating anything from level 0, an Emergency, to level 5, a Warning, and then on to level 6 and level 7, which are Informational and Debugging, respectively.
One of the most notable useful aspects of Syslog, though sometimes it can also be a hindrance, is how open-ended it is.
On the upside, this allows for a great deal of proprietary information or specifics to be transmitted by Syslog, unrestrained by rigid specifications.
On the downside, this creates an environment with relatively little message standardization, meaning that triggered Syslog events from one router may differ so much from another that it becomes a challenge to manage!
Syslog itself originated back in 1980 as an early Unix-like system logging solution, and eventually, it spread to other operating systems as well as hardware devices.
Ultimately it became standardized into the RFC, but the messaging content aspect remains wildly varied from vendor to vendor and device to device.
Syslog Server
Syslog itself relies heavily upon having a Syslog server of some kind to receive, store, and interpret Syslog messages because, after all, a device or application being able to send messages is of little use if there's nothing to receive them!
Syslog servers come in all manner of shapes and sizes – some are physical appliances meant for exceptionally large-scale environments, while others are smaller software-based services or applications, while still others function as stand-alone VMs added into an environment to do the appropriate monitoring.
Syslog Port
Syslog communicates via Port Number 514 and 601 via UDP, both of which are official assignments.
As touched upon above, Syslog itself is standardized in its implementation but the messages it sends along are anything but.
This means that while you can configure and adjust messaging for proprietary needs, it also means that you may have three different routers reporting the same thing via Syslog that all comes in just different enough to confuse or confound any alerts or notifications you may have setup.
This aspect of a Syslog environment always requires some extra due diligence to be sure all the quirks of each device and application are accounted for.
The ability of Syslog servers to go well beyond simply collecting and viewing messages is where their true power comes into play, however.
That's certainly undoubtedly quite useful, but a whole new echelon of functionality and capability come from being able to collect all those messages in a centralized place and perform analytics or visualized graphing of them, or to take it still a step further and have automated scripts or responses to common or predicted situations.
Outages can often be more or less unavoidable, but having a script fire off to immediately to begin doing damage control and bringing things back up, while simultaneously firing off notifications of what happened, can save valuable minutes if not hours of downtime.
Having a centralized place to view and manage your Syslog events is critical as well especially considering that most network devices – such as routers, firewalls, workstations, printers, and more – all communicate Syslog information, and that's not even bringing the application Syslog events to the table yet!
Having all of this information filter into a singular centralized location, a Syslog server, is crucial to staying on top of the data and being certain that important events are lost due to the signal to noise ratio.
Syslog servers also do a great job in helping to organize and even periodically archive over-abundance of data that can easily collect – while still keeping it available down the line if it becomes necessary to review.
Often Syslog servers will accept SNMP data as well as Syslog itself, providing a wider range of device coverage and a better breadth in terms of being able to respond to events.
When it comes to managing network environments more information is always useful, especially with software to intelligently receive and parse that information automatically!
Any good Syslog server will undoubtedly have two powerful features in particular – alerting and notifications.
Being able to trigger a pop-up on-screen, an alarm, or something of that nature is a splendid way to be able to stay on top of issues, or impending issues, without having to remain actively focused on watching it.
Similarly, notifications in the form of e-mails, text messages, and so forth provide coverage no matter where an admin happens to be.
Having troubles while away from the network is never an exciting thing to have happen – but it's far better to be aware and have a text message pop up within minutes of an outage or critical issue and be able to react accordingly.
Even better, thresholds can be set to monitor warnings or other non-critical events, allowing the proactive admin to avoid an issue altogether with a little preventative care.
Tasks can also be scheduled arbitrarily or to happen in some time-based fashion around these Syslog/SNMP events, further expanding the ability of a Syslog server to ease network maintenance and management via automation.
Many Syslog servers are accessed via the software itself on the server environment that it runs on, but some also have a range of web-console based access, which facilitates an ease of access when moving around a large office or, in some cases, remotely.
There naturally comes some risk to this in the case of network-based outages, but even in a worst case scenario it'd be no worse than having to interface with the server directly, anyways.
And there's certainly something to be said for being able to remotely jump in via web console from wherever you are after a triggered notification and make a few swift adjustments well before anything has a chance to actually go catastrophically wrong!
Utilization of diagnostic and reporting technologies are absolutely critical for maintaining a network with as much uptime and as few issues as possible.
The “ounce of prevention” idiom applies ten-fold when managing dozens or hundreds of computers all relying heavily on not just the network itself but also the wide array of other devices on said network! Syslog servers are precisely that preventative tool, and more – a centralized and powerful program to collect as much diagnostic information as possible and then parse and compare it against various thresholds and metrics, display graphs, and perform customized automated responses when necessary.
Something this powerful simply cannot be passed up when it comes to managing a network environment, critical or otherwise.
The level of potential automation via triggered scripts, the immediate alerting and notification, and even simply the aggregation of data and visualization of it – all of these are things which can help more than anything else in assessing, preventing, and handling network or device issues.
No network environment should be without a robust Syslog server to aid in keeping it healthy!
Syslog FAQs
What is Syslog used for?
The name Syslog is short for System Logging Protocol. This is a messaging standard that is used for sending performance and error data from running software that is either implementing applications or services within operating systems. Syslog is widely associated with Linux and devices that do not run Windows. This is because the Windows Events system can be used by software running on that operating system, feeding messages directly into the operating system’s notification handling system. So, it could be said that Syslog is used for devices that don’t run on Windows. Syslog messages have a specific format and, centralized logging servers would need to consolidate these messages into a common format in order to minge those notifications with Windows Events messages and get a system-wide view on statuses.
Where is syslog used?
The System Logging Protocol (Syslog) is an open standard, registered with the #internet Engineering Taskforce (IETF). As it is not a proprietary system, the guidelines can be accessed for free by anyone. Thus, the protocol is used widely by software developers. The standard was originally developed for the Sendmail project, which was developed on Unix. Since then, the Syslog standard has been adopted as a preferred standard for medssaging in programs written for Unix-like operating systems. However, there is no procedural reason why software written for Windows shouldn’t use it.
What devices use syslog?
The syslog messaging standard is widely-used on Unix-like operating systems. However, there is nothing to stop software written for other operating systems or firmware from using the standard. The logging system is used for logging on routers, switches, printers, and other peripheral and IoT devices. Messages can be broadcast over a network, which enables any syslog-compliant agent to collect the logs for processing. The standard port for these messages is UDP 514 but some developers use TCP port 6514 instead.
What are some popular Syslog servers?
Some popular Syslog servers include:
- Graylog
- Kiwi Syslog Server
- SolarWinds Syslog Server
- Nagios Log Server
- Logstash
How do I configure Syslog on a network device or application?
To configure Syslog on a network device or application, you will need to configure the device or application to send Syslog messages to the Syslog server, and specify the Syslog facility and severity level.
What is Syslog forwarding?
Syslog forwarding is the process of sending Syslog messages from one Syslog server to another, to enable centralized management and analysis of Syslog messages from multiple sources.
How do I troubleshoot issues with Syslog?
To troubleshoot issues with Syslog, you can try the following:
- Check the Syslog server logs and configuration settings to ensure they are correct and functional.
- Check the network connectivity between the Syslog server and the devices or applications sending Syslog messages.
- Verify that the Syslog messages are correctly formatted and contain relevant information.
- Use Syslog analysis tools or log parsers to help identify patterns or anomalies in the Syslog messages.