We all know that Splunk is one of the most famous log management tools on the market, but it isn't for everyone. Several more Splunk alternatives are a better fit for enterprises that need to monitor a massive volume of data. In this article, we'll look at the best Splunk alternatives available.
There are tools for Windows, macOS X, and Linux on the list. We've concentrated on solutions that can collect and centralize log data from a range of sources, as well as provide high-quality real-time monitoring features such as graphs and alerts.
Here’s our list of the best Splunk Alternatives:
- Graylog – EDITOR’S CHOICE This log manager is available for Linux and Docker and has pre-written modules for system monitoring and security scanning. The higher plans are hosted in the cloud. The on-premises version is free to use. Get a demo of Graylog Enterprise and Graylog Security.
- ManageEngine Log360 – FREE TRIAL This log management package provides manual search utilities and an automated SIEM data analyzer. Get a 30-day free trial.
- ManageEngine EventLog Analyzer – FREE TRIAL Gathers logs from over 700 sources using a combination of agentless log collection, agent-based log collection, and log imports. Start a 30-day free trial.
- Site24x7 – FREE TRIAL This cloud-based platform implements performance monitoring for networks, servers, cloud platforms, and applications and also includes a log manager. Start a 30-day free trial.
- Datadog Log Management A log management and cloud monitoring service that lets you collect log data from any source and store it centrally.
- Sumo Logic A SaaS-based log management application that can monitor both on-premises and cloud-based services.
- SolarWinds Security Event Manager A SIEM tool that collects logs in a centralized location.
- Sematext Logs A log management tool for gathering logs from your infrastructure. Logs can be searched using simple query syntax to pinpoint specific events.
- LogRhythm NextGen SIEM Platform Includes the LogRhythm NextGen SIEM Plattform, which is a log analysis tool.
- Paessler PRTG Network Monitor A free network monitoring and log monitoring solution from Paessler.
- LogDNA A free log management program for collecting and monitoring log data.
- Fluentd A data ingest tool that can handle structured, unstructured, and semi-structured data.
What is Splunk and what does Splunk do?
Splunk is a tool that indexes and searches log data stored in a system. It is advanced, scalable, and effective. It examines data generated by machines to provide operational intelligence. The real benefit of utilizing Splunk is that it does not require a database to store data because it makes full use of its indexes.
Splunk is a web-based program primarily used for searching, monitoring, and analyzing machine-generated Big Data. Splunk automatically captures, indexes, and correlates real-time data in a searchable container from which graphs, reports, alerts, dashboards, and visualizations can be generated. Its goal is to provide machine-generated data that can be used to recognize data trends, provide metrics, diagnose problems, and provide intelligence for business operations. Splunk is a software platform that may be used for application administration, security, compliance, and business and web analytics.
Searching for specific data in a large amount of complex data is simple using Splunk software. As you may be aware, determining which configuration is currently active in the log files can be difficult. The Splunk software includes a tool that allows users to diagnose configuration file issues and view the current settings in use to make things easier.
Splunk has swiftly established itself as a powerful log management solution since its initial release in 2007. It became the de facto solution for enterprises that generate massive volumes of log files and machine data due to its concentration on enterprise-grade log analysis and Security Incident and Event Management (SIEM). However, the log management landscape has altered dramatically in the last decade. Organizations now have new options for handling their log data that are more inexpensive, faster, and more optimized, thanks to modern distributed architectures like microservices, containers, and hybrid clouds.
Some of the features to look for in a Splunk alternative
- Ingest data from a variety of sources in a variety of forms.
- Search and filter log data by parsing and indexing it into fields.
- Log monitoring in real-time (or near real-time) with the ability to set alarms.
- Search screens, dashboards, graphs, and charts are used to create visualizations.
- Enterprise-scale capability without sacrificing speed or usability.
- Splunk is more expensive, but if you can't gather or store all of the log data you need within your budget, the logging solution isn't for you.
- A simple solution is to set up, configure, and manage additional staff or support expenditures.
- The option to deploy anywhere – cloud, self-hosted, on-premises – is a bonus feature.
Based on these qualities, we've compiled a list of Splunk alternatives to help you find the best log management and analysis solution for your company.
The Best Splunk Alternatives
1. Graylog – FREE TRIAL
Graylog is a good choice for those who have been following the development of the Splunk platform but who consider that system to be overdeveloped. When a company gets into development mode it just keeps going. Splunk started out as a free data processing platform and then started adding on charged-for facilities. The company keeps going and adding on new units, so now the whole platform is very complicated. Graylog is developing in a similar fashion to Splunk but it hasn’t reached the over-engineered stage.
Key Features:
- Log management
- Logfile archiving
- Opportunities for manual log analysis
- A system performance monitoring module
- A SIEM module
- A free edition
Graylog Open is an on-premises log manager that is available for free and will run on Linux or Docker. If all of your endpoints run Windows, you can access the tool through the Docker hosting option.
The two paid editions of Graylog are hosted in the cloud. The first is called Graylog Enterprise, which is a system monitoring package. The service is adaptable and you can add in data from different software packages. It will monitor servers and network devices and also track network traffic patterns. This package is similar to Splunk Oberservability Cloud but not quite as complicated and much easier to customize
The top plan is called Graylog Security, which equates to Splunk Enterprise Security. Again, this system isn’t as complicated as its Splunk counterpart, however, it provides a competent SIEM service.
Pros:
- A free package for Linux and Docker
- The paid editions are hosted in the cloud
- Cloud storage included with Graylog Enterprise and Graylog Security
- Compliance reporting
- Log archiving
Cons:
- Not as comprehensive as Splunk
You can download Graylog Open for free or get a demo of the Enterprise and Security packages. You can use Graylog Open for free.
EDITOR'S CHOICE
Graylog is our top pick for a Splunk alternative because this system provides a free log manager and then options for more comprehensive paid packages. The free tool is designed as an on-premises software package for Linux and Docker. The two paid plans both run on the Graylog cloud platform. The cloud-based services are an observability unit, called Graylog Enterprise and a SIEM, called Gaylog Security. There are rivals to Splunk Observability Cloud and Splunk Enterprise Security. However, the Graylog packages are much simpler than the Splunk systems. So, businesses that have looked at Splunk and found it to be a little over-engineered would be more interested in Gaylog’s products.
Download: Access a FREE Demo
Official Site: https://go2.graylog.org/see-demo-multi-dates
OS: Linux, Docker, or cloud
2. ManageEngine Log360 – FREE TRIAL
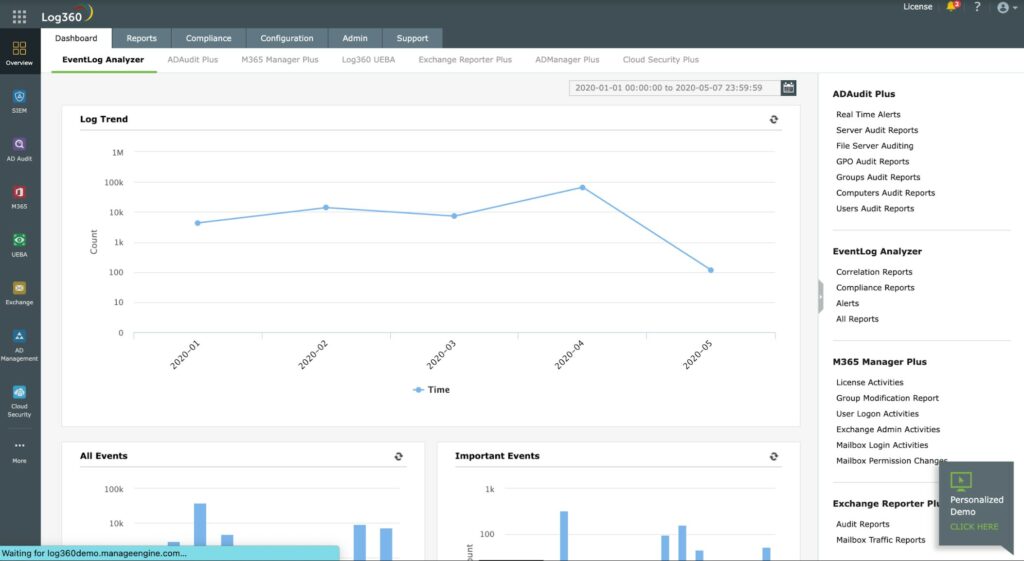
ManageEngine Log360 is an on-premises system that collects log messages in different formats and standardizes them so that they can be searched and stored together. The tool gathers Windows Events, Syslog, and software package logs from more than 700 different systems.
ManageEngine Log360 is a SIEM system that installs on Windows Server but collects log data from other operating systems across a network. The service acts as a log collector and manager as well as a security package.
The Log360 system gathers Windows Events and Syslog messages from operating systems and also interacts with more than 700 software packages to extract activity data. These different types of logs are then standardized into a common format so that they can be searched and filed together.
Key features:
- Log management
- SIEM
- Manual analysis tools
- File integrity monitoring
- Data protection standards compliance
The dashboard includes a data viewer that includes analysis tools. Meanwhile, all arriving log messages are searched for signs of malicious activities. The SIEM deploys user and entity behavior analytics to establish a standard of regular activity per user and per device. This baseline is constantly tweaked in response to new arriving logs. Threat detection looks for anomalous behavior that doesn’t match that activity standard.
When the service discovers suspicious activity, it realizes an alert. You can fine-tune alerts and decide what severity of earning should trigger a notification. Those notifications can be forwarded through service desk systems, including ManageEngine ServiceDesk Plus, Jira, and Kayoko.
Log360 files log messages and creates a meaningful directory structure to make event records easier to find for compliance auditing. The tool is suitable for compliance with GDPR, GLBA, PCI DSS, FISMA, HIPAA, and SOX.
Pros:
- Can monitor key server metrics and automatically send alerts to users or teams
- Offers on-premise and cloud deployment options, giving organizations more flexibility for deployment
- Can highlight interdependencies between applications to map out how performance issues can impact businesses operations
- Can automatically detect databases, server hardware, and devices for real-time asset management
Cons:
- Can take time to fully explore all features and options available
ManageEngine Log360 is offered in two versions: Free and Professional. The Free edition is limited to monitoring 25 workstations. You can get the Professional edition on a 30-day free trial.
3. ManageEngine EventLog Analyzer – FREE TRIAL
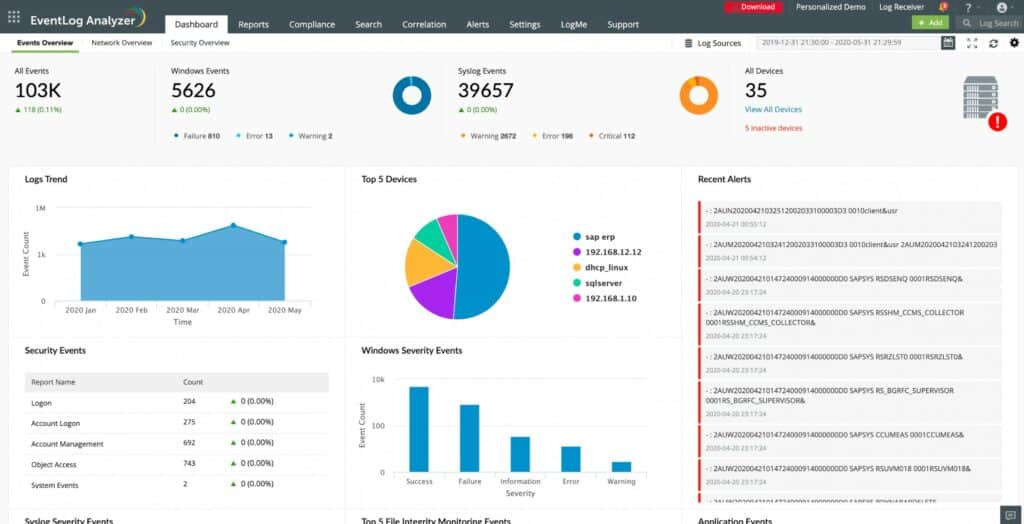
You can monitor system logs with ManageEngine EventLog Analyzer, a SIEM tool, and Splunk alternative. You may gather logs from over 700 sources using a combination of agentless log collection, agent-based log collection, and log imports with ManageEngine EventLog Analyzer. Identify the essential security incidents by navigating through collected logs with customized filters.
Key features:
- Filters
- Real-time event correlation
- Compliance reports
- Alerts
- Log collection and analysis
To uncover assault trends, real-time event correlation analyses log data. To determine when an alarm is raised, the product comes with 30 pre-configured SIEM correlation rules. The platform's correlation rules can also be adjusted, allowing you to specify different attack patterns and trigger situations.
You can use compliance reporting templates to prepare for audits for PCI DSS, HIPAA, FISMA, GDPR, SOX, and ISO 27001. Schedule compliance reports to run automatically, and then share them with the rest of your team in HTML, PDF, and CSV.
Pros:
- Customizable dashboards that work great for network operation centers
- Multiple alert channels ensure teams are notified across SMS, email, or app integration
- Uses anomaly detection to assist technicians in their day-to-day operations
- Supports files integrity monitoring that can act as an early warning system for ransomware, data theft, and permission access issues
- Forensic log audit features enable admins to create reports for legal cases or investigations
Cons:
- Takes time to fully explore the entire ManageEngine ecosystem
ManageEngine EventLog Analyzer is an excellent tool for businesses in need of a simple event log management solution. A free version is available that supports up to five log sources. The Premium Edition, which costs $595 (£464.64), is the most expensive paid edition. You can begin by registering for a 30-day free trial.
4. Site24x7 – FREE TRIAL
Site24x7 serves as a strong Splunk alternative by providing comprehensive log analysis, system monitoring, and performance insights in a cost-effective package. While Splunk is renowned for its advanced data analytics and log management features, Site24x7 delivers similar functionality with a focus on ease of use and affordability.
Key features:
- Full-stack observability
- Log management
- Log analyzer
- Customizable alerts
- Integrations with third-party systems
Site24x7’s log management tool provides real-time log data collection from various servers, networks, and applications, allowing users to gain immediate visibility into system performance, security incidents, and compliance status. The platform supports log aggregation, search, and filtering capabilities, enabling IT teams to quickly detect anomalies, troubleshoot issues, and ensure the overall health of their infrastructure.
One of the advantages of Site24x7 over Splunk is its simpler configuration and setup, making it accessible to organizations with limited resources or technical expertise. The platform also offers powerful monitoring and alerting features, helping businesses track key performance indicators and security events across their network.
Pros:
- Customizable dashboards for visualizing log data and monitoring key metrics
- Ensures adherence to industry standards and regulatory requirements
- Allows users to search and query log data to identify specific events, errors, or patterns
Cons:
- No on-premises option – this is a cloud-based SaaS platform
The Site24x7 platform is adaptable and can be added to by activating integrations, which are held in a library of plug-ins. You can examine the system in more depth by accessing a 30-day free trial.
5. Datadog Log Management
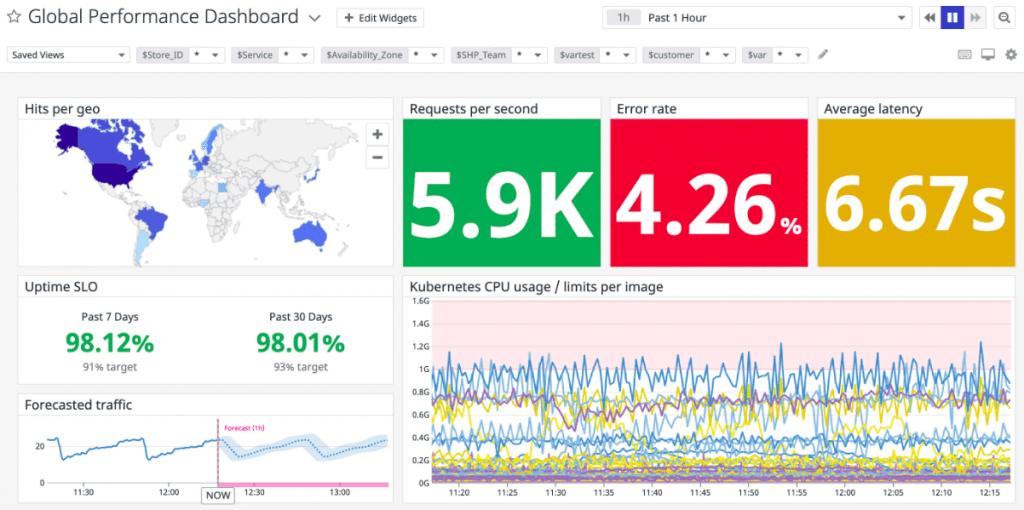
Datadog is a log management and cloud monitoring service that lets you collect log data from any source and store it centrally. Moreover, you can manage, search, and filter your logs with Datadog to find security incidents. The dashboard, which includes graphs and charts, can be used to view log data.
Key features:
- Central log collection
- Alerts
- Dashboard
- Filters
- Graphs and charts
- Log-processing pipelines
You may also use the platform to develop log-processing pipelines. Log-processing pipelines allow you to process logs gathered through integrations automatically. You can, for example, establish a channel for NGINX or MongoDB to automatically extract data from such service.
When a critical service is experiencing performance challenges, you'll receive an alert. External services such as Slack, Microsoft Teams, and Hangouts Chat can be used to route alerts so that you and your team can process them more quickly.

Pros:
- Supports live log collection as well as long-term archival options for SIEM solutions
- Can monitor both internally and externally giving network admins a holistic view of network performance and accessibility
- Allows businesses to scale their monitoring efforts reliably through flexible pricing options
Cons:
- Would like to see a longer trial period for testing
Datadog is a solid choice for businesses looking for a cloud-based log management system with a wide range of log gathering options and advanced data visualization capabilities. Log Management costs $1.27 (£0.99) per million log events each month, with a seven-day retention period.
6. Sumo Logic
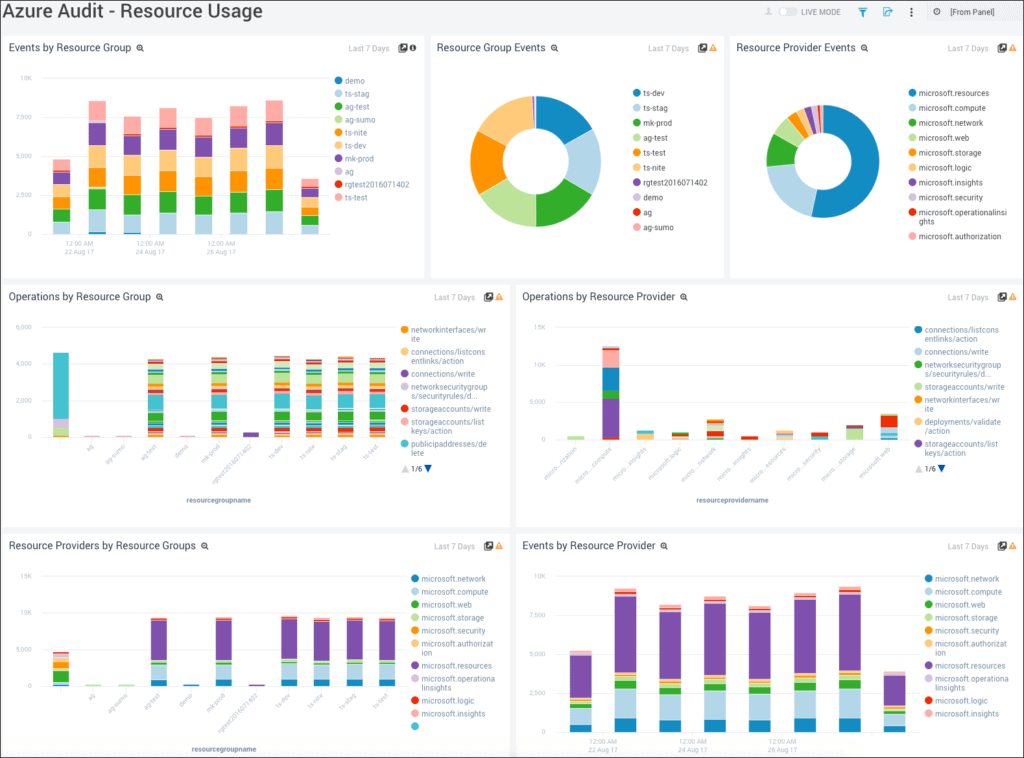
Sumo Logic is a SaaS-based log management application that can monitor both on-premises and cloud-based services. The platform includes integrations for AWS, Microsoft Azure, Google Cloud, Kubernetes, and Docker, allowing it to work alongside your current tools and services.
Key features:
- Threat intelligence
- Graphs and charts
- Integrations
- Dashboard
- Real-time alerts
- Log collection
Dashboards with graphs, charts, and predictive analytics give you a holistic picture of security events, making it easier to spot and fix problems as they arise. You can apply machine learning-driven root cause analysis to figure out what's causing a problem.
Indicators Of Compromise (IOC) indicators are highlighted in real-time by threat intelligence, allowing you to discover threats to your infrastructure faster. Anomaly detection aids in detecting performance anomalies, and real-time alerts alert you to hazards so you may act quickly to remedy them.

Pros:
- Supports multiple environments (Linux, Windows, and Mac OS)
- Simple installation – Uses wizards to streamline install and add-ons
- Has a host of templates and premade assets making the experience user friendly
Cons:
- Better suited for small to medium-sized businesses
Sumo Logic is one of the most reliable and easy-to-use SaaS-based Splunk alternatives. The Essentials version, which includes log analytics, dashboards, and real-time alerting, starts at $3.00 (£2.34) per GB of data.
7. SolarWinds Security Event Manager
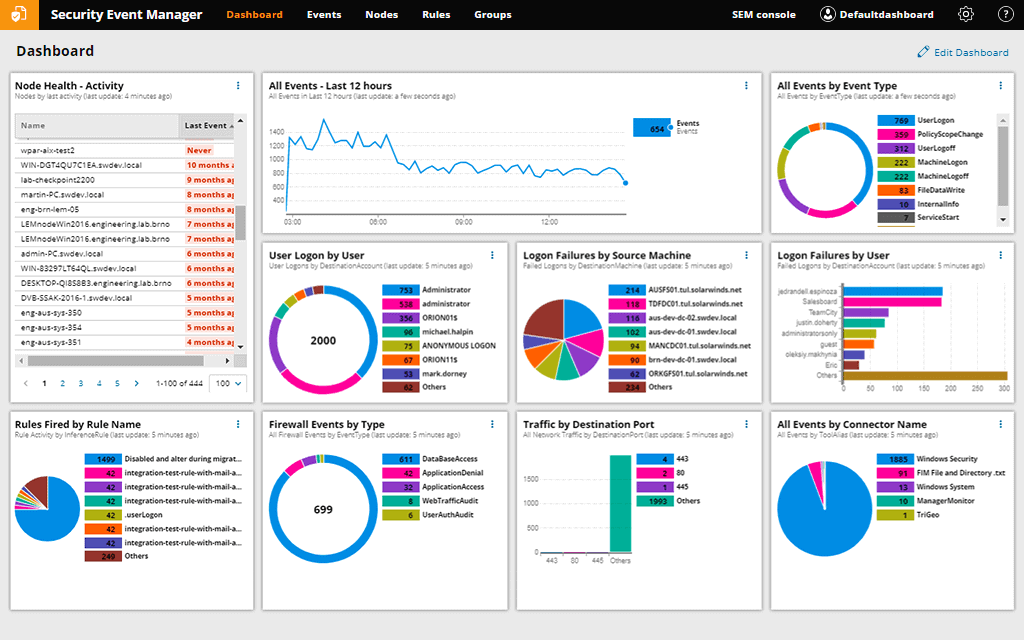
The SolarWinds Security Event Manager is a SIEM tool that collects logs in a centralized location. The platform collects data and using threat intelligence to detect and respond to threats automatically. When a security event occurs, threat intelligence notifies you and sends notifications directly to your inbox so you can keep track of them.
Key Features:
- Compliance reports
- Centralized log collection
- Automated threat detection and response
- Notifications
- Graphs and charts
- Dashboard
A dashboard view gives you a complete picture of what's going on in your environment. There are various visualization choices available, including graphs and pie charts, that allow you to quickly detect performance trends. To help identify compromised machines, you can look at the Login Failures by Source Machine pie chart.
Compliance reports make it simple to audit your environment. HIPAA, PCI DSS, FISMA, GLBA, GPG13, and other regulations have compliance reports available out of the box.

SolarWinds Security Event Manager(SSEM) is a SIEM solution for businesses looking for a low-maintenance, threat-intelligence-driven solution. Windows, macOS, and Linux are all supported.
Pros:
- Enterprise-focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Historical analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product built for professionals, requires time to fully learn the platform
You can test out SolarWinds Security Event Manager free through a fully functional 30-day trial. The starting price is $2,525 (£1,971).
8. Sematext Logs
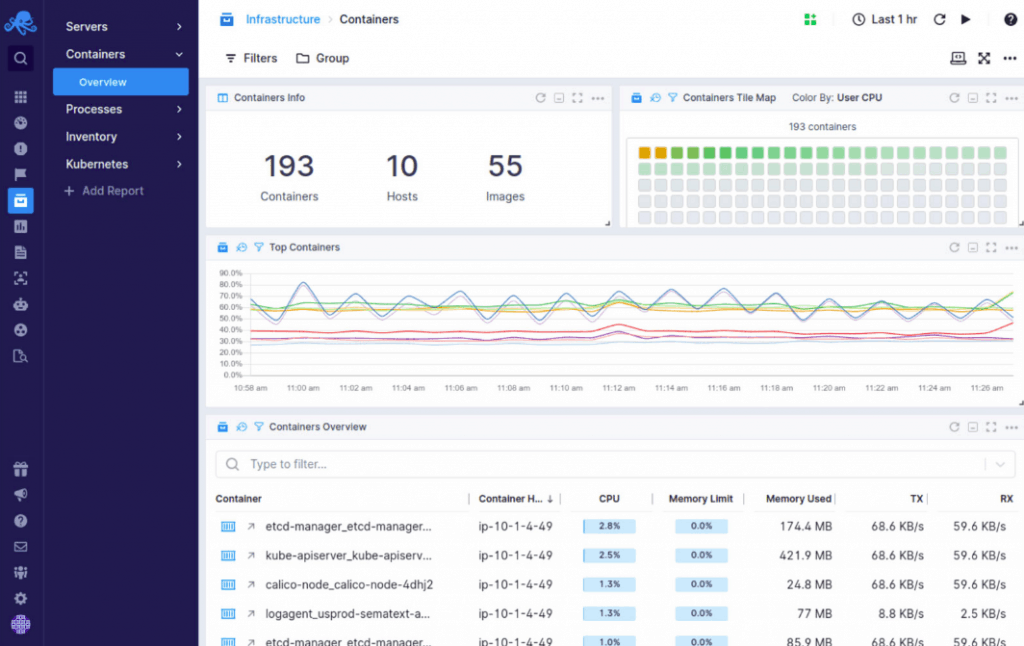
Sematext Logs is a log management tool for gathering logs from your infrastructure. Logs can be searched using simple query syntax to pinpoint specific events. You can construct custom dashboards using Sematext Logs to track performance trends in real-time.
Key features:
- Real-time alerts
- Graphs and charts
- Custom dashboards
- Reports
- Log data collection
You can start building reports in the Reports pane when constructing a dashboard to collect specific metrics to monitor. Graphs and charts are included in dashboards to help you visualize performance and security issues. When specific threshold circumstances are met, real-time alerts send you an email, Slack, or PagerDuty notification.

Pros:
- Uses Elasticsearch for flexible query options
- Supports data outside of just event logs such as SNMP reports
- Supports threshold-based alerts, ideal for maintaining SLAs
- Has a freeware version for testing
Cons:
- Relies on Kibana for data visualization
Sematext Logs is one of the most cost-effective log management solutions available, allowing you to have complete control over your monitoring experience. The Logs bundle is priced at $50 (£39.03) each month.
9. LogRhythm NextGen SIEM Platform
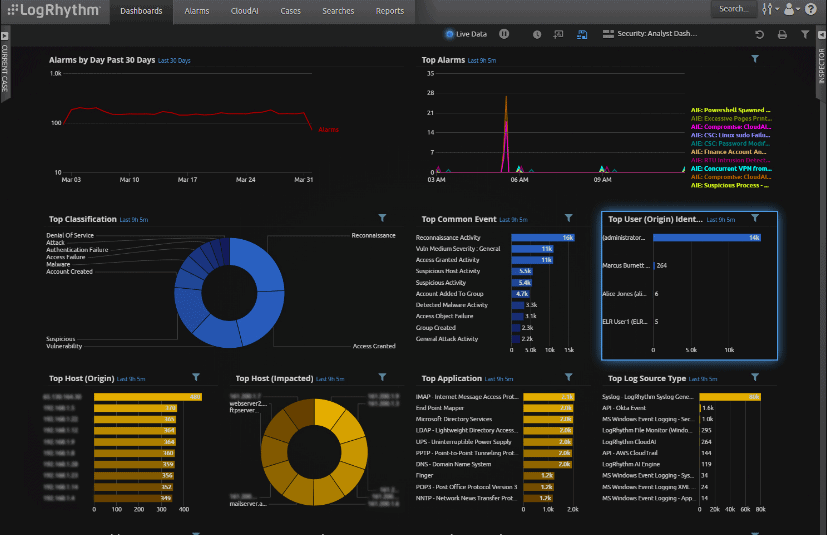
The LogRhythm XDR stack includes the LogRhythm NextGen SIEM Platform, which is a log analysis tool. LogRhythm AnalytiX, LogRhythm DetectX, and LogRhythm RespondX are the three tools that make up the LogRhythm XDR stack.
Key features:
- Alarms
- Custom dashboards
- Integrated SOAR
- Centralized log storage
- Structured and unstructured search
- AI engine
AnalytiX saves log data in a central location that you can search using structured and unstructured searches. Custom dashboards with visualization options for deeper visibility can also be used to view log data. An AI engine analyzes the records to identify potential risks. Out of the box, the engine has over 900 customizable correlation rule sets.
DetectX is a security analytics company that finds security flaws and sets off alarms. Machine learning discovers dangerous patterns and highlights them to the user, allowing the technology to spot dangers automatically. After the system detects a threat, the integrated SOAR solution RespondX will automatically undertake remedial actions.
Pros:
- Uses simple wizards to setup log collection and other security tasks, making it a more beginner-friendly tool
- Sleek interface, highly customizable, and visually appealing
- Leverages artificial intelligence and machine learning for behavior analysis
Cons:
- Would like to see a trial option
- Cross-platform support would be a welcomed feature
If you need a way to automate the log management process, the LogRhythm NextGen SIEM Platform is a viable option to consider. To request a price, you must contact the company directly for price information.
10. Paessler PRTG Network Monitor
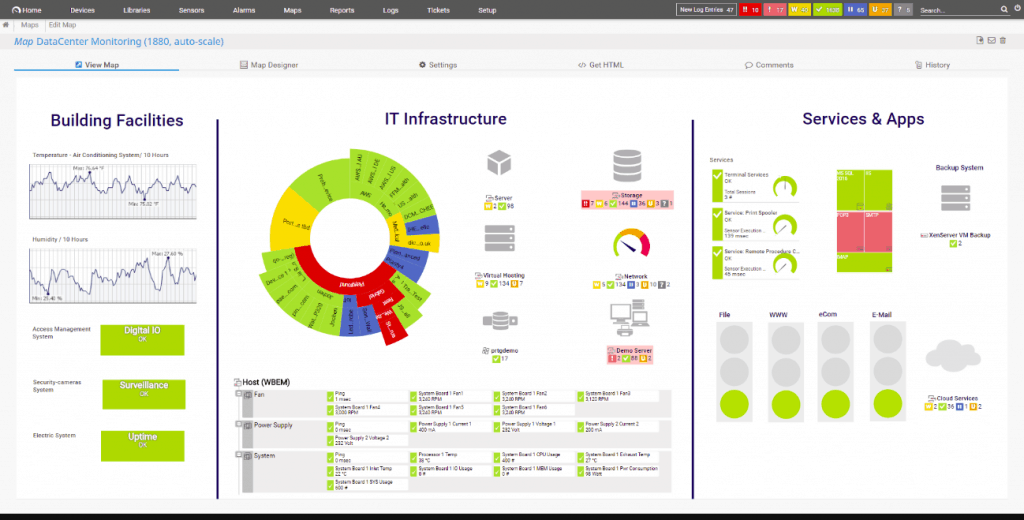
Paessler PRTG Network Monitor is a free network monitoring and log monitoring solution from Paessler. You may collect log data with Paessler PRTG Network Monitor's out-of-the-box sensors. Sensors display performance data as numerical numbers and knobs, allowing you to monitor live and historical data efficiently.
Key features:
- Alerts
- Automated responses
- Syslog Receiver sensor
- Out-of-the-box sensors
- Windows Event log sensor
- Log monitoring
The Windows Event Log Sensor is a valuable sensor for log management since it can monitor Windows log files, including system and application logs. The Syslog Receiver Sensor is another sound sensor that lets you track the number of received Syslog messages per second, the number of warning messages per second, the number of error messages per second, and more.

You may set Paessler PRTG Network Monitor to send you notifications anytime a critical parameter is exceeded using threshold-based alerts. The system can deliver notifications by email, SMS, push notifications, Slack messaging, and SNMP traps, or it can reply automatically by running HTTP actions or programs.
Pros:
- Uses a combination of packet sniffing, WMI, and SNMP to report network performance as well as discover new devices
- Autodiscovery reflects the latest inventory changes almost instantaneously
- Drag and drop editor makes it easy to build custom views and reports
- Supports a wide range of alert mediums such as SMS, email, and third-party integration
- Supports a freeware version
Cons:
- Is a very comprehensive platform with many features and moving parts that require time to learn
Paessler PRTG Network Monitor is a great option for small businesses looking for a low-cost log management solution. Up to 100 sensors can be used in the freeware version. You can upgrade to a premium version if you need more sensors. For 500 sensors, the paid version costs $1,750 (£1,367). It's compatible with both Windows and Mac.
11. LogDNA
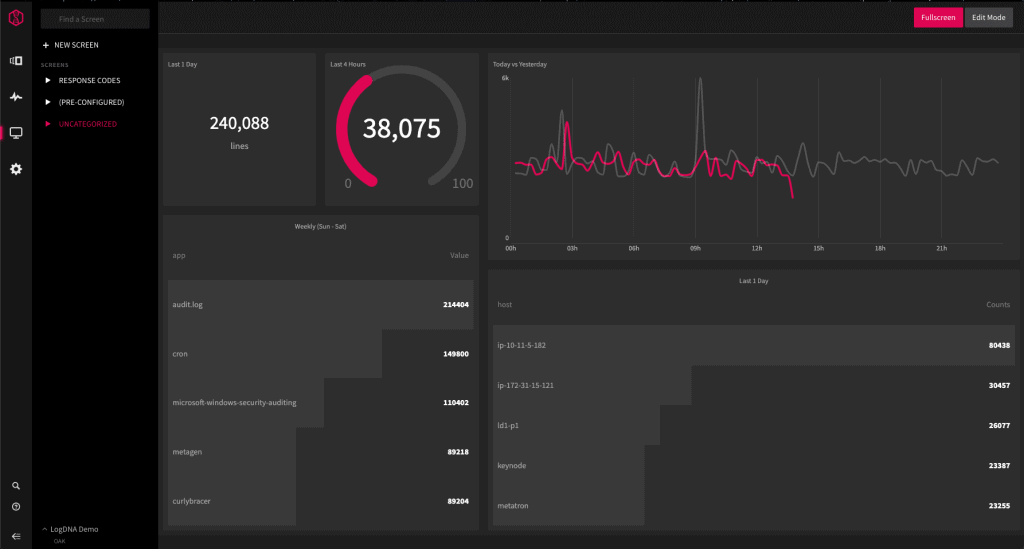
LogDNA is a free log management program for collecting and monitoring log data. Exclusion rules in LogDNA allow you to decrease the amount of log data you need to watch, making it easier to spot essential security incidents. Visualization tools such as charts and graphs make it easy to keep track of log data patterns at a glance.
Key features:
- Exclusion rules
- Usage reporting
- Graphs and charts
- Collect and monitor log data
- Alerts
- Team controls
Alerts provide immediate notification of system occurrences. The platform interfaces with various services, including PagerDuty, Slack, Webhooks, and other APIs, allowing you to receive alerts based on where you and your team are most active. Usage reporting gives you an up-to-date view of your log usage so you can see when resource consumption has to be managed.
You may utilize team controls to assist an entire team with a variety of features. Role-based access control, for example, allows you to restrict access to sensitive data, while SSO/SAML user authentication ensures that only authorized users have access to protected information.
Pros:
- A minimalistic interface helps highlight key insights
- Powerful exclusion rules are easy to build and customize
- Vast API library for integrations into other tools and messaging platforms
Cons:
- The trial is only 14-days long
- Reporting could be made easier, specifically when building custom reports
LogDNA is a fantastic option for companies that want to lessen their reliance on manual log processing. The Free version allows for a single user to have an infinite number of hosts and sources. Moreover, paid versions to start at $1.50 (£1.17) per GB per month for up to five users. It runs on Windows, macOS X, and Linux.
12. Fluentd
Fluentd is a data ingest tool that can handle structured, unstructured, and semi-structured data. It serves as a link between data sources and destinations, converting and routing data for various platforms, services, applications, and computer languages. Fluentd is an open-source technology used as a data aggregation service for Microsoft Operations Management Suite and other services. Fluentd is primarily a data gathering and routing service, with no log shipping or management capabilities. Plugins, which offer support for additional inputs and outputs, combine them with other solutions.
Key features:
- Filters
- Real-time event correlation
- Compliance reports
- Alerts
- Log collection and analysis
The CloudFront-log plugin, for example, can be used to ingest logs from Amazon CloudFront, while the elasticsearch plugin can be used to route logs to Elasticsearch. Fluentd only provides ingestion and routing services, so you'll have to develop your log management solution from the ground up. Fluentd has become a popular alternative to Logstash, transforming ELK into EFK. Fluentd is free in and of itself, but it, like the Elastic Stack, can become costly with time. Fluentd has a minimal memory and CPU footprint, but it relies on several other components to provide a complete log management solution. This is compounded by a time-consuming setup and customizing process.

Pros:
- Simple lightweight platform
- Free open source and transparent project
- Offers over 500 plugins to extend its functionality
- Available for Windows, Mac, and Linux environments
Cons:
- Not the best option for enterprises
- Could use more data visualization features
Conclusion
If you appreciate Splunk but feel it lacks a feature you need, there's no reason you couldn't supplement its capabilities with another tool.
Graylog and Datadog stand out as some of the best Splunk alternatives because of their cutting-edge user interfaces and superb visualization capabilities. We strongly advise that you explore numerous tools before purchasing to guarantee that you get a solution that closely suits your needs.