A DDoS attack is carried out with the help of several infected computers asking to access your network's internet resources at the same time. This leads to a slowdown in your websites and applications. It may not only cause financial loss but it can also lead to a dip in customer loyalty. Robust DDoS software or services are needed to protect your organization against any such malicious attacks.
DDoS protection software and services work to prevent such attacks on your websites and web resources by constantly monitoring the web traffic and setting a specific baseline for normal traffic inflow. A soon as an abnormal traffic flow is detected by the DDoS software it is diverted to a controlled source thereafter.
There are many DDoS services and software available today. While some are paid some of them offer free trials so you can test them out.
Here is our list of the top DDoS protection services:
- SolarWinds Security Event Manager – FREE TRIAL Simple, light-weight, and easy-to-use monitoring SIEM solution that provides several built-in connectors that gather logs from various sources and present them in a readable format. Get the 30-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A robust DDoS protection service that includes tools for vulnerability discovery, remediation, and prevention. Get a 30-day free trial.
- ManageEngine Log360 – FREE TRIAL provides unified cybersecurity that protects networks from DDoS attacks using AI, event correlation, and machine learning. Get a 30-day free trial.
- Sucuri Website Firewall Cloud-based web application firewall solution that protects your site from hackers, DDoS, viruses, and much more.
- Radware DefensePro A hybrid attack mitigation solution capable of performing L3 and L4 filtering operations in real-time for advanced DDoS and IoT botnet attack mitigation.
- Project Shield IA reverse proxy that sits between your website and the internet, filter the malicious traffic, and protects your site from layer 3/4 and layer 7 attacks.
- Nexusguard Web-based tool that protects your websites, applications, API and network infrastructure. It uses a multi-layered mechanism to identify, mitigate, and analyze DDoS attacks in real-time.
- Cloudflare One of the most powerful and widely used DDoS service providers. It can handle up to 51Tbps attack. It offers a free version with unmetered DDoS protection to the user.
- AWS Shield Ideal solution for small businesses. It protects your website for layer 3 and layer 4 attacks.
Our methodology for selecting the Best DDoS Protection Services:
- Prioritizing services that demonstrate quick and effective mitigation of DDoS attacks.
- Selecting services that provide real-time traffic monitoring and timely alerts for potential threats.
- Choosing services that can handle large volumes of traffic and adapt to varying attack vectors.
- Services must offer an easy-to-use interface and comprehensive reporting for efficient management.
- Considering the service's track record in DDoS protection and the quality of its customer support and documentation.
Top Best DDoS Protection Service or Software:
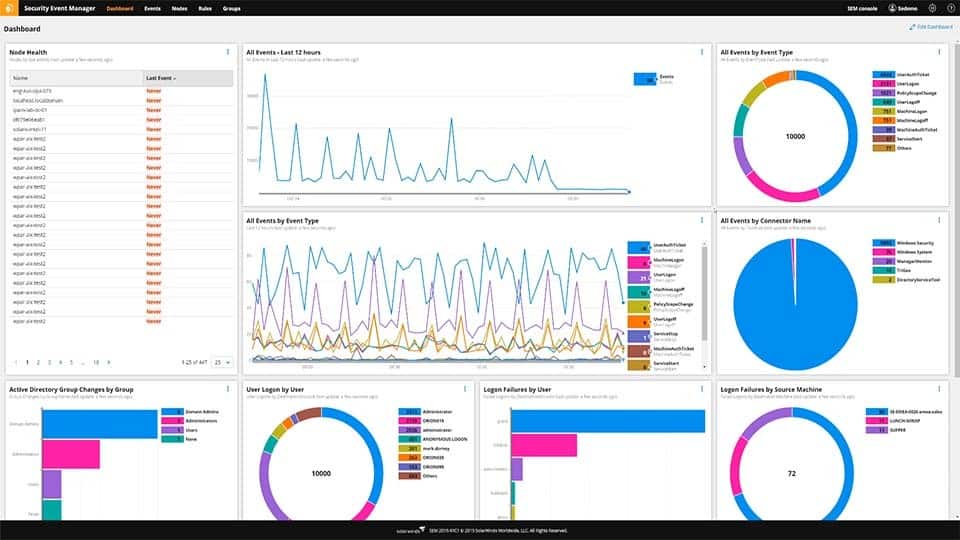
1. SolarWinds Security Event Manager – FREE TRIAL
SolarWinds is an active, lightweight, and easy-to-use monitoring SIEM solution that can improve your security posture. This affordable software comes with several built-in connectors that gather logs from various sources and present them in a readable format.
Key Features of SolarWinds SEM:
- It enhances security with insightful pfSense reporting and analysis.
- A centralized logon audit events monitor keeps track of all the logins and logouts.
- SolarWinds has advanced botnet detection capabilities that strengthen real-time monitoring.
- SIEM logs provide users with real-time insights for detecting and handling security risks.
- Automated monitoring and reporting simplify IT compliance management.
- SolarWinds uses a cyber threat analysis tool to protect networks.
- It successfully monitors events from large sources to detect DDoS activities on your network.
- Identifying threat patterns is simplified with the help of Event Correlation Software.
- Real-time log file analyzer leads to improved threat awareness.
- With file integrity monitoring software sensitive information is protected.
Why do we recommend it?
SolarWinds Security Event Manager is a top choice for its real-time monitoring capabilities, extensive log management, and advanced threat detection. It enhances security with its insightful analysis and automated reporting, making it a robust solution for enterprise-level security management.
Who is it recommended for?
This tool is best suited for larger enterprises that require a comprehensive SIEM system with a wide range of integrations and the ability to monitor large-scale networks.
Pros:
- Enterprise-focused SIEM with a wide range of integrations
- Simple log filtering, no need to learn a custom query language
- Dozens of templates allow administrators to start using SEM with little setup or customization
- Historical analysis tool helps find anomalous behavior and outliers on the network
Cons:
- SEM Is an advanced SIEM product built for professionals, requires time to fully learn the platform
SolarWinds is an effective way to maintain your network security. Its real-time activities and features make it one of the best software in the market. SolarWinds offer a fully functional 30-day free trial.
EDITOR'S CHOICE
SolarWinds Security Event Manager is our top pick for DDoS protection services, offering a comprehensive and efficient solution for attack mitigation. It stands out for its advanced features such as real-time monitoring, event correlation, and botnet detection, combined with a user-friendly interface and automated reporting. SolarWinds SEM's scalability and flexibility make it an ideal choice for enterprises, with its historical analysis tool providing additional insights into network anomalies. This combination of features makes it a robust defense against DDoS attacks.
Download: SolarWinds Security Event Manager 30-day Free Trial
OS: SolarWinds SEM is compatible with various operating systems
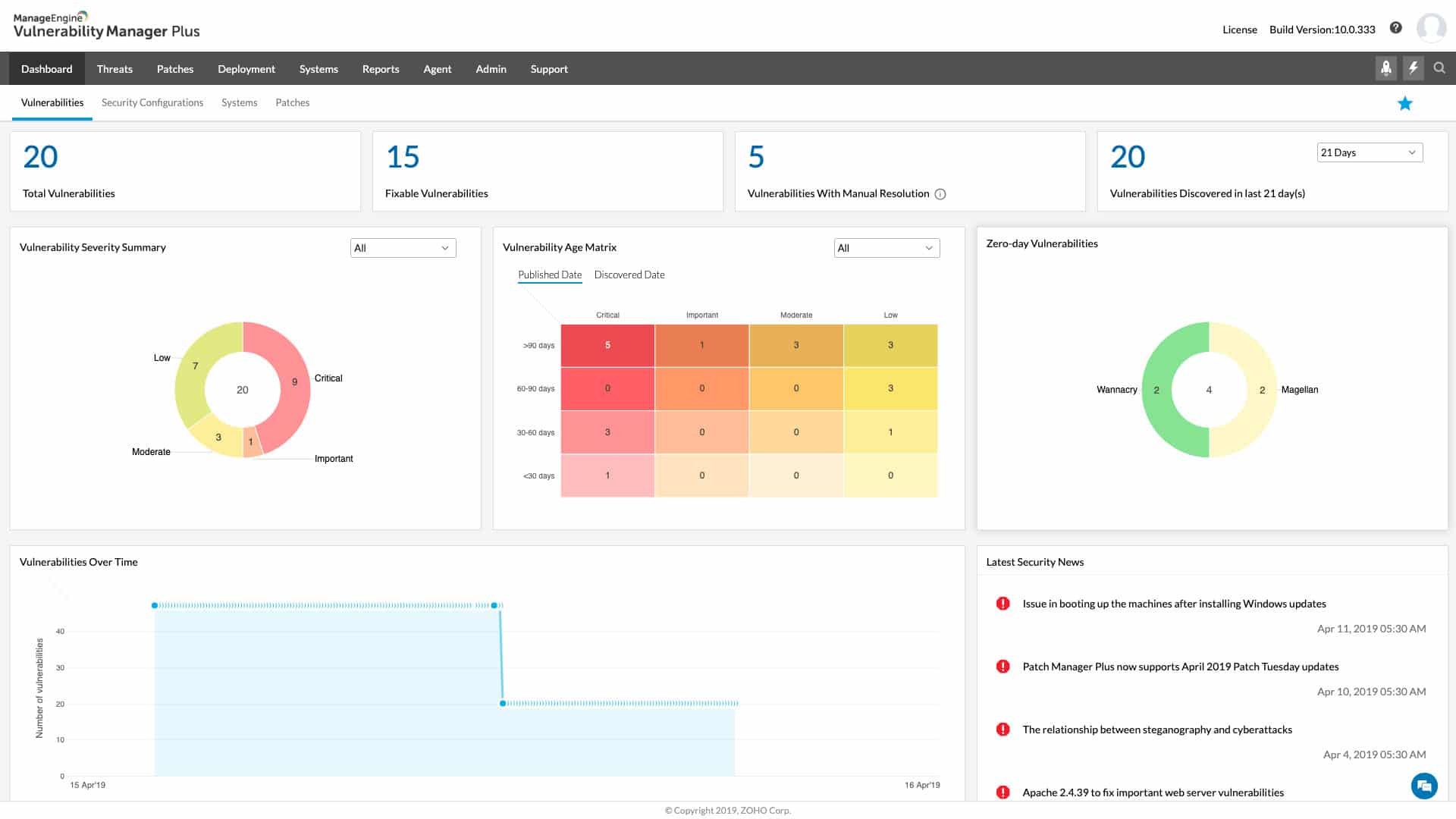
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus is a vulnerability management software solution that helps businesses and organizations identify, prioritize, and remediate security vulnerabilities in their networks and systems. It provides a range of tools and features for vulnerability assessment and management, including vulnerability scanning, risk assessment, reporting, and more.
Key Features
- Holistic vulnerability discovery, management, and remediation
- Offers vulnerability classification and prioritization
- Integrates well into enterprise networks and existing cyber security teams
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a comprehensive tool for vulnerability management, offering robust features for discovering, managing, and remediating vulnerabilities. Its integration with enterprise networks and continuous scanning capabilities make it a valuable asset for maintaining network security.
With Vulnerability Manager Plus, users can scan their networks and systems for vulnerabilities, assess the risks associated with them, and create plans to remediate them. This can help organizations improve their overall security posture and reduce their risk of cyber attacks.
Vulnerability Manager Plus includes the ability to scan for vulnerabilities regularly, generate reports and alerts, and prioritize vulnerabilities based on risk levels.
Who is it recommended for?
This tool is particularly suitable for organizations that require continuous vulnerability scanning and robust reporting to enhance their cyber security posture across diverse platforms.
Pros:
- Great for continuous scanning and patching throughout the lifecycle of any device
- Robust reporting can help show improvements after remediation
- Flexible – can run on Windows, Linux, and Mac
- Backend threat intelligence is constantly updated with the latest threats and vulnerabilities
- Supports a free version, great for small businesses
Cons:
- The ManageEngine ecosystem is very detailed, best suited for enterprise environments
Download a 30-day free trial of ManageEngine Vulnerability Manager Plus with All Features.
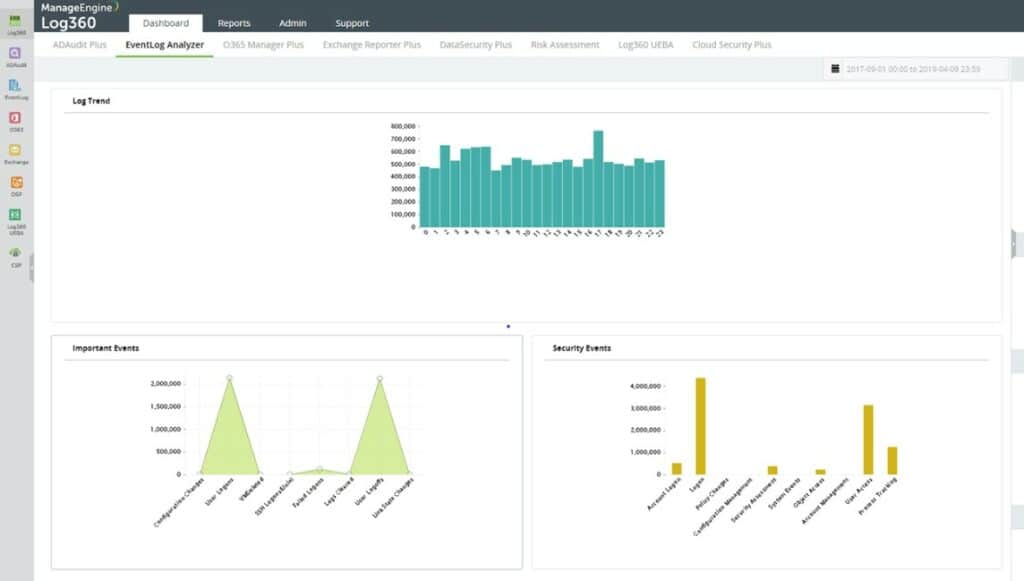
3. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is a powerful SIEM solution that offers advanced security analytics and monitoring capabilities to detect, prioritize, investigate, and respond to security threats across on-premises, cloud, and hybrid networks.
Key Features:
- AI-powered DDoS protection
- Support for a wide range of compliance standards
- Robust reporting and auditing capabilities
Why do we recommend it?
ManageEngine Log360 excels in providing advanced security analytics and DDoS protection. It leverages AI, threat intelligence, and user behavior analytics, making it a powerful SIEM solution for diverse cybersecurity needs.
ManageEngine Log360 excels in its ability to provide DDoS protection by leveraging real-time event correlation engines, threat intelligence, user and entity behavior analytics, and advanced threat analytics technology.
The platform also provides holistic security visibility, ensuring compliance with various regulatory mandates such as HIPAA for healthcare, PCI DSS, GLBA for finance, FISMA for US federal agencies, ISO 27001, SOX, and many more.
With its audit-ready report templates and compliance violation alerts, Log360 is the perfect tool for proactive threat hunting and incident response. Simply put, ManageEngine Log360 is a great choice for organizations looking to enhance their cybersecurity posture and protect their network from DDoS attacks.
Who is it recommended for?
Log360 is recommended for organizations that need a comprehensive SIEM solution with cross-platform monitoring capabilities, especially those needing to comply with various regulatory standards.
Pros:
- Great dashboard visualizations, ideal for NOCs and MSPs
- Can integrate multiple threat data steams into the platform
- Offers robust searching of logs for live and historical event analysis
- Provides monitoring cross-platform for Windows, Linux, and Unix systems
- Can monitor configuration changes, preventing privilege escalation
Cons:
- ManageEngine offers a suite of advanced services and features can time to explore and test out
You test out ManageEngine Log360 for yourself through a free 30-day trial.
4. Sucuri Website Firewall
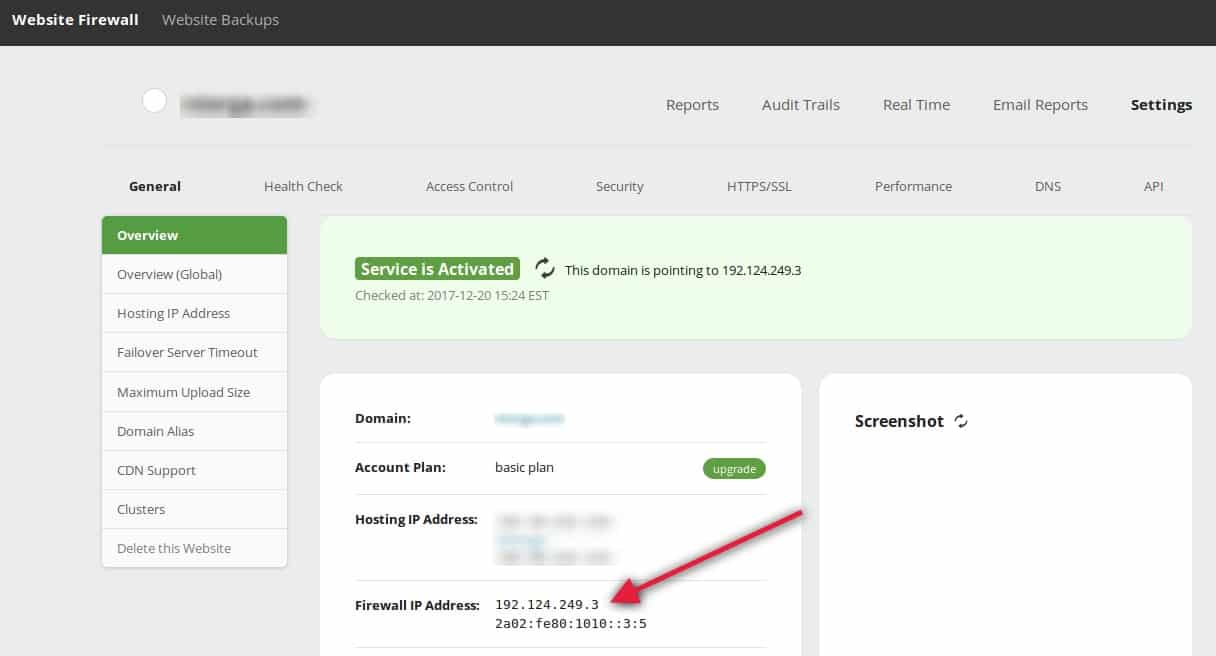
Sucuri firewall is an all-in-one solution for your website security needs. It is a cloud-based WAF that can protect your site from hackers, DDoS, viruses, and much more.
Key Features:
- It protects against SQL injections, XSS, RCE, and many other attacks.
- The geo-blocking feature blocks visitors from the top 3 countries with DDoS attacks.
- It successfully inspects all the incoming HTTP/HTTPS traffic and blocks the suspicious ones.
- Improves your security posture with virtual hardening and patching.
- Provides Brute force protection.
- All the plans provide full DDoS protection to the users.
- Gives one-click 2FA, captcha, and password protection on all your site pages.
- With the smart caching feature you can cache dynamic pages too.
Why do we recommend it?
Sucuri Website Firewall is a comprehensive cloud-based solution that offers robust protection against a range of threats, including SQL injections, XSS attacks, and DDoS attacks. Its geo-blocking and HTTP/HTTPS traffic inspection features enhance website security significantly.
It combines a WAF (Web Application Firewall), IDS (Intrusion Detection System), and CDN (Content Delivery Network).
Who is it recommended for?
This firewall is ideal for businesses of all sizes needing a versatile and easy-to-implement web application firewall with integrated DDoS protection.
Pros:
- Ideal solution for environments needing to protect their applications and testing environments
- Uses simple rules and templates to start mitigating/preventing DDoS attacks right away
- Users can block by IP, geolocation, traffic type, and behavior
- Works well in both medium and large environments – flexible pricing
Cons:
- VIP support requires the Business Platform pricing tier
Sucuri firewall offer 4 plans to its users: Basic, Pro, Business, and Custom Solutions. Depending upon your business requirement you can opt for any of the plans and rest assured that your website will be protected adequately.
5. Radware DefensePro
Radware DefensePro is a DDoS protection solution that helps you to fight against different kinds of attacks by mitigating zero-day DoS/DDoS attacks in real-time. It provides advanced protection from high-volume and short-duration threats including, DNS, TKS/SSL, PDoS, and RDoS attacks.
Key Features:
- Advanced prevention of DDoS attacks.
- DefensePro comes with a multi-purpose CPU that provides the flexibility and scalability needed for standard operations.
- Provides DoS Mitigation Engine that is capable to perform L3 and L4 filtering operations at a rate of over 10 million PPS.
- DefensePro hardware is specifically designed for DDoS attack mitigation
- Uses a Local-Out-of-Path attack mitigation solution to combine the best of in-line and out-of-path attack mitigation methods.
- DefensePro VA available from 200 Mbps through 20 Gbps of legitimate throughput.
Why do we recommend it?
Radware DefensePro is a high-capacity DDoS defense solution, known for its ability to mitigate zero-day DoS/DDoS attacks in real-time. Its multi-purpose CPU and advanced filtering capabilities make it highly effective against a variety of threats.
Who is it recommended for?
DefensePro is best suited for organizations that require a robust hardware solution for real-time attack mitigation, especially in high-traffic environments.
Pros:
- Can combat DDoS attacks as well as a myriad of other threats
- Supports L3 and L4 filtering
- Supports a variety of DDoS mitigation plans
Cons:
- Not ideal for those looking for a non-hardware solution
Learn more about Radware's full range of defensive products on their website.
6. Project Shield
Project Shield was launched in 2013 as a free service to news publishers, journalists, human rights organizations, and election monitoring sites. It is the creation of Jigsaw, which is an offshoot of Alphabet, Google’s parent company.
Key Features:
- Project Shield gives you unlimited protection with the help of its DDoS tools and Google’s infrastructure including layer 3/4 and layer 7 attacks.
- To enhance the site protection further it provides controls in the form of JavaScript cookies and IP blacklists.
- All the traffic flows through Google’s data servers where it is analyzed and filtered.
- With Project Shield, you have access to real-time site statistics. This allows a quick tour of the site traffic, bandwidth, and errors.
- Customizable caching strengthens the DDoS defenses, saves bandwidth, and improves the site performance too.
- An impressive feature about this service is that even if you approach it amid an attack it will help you out.
Why do we recommend it?
Project Shield is a unique offering that provides unlimited DDoS protection using Google's infrastructure. It is particularly effective in filtering layer 3/4 and layer 7 attacks, making it a reliable choice for targeted organizations.
It acts as a reverse proxy that sits between your website and the internet, filtering the potential malicious traffic.
Who is it recommended for?
This service is specifically designed for news publishers, journalists, human rights organizations, and election monitoring sites, offering them free, high-quality DDoS protection.
Pros:
- Free for journalists, human rights organizations, and new agencies
- Backed by a branch of Google
- Leverages Google’s infrastructure to inspect and mitigate malicious traffic
- Provides remediation for new customers during an attack
Cons:
- Not available for all users
So, if you belong to the media, an election, or human rights organization and are unable to afford the expensive solutions to protect your site from DDoS then Project Shield is here to your rescue.
7. Nexusguard
Your search for all-round protection against DDoS ends with Nexusguard. With this service provider, you can protect your websites, applications, API and network infrastructure too.
Key Features:
- It provides 3 pillar cybersecurity platform in the form of application protection, origin protection, and DNS protection.
- Nexusguard is loaded with a collective mitigation capacity of 144 Tbps and high-performing scrubbing centers that are spread out geographically.
- It employs a multi-layered mechanism to identify, mitigate, and analyze DDoS attacks in real-time.
- By using wire-speed Access Control Lists, Nexusguard filters the traffic for bandwidth flood.
- It also keeps a track of fake IPs and infected hosts.
- By using Statistical Analysis it identifies and filters exorbitant traffic rates from zombie clients.
- With the help of its DPI engine, Nexusguard can achieve comprehensive application layer intelligence.
- By applying rate limiting, the exploitation of system and bandwidth can be limited against the set baselines.
Why do we recommend it?
Nexusguard stands out for its comprehensive three-pillar cybersecurity approach and robust infrastructure, ensuring real-time protection against DDoS attacks with a remarkable 144 Tbps mitigation capacity.
Nexusguard offers 100% uptime to its users, which means you don’t have to worry about any disruptions.
Who is it recommended for?
This tool is ideal for organizations seeking extensive DDoS protection across websites, applications, and networks, especially those needing sophisticated traffic filtering and uptime assurance.
Pros:
- Offers a global network for nodes to mitigate attacks and outages
- Provides two-factor authentication for additional security
- Can monitor protection status and bandwidth protection through a simple dashboard
Cons:
- Must request pricing from their sales team
Nexusguard provides a host of customized solutions to monitor your site traffic and performance in real-time. You also have access to various reports generated that include ‘events monitored’, ‘attacks dropped’, ‘actions taken’, and so on. You can schedule a demo on their site.
8. Cloudflare
Cloudflare is one of the most efficient and powerful DDoS service providers on our list. With a network capacity of 51Tbps, it is 15 times larger than the biggest attack recorded. To keep pace with the latest forms of attacks Cloudflare uses an IP reputation database that successfully blocks threats across 20 million properties.
Key Features:
- It deploys rate limiting to restrict visitors with unusually high request rates.
- It offers 4 different versions to suit the needs of various enterprises and businesses.
- The Free version is offered to individuals with a personal website. This free tier offers unmetered DDoS protection to the user.
- Cloudflare acts as a reverse proxy that sits between the visitors and the host site to filter and detect DDoS.
- For protection against known Botnets, Cloudflare uses fingerprints for HTTP requests.
- This cloud-based DDoS protection system is capable of dealing with 3 and 4 layer as well as 7 layer attacks.
- The centralized and decentralized mitigation systems work in under 3 seconds.
- You can integrate Cloudflare logs with third-party SIEMs.
Why do we recommend it?
Cloudflare excels in DDoS mitigation with its expansive 51Tbps network and innovative IP reputation database, effectively shielding against the most aggressive attacks.
Who is it recommended for?
Perfect for businesses of all sizes, Cloudflare offers versatile solutions, from a free version for personal websites to advanced options for enterprises needing comprehensive attack protection.
Pros:
- One of the fastest DNS services on the market
- Can automatically update record changes from parent DNS servers
- Supports a fully functional free version (great for small businesses)
Cons:
- Offers a wide range of features that can take time to explore
The Cloudflare DDoS solution is one of the best-performing services in the industry. It provides a comprehensive solution against DDoS attacks to secure websites, applications, and networks too. You can contact their sales team to find out more.
9. AWS Shield
A product of the Amazon Web Series, the AWS Shield is an ideal DDoS solution for all the small businesses that choose to host with Amazon. This DDoS protection service protects against layer 3 and layer 4 attacks (Standard plan).
Key Features:
- AWS Shield employs flow monitoring to analyze incoming traffic.
- It is cloud-based and protects applications, DNS, and APIs.
- It also uses advanced defense tools like packet filtering and prioritizing traffic to manage traffic on the client network.
- It provides an added benefit if you use Amazon CloudFront and Amazon Route 53.
- With the advanced plan, you will get 24/7 support for DDoS attacks.
- In the advanced plan, AWS Shield deploys your Access Control List to protect you against the largest DDoS attack also.
- Detailed metrics on attacks are also provided with the advanced plan.
Why do we recommend it?
AWS Shield is specifically tailored for AWS environments, offering seamless integration and effective protection against layer 3 and 4 DDoS attacks, especially beneficial for those already using AWS services.
It offers two versions to its users; AWS Shield Standard and AWS ShieldAdvanced. The standard version is free while the advanced costs approximately $3000 per month.
Who is it recommended for?
Ideal for small businesses and enterprises using AWS infrastructure, seeking a centralized, cloud-based DDoS solution with the flexibility of Standard and Advanced plans.
Pros:
- Designed specifically for AWS cloud environments
- AWS customers can access AWS Shield from their existing AWS products
- Offers a centralized solution to protect AWS assets
Cons:
- Setup can be complex, requiring knowledge of AWS architecture
- Designed specifically for AWS – not the best option for non-AWS customers
Depending on how it is used, the AWS Shield can be one of the most costly DDoS protection plans. If you are looking for a basic level of DDoS protection then the standard plan is a good option. However, the advanced plan comes with plenty of features but at a high cost.
Conclusion
The above-mentioned are the 7 best DDoS protection solutions for you. You couldn't go wrong selecting any of the software aforementioned as they are all efficient on resources and perform well when it comes to protecting against DDoS attacks. Depending on your organization's needs and resources you can opt for the most suitable one.