Varonis is a data protection system that doesn’t follow conventional threat hunting techniques, which focus on trying to stop threats from spreading on a network or system.
Varonis uses advanced threat detection technologies that scan your priceless data and activity on your accounts.
If any suspicious activity is found, it is able to lock down your information so that no malicious applications are able to alter or damage your files.
It is able to lock onto insider threats as well, so if you have any employees within the organization that are trying to access information that they have no security clearance for, they will be prevented from handling this data.
Deep data is another element that works really well in Varonis, and it lets you rest easy knowing that your network is constantly being protected by continuous monitoring and alerting.
Here is our list of the best Varonis alternatives:
- SolarWinds Access Rights Manager – FREE TRIAL This software package provides a new front end for all of your Active Directory instances, enabling you to unify their management. It also provides analysis of groups, accounts, and permissions so that you can tighten up system controls. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL This service accesses AD and then tricks user activity as well as offering and analyzer of all permissions and groups. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine Endpoint DLP Plus – FREE TRIAL Offers real-time data monitoring, enforces data security policies, delivers detailed reports for breaches, analyzes user activity for insider threats, and aids GDPR/HIPAA/PCI-DSS compliance. Download a 30-day free trial.
- Lepide Data Security Platform This security monitoring system interfaces to AD and performs analysis of permissions and also user activity. It lets you make bulk changes to AS and stores logs of those changes for auditing. Runs on Windows and Windows Server or on cloud platforms.
- Netwrix Auditor A security assessment package that has a specific version for managing Active Directory. Installs on Windows and Windows Server.
- Stealthbits Stealthaudit This tool includes an analyzer for Active Directory that highlights weaknesses in your permissions structure. Installs on Windows Server.
Varonis also lets you understand the threat security classification system by looking at threat models that explain context and will help make your threat assessments that much more accurate. Overall, this is a decent product that works well for small to medium sized businesses.
The Active Directory functionality is probably the most useful feature for a system administrator or IT professional as it provides lots of details and insight into your operating environment.
There are plenty of audit trail records in Active Directory, so using the right application to sift through this mountain of data is essential.
Varonis is able to monitor Group Policy activity, and alerts users to the changes that are happening on your system, such as unauthorized user activity and change control violations.
You are able to look at comparative before and after stats that show you what has been going on as well.
It is also able to perform a risk assessment, which tracks your system’s health with predefined tools and dashboards that can be edited to your heart’s content.
You can highlight risks such as user passwords that never expire, or enabled system logins that shouldn’t be active.
Varonis is also an application that can be integrated with other analytical and reporting centered programs such as Splunk, LogRhythm, CyberArk, ArcSight, Radar and FireEye.
These programs take massive volumes of data and shape them into reports, graphs, and dashboards that let you visualize your data in a more human readable form.
There are also customizable APIs for you to choose from if you need to develop custom functions and integrations between your systems and Varonis.
This is especially useful if you need to analyze data from a custom made application that is lacking these advanced features.
Related Post: Best Active Directory Monitoring Tools
The best Varonis Alternatives of 2024:
If you are managing a Windows environment with Active Directory and other Microsoft technologies, then you know that getting the right information at the right time is essential.
We want to look at other solutions that are out there.
There are plenty of alternatives for you to try out, so we see what other applications are available for you to try out, and what features they have.
1. SolarWinds Access Rights Manager – FREE TRIAL
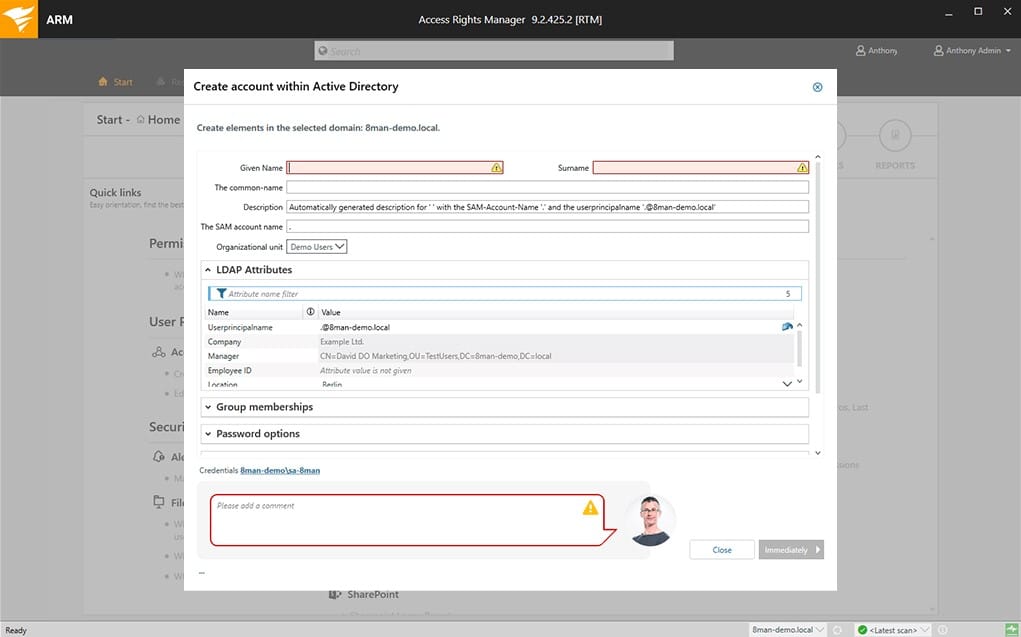
SolarWinds developed an awesome product that looks at the access rights within an Active Directory Environment, and have made a highly functional product that does exactly what it says.
It has recently been added to the SolarWinds family, so we can expect to see some changes to the platform, but these are likely to be only in the positive territory.
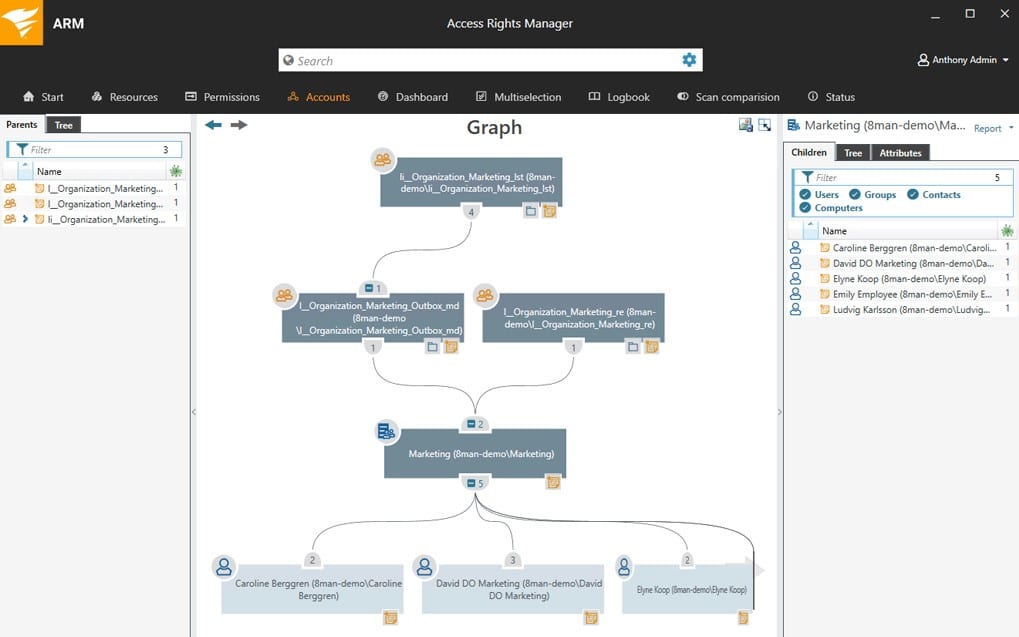
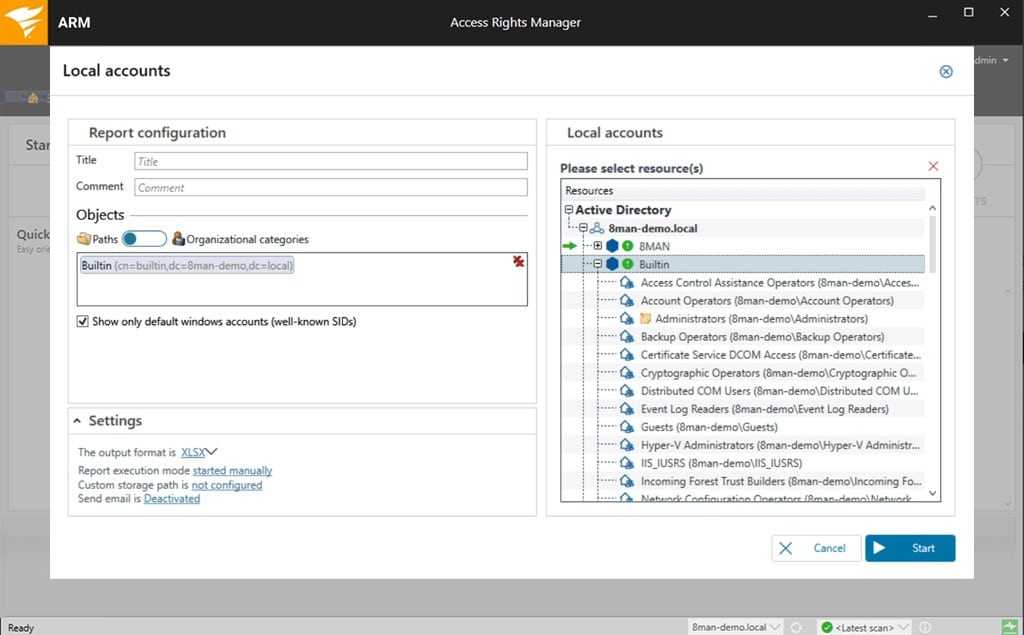
From this application you are able to look at permission analysis, documentation and reporting, security monitoring, roles and process monitoring, user provisioning and more.
Anyone that is looking for comprehensive permission analysis reports will find that Access Rights Management is really easy to get information on.
Permission Analysis displays a fully comprehensive overview of the entire access rights allocations that are currently active.
This helps with the resource allocation within the organization, and is a great way to stay on top of all of the current permissions that are active across your domains.
Security Monitoring is able to pick up any anomalous activity across the domain, and will tell you very quickly if something is not set up correctly.
User provisioning is easy to setup and easy to use, and new users are quickly identified so that any changes that need to be done can be quickly picked up.
This all helps with the documentation and reporting aspects of your job role as a system administrator.
This tool is very Comprehensive and has tons of Great features that make it one of the Best Varonis alternatives on the market.
Pros:
- Provides a clear look into permission and file structures through automatic mapping and visualizations
- Preconfigured reports make it easy to demonstrate compliance
- Any compliance issues are outlined after the scan and paired with remediation actions
- Sysadmins can customize access rights and control in Windows and other applications
Cons:
- SolarWinds Access Rights Manager is an in-depth platform designed for sysadmin which may take time to fully learn
We highly suggest you download a 30-day free trial and get started to get a feel of how it works!
2. ManageEngine ADAudit Plus – FREE TRIAL
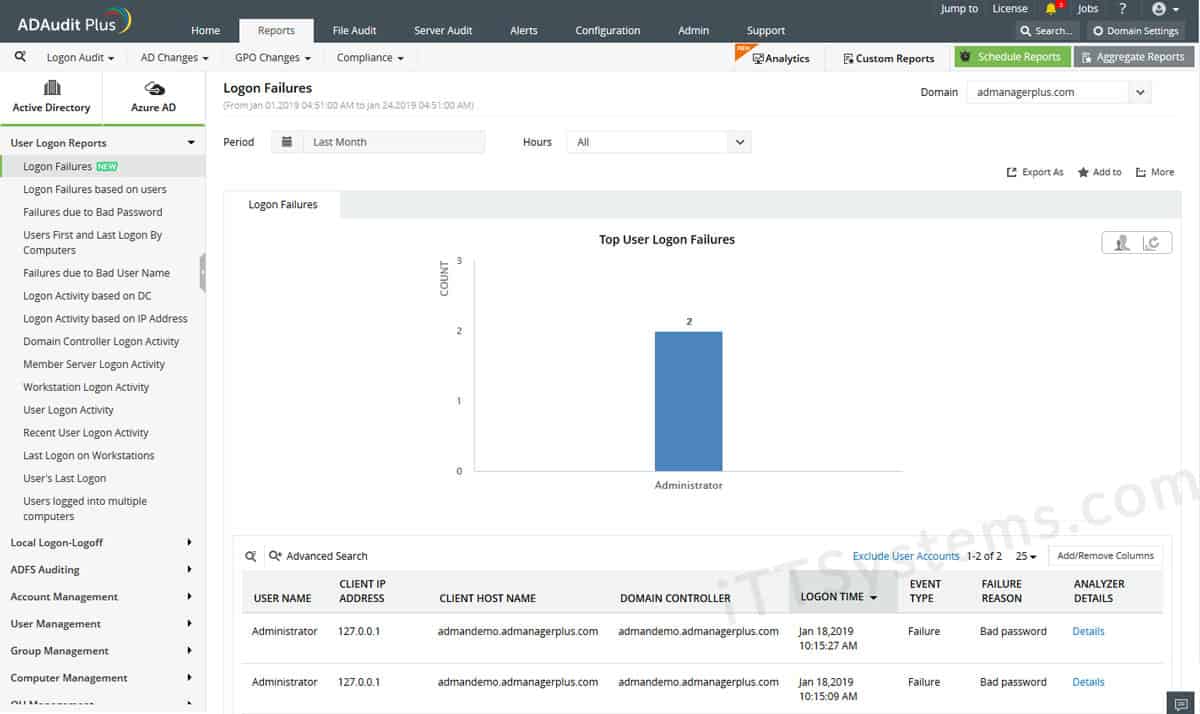
ManageEngine ADAudit Plus is a realtime tool that can tell you what is taking place on your network with regard to Active Directory activity.
It is able to audit essential service servers such as Domain Controllers, and can monitor and report on any and all activities that are currently underway within them.
If you think about the most commonly reported on features such as Users, Groups, GPO, Computers, OU, DNS, AD Schema, Configuration changes and over 200 detailed event triggers that will give you the ability to generate accurate and effective reports via the GUI.
These can also be activated via an email function that automatically delivers these reports directly to your inbox so that you can concentrate with other tasks.
Windows-based machines that run on an Active Directory need to be audited, and ADAudit Plus is able to do this easily, and in real-time.
It monitors, audits and reports with all of the information that you need to make accurate reports and assessments.
Because it is so comprehensive in the way that it captures data, it is a great tool for tracking insider threats.
It is able to pick up all of the telltale signs of account tampering, and can tel you what changes have been made from which computer, IP address and user, as well as the time and date of the changes.
If user logins are a concern in your organization, then you can use the User Login feature to actively track logon activity.
You can configure email alerts so that when a specific user logs in anywhere on the network, you will be informed and ready.
It also tracks login history as well as sign in attempts and failed password entries.
Pros:
- Detailed reporting, can generate compliance reports for all major standards (PCI, HIPAA, etc)
- Supports multiple domains
- Supports delegation for NOC or helpdesk teams
- Allows you to visually view share permissions and the details of security groups
Cons:
- Is a comprehensive platform that takes time to fully explore
Standard edition is $595 and the Professional version is $945. You can start with a 30-day free trial.
3. ManageEngine Endpoint DLP Plus – FREE TRIAL
Endpoint DLP Plus by ManageEngine is a robust tool offering comprehensive data loss prevention capabilities across endpoints. It serves as a compelling alternative to Varonis, particularly in its ability to monitor and protect sensitive information within an organization’s IT environment. Designed for businesses seeking to safeguard their critical data against leaks and unauthorized access, Endpoint DLP Plus excels in providing real-time monitoring and detailed control over data movement.
Key features:
- Real-Time Data Monitoring: Offers continuous surveillance of sensitive data across all endpoints, ensuring immediate detection of unauthorized access or data exfiltration attempts.
- Comprehensive Data Protection: Enforces strict data security policies to control how data is used and transferred, helping to prevent data breaches and ensure regulatory compliance.
- Detailed Reporting and Alerts: Generates detailed reports and real-time alerts on data security incidents, making it easy for IT teams to respond promptly and effectively.
- User Behavior Analytics: Analyzes user activities to identify unusual behavior patterns that may indicate insider threats or compromised accounts.
- Integrated Compliance Management: Supports compliance with major standards such as GDPR, HIPAA, and PCI-DSS, by providing tools to monitor, audit, and report on sensitive data handling.
Why do we recommend it?
Endpoint DLP Plus is recommended as a strong alternative to Varonis due to its comprehensive set of features that provide effective monitoring, protection, and management of sensitive data across endpoints. Its ability to deliver detailed insights and real-time security updates makes it a valuable asset for any organization concerned with data security.
Who is it recommended for?
This tool is particularly suited for IT administrators and security teams in medium to large organizations that handle large volumes of sensitive data and require stringent data protection measures. Endpoint DLP Plus is also ideal for businesses needing to adhere to strict regulatory requirements.
Pros:
- Extensive Monitoring Capabilities: Ensures thorough oversight of all data interactions and movements across endpoints
- Advanced Threat Detection: Detects and responds to both external and internal threats effectively
- User-Friendly Interface: Simplifies the management of data security protocols, making it accessible for users with varying levels of tech expertise
- Flexible Policy Implementation: Allows customization of security policies to meet specific organizational needs
- Cost-Effective: Offers a competitive pricing structure, providing a financially viable alternative to Varonis
Cons:
- Initial Setup Complexity: Setting up and configuring all features can be complex and may require a significant time investment
- Resource Intensive: High-level functionality may demand substantial system resources, potentially affecting system performance
Endpoint DLP Plus stands out as a strong candidate for organizations looking for an alternative to Varonis, offering comprehensive data protection capabilities that ensure sensitive data is securely managed and monitored. Its robust feature set, coupled with a user-friendly interface and cost-effectiveness, makes it an excellent choice for enhancing enterprise data security. Start a 30-day free trial.
4. Lepide Data Security Platform
Lepide Data Security Platform is a data-centric audit and protection solution that provides users with proven compliance and security features.
They have a massive client base, with big names such as KPMG and Coca-Cola being just 2 of them.
If you think that this system could work in your environment then why not schedule a demo below and take a look.
Lepide Data Security Platform is a complete solution that offers enterprise-level tools that not only work well on-premise, but in the cloud too.
It offers discovery and classification features that will let you find out what data is the most sensitive on your network, and where it is located.
It can also show you who has access to resources within your organization by looking at the Active Directory permissions and how they are currently set on your system.
User interaction is also traceable with the auditing and log features that the system works with, which means that you can figure out who has been accessing what.
Lepide Data Security Platform also ships with a highly functional dashboard that shows you exactly what is going on within the network.
It allows you to see an overall perspective of how the system is currently running, as well as how the current environment has been changed, as well as by who.
This gives you a powerful and real time tool for tracking insider threats and suspicious user activity.
The Access Government Insights dashboard lets you see exactly what you need to see if you are monitoring files and modification information.
This means that any changes that are detrimental to the system are easily detected and can then be acted on.
Over all the system works really well and is user-friendly to setup and use, which is great all round.
Pros:
- A simple way to see the last login, name, and CN path of multiple accounts at once
- Can quickly create CSVs or HTML format reports
- Supports bulk AD objects changes
- Lightweight – doesn’t require a lot of resources
- Completely free
Cons:
- Fairly limited, similar tools allow for more functionality like bulk password changes and unlocks
Pricing: Pricing is available on request, for more information check out the following link over here.
Download: https://www.lepide.com/data-security-platform/
5. Netwrix Auditor
Netwrix Auditor for Active Directory is a reporting tool that offers additional features such as security intelligence within an Active Directory Environment where it is able to look at the Group Policies that are in place.
This is very helpful as it gives you an idea of what is happening with security policies within the environment, and is especially useful if you are tasked with generating reports for management to look at.
Things that are normally quite difficult to compile into a report are made easy with Netwrix, with things such as locked out accounts, password expiry and other user related metrics all easily available for putting into a report.
Netwrix Auditor features comprehensive change auditing that detects all changes in the Active Directory system, and alerts to Group Policy changes.
It also provides you with the important facts that you need to establish who changed which settings, and when. This is extremely important when security intelligence is required for investigations.
All of these vital pieces of information are easily accessible and can be added to a report without too much hassle, which is great if you are responsible for compiling vast lists of users for an organization.
Netwrix Auditor also has built-in reports that include critical changes to the Active Directory system, including password policy changes, software settings, domain controllers, OU, and AD users.
This means that if you pick up any abnormalities you can take swift action and query any activity that seems out of place and abnormal.
Pros:
- Offers detailed auditing and reporting that helps maintain chain of custody for sensitive files
- Offers hardware and device monitoring to track device health alongside security
- Allows sysadmin to implement automated remediation via scripts
- Integrates with popular help desk platforms for automatic ticket creation
Cons:
- The trial could be a bit longer for testing
Pricing: There are three different pricing models available, depending on your organization’s size and requirements. To find out which one would suit you the best, check out the pricing page here, and send them a pricing request.
20-Day Free Trial Available below as well!
Download: If you would like to try out the application it can be downloaded from here:
https://www.netwrix.com/active_directory_auditing.html
6. Stealthbits
Stealthbits has been designed as a reporting and auditing tool that gives you access to all the information in your active directory.
This helps you to identify any problems in your current setup and also to further secure the AD setup and optimize it after you have identified any inefficiencies and security problems along the way.
AD Objects and Attributes are important metrics to keep on top of, so it is essential that you use a tool like this to give you greater visibility with what is actually happening within the Active Directory itself.
Stealthbits takes all of this information and helps you make informed decisions about how you should be running the Active Directory system.
Other important features to look out for include privileged accounts and users who may have access to files and network resources that they shouldn’t.
The interface is easy to use, and the pre-made reports are quite helpful, especially if you have been asked to look at specific reporting flags such as password expiry and account lockout frequency.
Another important factor when looking at how to manage your Active Directory reporting tasks is Group Policy Objects, also known as GPO.
From here you can audit the GPO and order the reports by whichever metric you need.
The reports are useful if you need to find out if specific users have access to important files and network shares.
If you do not have the right tools for looking at Active Directory, then you are not going to be able to investigate fully when you come across issues on your system.
Stealthbits lets you keep track of the inventory of your network, so that you can report and analyze any of the issues that you might be experiencing within your company’s network.
Pros:
- Simple yet informative reporting and admin consoles
- Can easily view account permissions to identify security issues and leftover accounts
- Premade reports help you get started right away
- Can set multiple alert flags to streamline your audits
Cons:
- Can take time to explore all features
Pricing: Check out pricing here.
Download: https://www.stealthbits.com/active-directory-auditing-solution
Conclusion
The importance of Auditing and Reporting Active Directory Credentials, Permissions and other valuable information is essential if you are trying to remain compliant with the rules and regulations of your particular industry.
While it is not impossible to generate reports from a standard Active Directory installation, it is certainly not the easiest thing to do.
When you need to find very specific events and instances of activity then it is always better to use a third-party tool when it comes to creating AD reports.
The long lists of features that each of these applications brings to your own situation will be very useful to you and your team, especially if you need to maintain some form of change control in your environment.
We hope that you have found this information useful and interesting and that if you are in the market for a similar solution then we hope that you can now make an informed decision about which application could suit your requirements the best.